Report (10)
•
0 likes•779 views
This threat report summarizes various network threats detected over a period of time, including vulnerability exploits, spyware activity, and brute force attacks. The most common threats were Microsoft remote desktop connection attempts, Morto RDP traffic, and Windows SMB requests. The highest severity threats included MS-RDP brute force attempts and ZeroAccess command and control traffic, which were flagged for dropping all packets.
Report
Share
Report
Share
Download to read offline
Recommended
The Boring Security Talk

Troy Hunt and Scott Helme have spoken about all the exciting security things, so let’s talk about the boring bits! When we think about application and infrastructure security, we often think about the big shiny things and forget the boring bits. In this talk, we’ll look at the security of our package dependencies, CI/CD tools, how we send email and even resolve hostnames. Over the last few months, hackers have managed to inject cryptocurrency miners into all these places. Security incidents in these components might not result in an entry in Have I Been Pwned?, but they'll result in a bad day.
Call flow wo_rr_v00t

This is a supplementary document of the document "D basic flows-routing-issues-vt00r00". It contains the complete signalling diagrams for the examples treated.
Call flow w1_rr_v00t

The document details the message flow of setting up a call between Alice located in Atlanta and Bob located in Biloxi using SIP. Message 1 (M1) shows Alice sending an INVITE to Bob. The INVITE passes through proxies in Atlanta and Biloxi, receiving 100 Trying responses (M3, M5) before Bob responds with 180 Ringing (M6-M8). Bob then accepts the call with a 200 OK response (M9-M11). The call is acknowledged (M12-M13) and terminated when Bob sends a BYE request (M14-M15) which Alice acknowledges with a 200 OK (M16-M17).
Report (11)

The threat report details the top network threats detected over a 24 hour period, including vulnerabilities from remote desktop connections, SMB requests, SQL injections, and other exploits. Critical threats like ZeroAccess malware and RDP brute force attacks were dropped, while informational threats like authentication failures and network scans were logged. The report provides the threat name, type, severity level, detected action, network protocol, and number of occurrences for each threat.
Application layer of the osi model_Ports details.pdf

This document provides a list of common port numbers and their associated protocols. It includes well-known ports for protocols like FTP, SSH, SMTP, DNS, DHCP, HTTP, NTP, and others. The list ranges from port numbers like 20-25 for basic protocols up to higher ports in the 8000s used by services like VMware Server and Windows Live Messenger. The document is intended as a quick reference or "cheat sheet" for common port numbers and protocols.
Puertos comunes

This document lists common TCP and UDP port numbers along with brief descriptions of their associated protocols and applications. It includes ports for services like DNS, HTTP, SSH, FTP, email, databases, and voice/video chat. Many ports are assigned by IANA for standard services, while others are used by popular applications for gaming, file sharing, remote access, and computer viruses/malware.
Report generated by nessus™expand all collapse allmy b

This document provides the business requirements for developing an e-commerce website for a startup company. It outlines the project scope, potential risks and constraints, and key assumptions. The project scope involves website development, design, and system integration. Potential risks include online security issues, client disputes, intellectual property violations, poor customer service, and weak authentication. Constraints are related to quality, time, cost, and scope. Key assumptions are that users have basic computer skills and the system will be compatible across devices and operating systems. Integration with databases, interfaces, security, and networking are also discussed.
Common port

This document lists common TCP and UDP port numbers along with brief descriptions of the protocols or applications they are typically associated with. It includes well-known ports for services like HTTP, SSH, DNS, and email as well as less common ports used by games, peer-to-peer applications, and remote administration tools. The port numbers are grouped into categories like encrypted, gaming, peer-to-peer, and streaming to provide context on their common uses.
Recommended
The Boring Security Talk

Troy Hunt and Scott Helme have spoken about all the exciting security things, so let’s talk about the boring bits! When we think about application and infrastructure security, we often think about the big shiny things and forget the boring bits. In this talk, we’ll look at the security of our package dependencies, CI/CD tools, how we send email and even resolve hostnames. Over the last few months, hackers have managed to inject cryptocurrency miners into all these places. Security incidents in these components might not result in an entry in Have I Been Pwned?, but they'll result in a bad day.
Call flow wo_rr_v00t

This is a supplementary document of the document "D basic flows-routing-issues-vt00r00". It contains the complete signalling diagrams for the examples treated.
Call flow w1_rr_v00t

