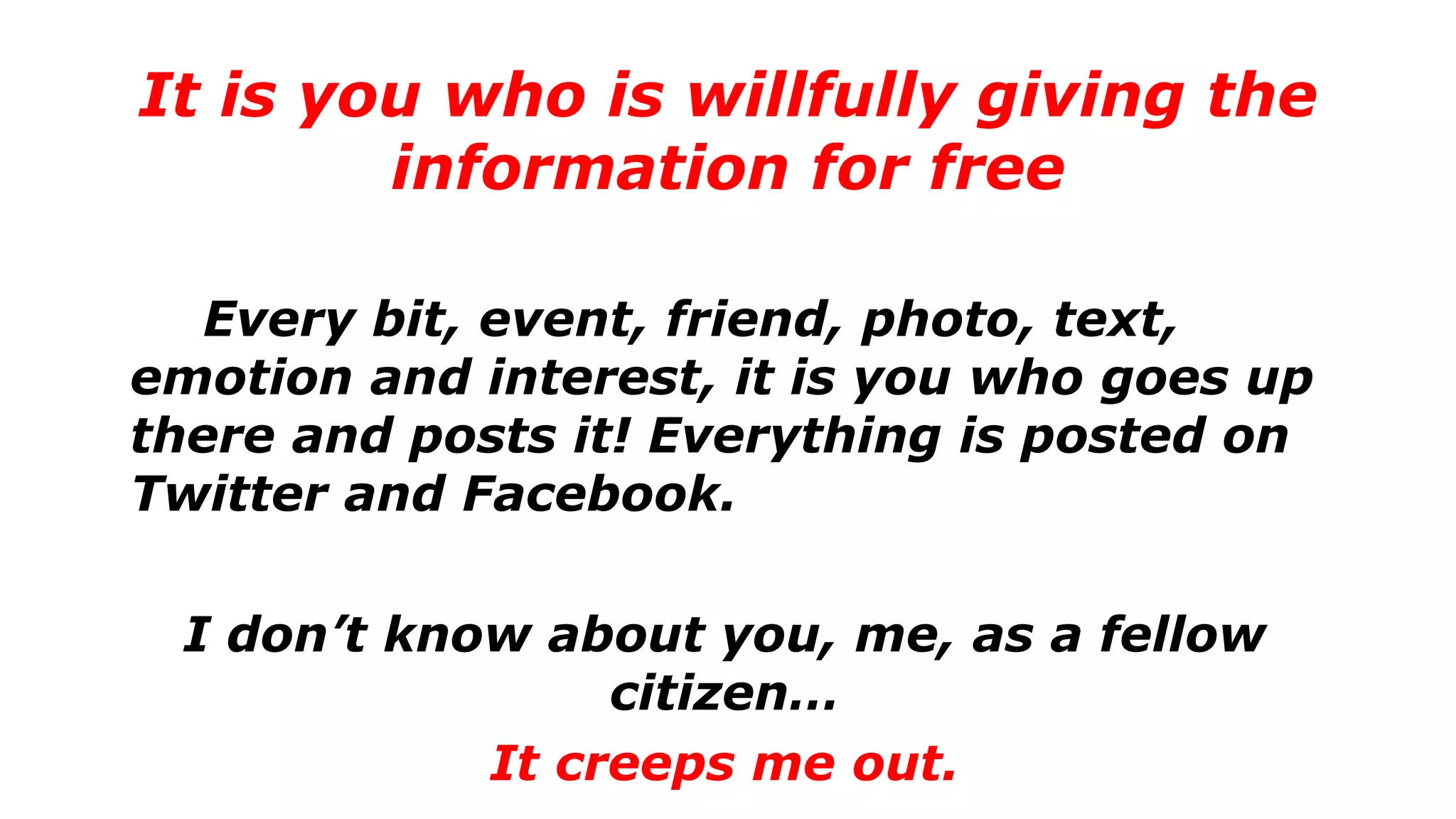
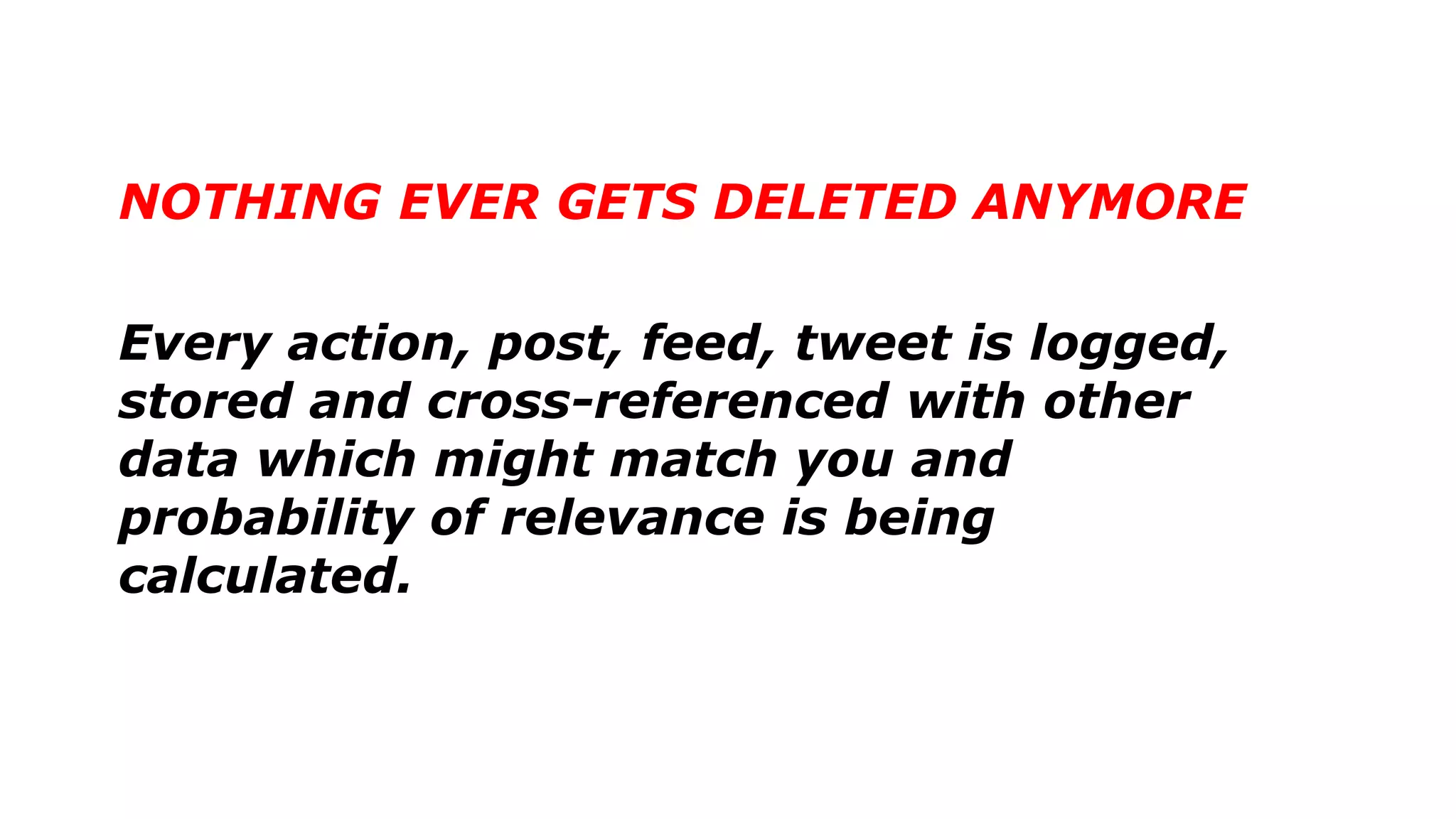
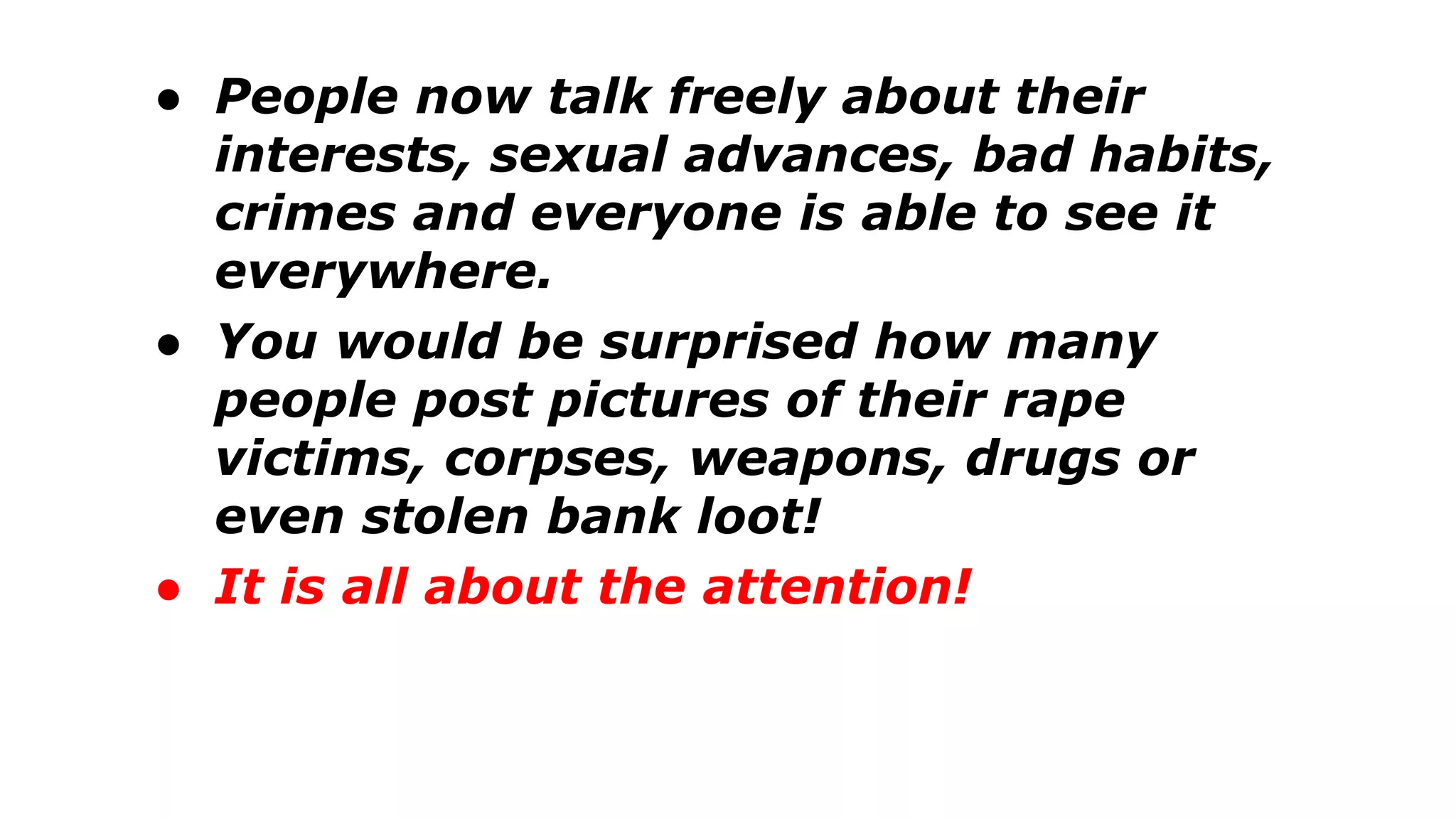
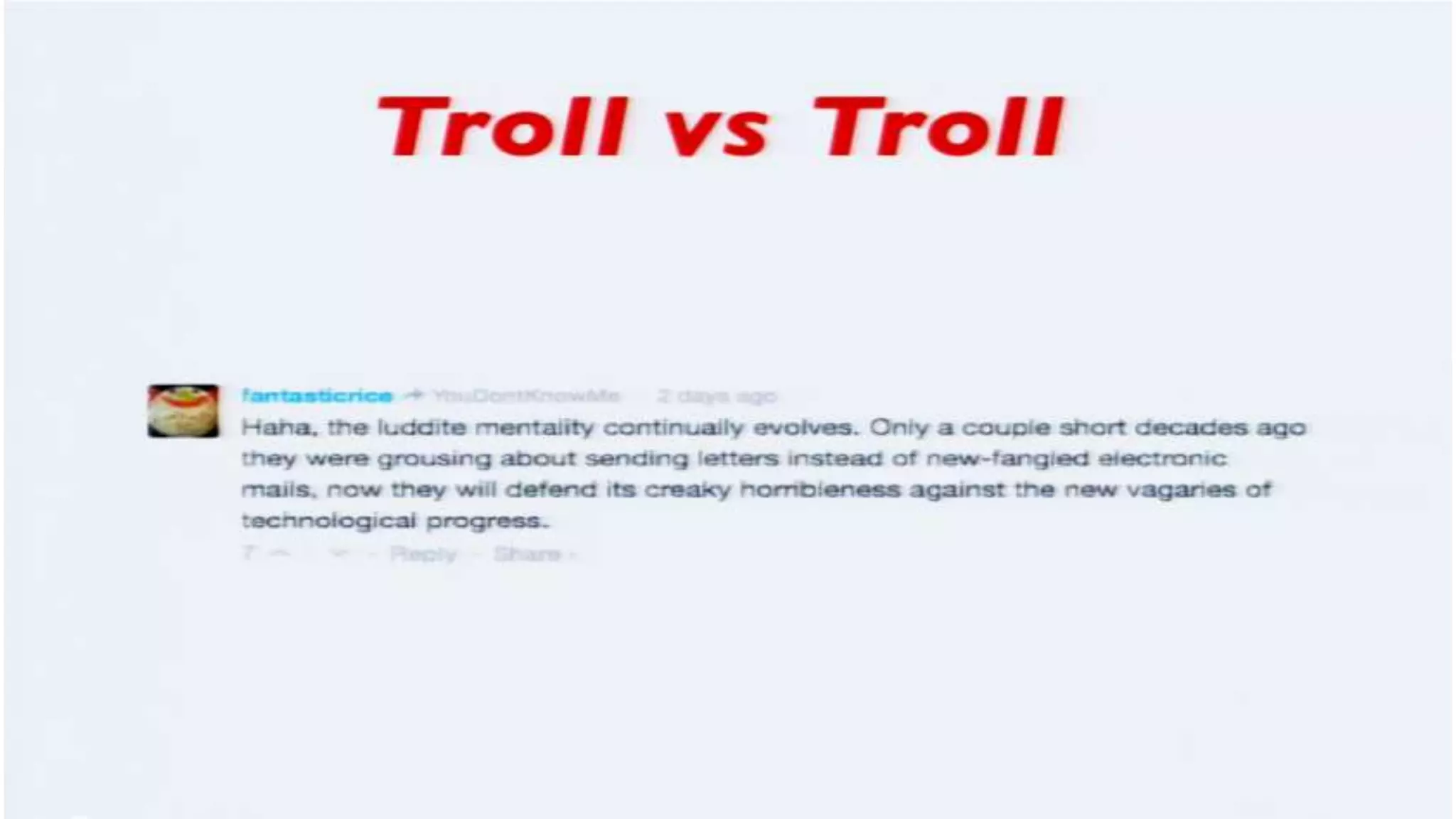
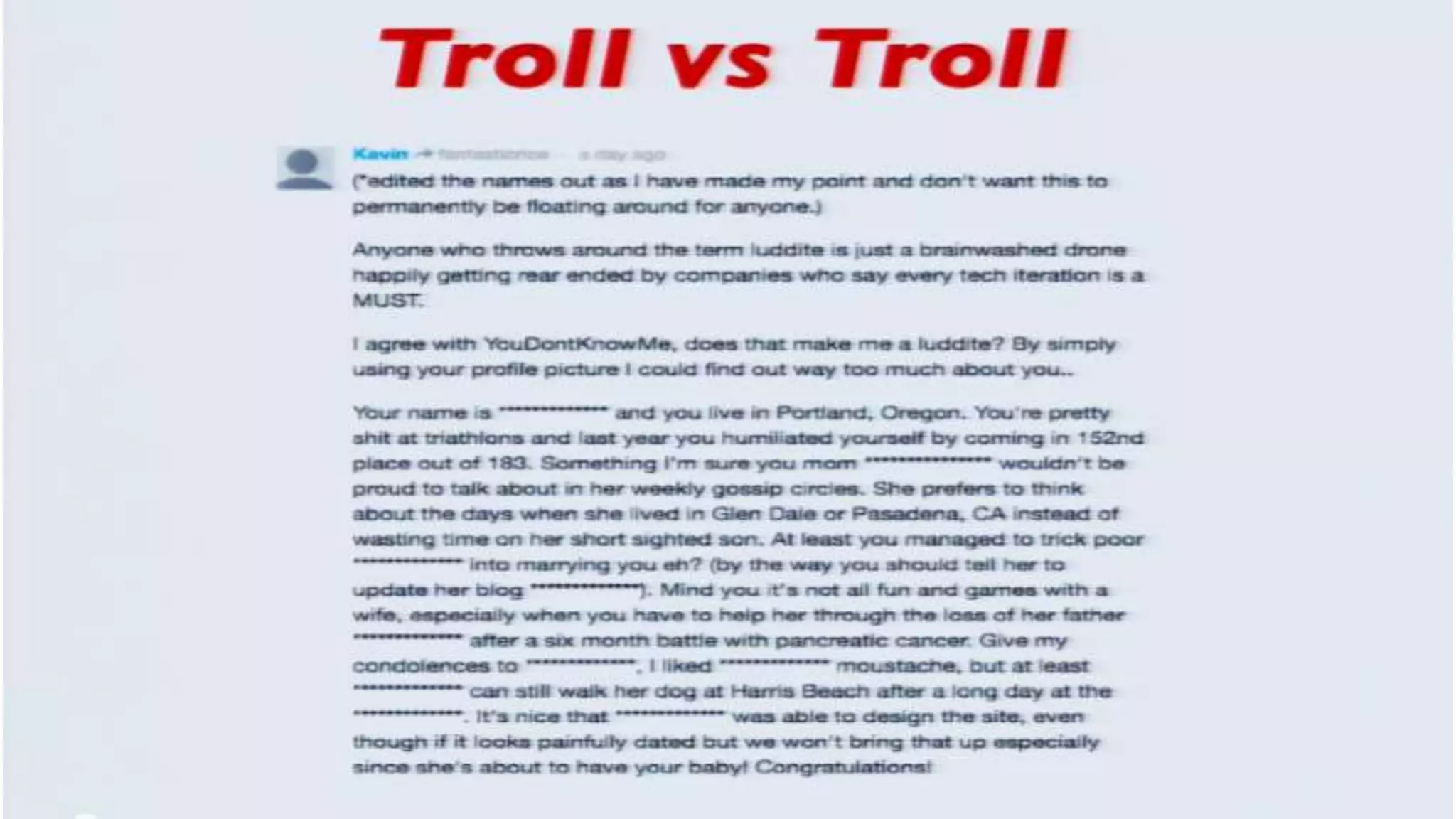
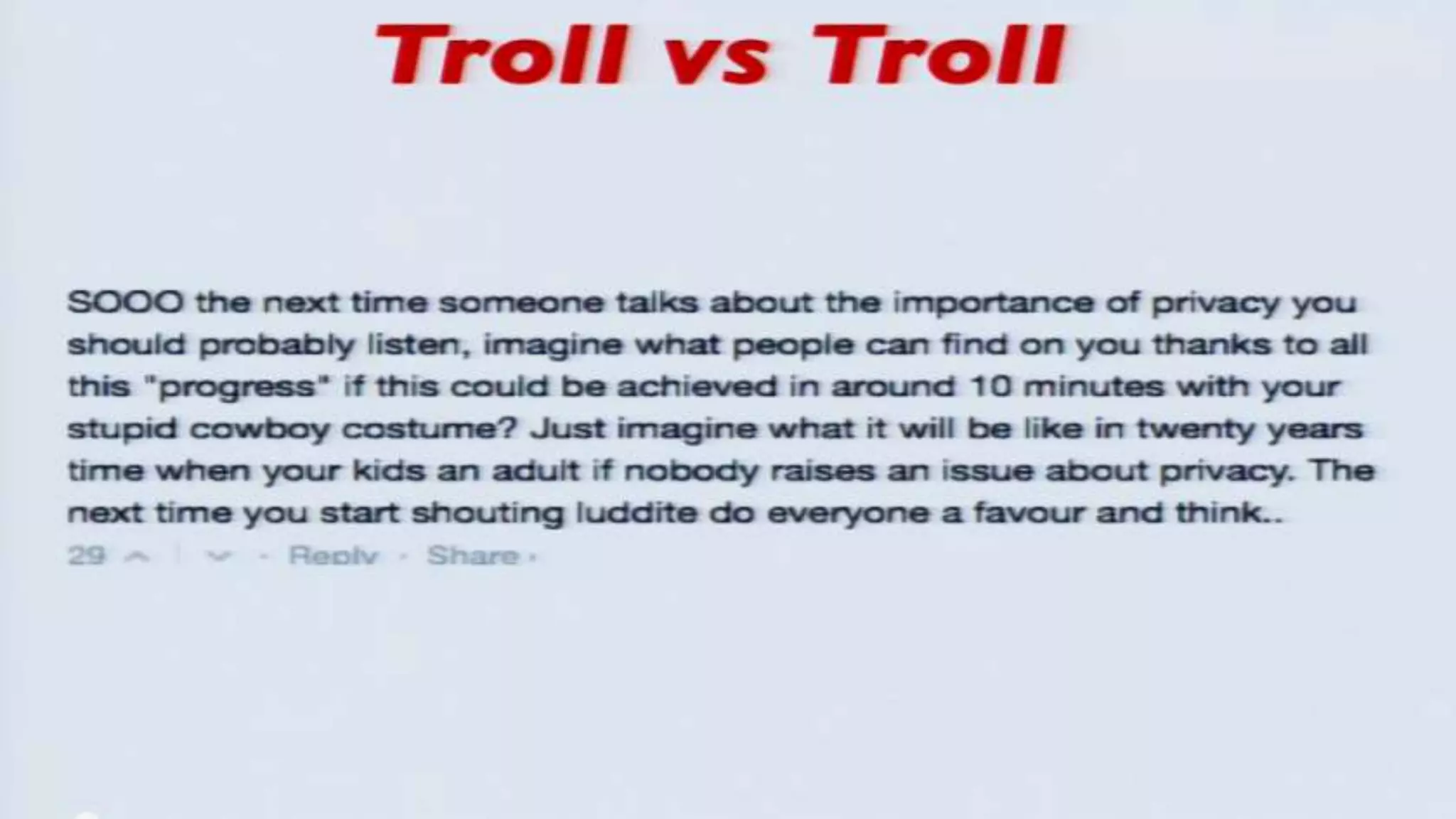
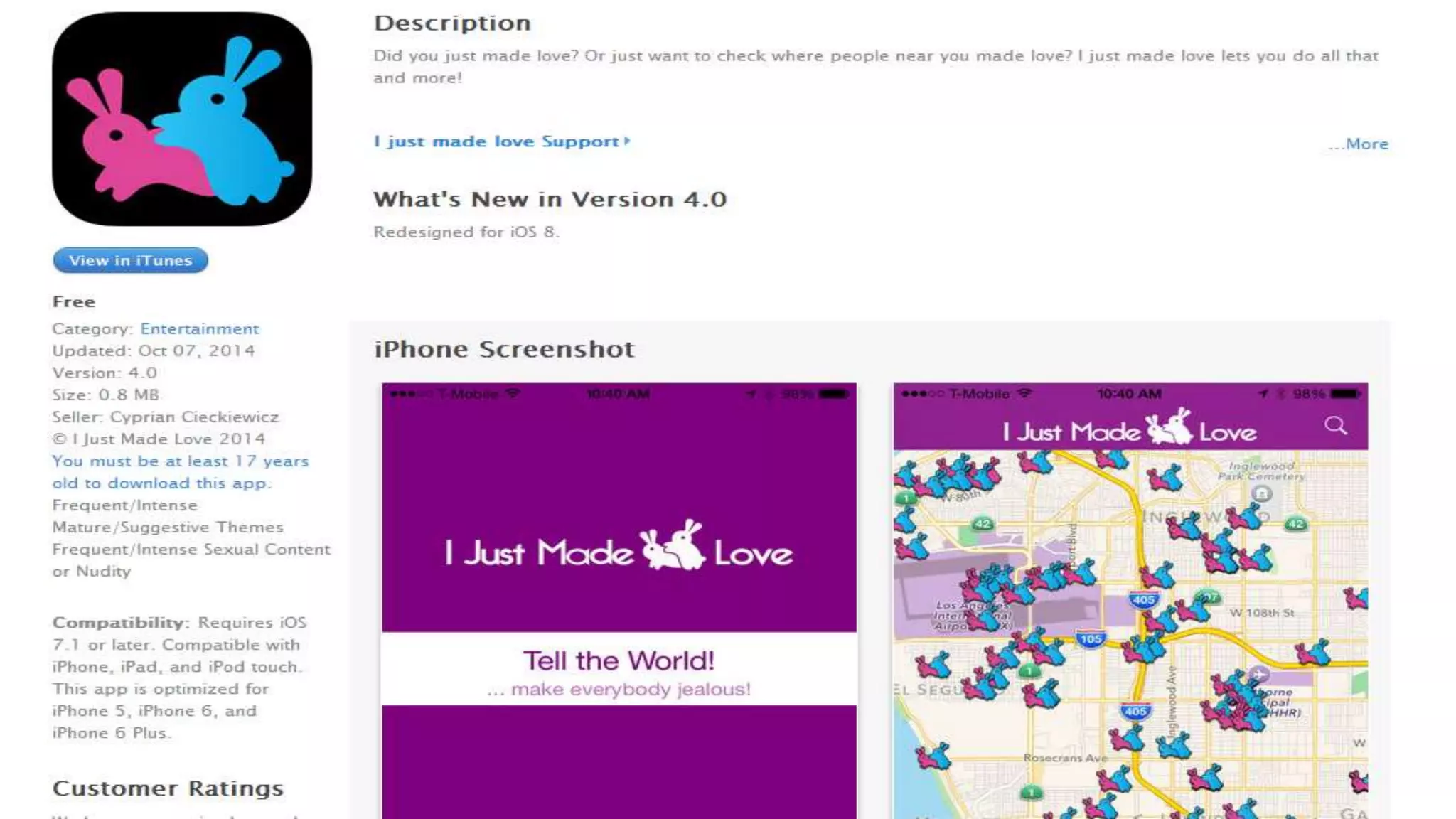
