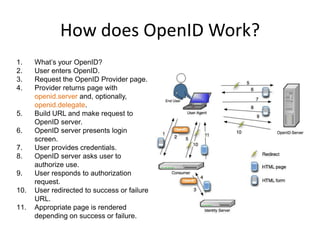
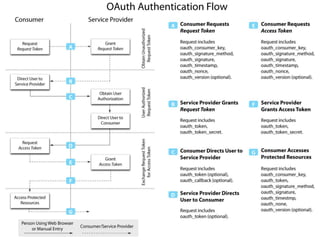
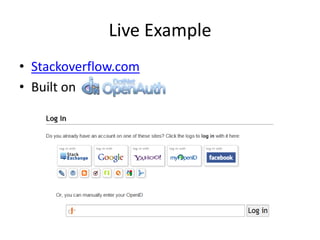
Open ID & OAuth allows users to verify their identity across multiple websites without needing separate logins for each site. OpenID handles user authentication by allowing users to log in with an OpenID username and password. OAuth authorizes third party applications to access user data without sharing the user's actual credentials. Many major websites use these standards, including Google, Facebook, and Twitter. The document provides code examples for implementing OpenID and OAuth authentication.