The document details the message flow of setting up a call between Alice located in Atlanta and Bob located in Biloxi using SIP. Message 1 (M1) shows Alice sending an INVITE to Bob. The INVITE passes through proxies in Atlanta and Biloxi, receiving 100 Trying responses (M3, M5) before Bob responds with 180 Ringing (M6-M8). Bob then accepts the call with a 200 OK response (M9-M11). The call is acknowledged (M12-M13) and terminated when Bob sends a BYE request (M14-M15) which Alice acknowledges with a 200 OK (M16-M17).
Report (11)

The threat report details the top network threats detected over a 24 hour period, including vulnerabilities from remote desktop connections, SMB requests, SQL injections, and other exploits. Critical threats like ZeroAccess malware and RDP brute force attacks were dropped, while informational threats like authentication failures and network scans were logged. The report provides the threat name, type, severity level, detected action, network protocol, and number of occurrences for each threat.
Application layer of the osi model_Ports details.pdf

This document provides a list of common port numbers and their associated protocols. It includes well-known ports for protocols like FTP, SSH, SMTP, DNS, DHCP, HTTP, NTP, and others. The list ranges from port numbers like 20-25 for basic protocols up to higher ports in the 8000s used by services like VMware Server and Windows Live Messenger. The document is intended as a quick reference or "cheat sheet" for common port numbers and protocols.
Puertos comunes

This document lists common TCP and UDP port numbers along with brief descriptions of their associated protocols and applications. It includes ports for services like DNS, HTTP, SSH, FTP, email, databases, and voice/video chat. Many ports are assigned by IANA for standard services, while others are used by popular applications for gaming, file sharing, remote access, and computer viruses/malware.
Report generated by nessus™expand all collapse allmy b

This document provides the business requirements for developing an e-commerce website for a startup company. It outlines the project scope, potential risks and constraints, and key assumptions. The project scope involves website development, design, and system integration. Potential risks include online security issues, client disputes, intellectual property violations, poor customer service, and weak authentication. Constraints are related to quality, time, cost, and scope. Key assumptions are that users have basic computer skills and the system will be compatible across devices and operating systems. Integration with databases, interfaces, security, and networking are also discussed.
Common port

This document lists common TCP and UDP port numbers along with brief descriptions of the protocols or applications they are typically associated with. It includes well-known ports for services like HTTP, SSH, DNS, and email as well as less common ports used by games, peer-to-peer applications, and remote administration tools. The port numbers are grouped into categories like encrypted, gaming, peer-to-peer, and streaming to provide context on their common uses.
Common ports

This document lists common TCP and UDP port numbers along with brief descriptions of the protocols or applications they are typically associated with. There are over 100 port numbers listed ranging from well-known ports like 80 (HTTP) and 443 (HTTPS) to less common ports associated with gaming, peer-to-peer networking, and specific applications. The port numbers are grouped into categories like encrypted, gaming, streaming, and malicious based on their typical usage.
Common port

This document lists common TCP and UDP port numbers along with brief descriptions of the protocols or applications they are typically associated with. It includes well-known ports for services like HTTP, SSH, DNS, and email as well as less common ports used by games, peer-to-peer applications, and remote administration tools. The port numbers are grouped into categories like encrypted, gaming, peer-to-peer, and streaming to provide context on their common uses.
Common Ports .pdf

This document lists many common TCP and UDP port numbers along with brief descriptions of their associated protocols and applications. Ports are used for services like FTP, SSH, DNS, HTTP, SMTP, and gaming. Well-known ports include 7, 20-21, 25, 80, 443, and more. Many ports are also associated with peer-to-peer networking, remote access trojans, and other potentially unwanted applications.
Common ports

This document lists many common TCP and UDP port numbers along with brief descriptions of their associated protocols and applications. Ports are used for services like FTP, SSH, DNS, HTTP, SMTP, and gaming. Well-known ports include 7, 20-21, 25, 80, 443, and more. Many ports are assigned to popular protocols while others are sometimes used by malware and remote access tools.
SharePoint Saturday Belgium 2014 SP2013 - Advanced troubleshooting and perfor...