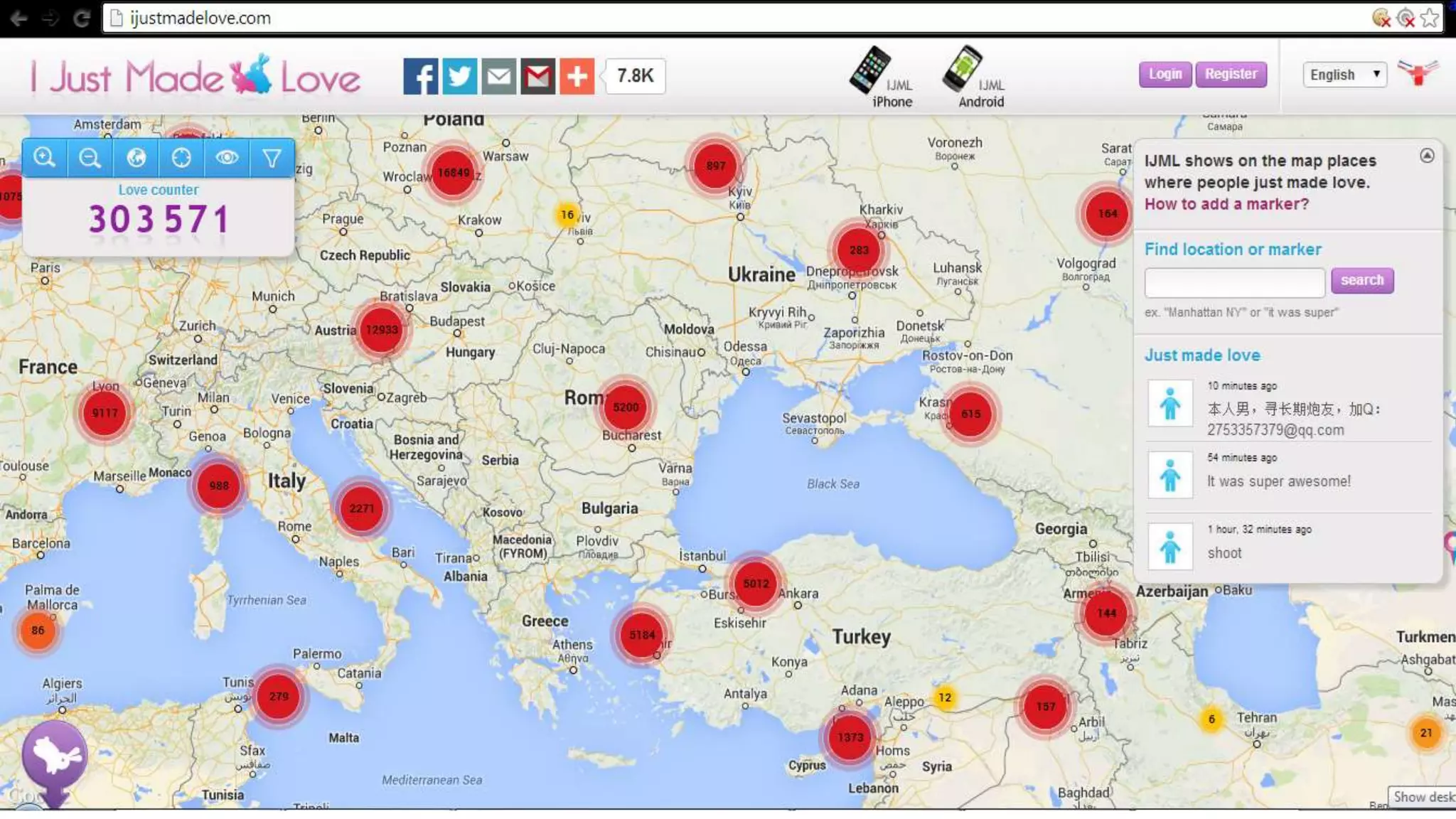
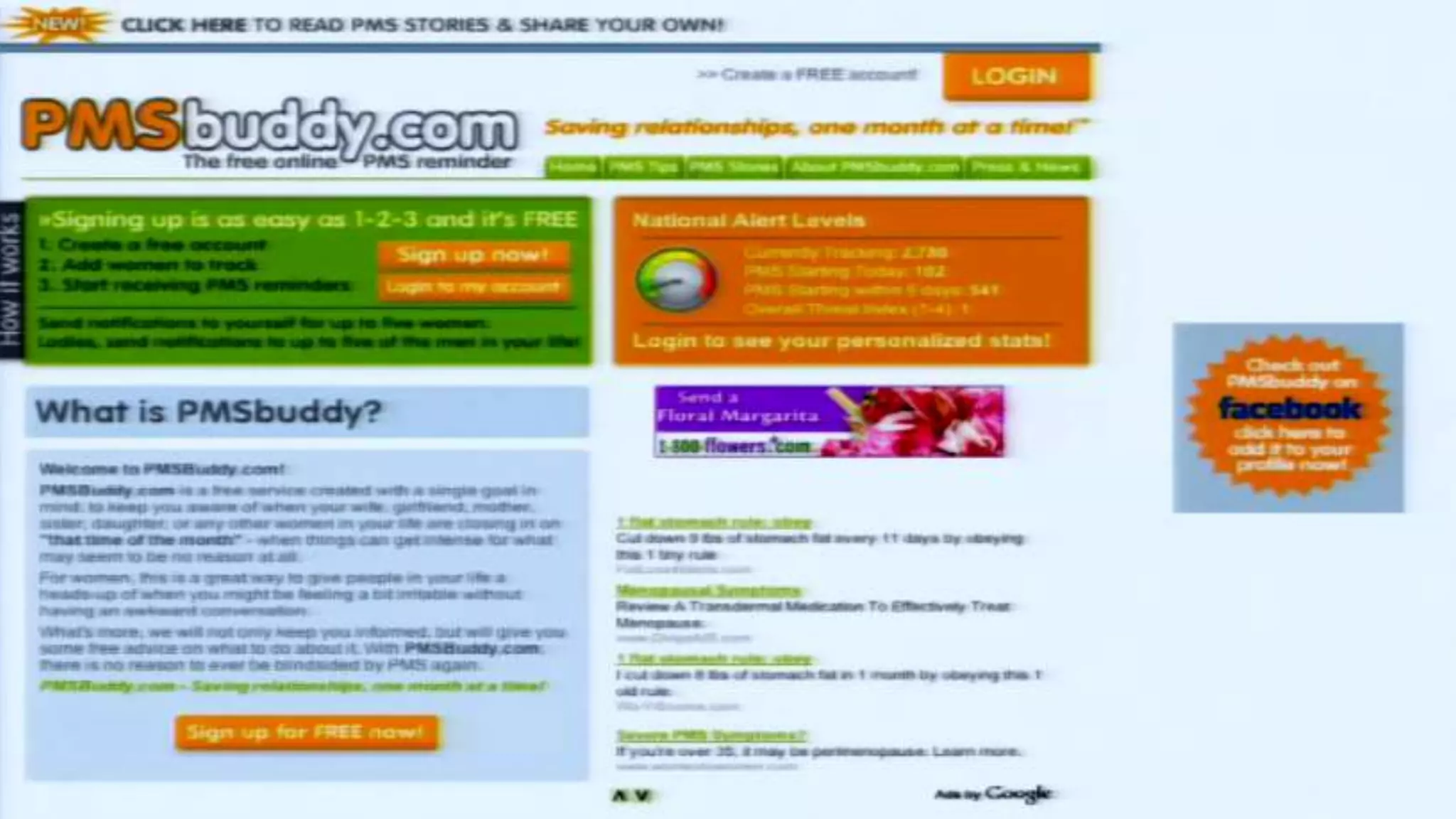
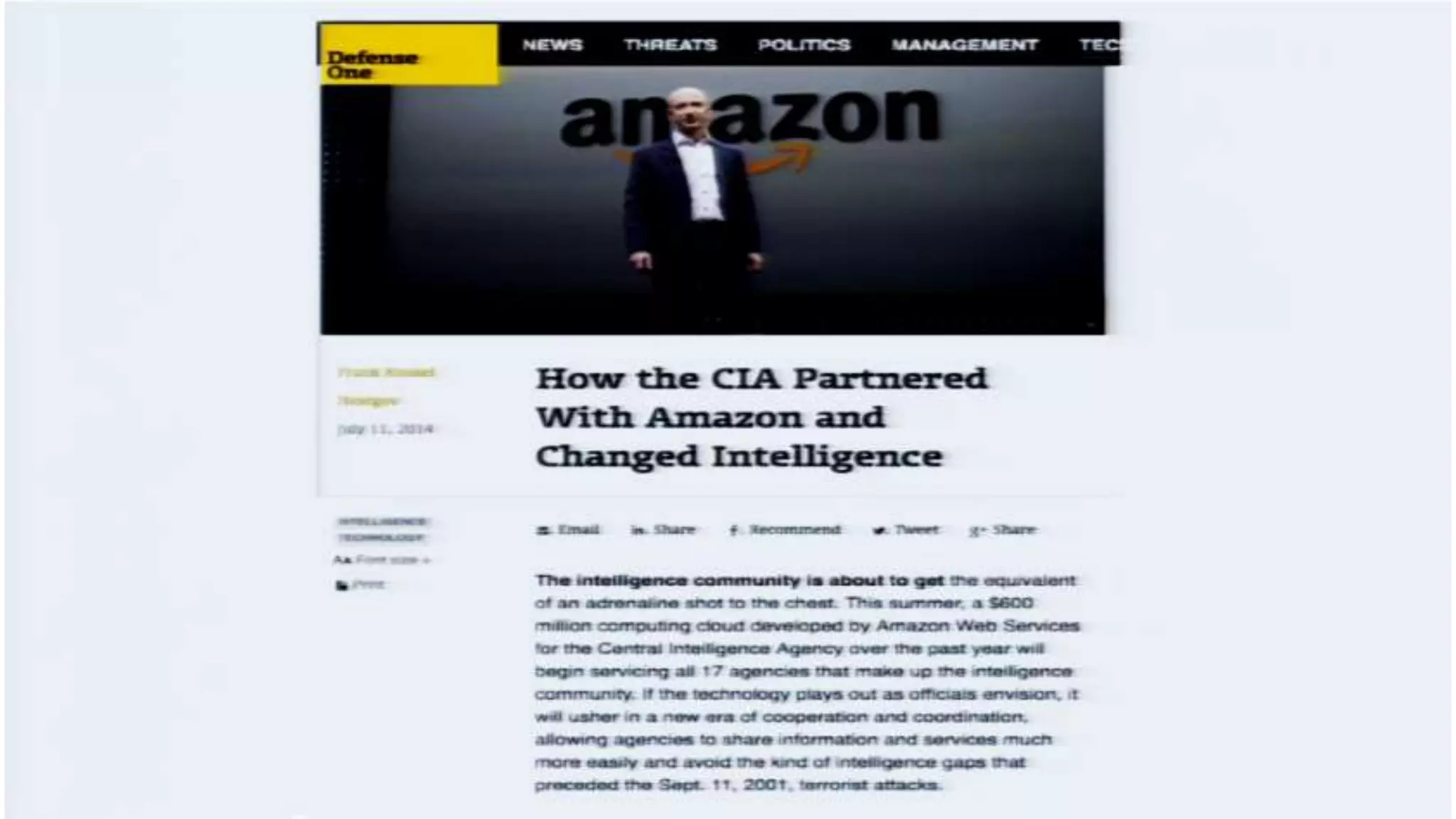
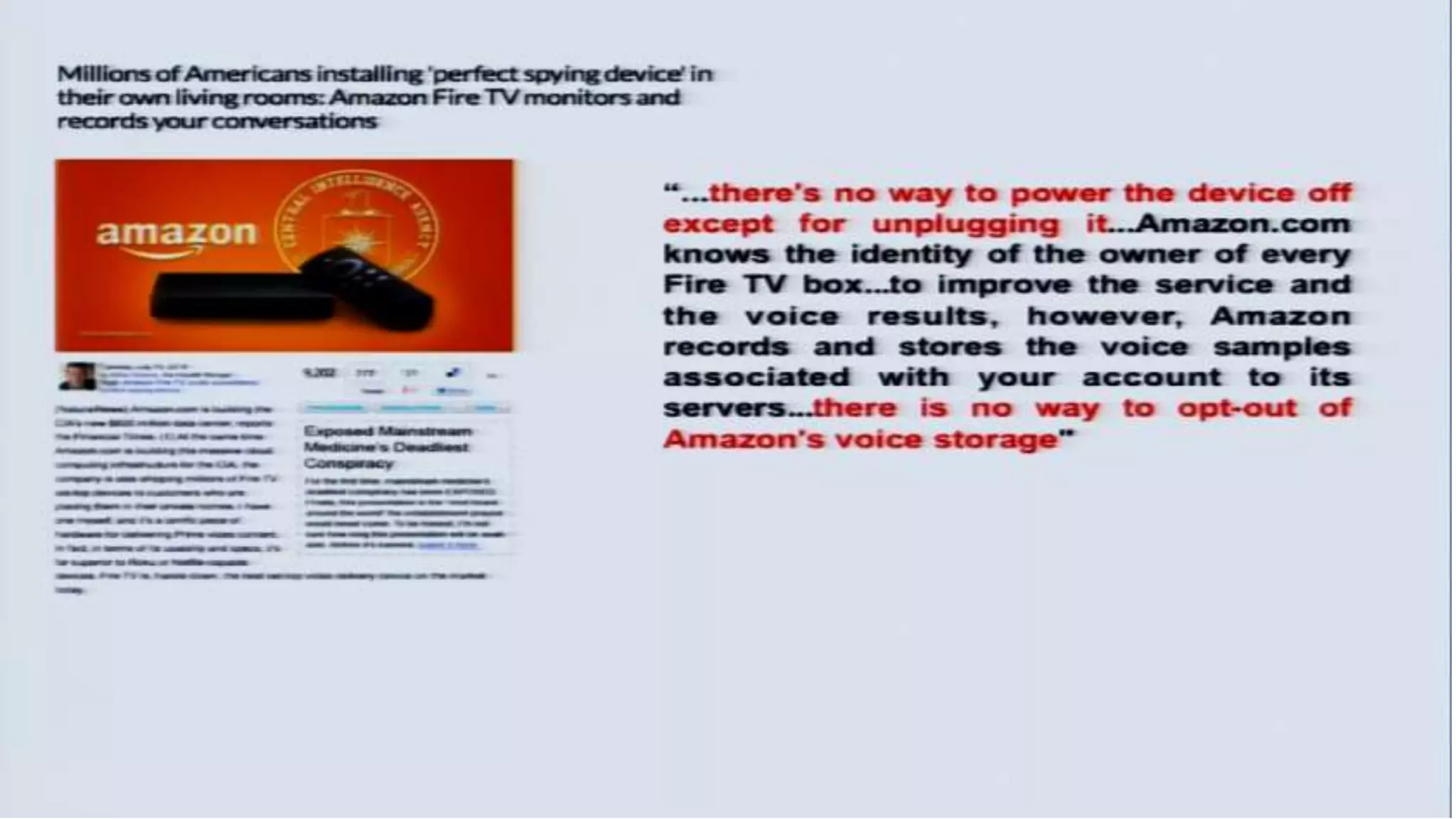
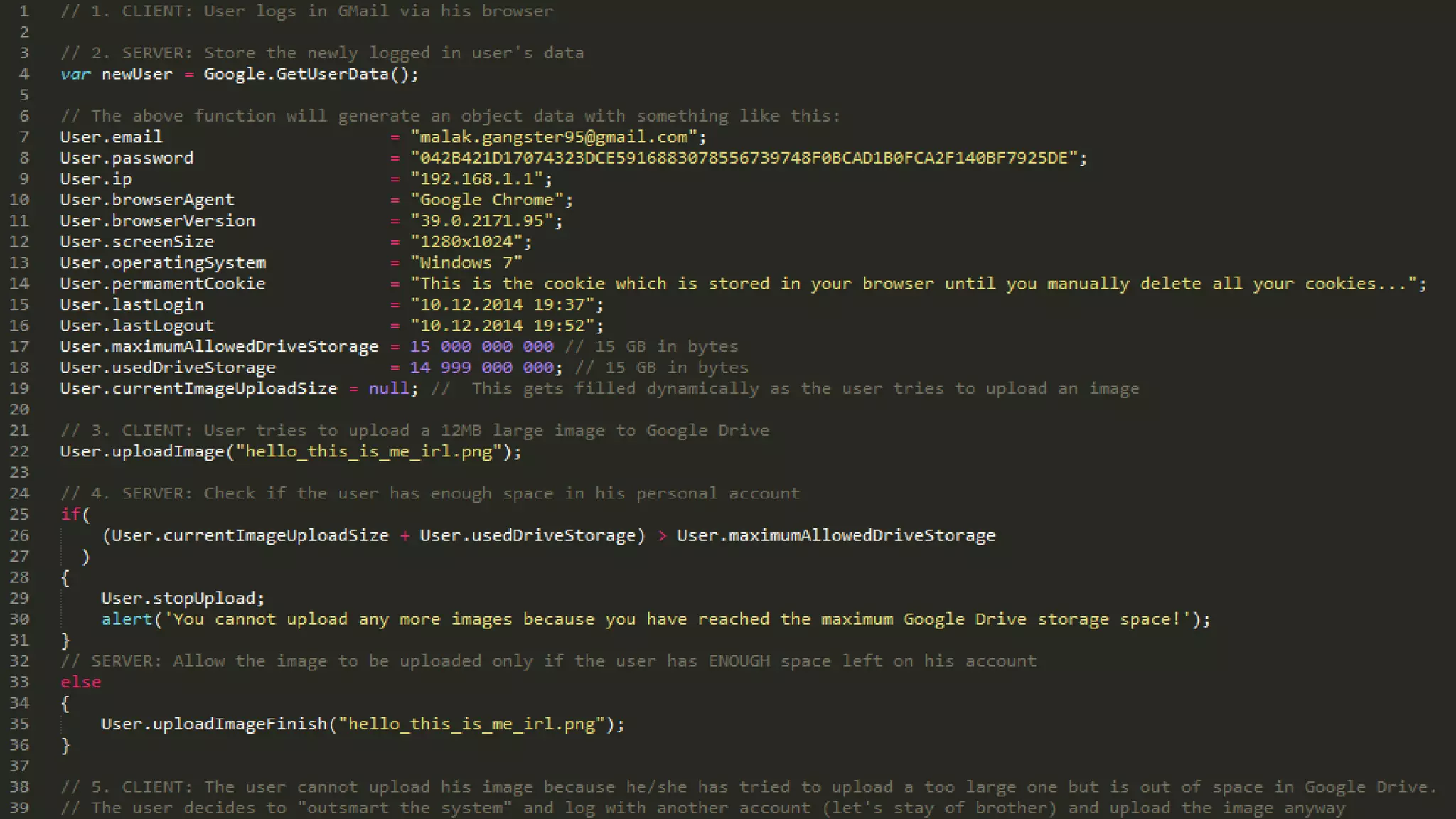
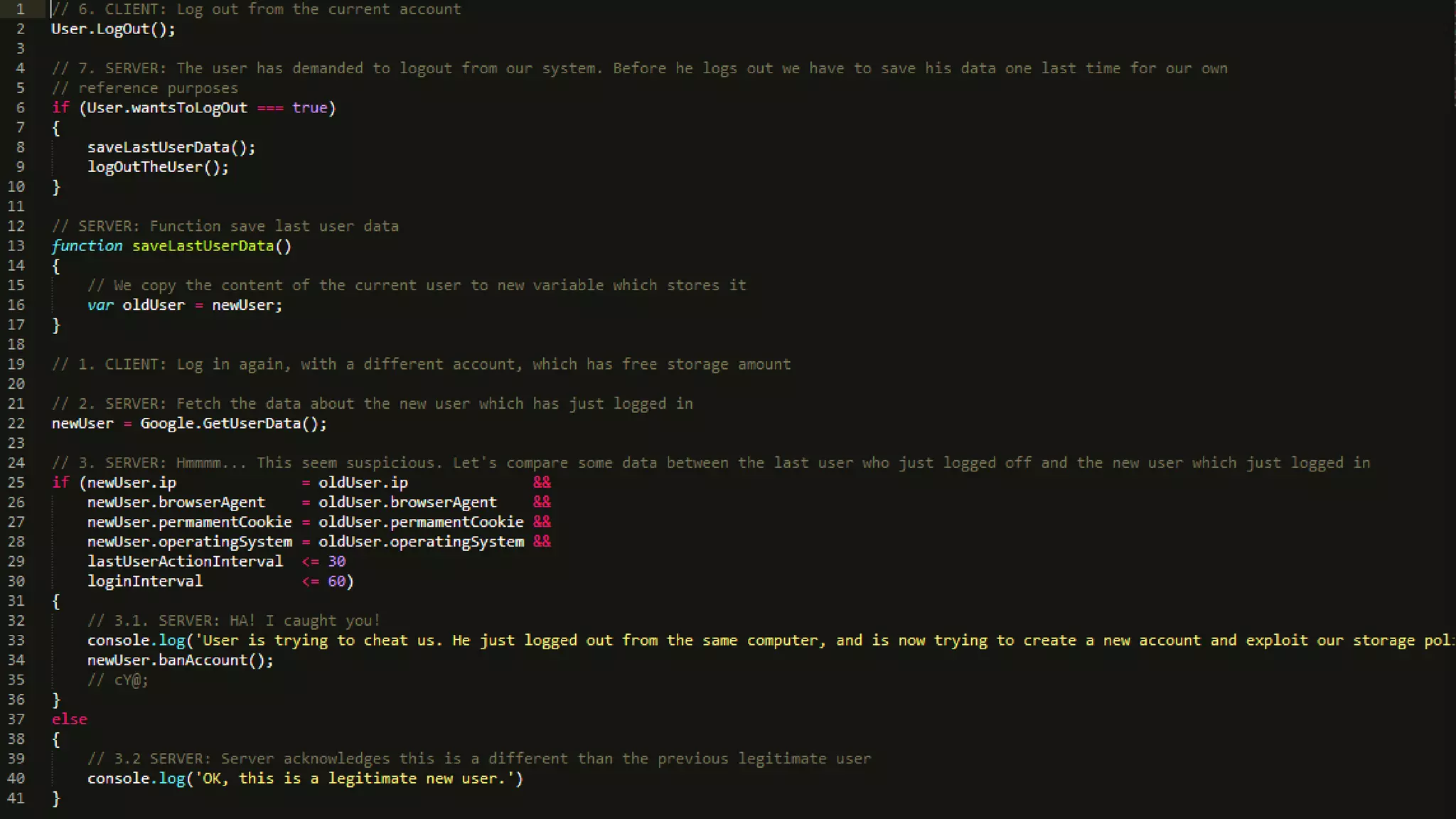
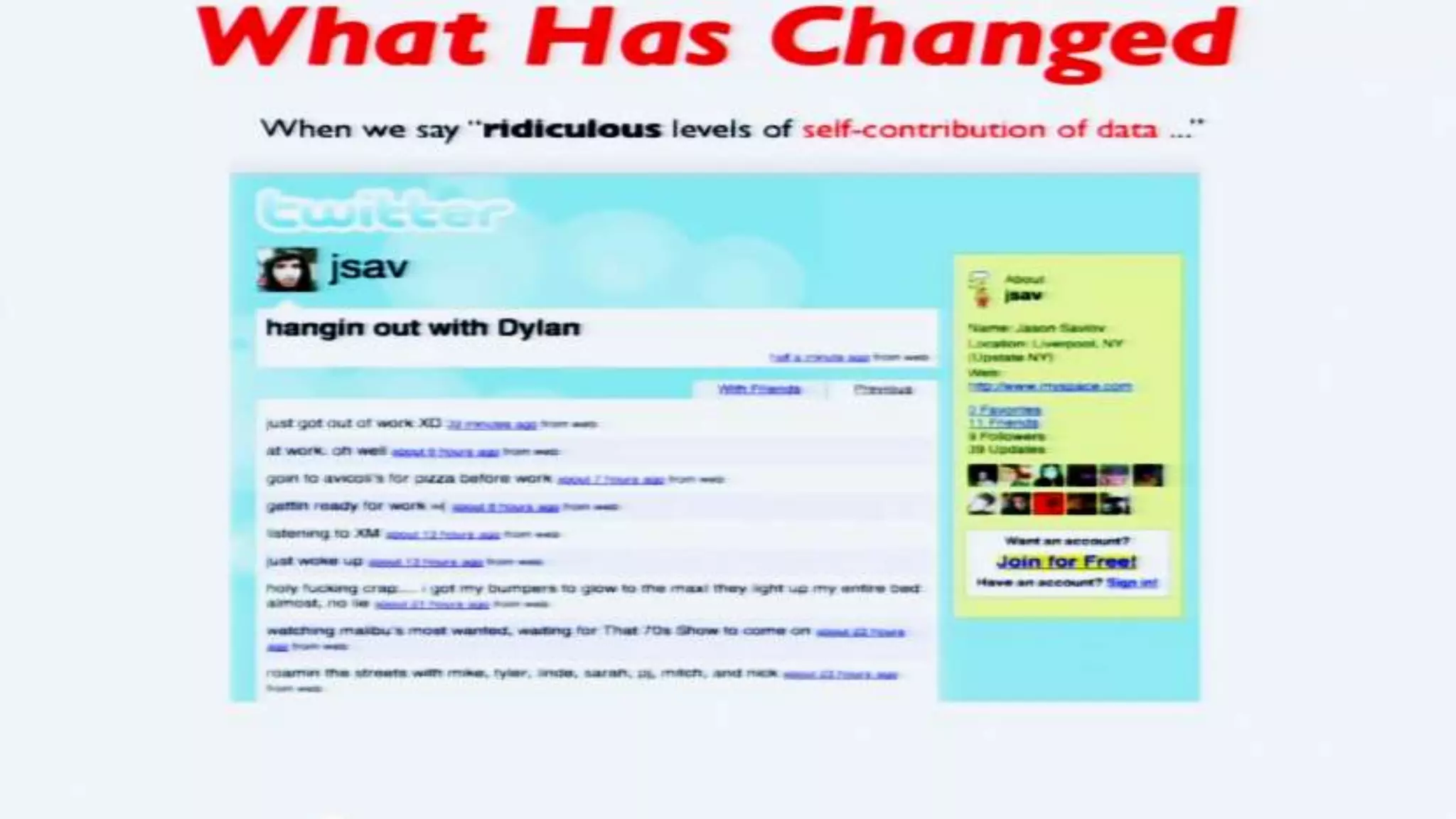
