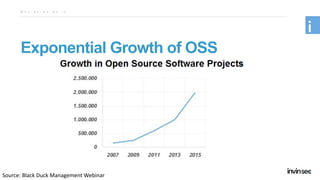
This document discusses whether open source software can be secure. It begins by defining open source software as software with publicly available source code and a license allowing anyone to study, change and distribute the software. It then notes that open source is collaborative in nature, with better ideas and faster bug fixing coming from more contributors. However, it also acknowledges that open source software can be insecure if vulnerable libraries are used or dependencies are not checked carefully. The document argues that open source and security are possible if security is a first-class concern, through following best practices like the OWASP Top 10, monitoring dependencies, and maintaining transparency around vulnerabilities and updates.