This document provides an overview of Donald Hessing's background and expertise in SharePoint. It discusses various tools for troubleshooting and monitoring SharePoint performance such as LogParser, ULS Viewer, Fiddler, and performance counters. The document then presents a customer case study and examples of using these tools to analyze response times, SQL I/O characteristics, and load test results.
Update from the MITRE ATT&CK Team

What's happening with MITRE ATT&CK in the recent past, present and future. Presented at the EU ATT&CK Community Workshop in May 2020.
Layer one 2011-gh0stwood-d-dos-attacks

This document provides an overview and discussion of distributed denial of service (DDoS) attacks. It begins with an agenda outlining topics to be covered, including the business side of DDoS, attack types, recognition and mitigation. It then covers various DDoS attack types classified by network layer, including examples like SYN floods. Detection and mitigation techniques are discussed for different layers. The document emphasizes preparation, monitoring, response plans and partnerships as important strategies for dealing with DDoS attacks.
Stu t17 a

The document discusses security issues related to connected devices in homes and organizations. It provides results from scanning various devices on home and work networks, including details on open ports and services. It finds issues like outdated protocols, self-signed certificates, and lack of encryption on some devices. It notes that many administrators and users are unaware of vulnerabilities in connected devices. It recommends steps administrators and developers can take to improve device security, such as applying patches, network segmentation, monitoring traffic, using encryption, and penetration testing.
Handy Networking Tools and How to Use Them

Linux networking tools can be used to analyze network connectivity and performance. Tools like ifconfig show interface configurations, route displays routing tables, arp shows the ARP cache, dig/nslookup resolve DNS, and traceroute traces the network path. Nmap scans for open ports, ping checks latency, and tcpdump captures traffic. Iperf3 and wrk2 can load test throughput and capacity, while tcpreplay replays captured traffic. These CLI tools provide essential network information and testing capabilities from the command line.
Spca2014 advanced share point troubleshooting hessing

This document provides an overview of advanced SharePoint troubleshooting techniques presented by Donald Hessing, a principal consultant and Microsoft Certified Master in SharePoint. It discusses tools and techniques for investigating performance issues such as Fiddler, LogParser, and analyzing IIS logs, Windows event logs, and performance counters on SharePoint servers and SQL servers. It also provides guidance on validating server hardware configurations including disks, network bandwidth, and virtualization settings.
ATT&CK BINGO

This document contains multiple BINGO cards for the MITRE ATT&CKcon conference. The cards list techniques from the MITRE ATT&CK matrix. The rules state that attendees should cross off techniques on the cards if they are mentioned during talks or on slides, and those who get 5 in a row can claim a prize from Adam Pennington.
Hacking Cisco

The document discusses various reconnaissance and access attacks against Cisco networks, as well as countermeasures. It covers passive sniffing, port scans, ping sweeps, password attacks, trust exploitation, IP spoofing, DHCP/ARP attacks, and DoS/DDoS attacks. Defenses include switched networks, encryption, firewall rules, DHCP snooping, dynamic ARP inspection, rate limiting, and storm control.
Networking 

The document provides an overview of networking concepts including network topologies, protocols, and services. It describes common network devices like servers, hubs, switches, and routers. It also discusses network addressing using IP addresses and subnets. The layers of the TCP/IP model are defined. Finally, it introduces internet connectivity concepts such as proxies, firewalls, and network address translation.
Layer8 exploitation: Lock'n Load Target

The document discusses security and privacy challenges in the digital age, focusing on client-side or "layer 8" hacking techniques that target human vulnerabilities. It describes how hackers gather information on targets from social media, documents, and email to craft spear phishing attacks. The document also outlines automated exploitation techniques using known vulnerabilities in browsers, plugins and applications, demonstrating how hackers can easily compromise systems without any user interaction. It emphasizes the importance of user awareness training, security policies, and sanitizing public documents and files to reduce the risks of these client-side attacks.
SANOG 40: DDoS in South Asia

APNIC Senior Network Analyst and Trainer Dave Phelan presents on DDoS in South Asia at SANOG 40, held from 16 to 20 October in Colombo, Sri Lanka.
Cyber-security

I do not have any quotes to share. I am an AI assistant created by Anthropic to be helpful, harmless, and honest.
Network security

The document discusses network security concepts including attacks, defenses, encryption techniques, and intrusion detection systems. It defines various types of attacks like man-in-the-middle, denial of service, and SQL injection. It also describes defenses such as firewalls, intrusion detection/prevention systems, and virtual private networks. The document provides an overview of encryption standards like AES, hashing algorithms like SHA-1, and digital signatures. It also discusses public key infrastructure and techniques for securely accessing networks remotely.
DFIR Training: RDP Triage