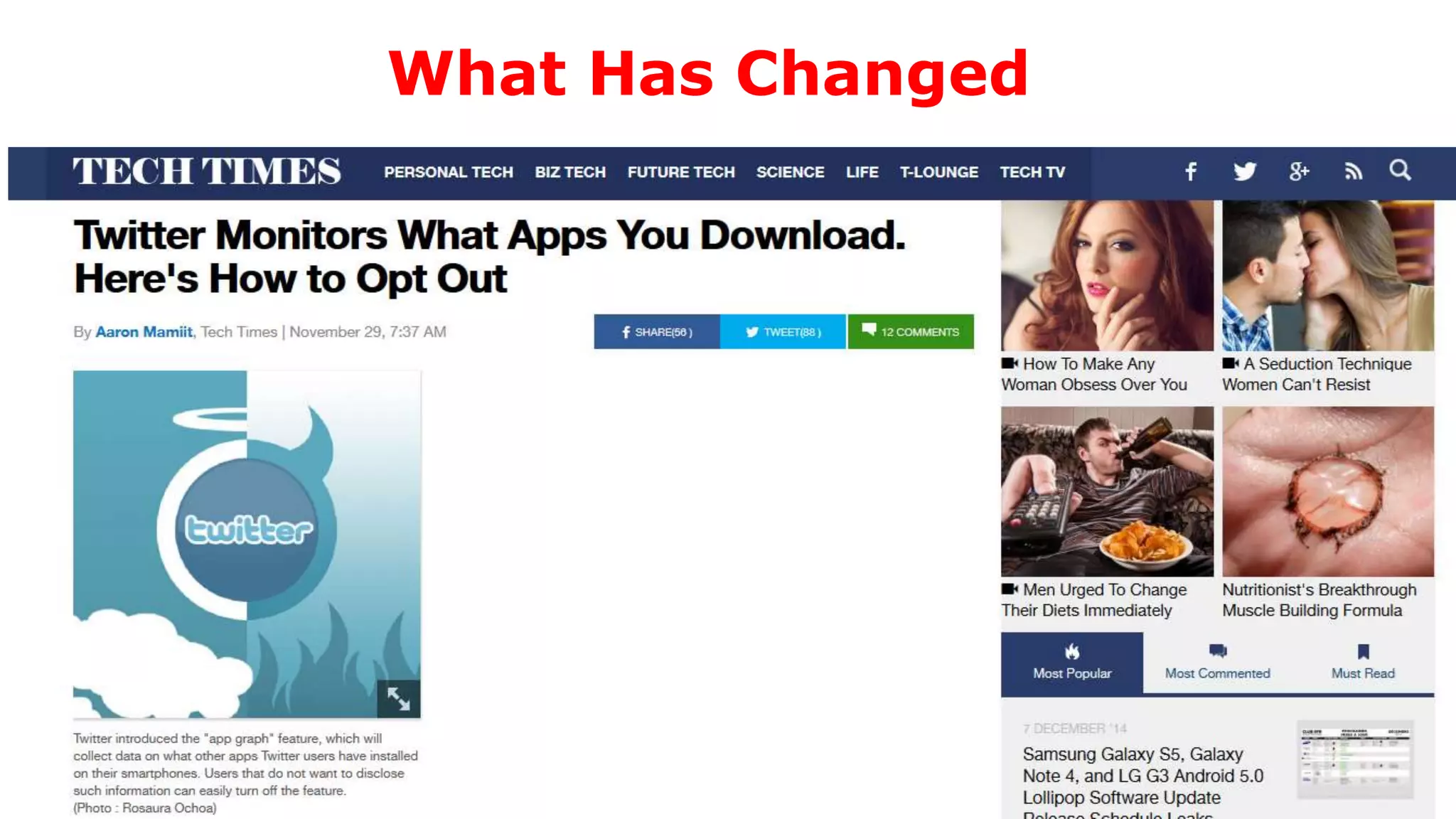
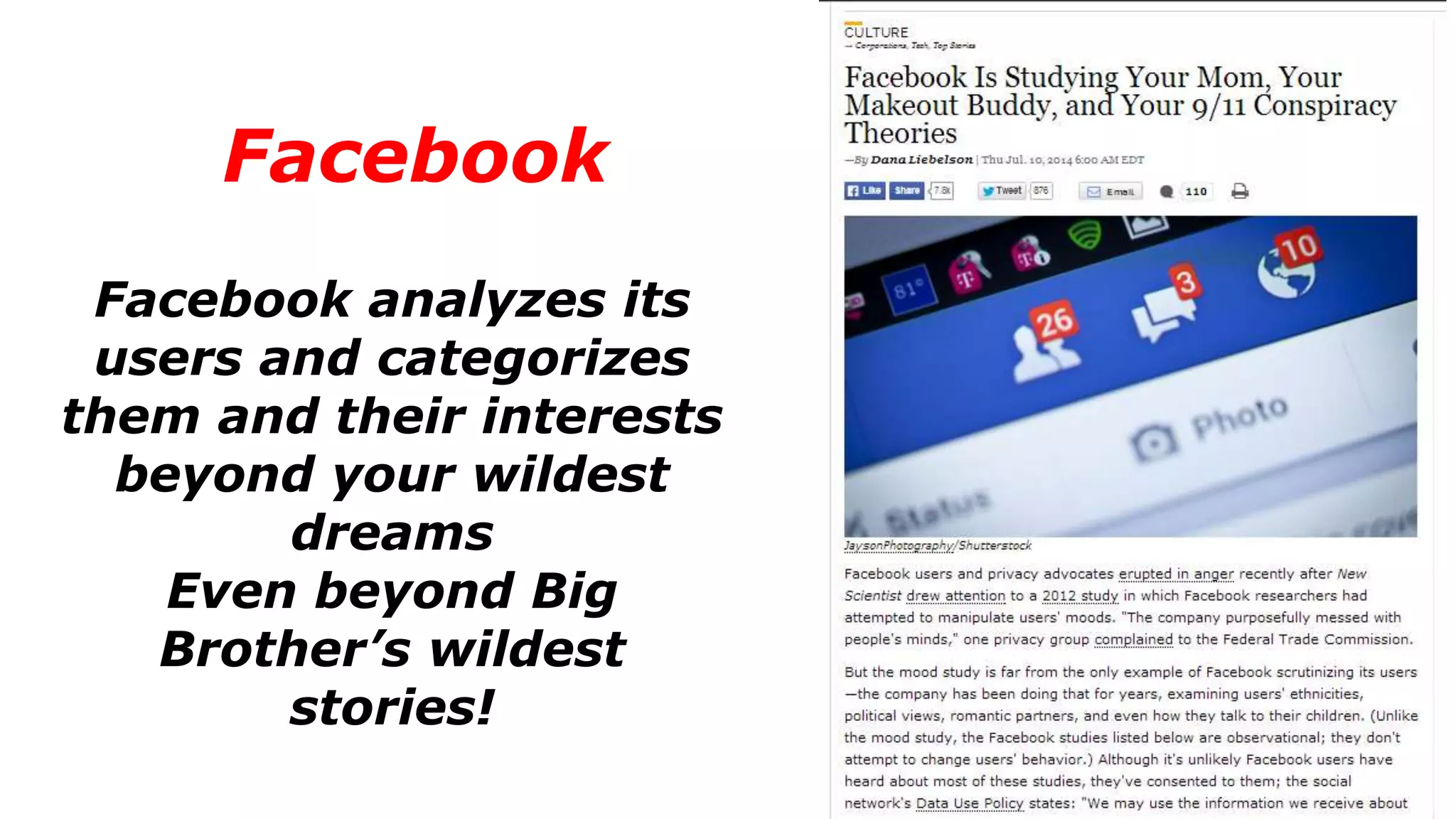
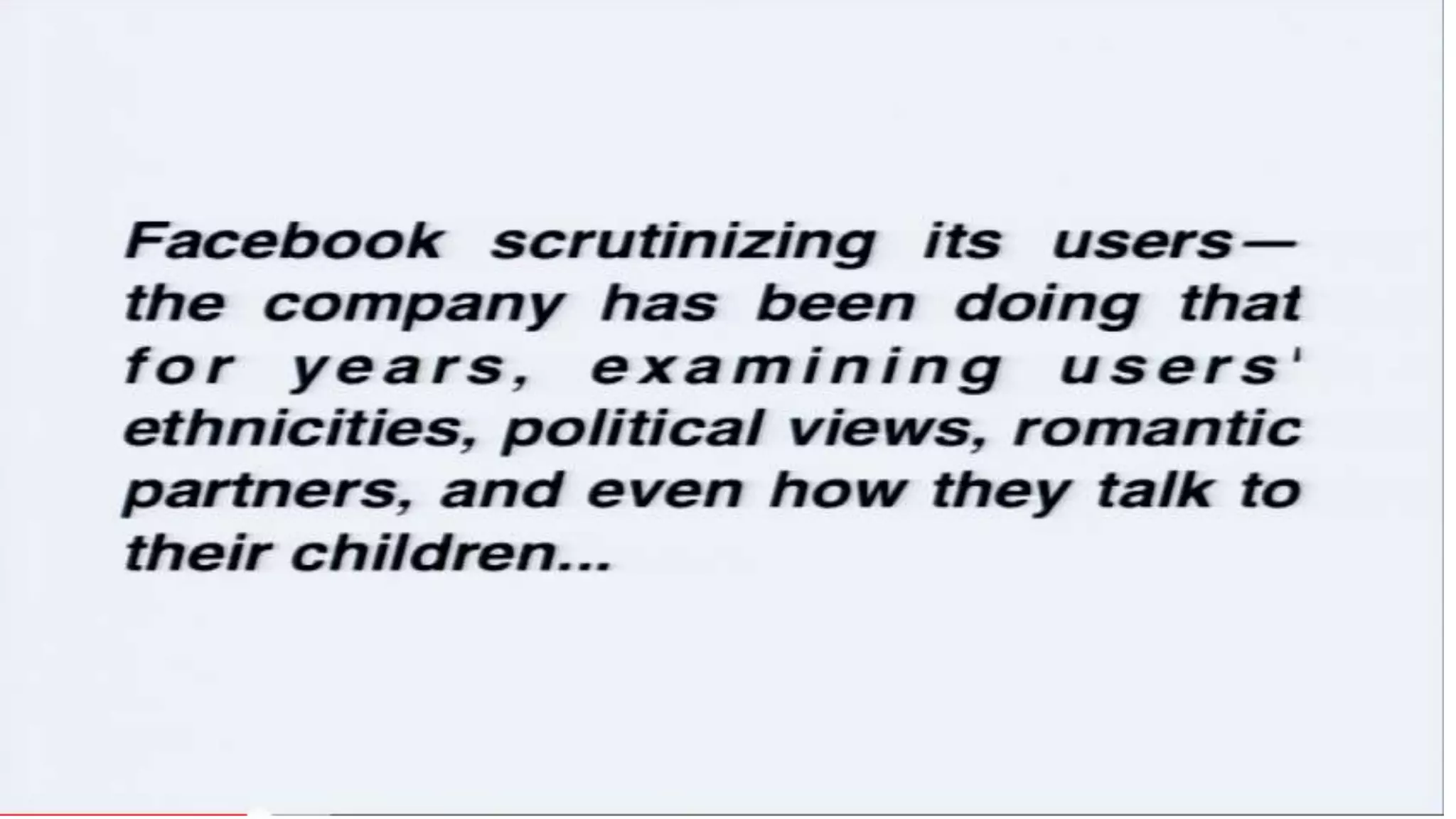
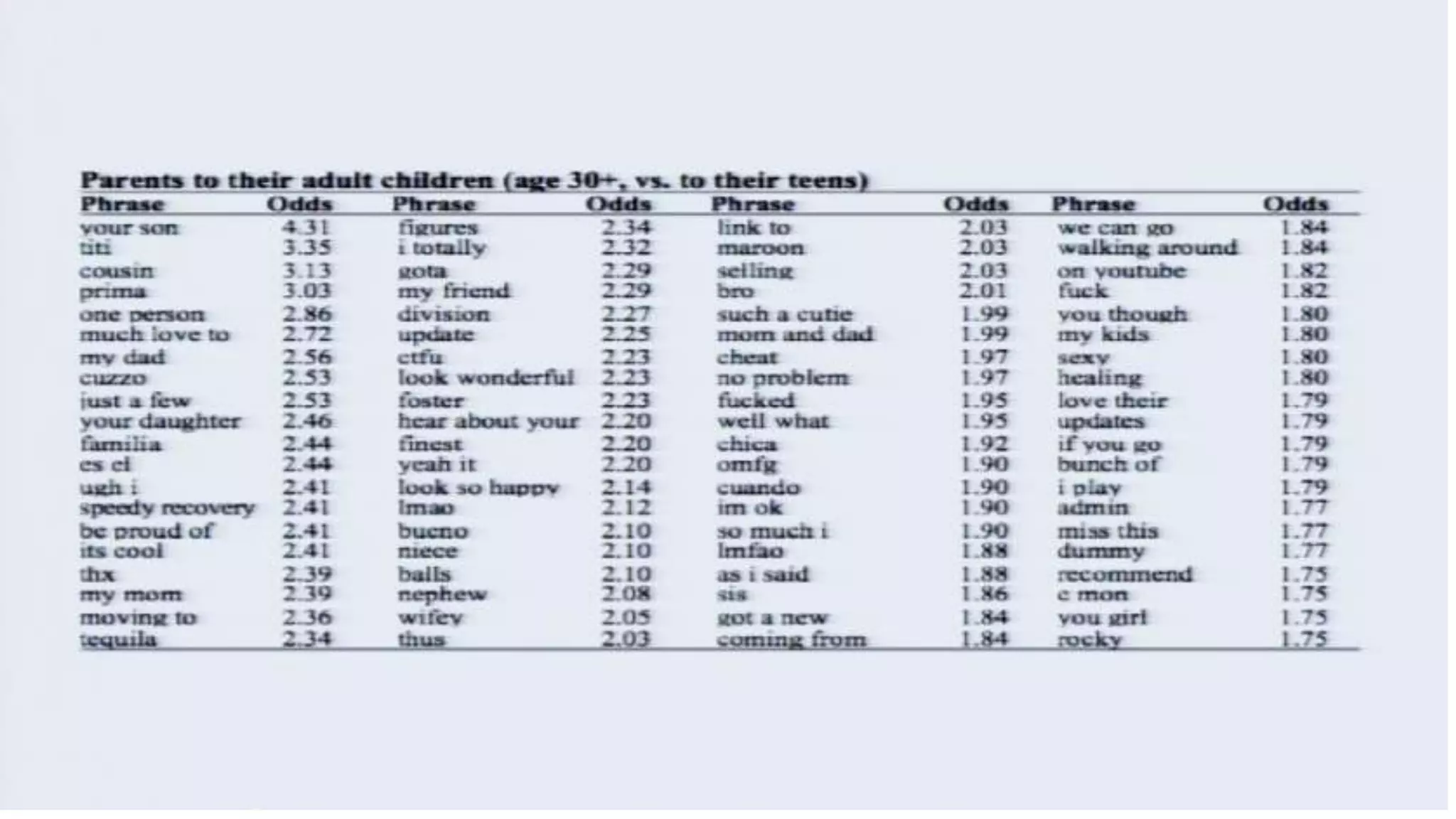
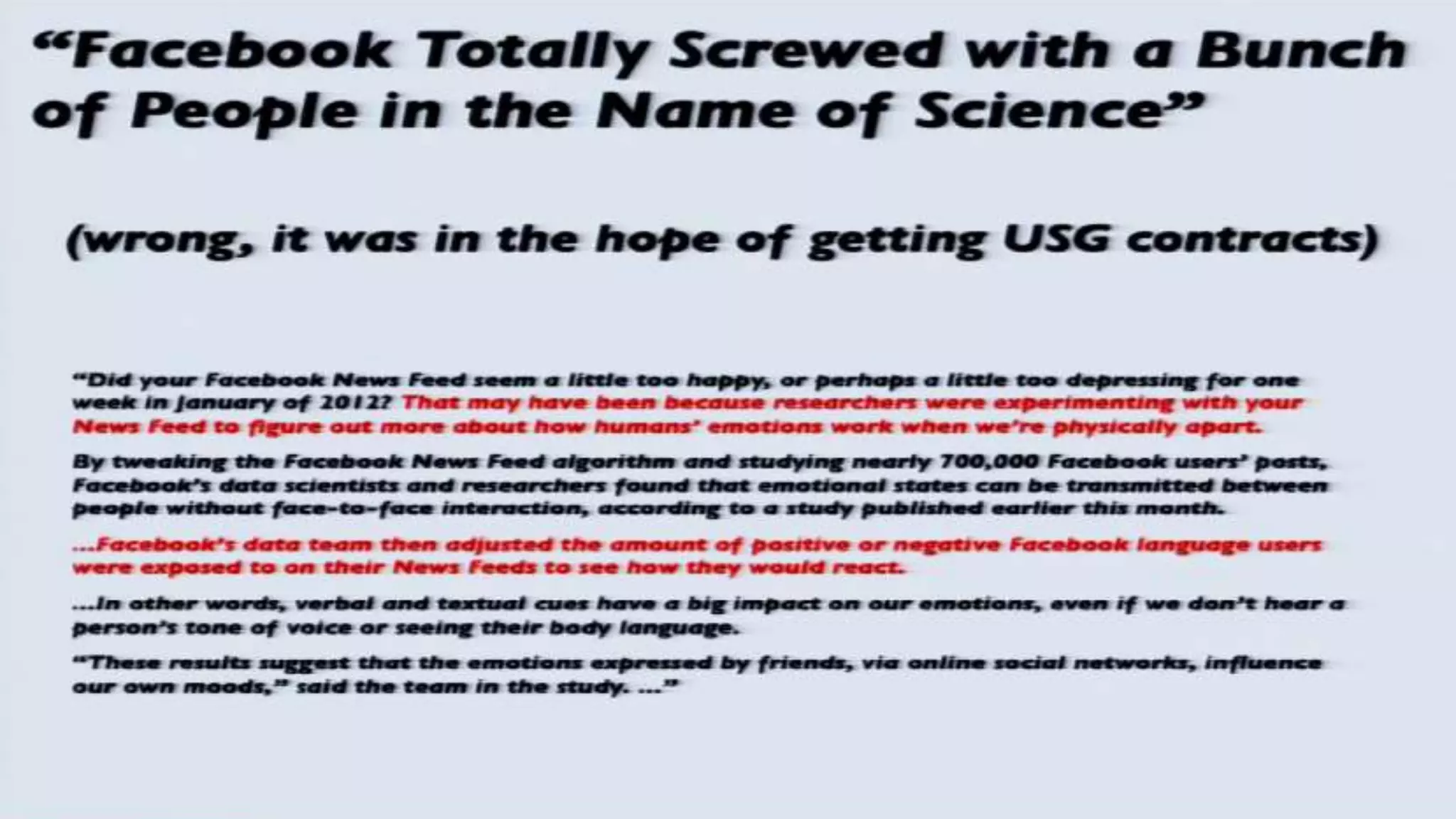
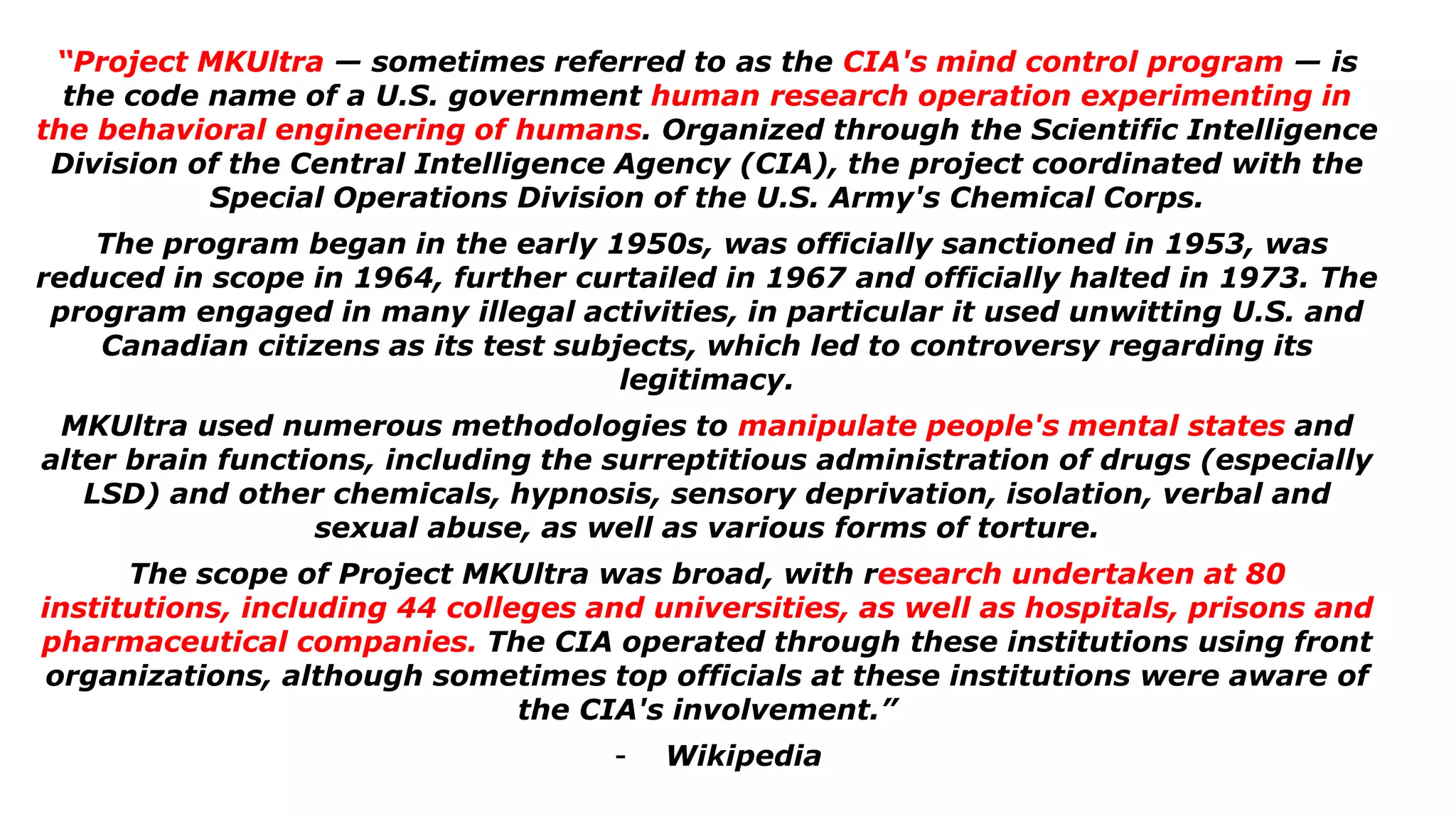
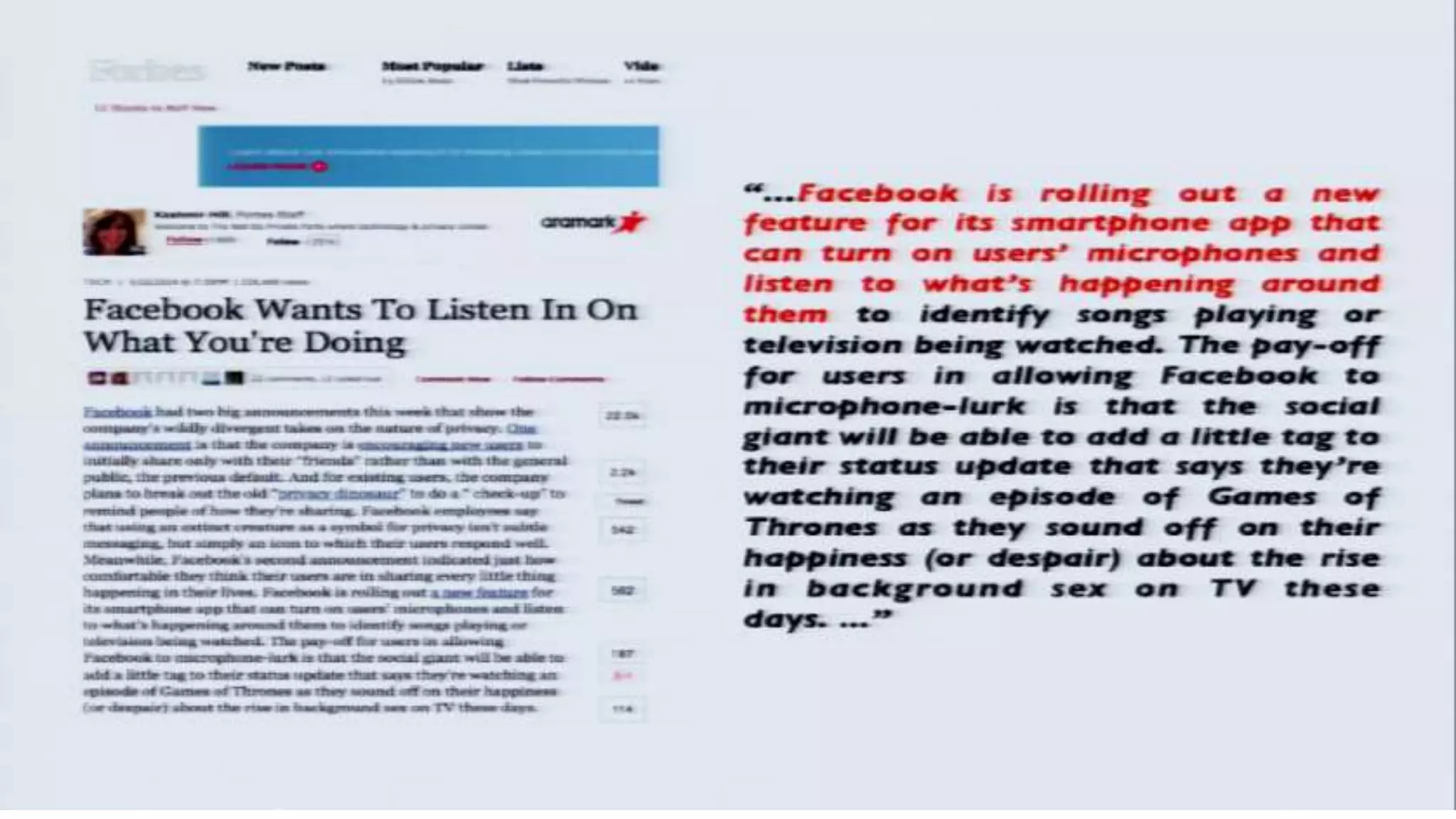
