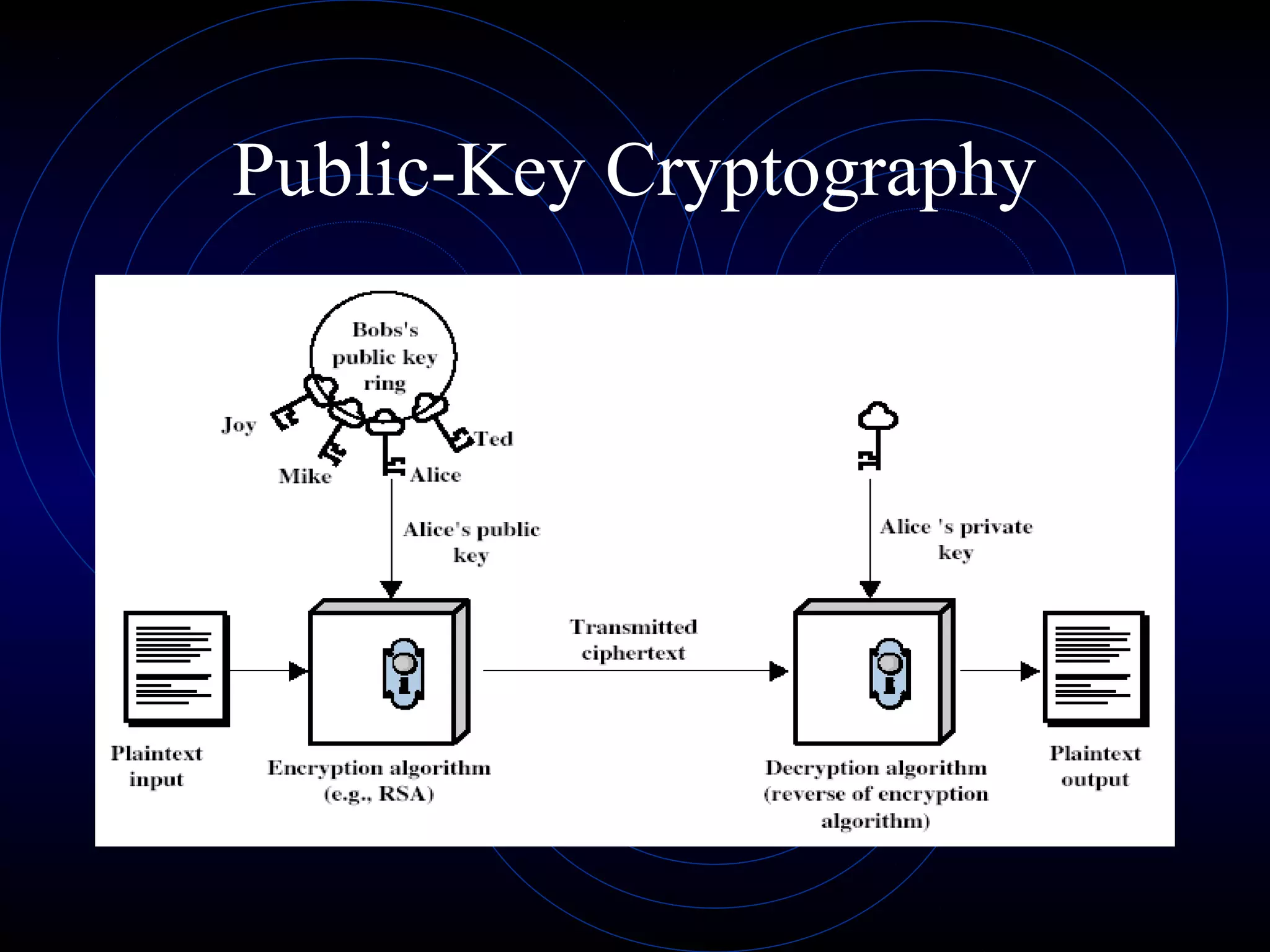
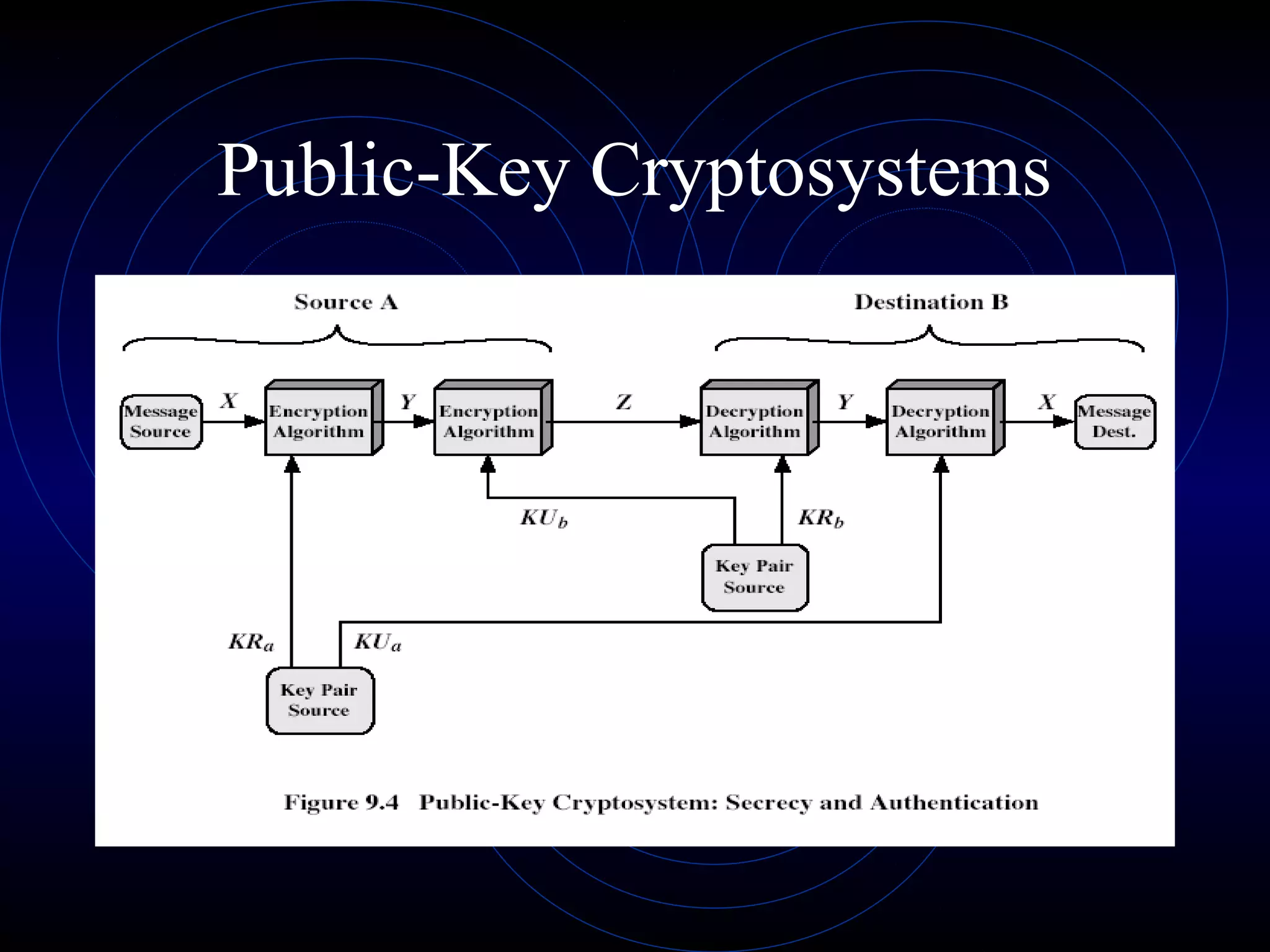
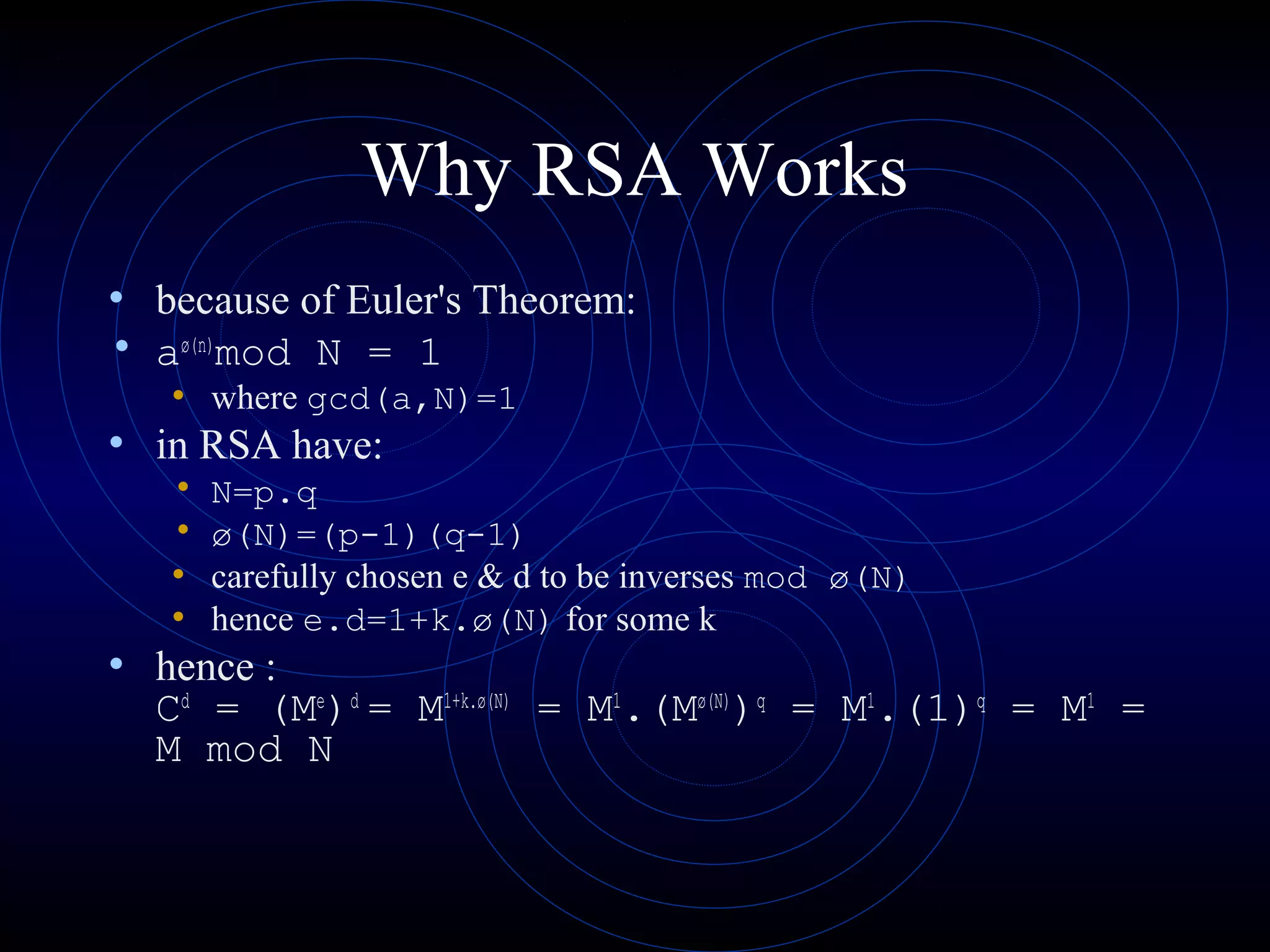
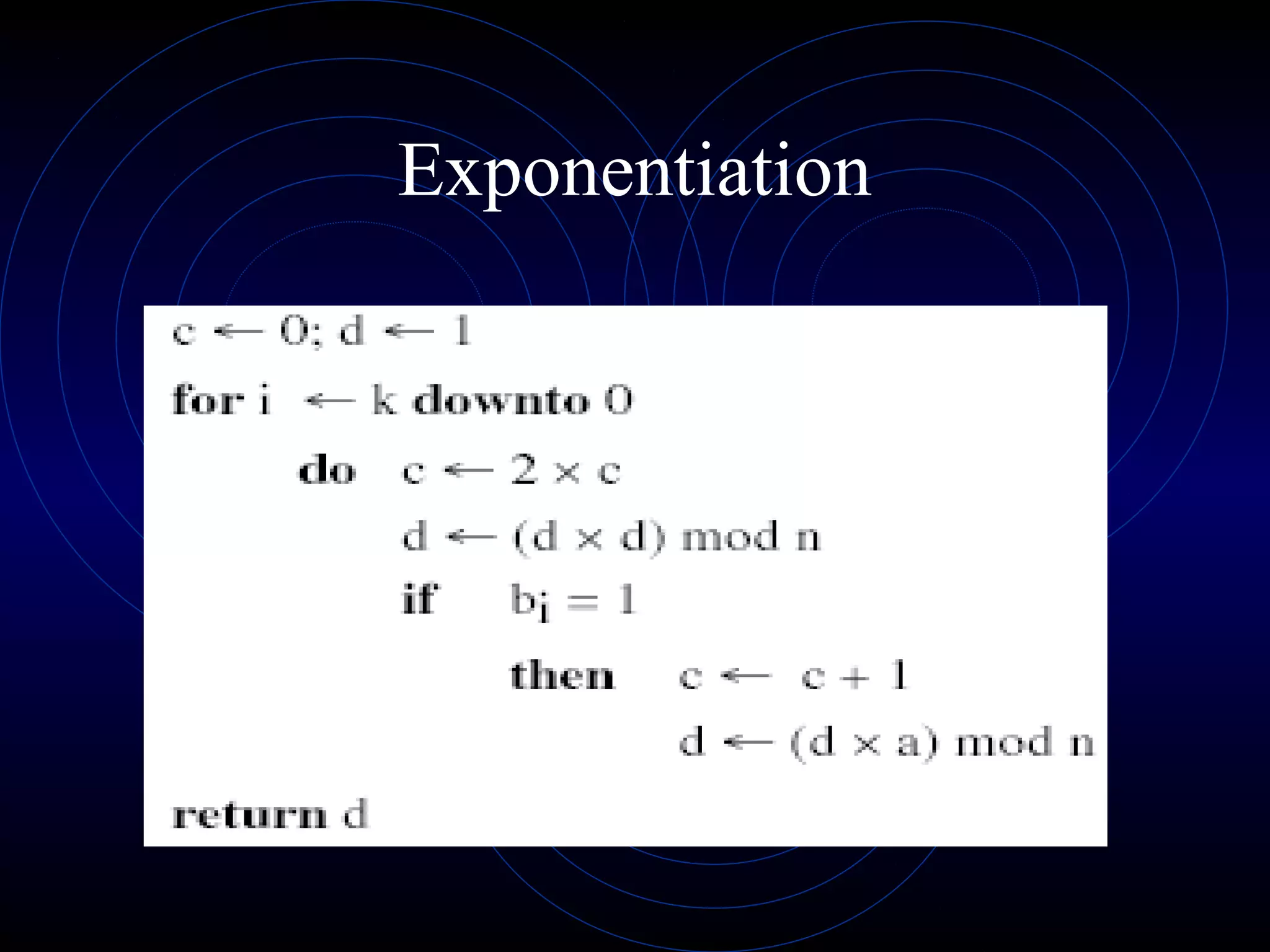
This document discusses public key cryptography and the RSA algorithm. It begins by explaining the limitations of private key cryptography and how public key cryptography addresses issues like key distribution and digital signatures. It then describes how RSA works, using two keys - a public key for encryption and a private key for decryption. It explains the key generation process, how messages are encrypted and decrypted, and discusses the mathematical principles and security of the RSA algorithm.