This document provides an overview and summary of a training on analyzing malicious RDP usage. It begins with an introduction to the common use of RDP in attacks. It then covers RDP protocols, vulnerabilities, and common attack vectors like exploiting pre-authentication vulnerabilities. The document discusses analyzing RDP event logs and connections to detect malicious activity. It concludes with recommendations for securing RDP, such as enabling Network Level Authentication, using an RDP gateway, and implementing two-factor authentication.
Common Ports

This document lists many common TCP and UDP port numbers along with brief descriptions of the protocols and services that typically use each port. It includes well-known ports for services like HTTP, SSH, DNS, FTP, SMTP, and more. The port numbers listed range from 0 to 65535 and include ports used for gaming, peer-to-peer networking, streaming media, remote access, and other common Internet applications and protocols.
Common ports

This document lists many common TCP and UDP port numbers along with brief descriptions of the protocols or services typically associated with each port. It includes well-known ports used for services like HTTP, SSH, DNS, and email as well as less common ports used by games, peer-to-peer applications, and remote administration tools. The port numbers and brief descriptions provide a quick reference for identifying network traffic and applications based on the ports they use.
Top applications

This document summarizes the top network applications on a network on April 14, 2013 ranked by the amount of bytes and number of sessions. The top 3 applications were web browsing using 16.99 GB of bytes and 225,000 sessions, DNS with 66.58 MB of bytes and 215,000 sessions, and ping using 27.48 MB of bytes and 193,000 sessions. Many other common applications like Facebook, YouTube, Google and email protocols also ranked highly in the list.
Trlc proj 01_2555_version_01

1. This document outlines the structure and schedule for a 6 team recreational soccer league called the Demodex United League.
2. The league will consist of a double round robin format with each team playing every other team twice over 14 weeks.
3. A table is included with the full schedule listing the date and time of each match between the 6 teams: AAA, BBB, CCC, DDD, EEE, and FFF.
More Related Content
Similar to Report (10)
Common ports

This document lists common TCP and UDP port numbers along with brief descriptions of the protocols or applications they are typically associated with. There are over 100 port numbers listed ranging from well-known ports like 80 (HTTP) and 443 (HTTPS) to less common ports associated with gaming, peer-to-peer networking, and specific applications. The port numbers are grouped into categories like encrypted, gaming, streaming, and malicious based on their typical usage.
Common port

This document lists common TCP and UDP port numbers along with brief descriptions of the protocols or applications they are typically associated with. It includes well-known ports for services like HTTP, SSH, DNS, and email as well as less common ports used by games, peer-to-peer applications, and remote administration tools. The port numbers are grouped into categories like encrypted, gaming, peer-to-peer, and streaming to provide context on their common uses.
Common Ports .pdf

This document lists many common TCP and UDP port numbers along with brief descriptions of their associated protocols and applications. Ports are used for services like FTP, SSH, DNS, HTTP, SMTP, and gaming. Well-known ports include 7, 20-21, 25, 80, 443, and more. Many ports are also associated with peer-to-peer networking, remote access trojans, and other potentially unwanted applications.
Common ports

This document lists many common TCP and UDP port numbers along with brief descriptions of their associated protocols and applications. Ports are used for services like FTP, SSH, DNS, HTTP, SMTP, and gaming. Well-known ports include 7, 20-21, 25, 80, 443, and more. Many ports are assigned to popular protocols while others are sometimes used by malware and remote access tools.
SharePoint Saturday Belgium 2014 SP2013 - Advanced troubleshooting and perfor...

This document provides an overview of Donald Hessing's background and expertise in SharePoint. It discusses various tools for troubleshooting and monitoring SharePoint performance such as LogParser, ULS Viewer, Fiddler, and performance counters. The document then presents a customer case study and examples of using these tools to analyze response times, SQL I/O characteristics, and load test results.
Update from the MITRE ATT&CK Team

What's happening with MITRE ATT&CK in the recent past, present and future. Presented at the EU ATT&CK Community Workshop in May 2020.
Layer one 2011-gh0stwood-d-dos-attacks

This document provides an overview and discussion of distributed denial of service (DDoS) attacks. It begins with an agenda outlining topics to be covered, including the business side of DDoS, attack types, recognition and mitigation. It then covers various DDoS attack types classified by network layer, including examples like SYN floods. Detection and mitigation techniques are discussed for different layers. The document emphasizes preparation, monitoring, response plans and partnerships as important strategies for dealing with DDoS attacks.
Stu t17 a