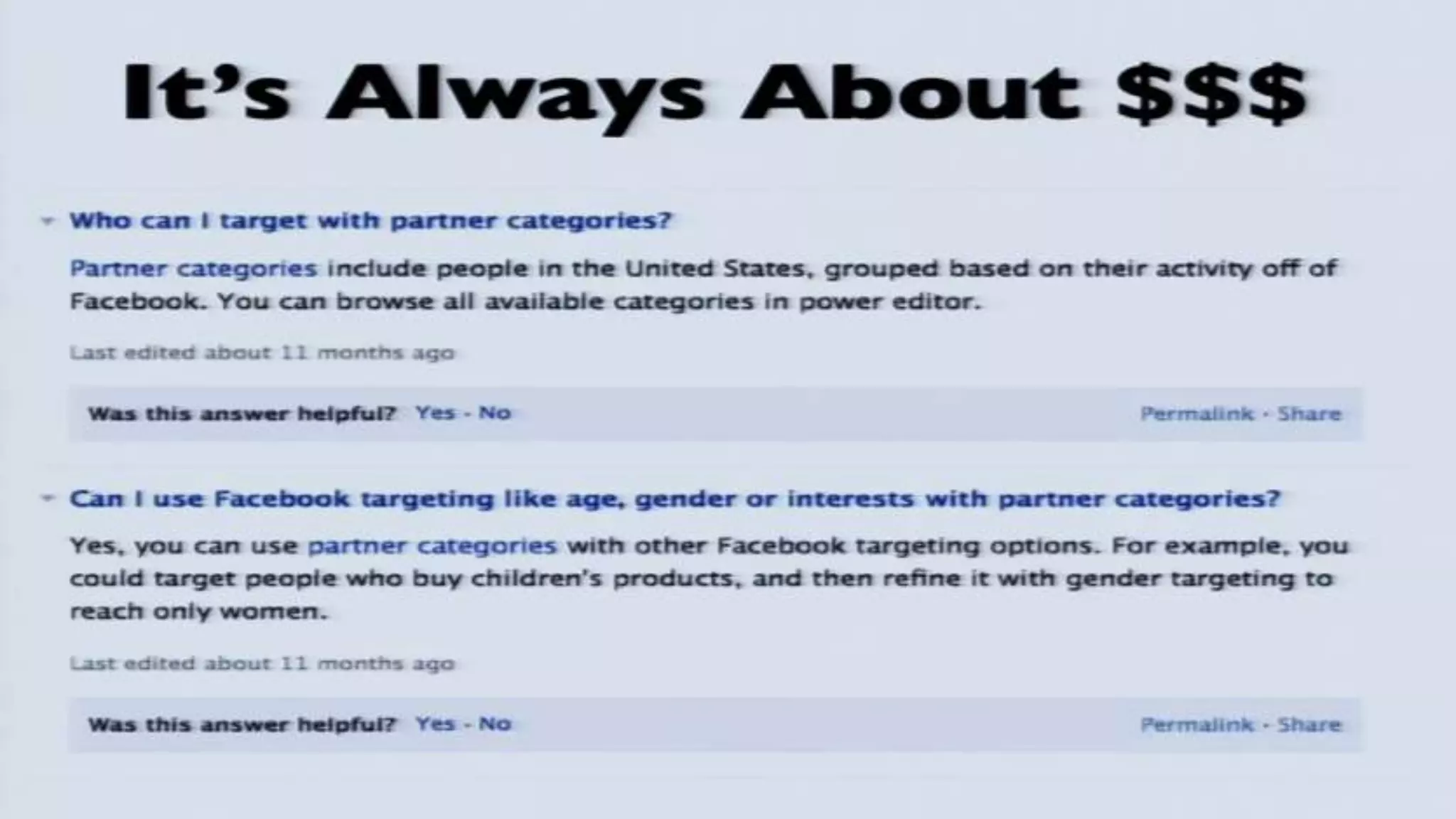
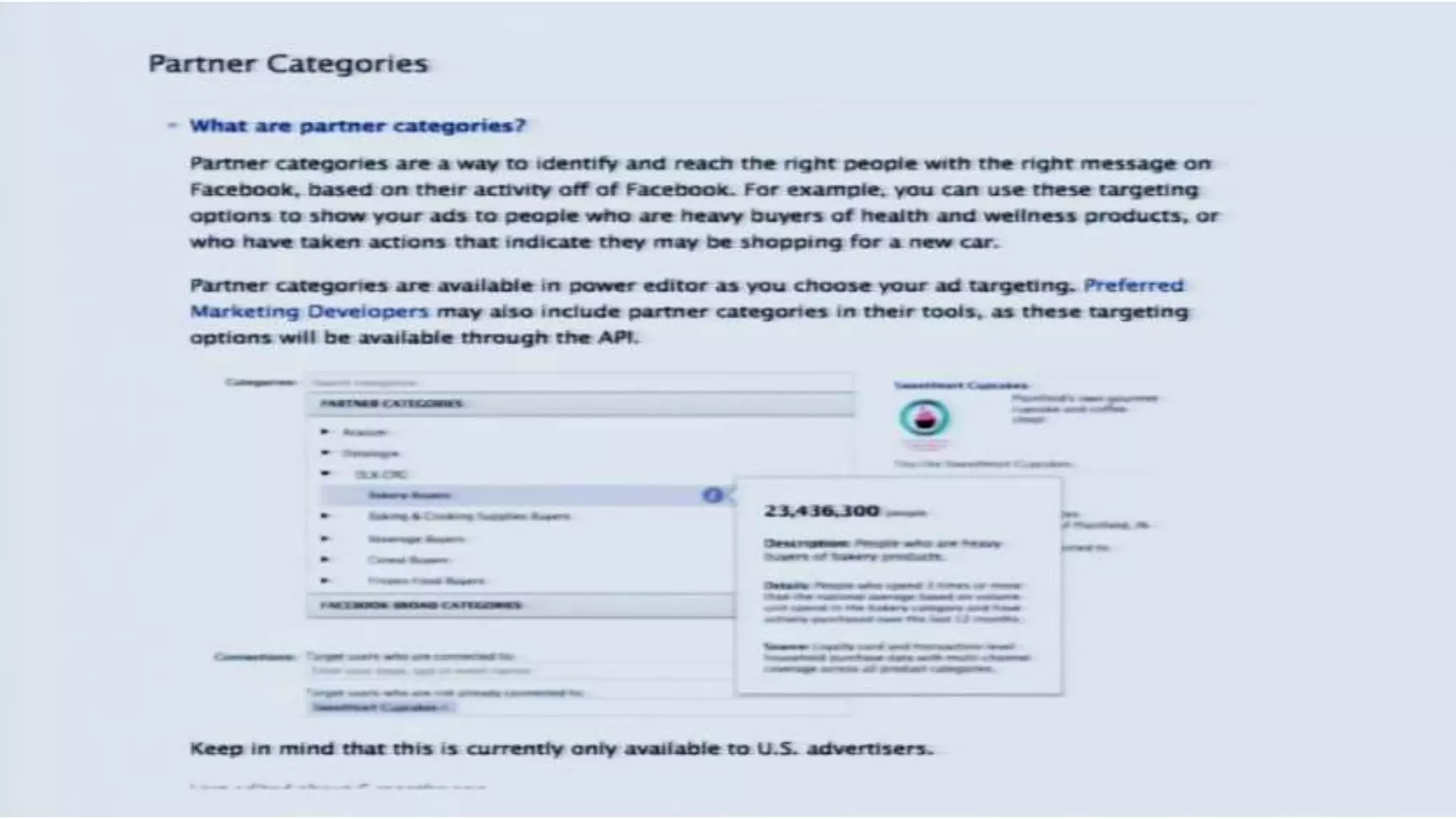
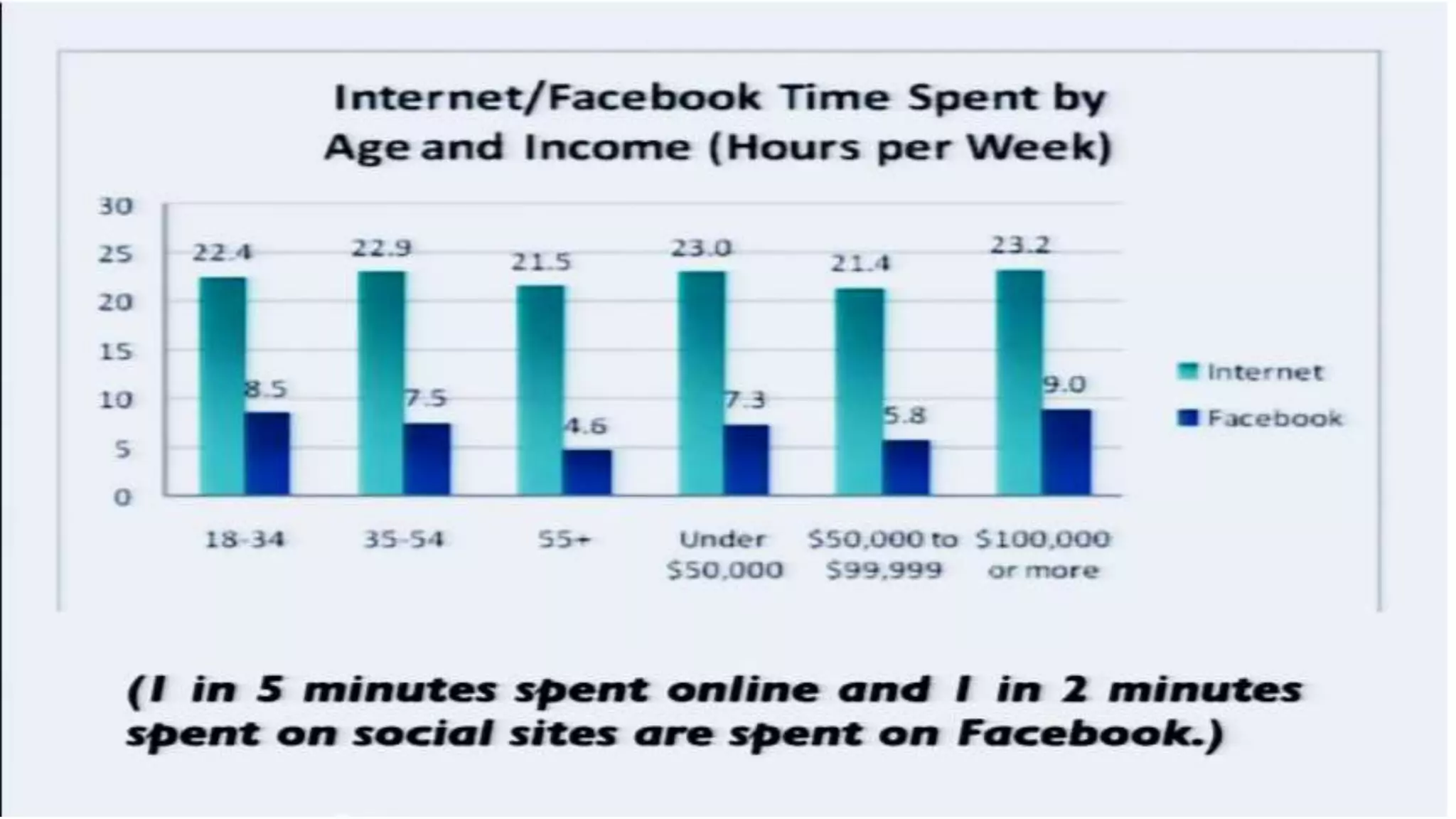
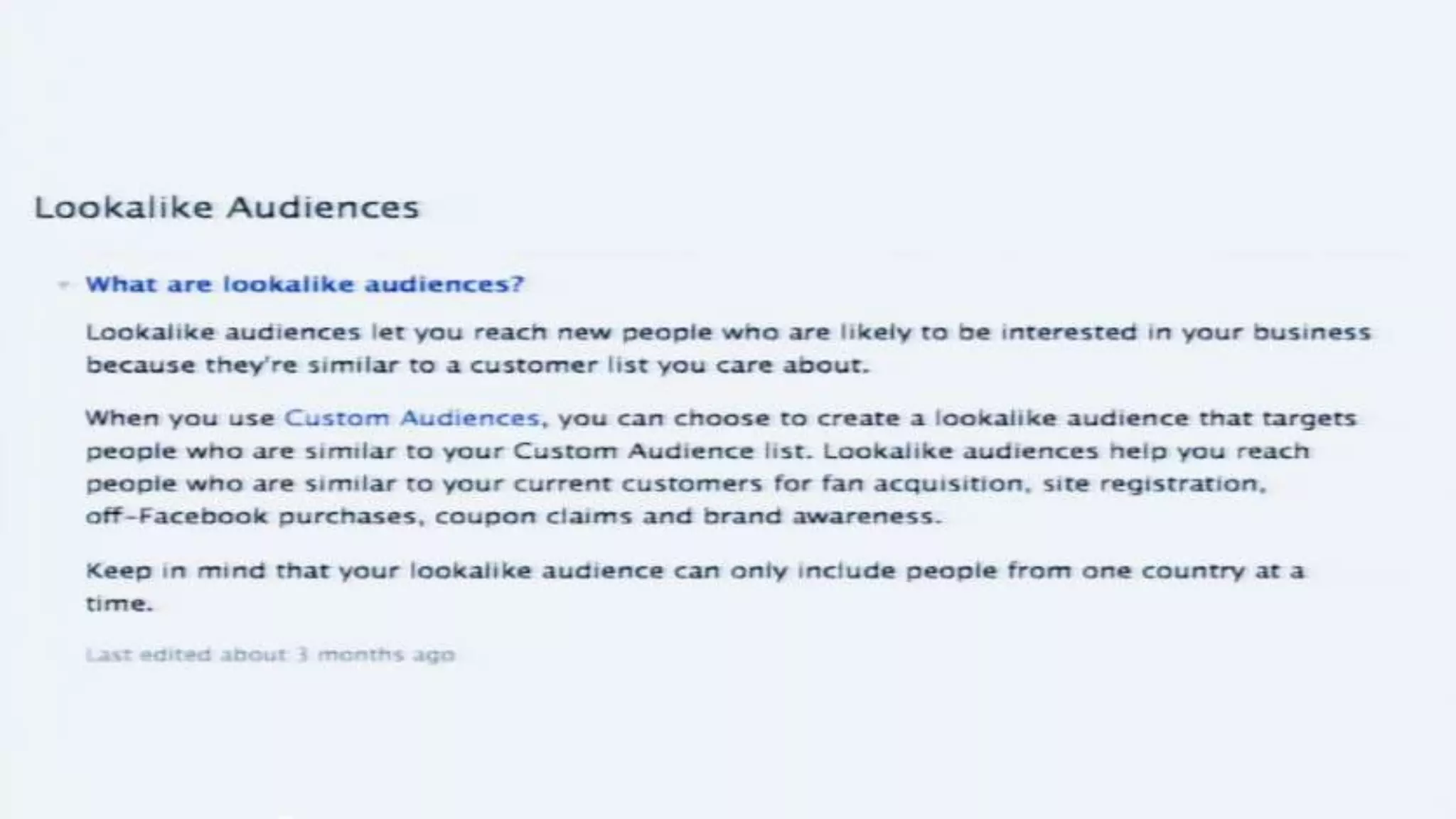
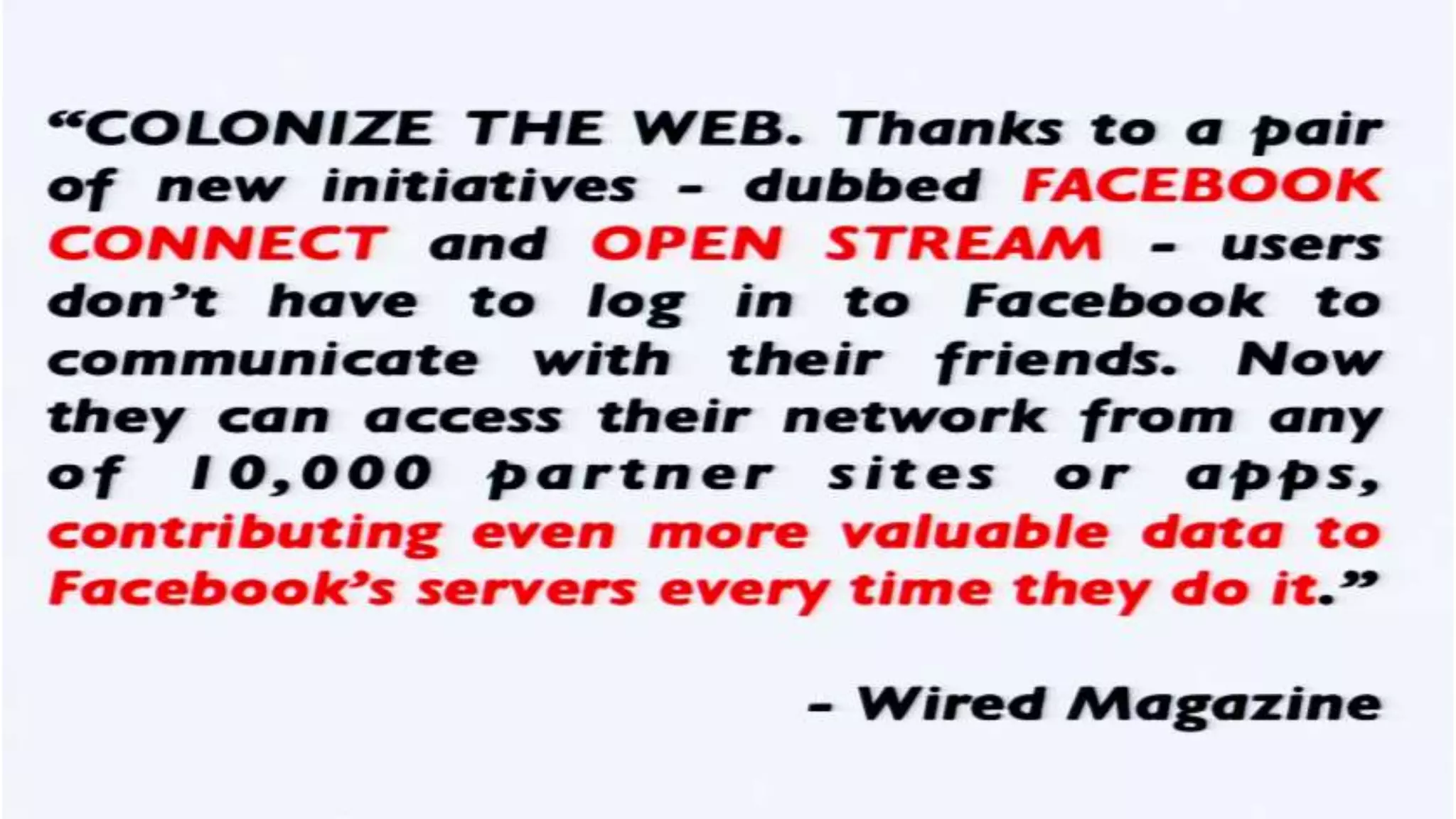
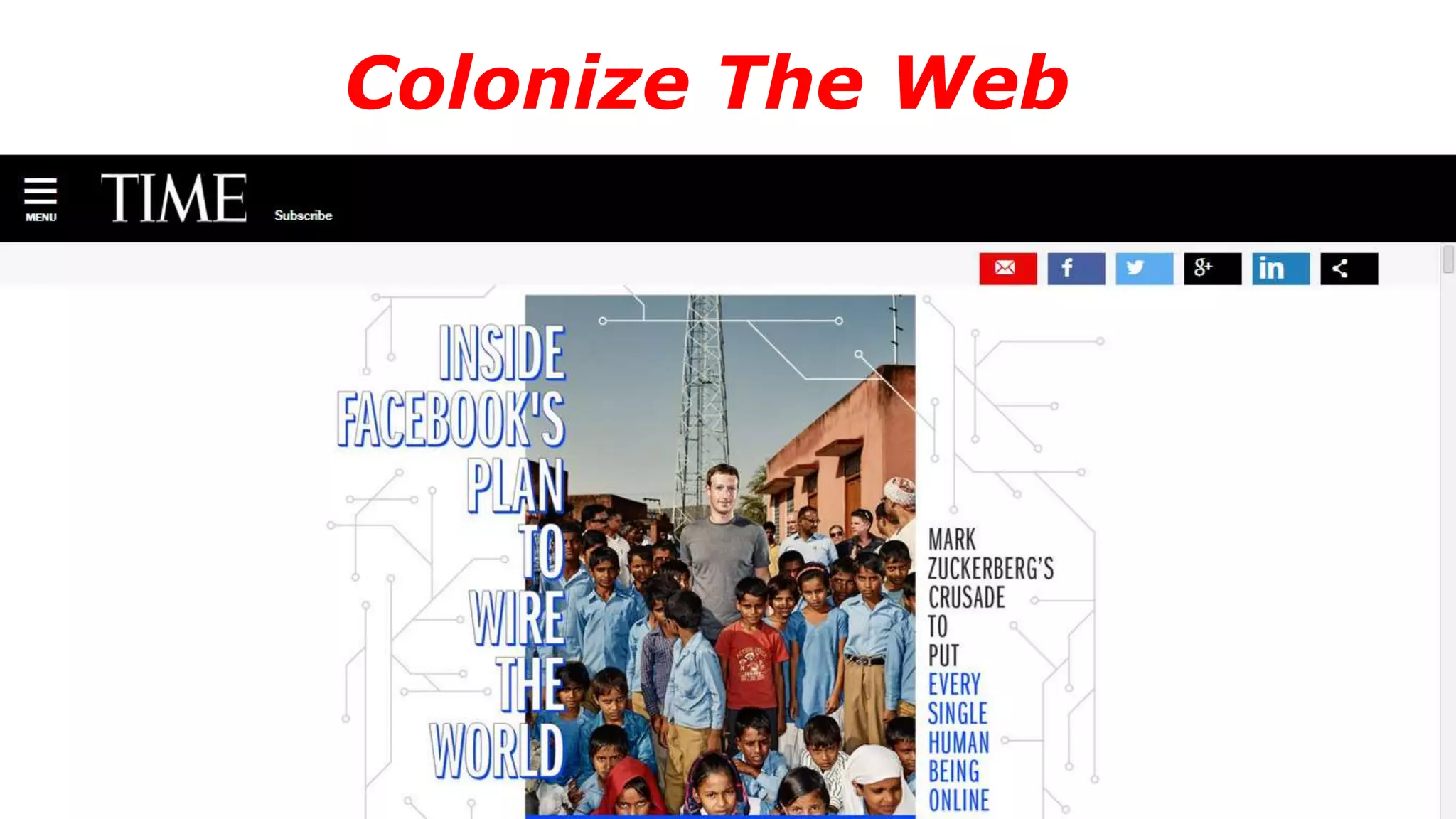
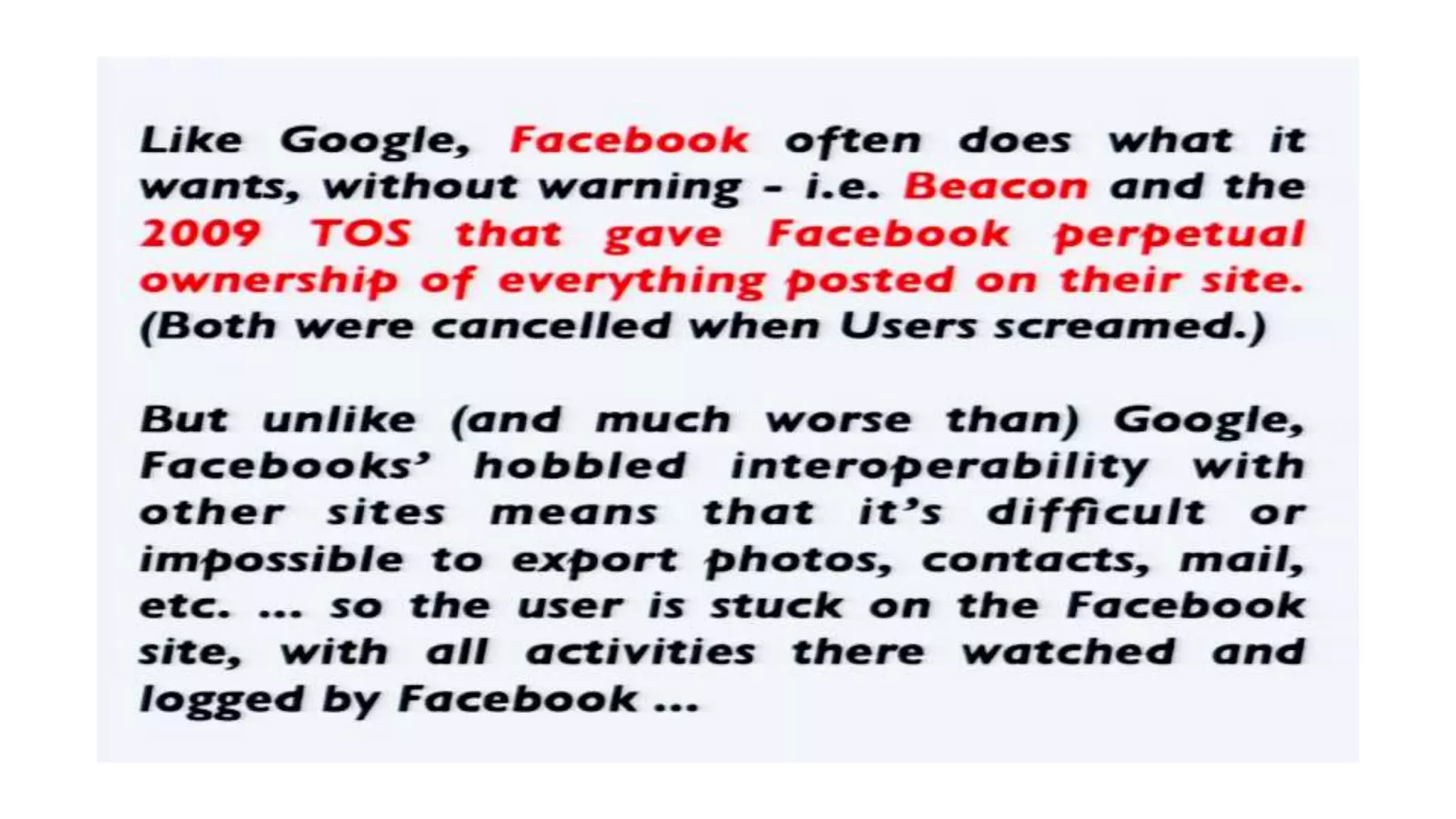
