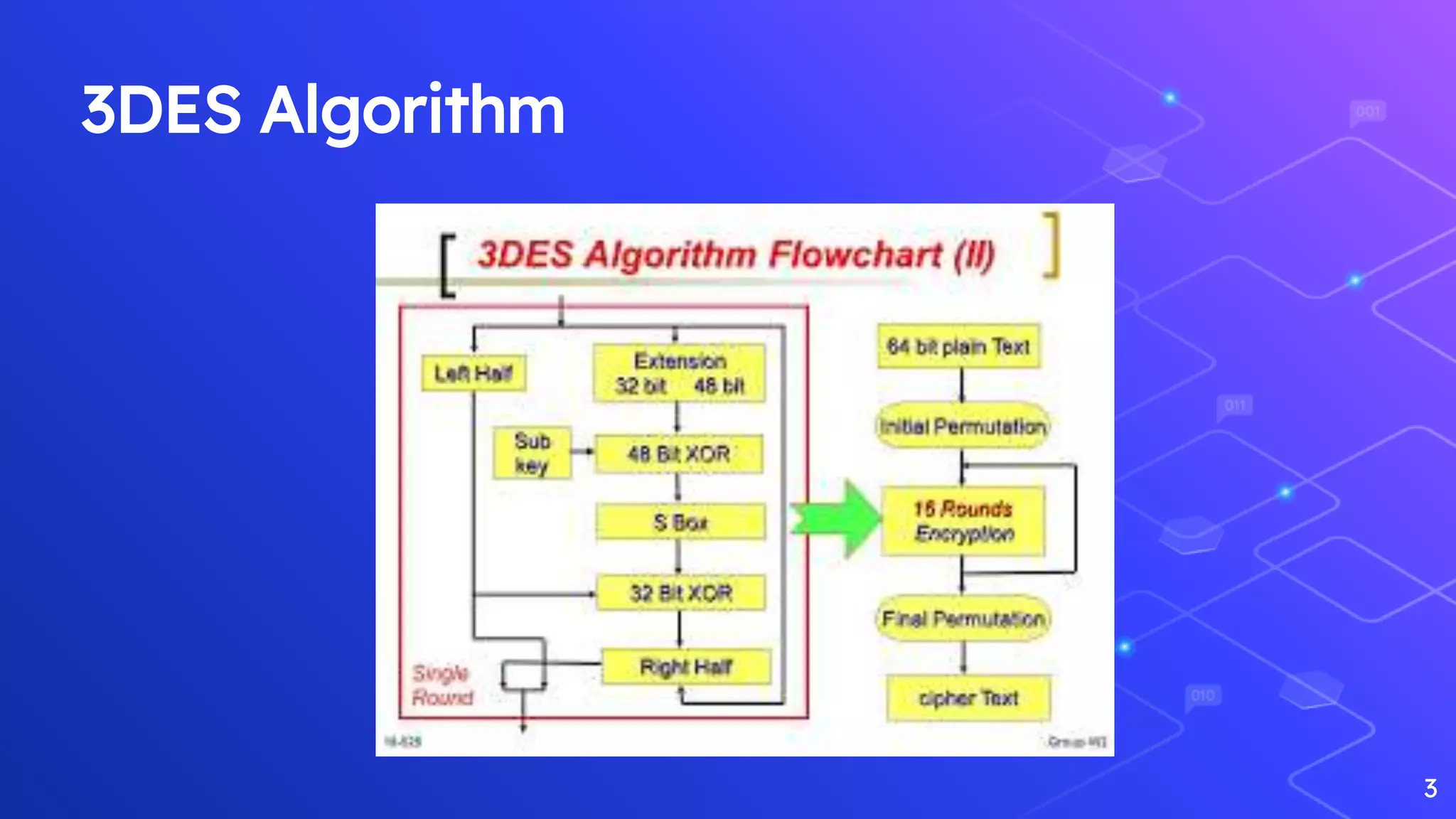
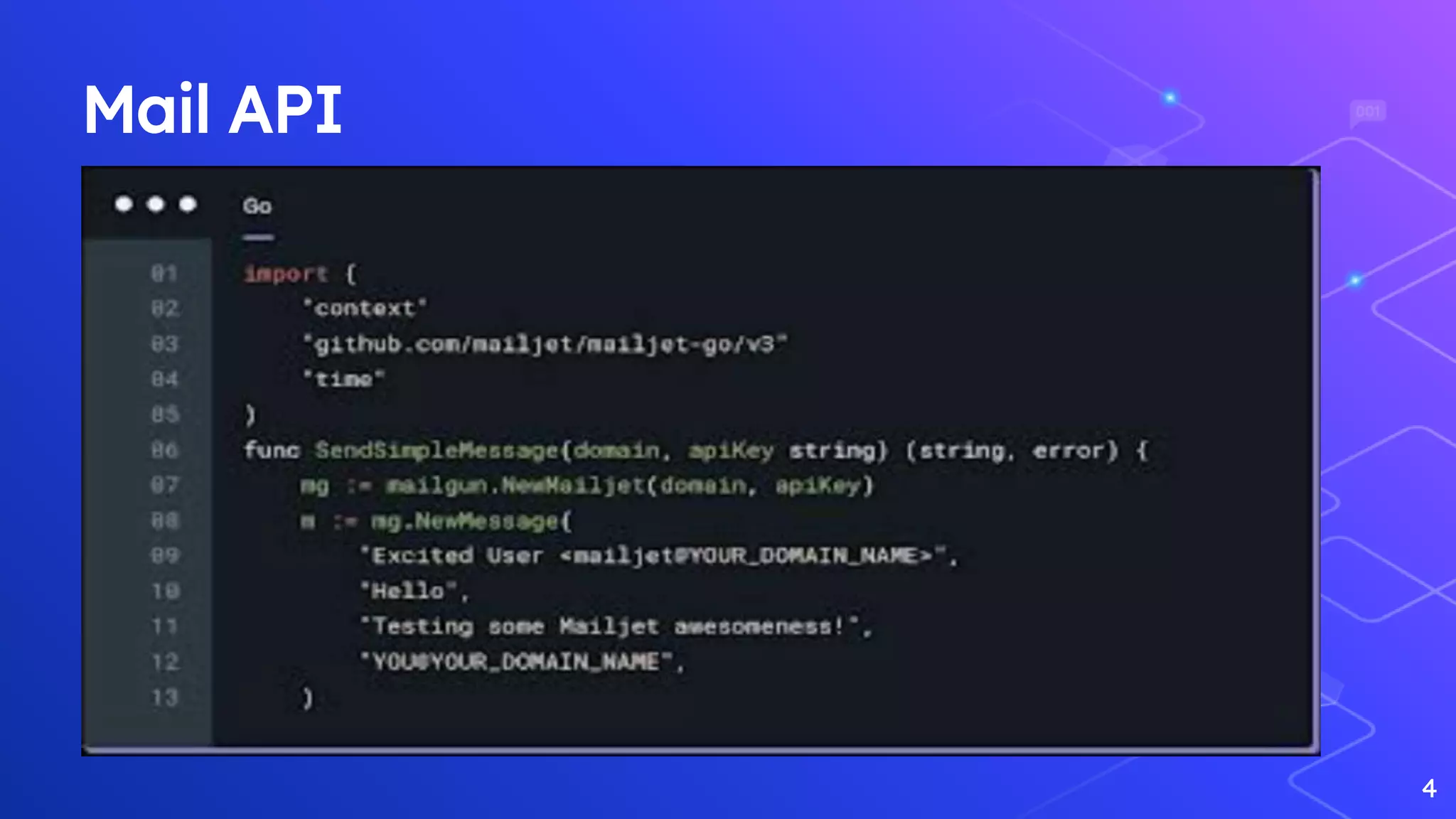
This document presents an online file storage system that uses RSA and 3DES encryption algorithms. It describes how files can be uploaded from a React client-side app to an Azure Storage blob using an Azure Storage SDK and shared access signature tokens. The document then references papers on RSA encryption and decryption as well as articles about Windows Azure storage services.