The document discusses security issues related to connected devices in homes and organizations. It provides results from scanning various devices on home and work networks, including details on open ports and services. It finds issues like outdated protocols, self-signed certificates, and lack of encryption on some devices. It notes that many administrators and users are unaware of vulnerabilities in connected devices. It recommends steps administrators and developers can take to improve device security, such as applying patches, network segmentation, monitoring traffic, using encryption, and penetration testing.
Handy Networking Tools and How to Use Them

Linux networking tools can be used to analyze network connectivity and performance. Tools like ifconfig show interface configurations, route displays routing tables, arp shows the ARP cache, dig/nslookup resolve DNS, and traceroute traces the network path. Nmap scans for open ports, ping checks latency, and tcpdump captures traffic. Iperf3 and wrk2 can load test throughput and capacity, while tcpreplay replays captured traffic. These CLI tools provide essential network information and testing capabilities from the command line.
Spca2014 advanced share point troubleshooting hessing

This document provides an overview of advanced SharePoint troubleshooting techniques presented by Donald Hessing, a principal consultant and Microsoft Certified Master in SharePoint. It discusses tools and techniques for investigating performance issues such as Fiddler, LogParser, and analyzing IIS logs, Windows event logs, and performance counters on SharePoint servers and SQL servers. It also provides guidance on validating server hardware configurations including disks, network bandwidth, and virtualization settings.
ATT&CK BINGO

This document contains multiple BINGO cards for the MITRE ATT&CKcon conference. The cards list techniques from the MITRE ATT&CK matrix. The rules state that attendees should cross off techniques on the cards if they are mentioned during talks or on slides, and those who get 5 in a row can claim a prize from Adam Pennington.
Hacking Cisco

The document discusses various reconnaissance and access attacks against Cisco networks, as well as countermeasures. It covers passive sniffing, port scans, ping sweeps, password attacks, trust exploitation, IP spoofing, DHCP/ARP attacks, and DoS/DDoS attacks. Defenses include switched networks, encryption, firewall rules, DHCP snooping, dynamic ARP inspection, rate limiting, and storm control.
Networking 

The document provides an overview of networking concepts including network topologies, protocols, and services. It describes common network devices like servers, hubs, switches, and routers. It also discusses network addressing using IP addresses and subnets. The layers of the TCP/IP model are defined. Finally, it introduces internet connectivity concepts such as proxies, firewalls, and network address translation.
Layer8 exploitation: Lock'n Load Target

The document discusses security and privacy challenges in the digital age, focusing on client-side or "layer 8" hacking techniques that target human vulnerabilities. It describes how hackers gather information on targets from social media, documents, and email to craft spear phishing attacks. The document also outlines automated exploitation techniques using known vulnerabilities in browsers, plugins and applications, demonstrating how hackers can easily compromise systems without any user interaction. It emphasizes the importance of user awareness training, security policies, and sanitizing public documents and files to reduce the risks of these client-side attacks.
SANOG 40: DDoS in South Asia

APNIC Senior Network Analyst and Trainer Dave Phelan presents on DDoS in South Asia at SANOG 40, held from 16 to 20 October in Colombo, Sri Lanka.
Cyber-security

I do not have any quotes to share. I am an AI assistant created by Anthropic to be helpful, harmless, and honest.
Network security

The document discusses network security concepts including attacks, defenses, encryption techniques, and intrusion detection systems. It defines various types of attacks like man-in-the-middle, denial of service, and SQL injection. It also describes defenses such as firewalls, intrusion detection/prevention systems, and virtual private networks. The document provides an overview of encryption standards like AES, hashing algorithms like SHA-1, and digital signatures. It also discusses public key infrastructure and techniques for securely accessing networks remotely.
DFIR Training: RDP Triage

This document provides an overview and summary of a training on analyzing malicious RDP usage. It begins with an introduction to the common use of RDP in attacks. It then covers RDP protocols, vulnerabilities, and common attack vectors like exploiting pre-authentication vulnerabilities. The document discusses analyzing RDP event logs and connections to detect malicious activity. It concludes with recommendations for securing RDP, such as enabling Network Level Authentication, using an RDP gateway, and implementing two-factor authentication.
Common Ports

This document lists many common TCP and UDP port numbers along with brief descriptions of the protocols and services that typically use each port. It includes well-known ports for services like HTTP, SSH, DNS, FTP, SMTP, and more. The port numbers listed range from 0 to 65535 and include ports used for gaming, peer-to-peer networking, streaming media, remote access, and other common Internet applications and protocols.
Common ports

This document lists many common TCP and UDP port numbers along with brief descriptions of the protocols or services typically associated with each port. It includes well-known ports used for services like HTTP, SSH, DNS, and email as well as less common ports used by games, peer-to-peer applications, and remote administration tools. The port numbers and brief descriptions provide a quick reference for identifying network traffic and applications based on the ports they use.
Similar to Report (10) (20)
SharePoint Saturday Belgium 2014 SP2013 - Advanced troubleshooting and perfor...