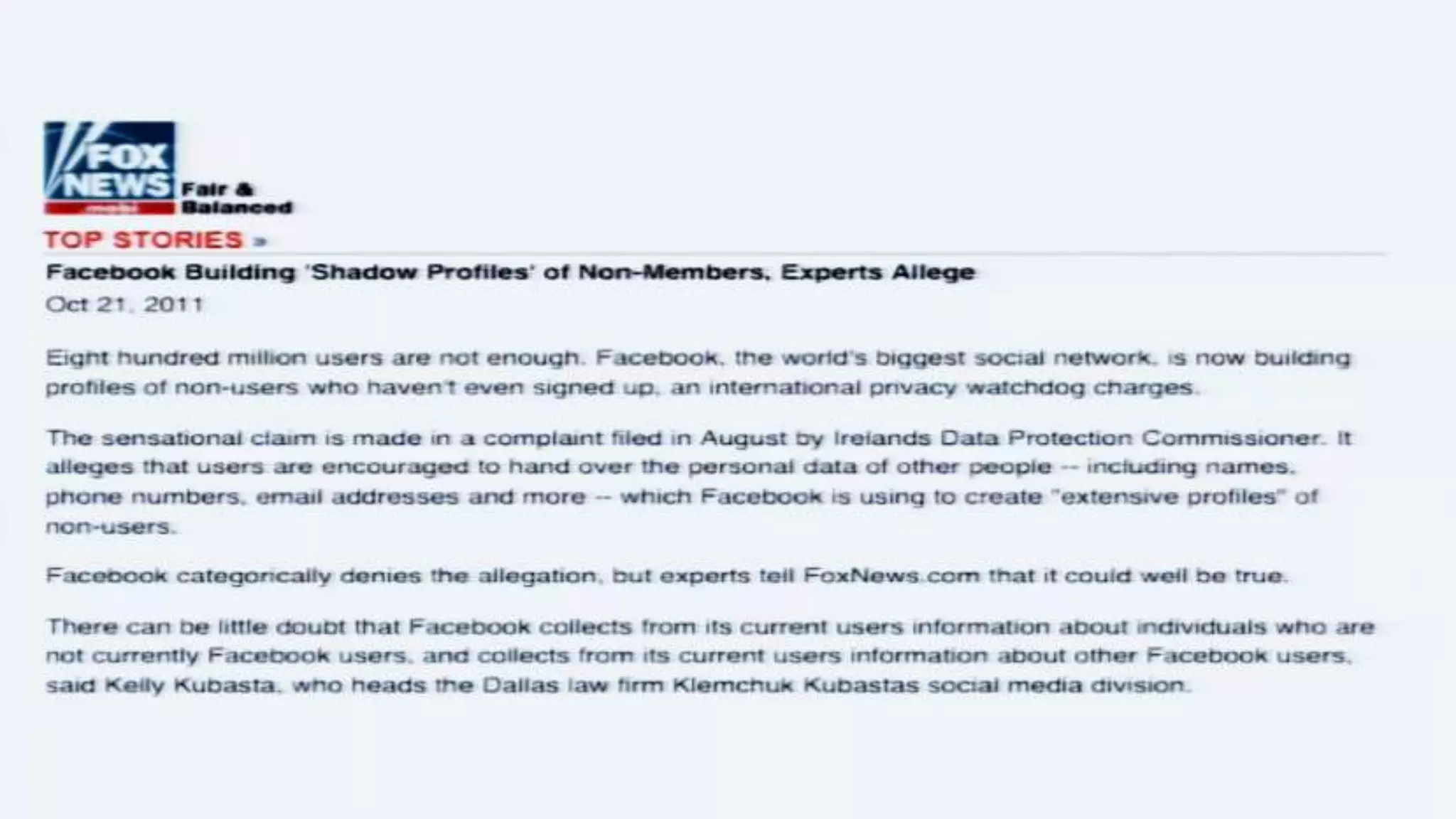
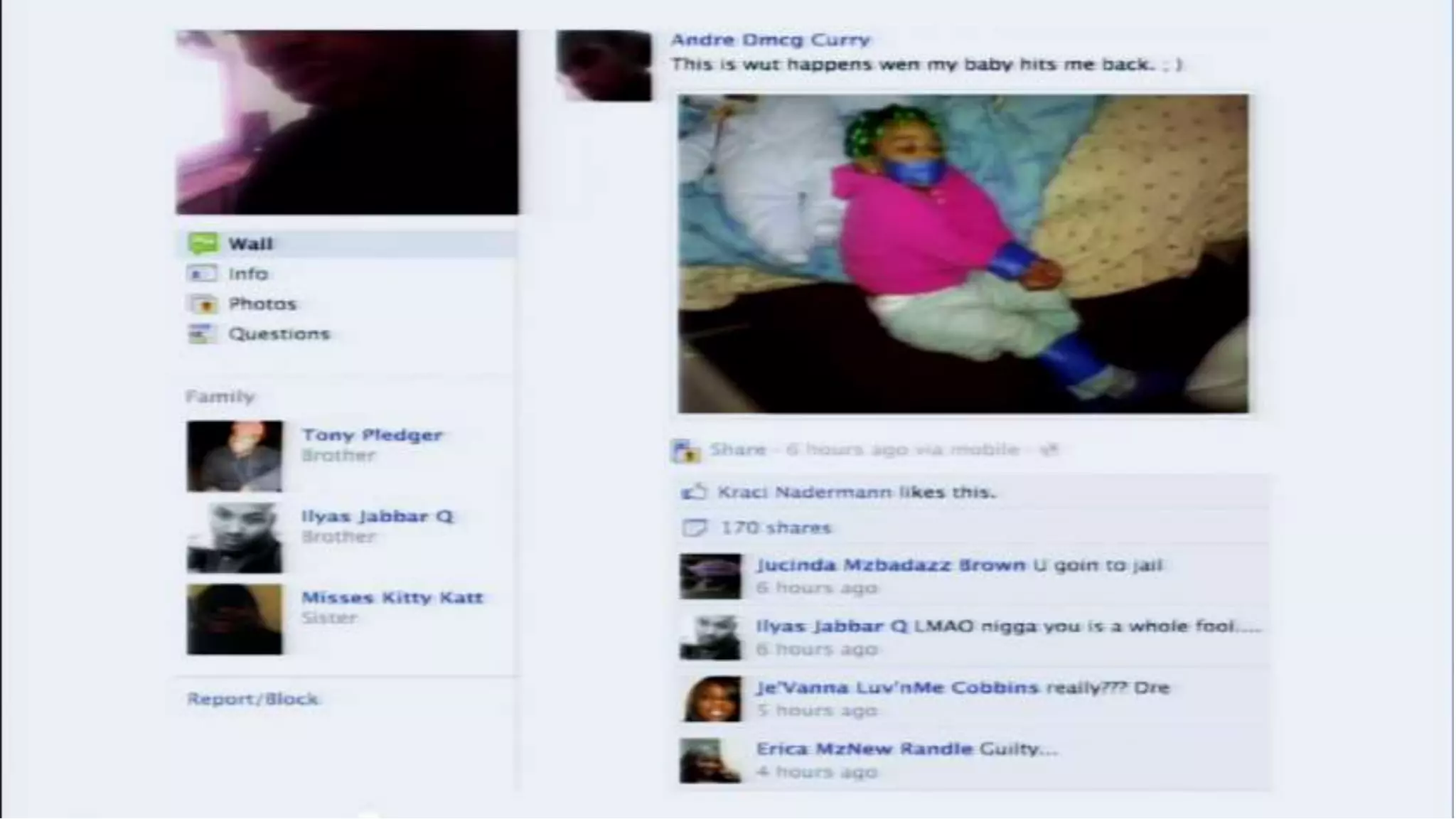
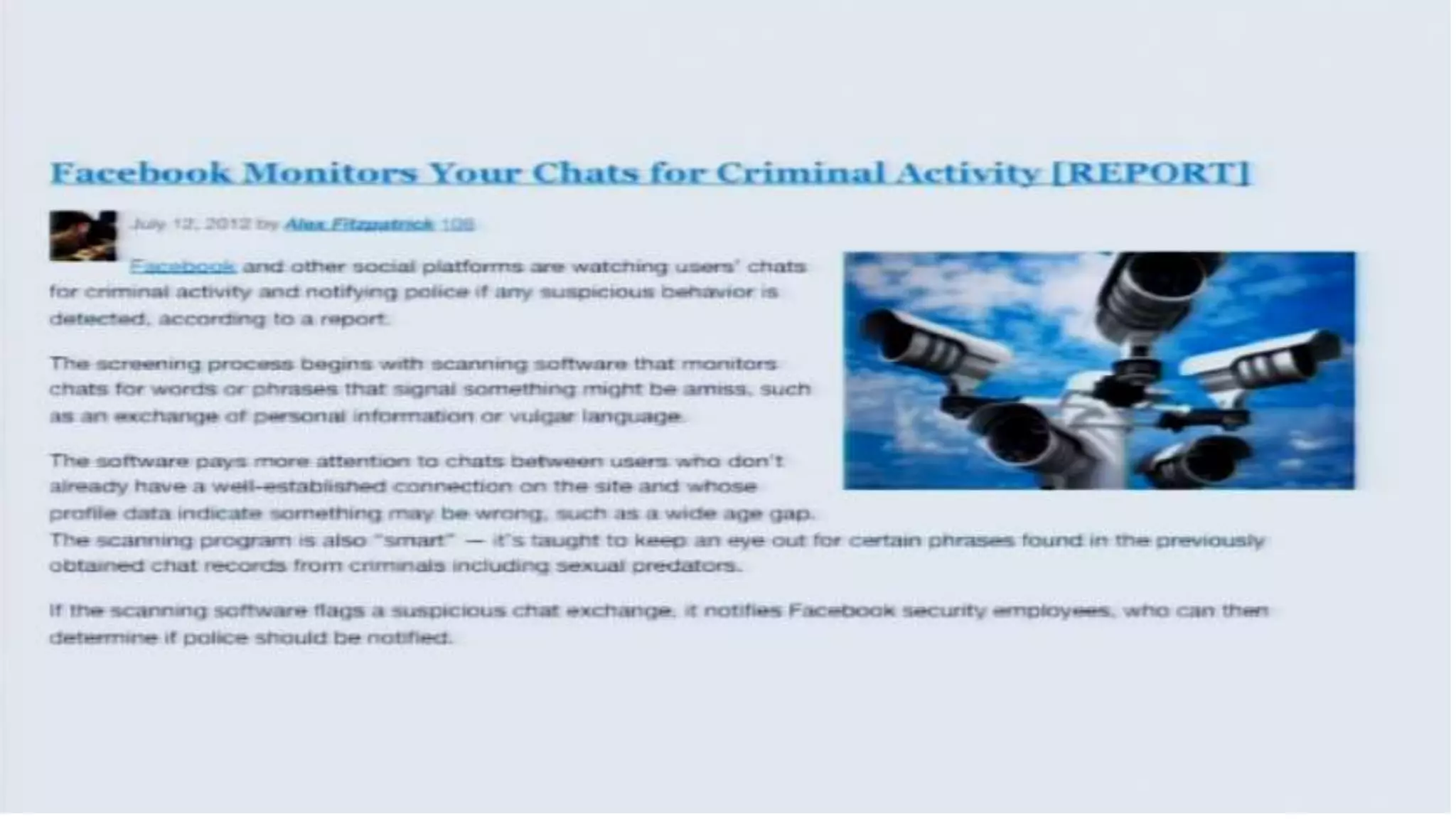
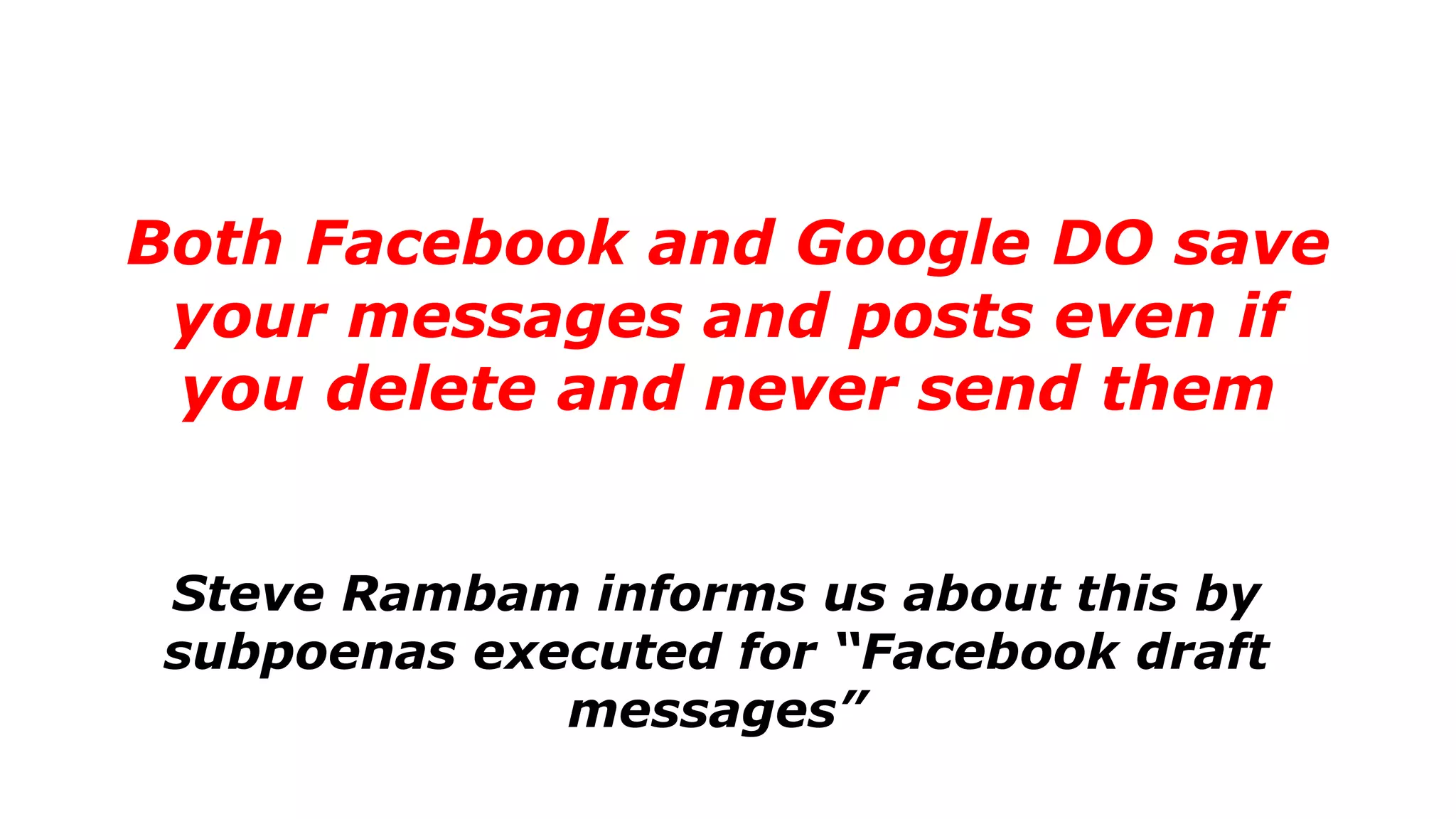
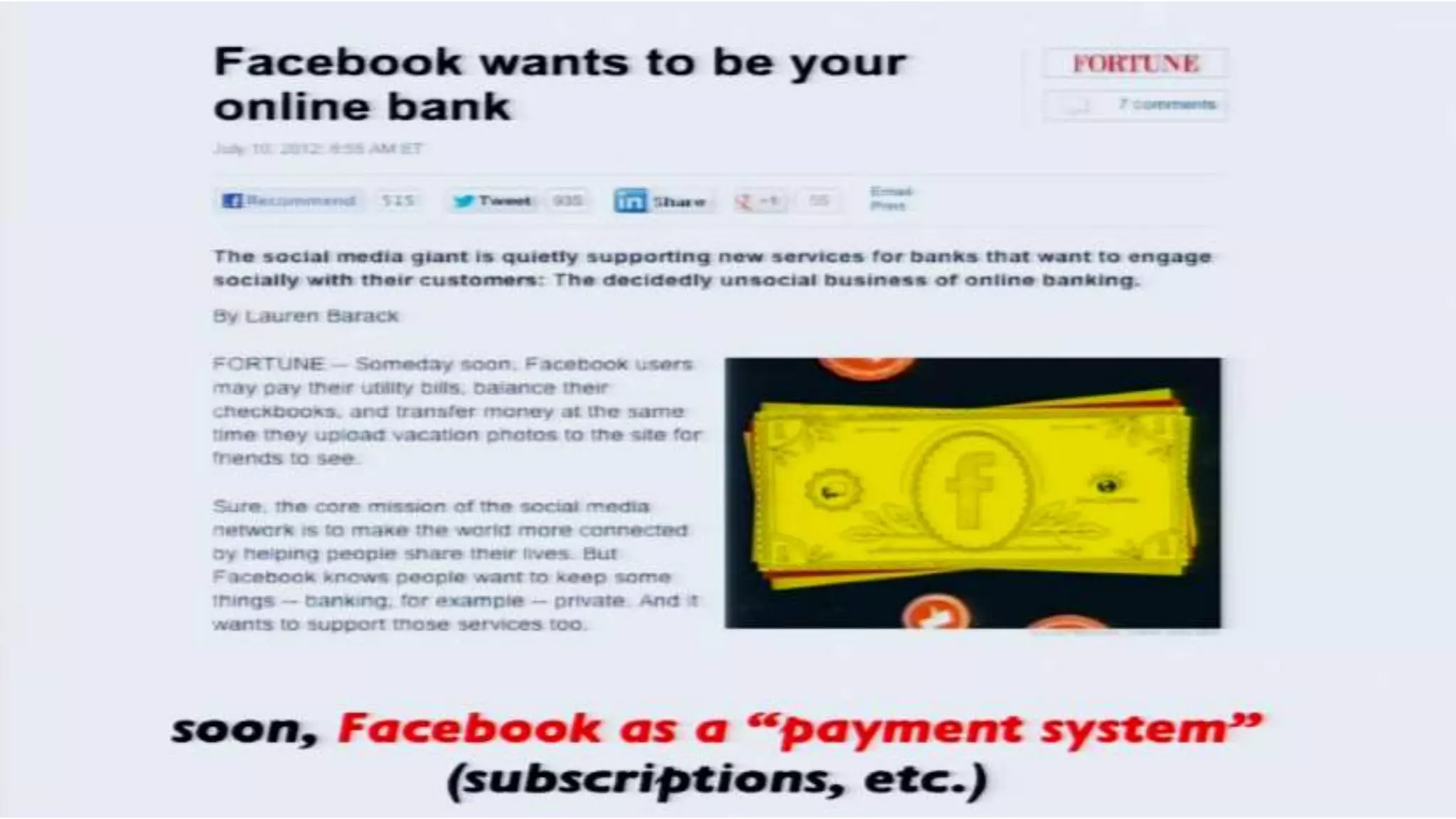
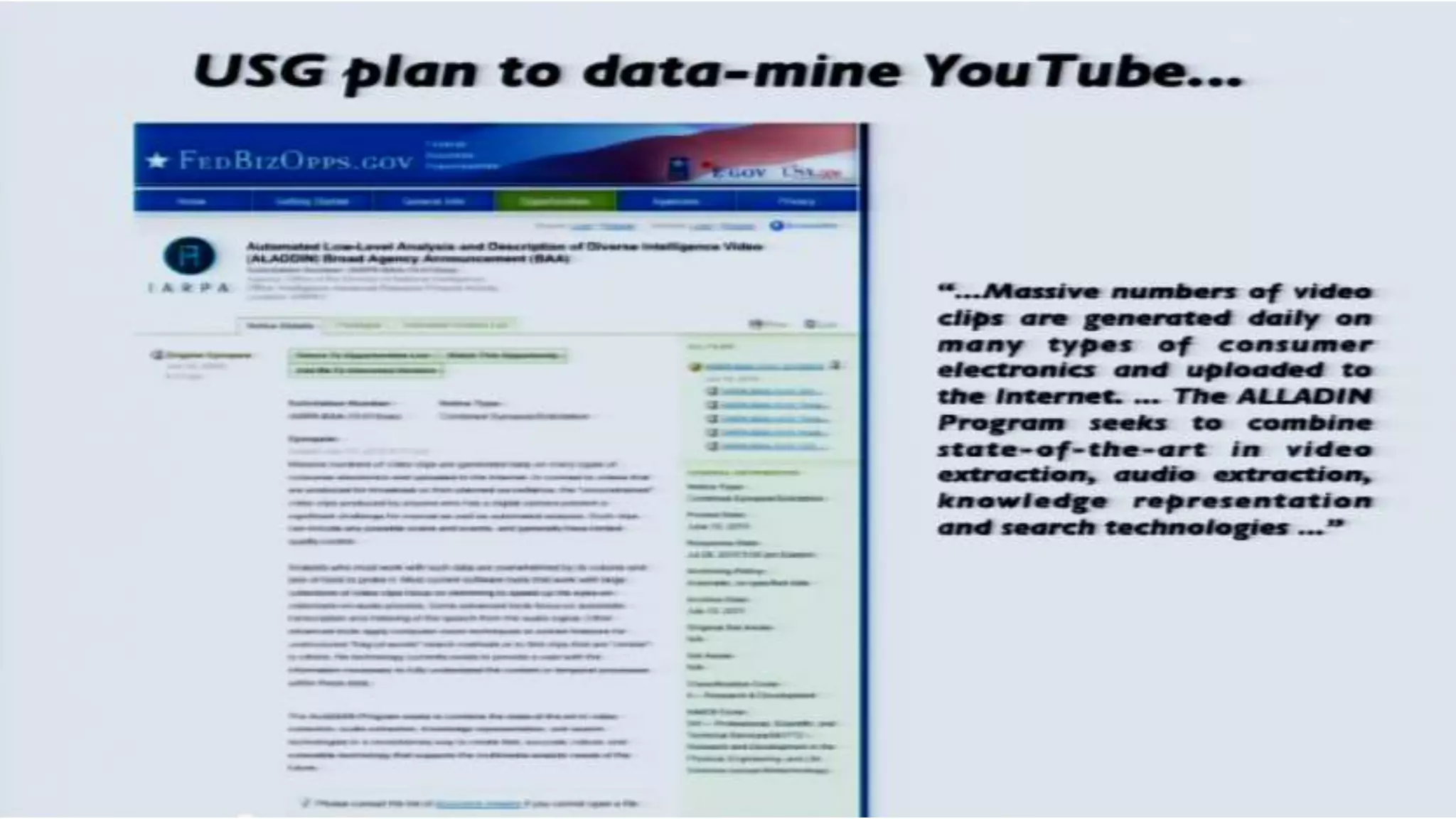
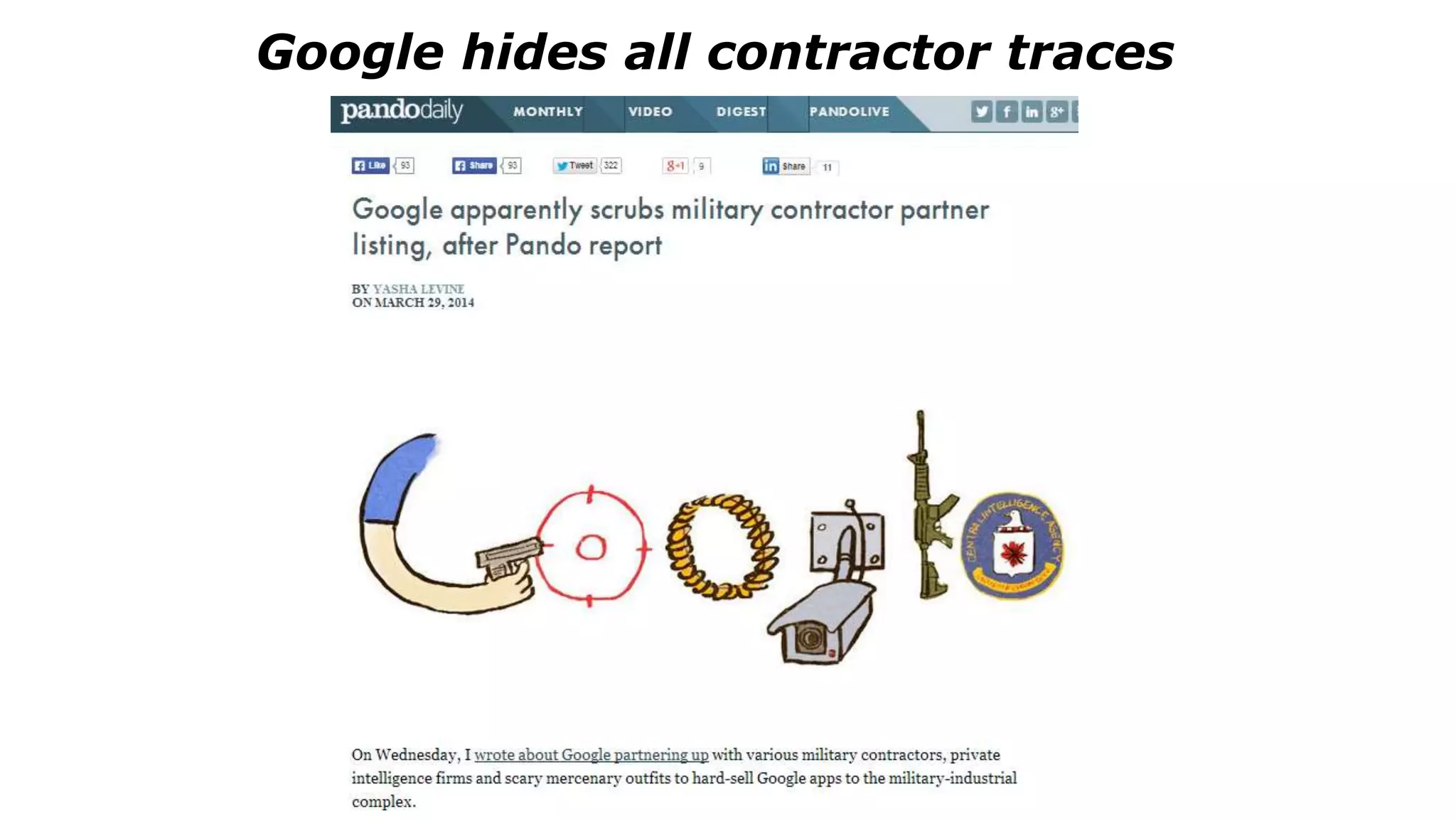
