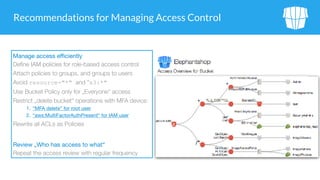
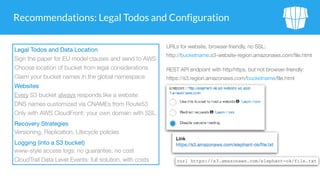
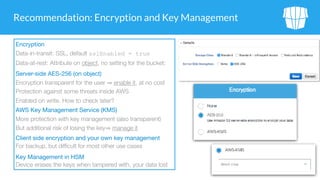
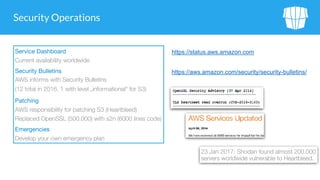
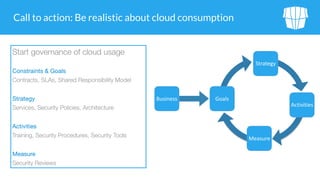
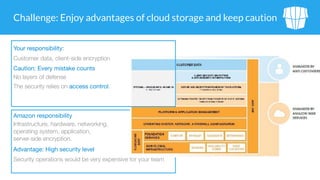
The document outlines security issues and management practices for using Amazon S3, emphasizing the shared responsibility model between AWS and its users. Key topics include access control frameworks, incident responses, and recommendations for maintaining data security and compliance. The document also addresses potential risks associated with S3 outages and provides strategies for efficient resource management and encryption.





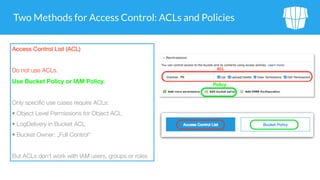
![Access Control with Policies
Policies
Policy is AWS’s universal access language
Bucket policy is the successor to ACLs
Syntax: JSON = Java Script Object Notation
Semantics: Policy Grammar
Specific actions (53) s3:GetObject, PutObject,
Construct by copy/paste or
build with AWS Policy Generator
{
"Version":"2012-10-17",
"Statement":[
{
"Sid":"AddPerm",
"Effect":"Allow",
"Principal": "*",
"Action":["s3:GetObject"]
"Resource":["arn:aws:s3:::example.com/*"]
}
]
}
From AWS reference:
Website on S3 with read access for everyone](https://image.slidesharecdn.com/schnedermanncsacee20170309-170812133025/85/Overview-of-Security-Issues-with-Amazon-S3-10-320.jpg)