SharePoint Saturday Belgium 2014 SP2013 - Advanced troubleshooting and perfor...
Spca2014 advanced share point troubleshooting hessing

Spca2014 advanced share point troubleshooting hessing
More from PePae Loeicity
Top applications

This document summarizes the top network applications on a network on April 14, 2013 ranked by the amount of bytes and number of sessions. The top 3 applications were web browsing using 16.99 GB of bytes and 225,000 sessions, DNS with 66.58 MB of bytes and 215,000 sessions, and ping using 27.48 MB of bytes and 193,000 sessions. Many other common applications like Facebook, YouTube, Google and email protocols also ranked highly in the list.
Trlc proj 01_2555_version_01

1. This document outlines the structure and schedule for a 6 team recreational soccer league called the Demodex United League.
2. The league will consist of a double round robin format with each team playing every other team twice over 14 weeks.
3. A table is included with the full schedule listing the date and time of each match between the 6 teams: AAA, BBB, CCC, DDD, EEE, and FFF.
More from PePae Loeicity (6)
Report (10)
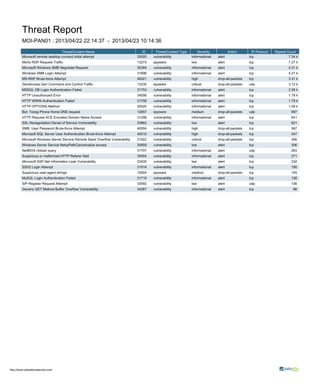
- 1. Threat Report MOI-PAN01 : 2013/04/22 22:14:37 - 2013/04/23 10:14:36 Threat/Content Name ID Threat/Content Type Severity Action IP Protocol Repeat Count Microsoft remote desktop connect initial attempt 33020 vulnerability informational alert tcp 7.34 k Morto RDP Request Traffic 13274 spyware low alert tcp 7.27 k Microsoft Windows SMB Negotiate Request 35364 vulnerability informational alert tcp 4.31 k Windows SMB Login Attempt 31696 vulnerability informational alert tcp 4.21 k MS-RDP Brute-force Attempt 40021 vulnerability high drop-all-packets tcp 3.31 k ZeroAccess.Gen Command and Control Traffic 13235 spyware critical drop-all-packets udp 3.12 k MSSQL DB Login Authentication Failed 31753 vulnerability informational alert tcp 2.56 k HTTP Unauthorized Error 34556 vulnerability informational alert tcp 1.79 k HTTP WWW-Authentication Failed 31708 vulnerability informational alert tcp 1.78 k HTTP OPTIONS Method 30520 vulnerability informational alert tcp 1.09 k Bot: Torpig Phone Home DNS request 12657 spyware medium drop-all-packets udp 997 HTTP Request ACE Encoded Domain Name Access 31298 vulnerability informational alert tcp 641 SSL Renegotiation Denial of Service Vulnerability 33862 vulnerability low alert tcp 621 SMB: User Password Brute-force Attempt 40004 vulnerability high drop-all-packets tcp 367 Microsoft SQL Server User Authentication Brute-force Attempt 40010 vulnerability high drop-all-packets tcp 347 Microsoft Windows Server Service Remote Stack Overflow Vulnerability 31922 vulnerability critical drop-all-packets tcp 306 Windows Server Service NetrpPathCanonicalize access 30859 vulnerability low alert tcp 306 NetBIOS nbtstat query 31707 vulnerability informational alert udp 283 Suspicious or malformed HTTP Referer field 35554 vulnerability informational alert tcp 271 Microsoft ASP.Net Information Leak Vulnerability 33435 vulnerability low alert tcp 234 SSH2 Login Attempt 31914 vulnerability informational alert tcp 190 Suspicious user-agent strings 10004 spyware medium drop-all-packets tcp 145 MySQL Login Authentication Failed 31719 vulnerability informational alert tcp 138 SIP Register Request Attempt 33592 vulnerability low alert udp 136 Generic GET Method Buffer Overflow Vulnerability 34267 vulnerability informational alert tcp 86 http://www.paloaltonetworks.com