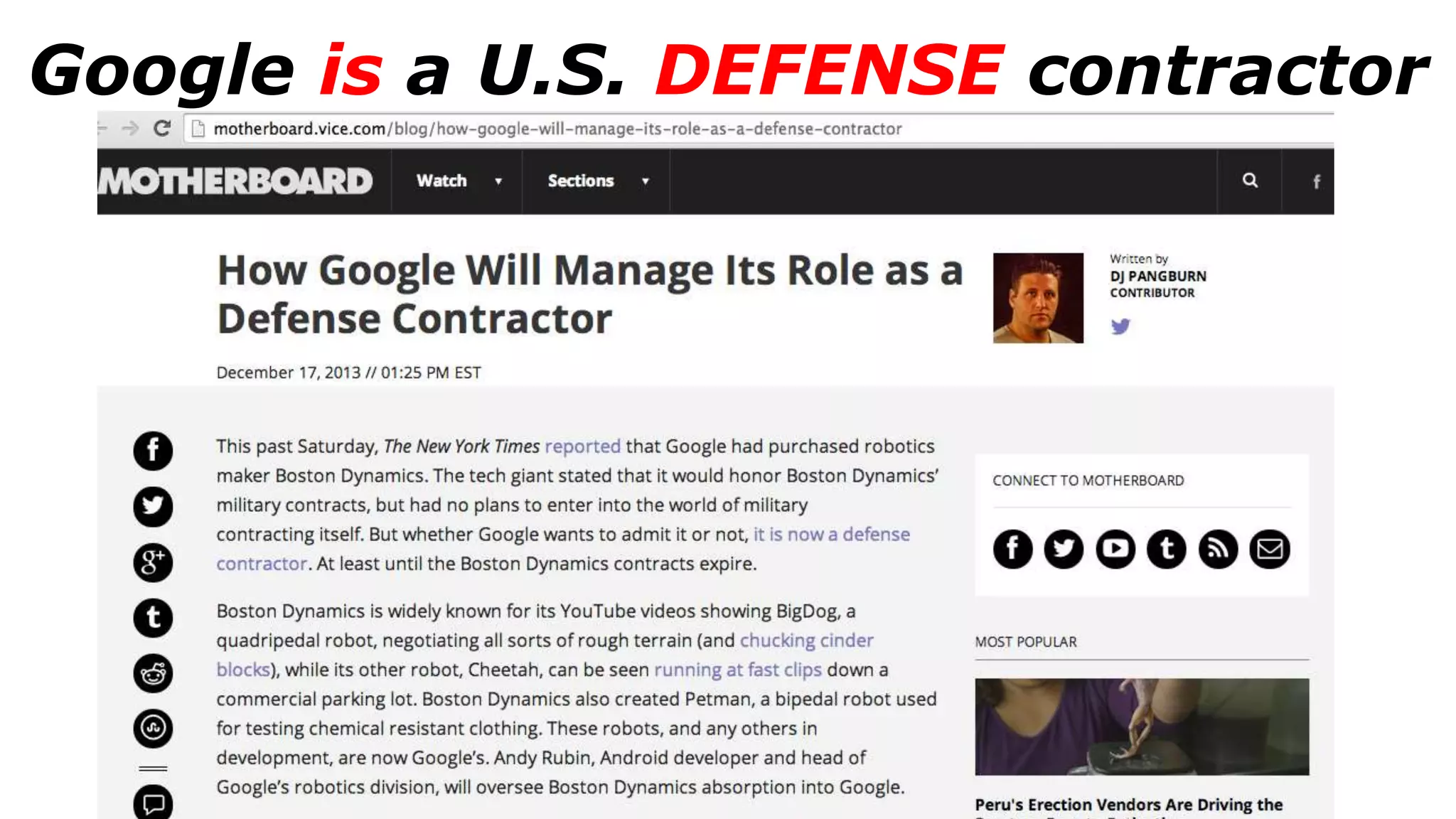
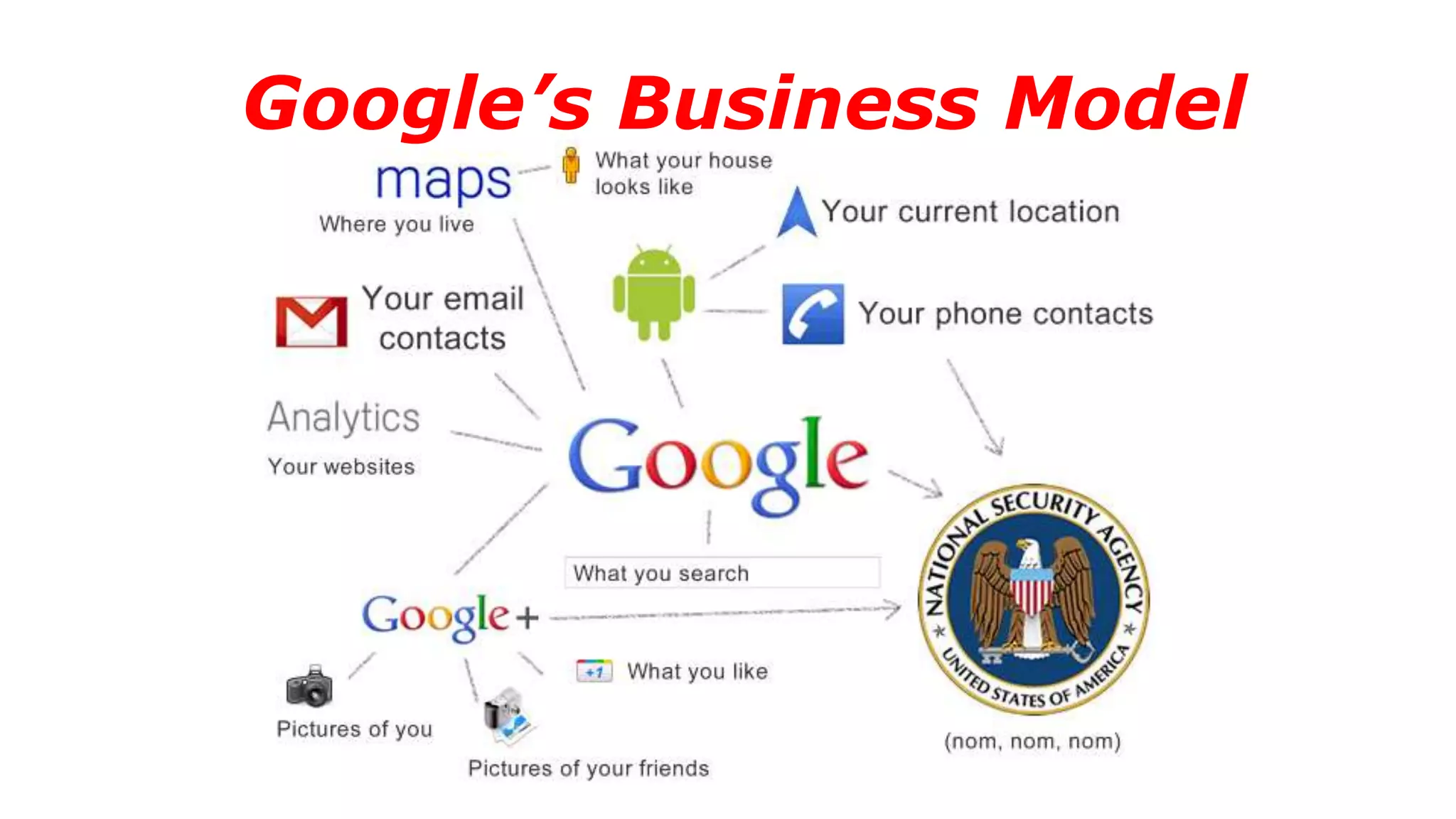
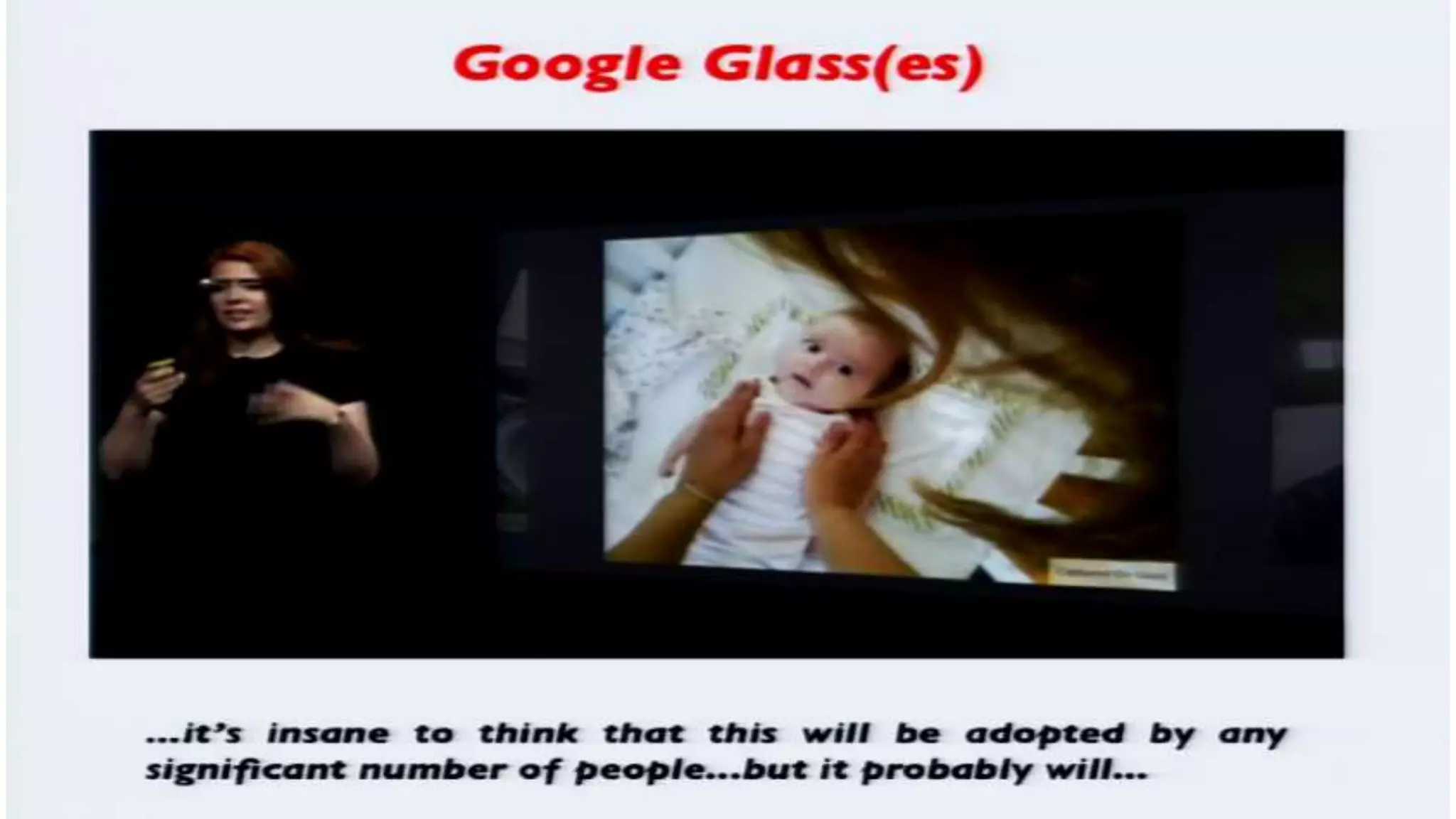
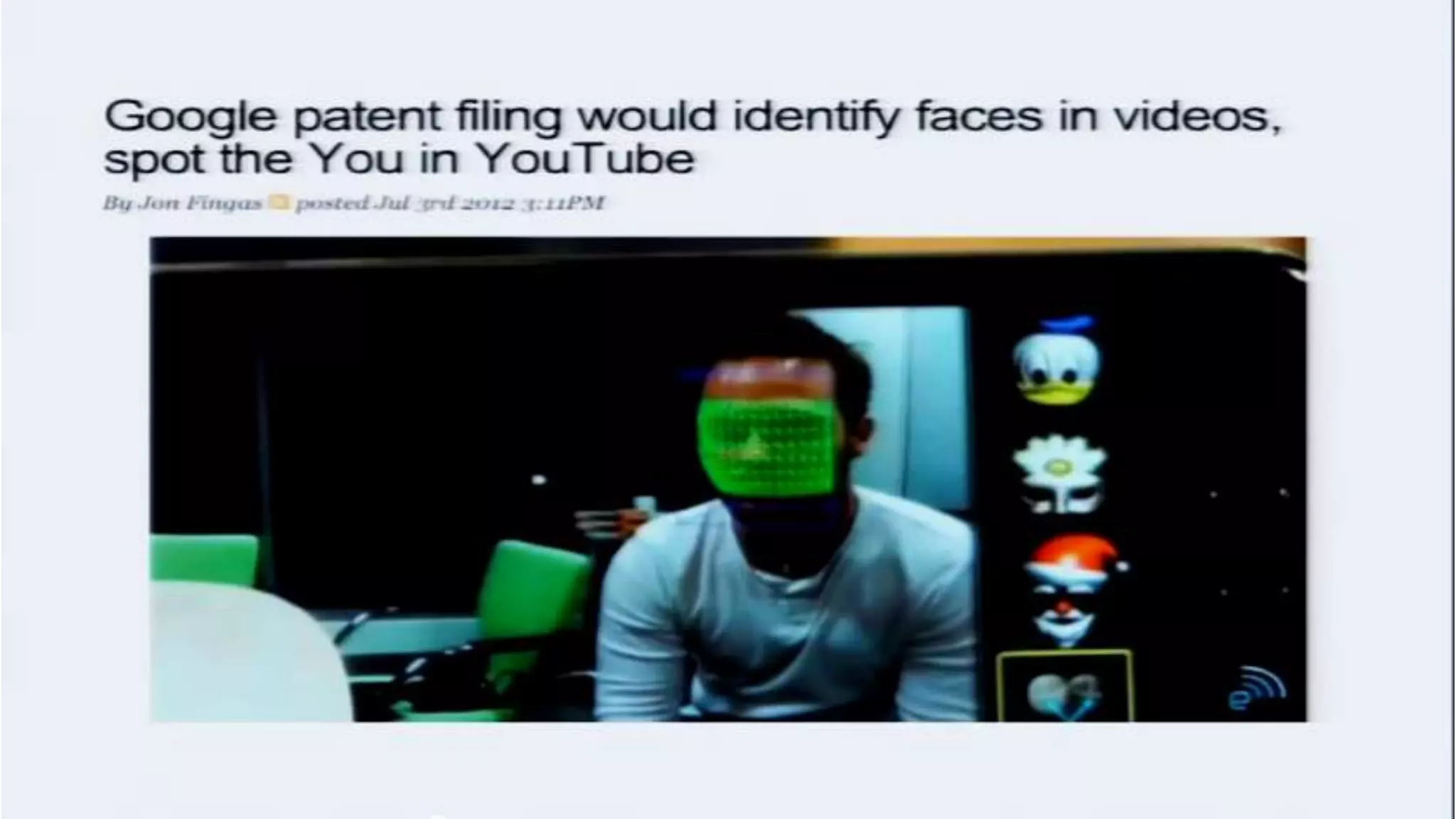
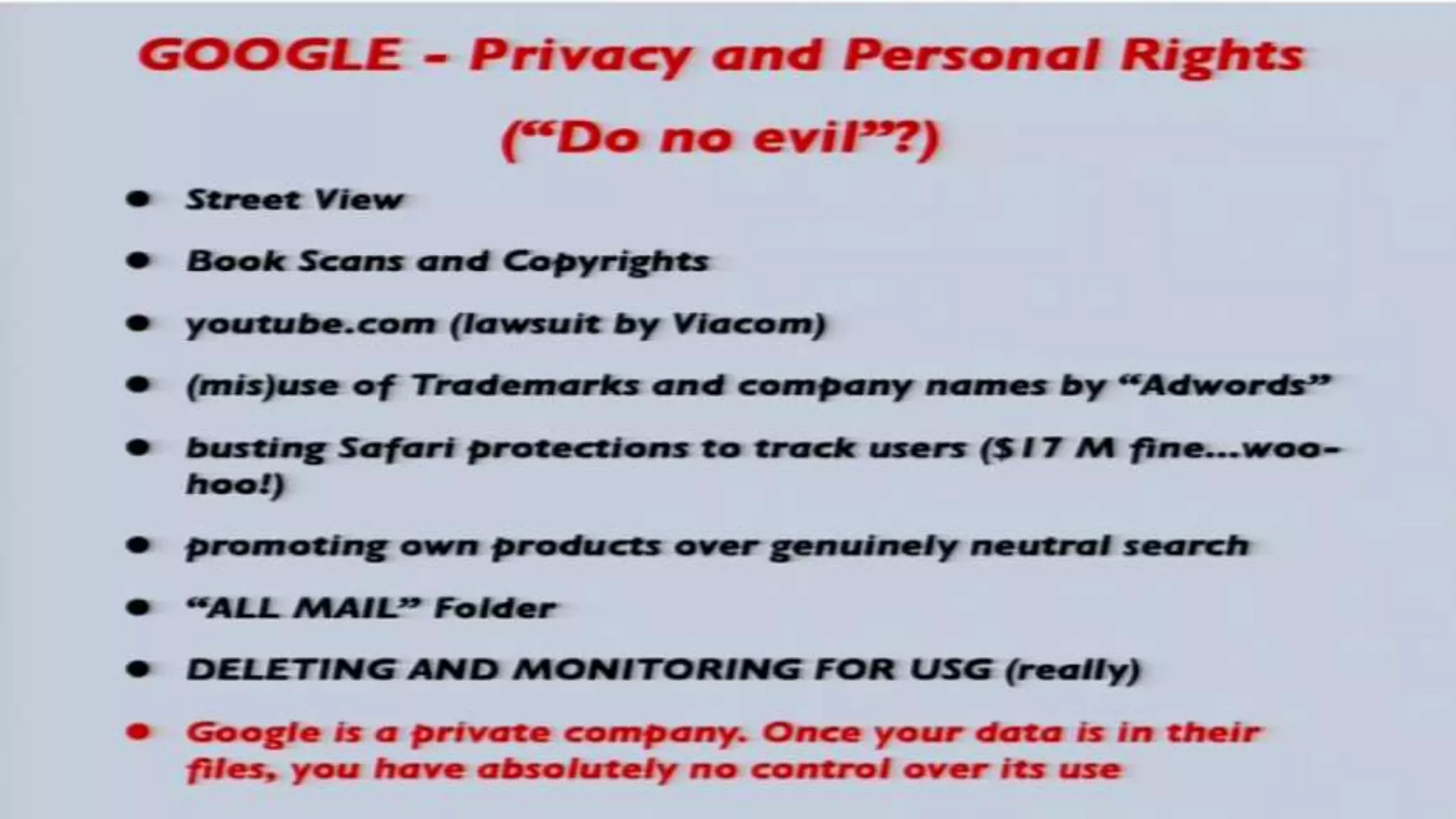
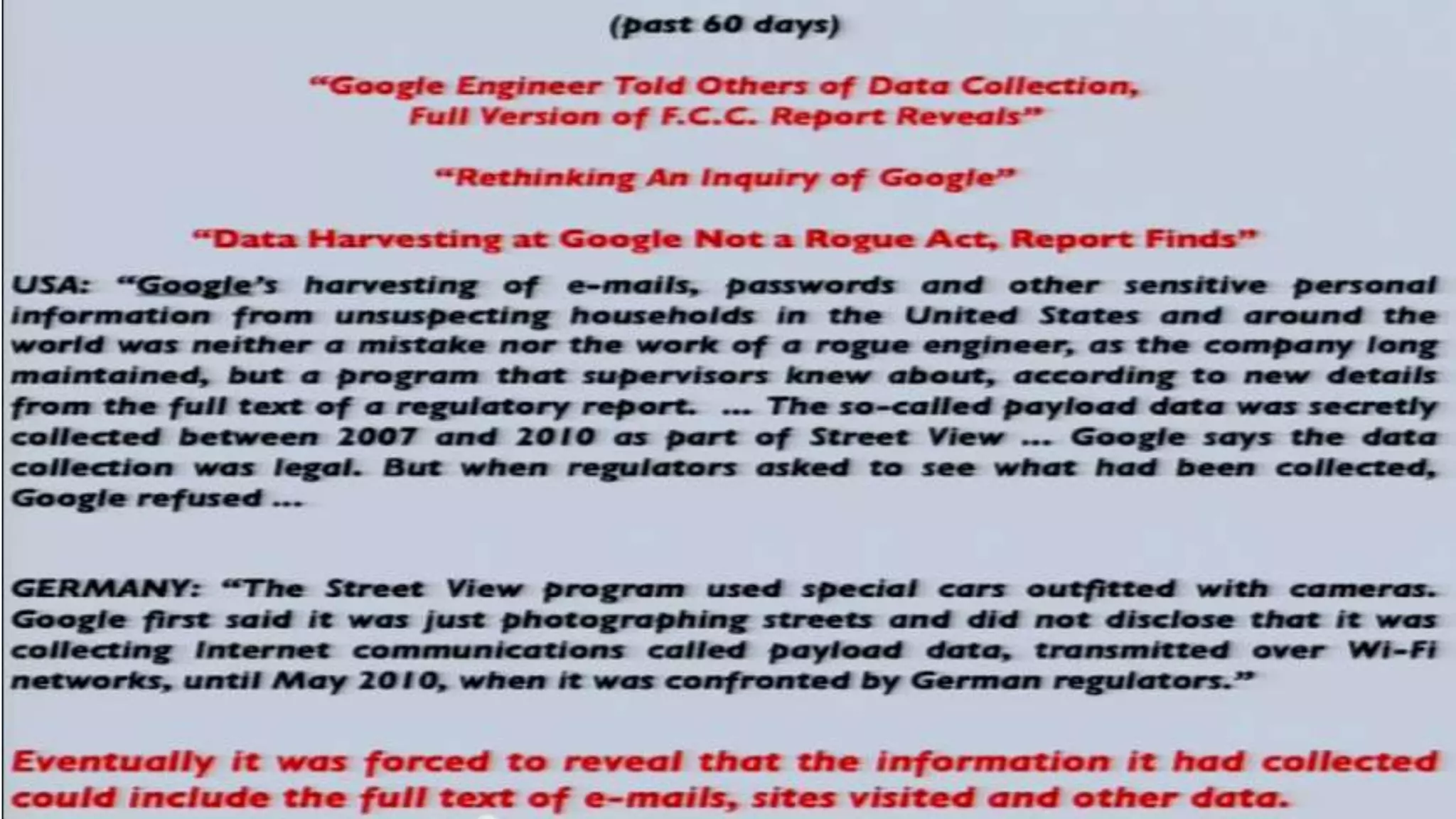
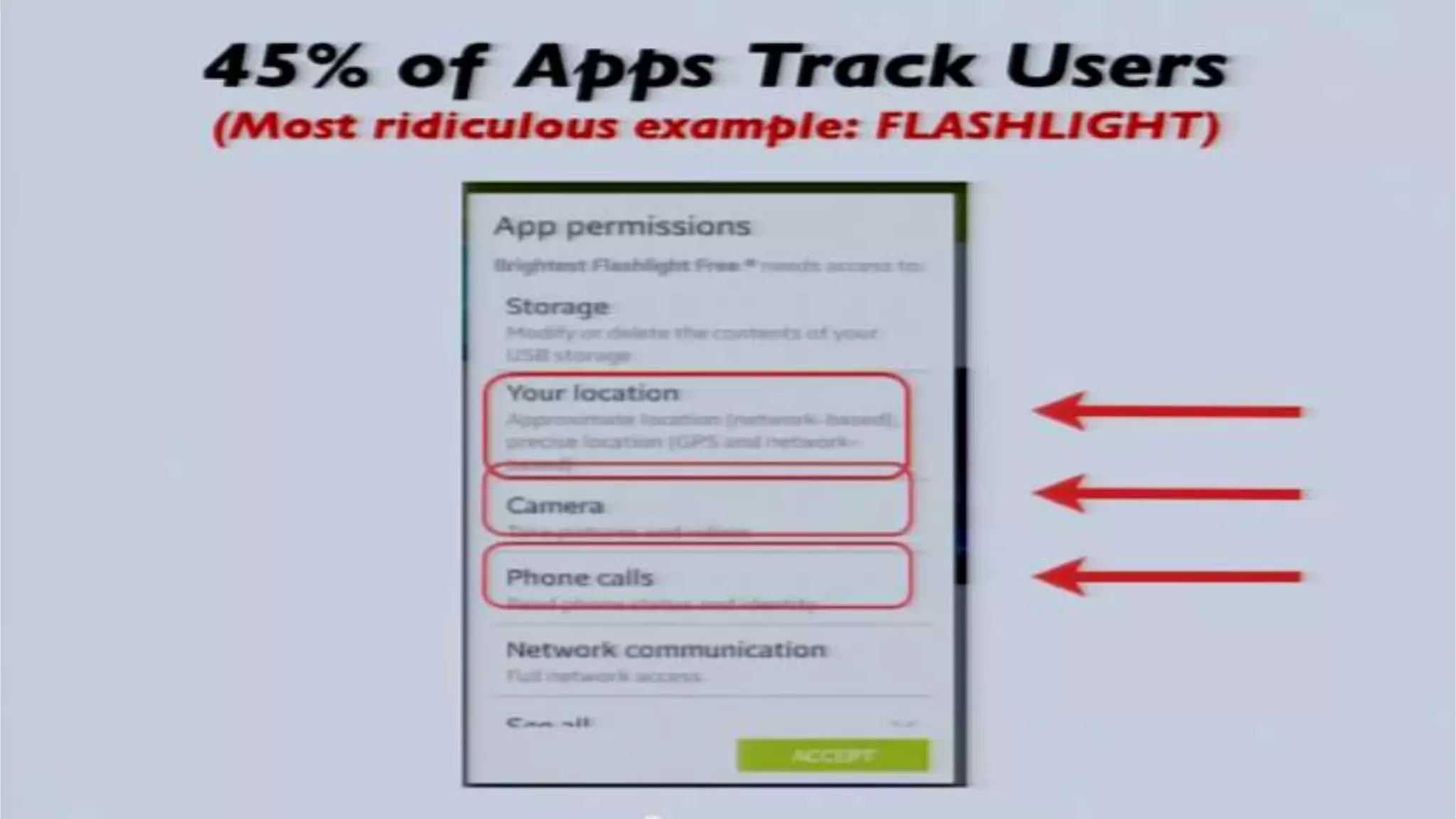
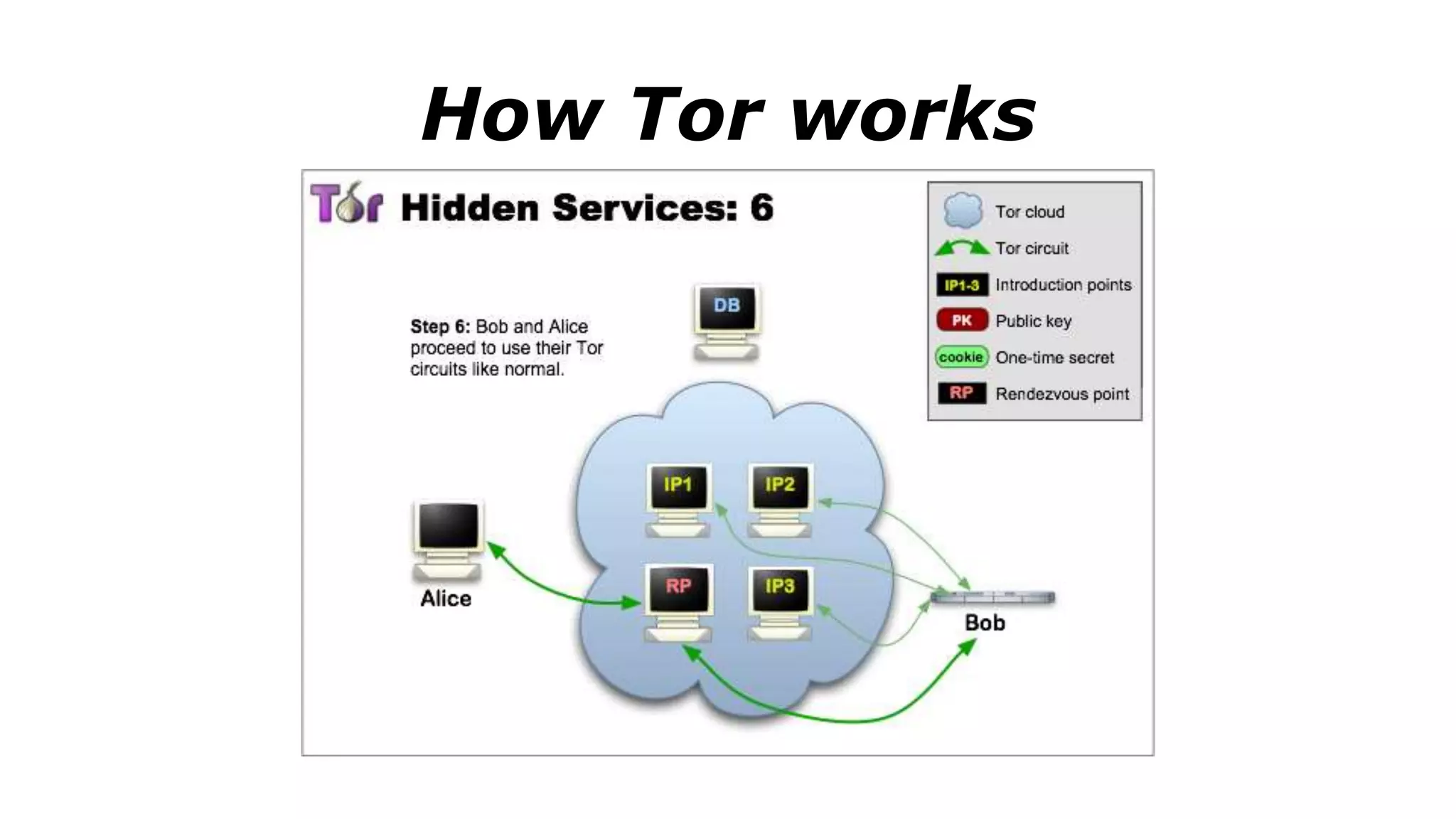
