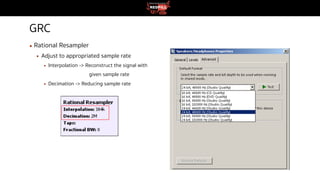
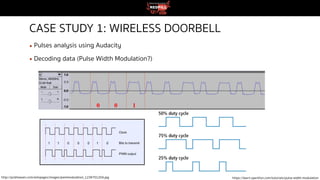
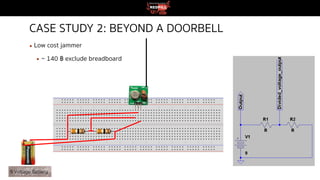
This document discusses radio frequency (RF) hacking beyond just broadcast radio. It begins with warnings about legal restrictions on signal interference and jamming. It then provides an overview of RF communication technologies and spectrum regulations in Thailand. Several RF security assessment tools are presented, both hardware tools like software-defined radios and software like GNU Radio Companion. Three case studies are described that demonstrate capturing wireless signals from devices like doorbells and car key fobs and retransmitting them using Raspberry Pi. Issues like rolling codes that change signals over time are also addressed. The document emphasizes that RF hacking skills require responsible and legal use.