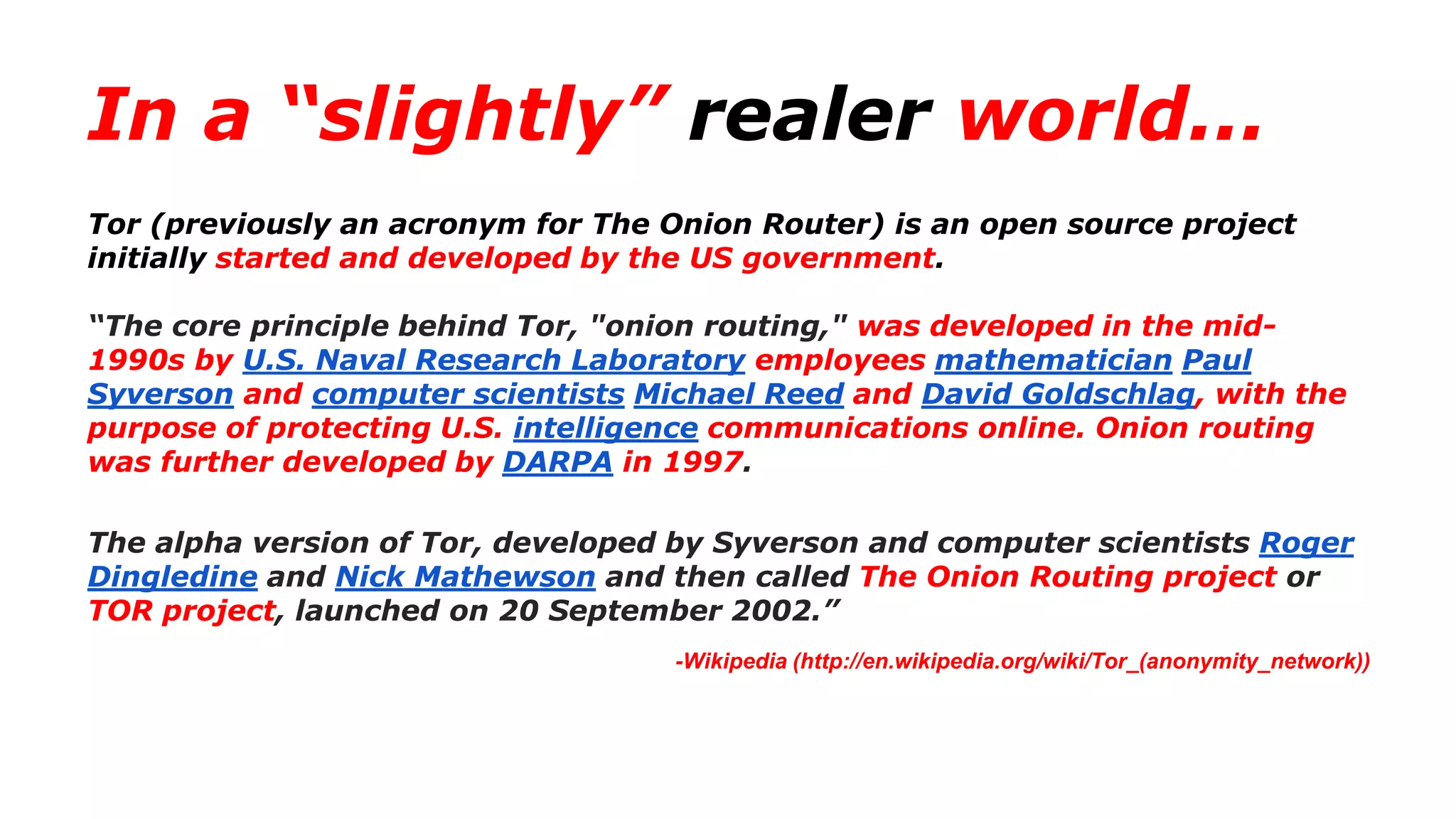
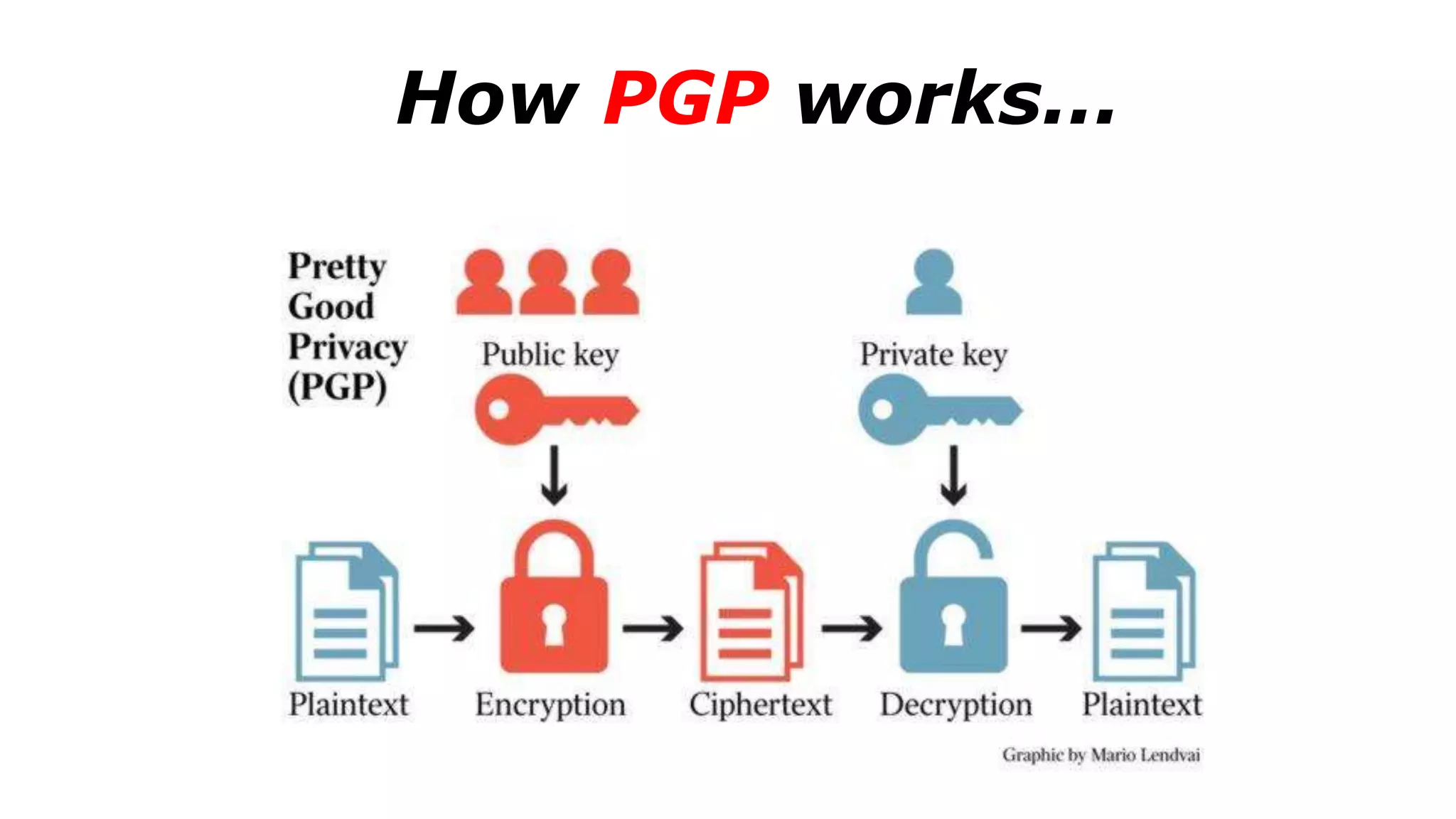
The document discusses a presentation on the erosion of privacy in the modern digital age, emphasizing that individuals willingly contribute personal information to companies, which then use that data for targeted marketing. It highlights that privacy concerns are more significantly influenced by consumer behavior and corporate data collection than by government surveillance. The speaker also provides insights into protective tools and practices for enhancing online privacy.