Phantom Virtualization Tap Plus RSA NetWitness Add Up to Exceptional Gains in Monitoring, Visibility, Cost-Savings and ROI
- 1. Technology Alliance Partner I Solution Brief Phantom Virtualization Tap Plus RSA NetWitness Add Up to Exceptional Gains in Monitoring, Visibility, Cost-Savings and ROI Net Optics and EMC-RSA The Challenge Solution Highlights Virtualization deployments can offer many great, cost-saving benefits, however it also creates new challenges when it comes to network security, compliance, and meeting regulations and SLAs. The introduction of vSwitches means that current physical monitoring tools, such as the EMC – RSA NetWitness™Investigator, cannot easily extend into the Intra-VM level within virtual hypervisors. The time may not yet be ideal for investment in new virtualization-specific tools and training, and the company may wish to continue leveraging such system resources as vCPU, vRAM, vNIC, storage and others. · Leverages current policies and tool previous existing NetWitness investment in converged environments to deliver full value The Solution The EMC-RSA and Net Optics joint solution leverages the scalability and powerful analytics of the NetWitness platform with the Phantom Virtualization Tap’s ability to deliver 100 percent visibility. In combination, they can protect sensitive data, maximize user experience, reduce mean time to resolution, and quickly—or even proactively— identify potential threats, • Captures data passing between virtual machines (VMs) and sends traffic of interest to virtual and physical monitoring tools of choice into your EMC RSA NetWitness • Supports all major hypervisors, including Xen, Oracle VM, vSphere 5, KVM, and Hyper-V. vSphere 4.X and 5.X, Microsoft Hyper-V 2012, Xen, Oracle VM, KVM, and Parallels 6.0 • Achieves pervasive visibility and obtain situational awareness into the content of all network traffic and discrete behavior of entities operating across the network. This solution offers users knowledge and confidence that their virtual data centers attain • Detects advanced threats including insider threats, zero-day exploits and targeted malware, advanced full visibility of their intra-VM (“east-west”) traffic. The Phantom Virtualization Tap is a persistent threats, fraud, espionage, data exfiltration, VMsafe, kernel module that lets customers export traffic of interest from their virtual and continuous monitoring of security controls. machines to their existing RSA NetWitness Investigator appliance. This enables the RSA • Obtains actionable intelligence by performing NetWitness to receive encapsulated traffic of interest. It can then terminate the GRE real-time, free-form contextual analysis of network headers and fully inspect/audit the network packets in unaltered state to meet SLAs and and log data captured and reconstructed by the achieve regulatory compliance. NetWitness network security monitoring platform. The Net Optics Phantom Virtualization Tap contributes superior network traffic monitoring and access capabilities for virtualized computing environments. This Tap captures data passing between virtual machines (VMs) and sends traffic of interest to NetWitness. The Phantom Virtualization Tap supports all major hypervisors, including vSphere 4.x and 5.x, Microsoft Hyper-V 2012, Citrix XenServer, Oracle VM, KVM, and Parallels 6.0. Deep visibility of packet-level data makes for smooth management of virtual network security, compliance, and performance. Because the Phantom Virtualization Tap bridges virtual-to-physical in converged environments, a customer can leverage current policies and physical monitoring tools to derive their full invested values. In addition, the Phantom Virtualization Tap can replicate all traffic within the virtual switch, apply smart TapFlow™ filtering, and send only traffic of interest to the RSA NetWitness appliance. Sending only relevant traffic for monitoring optimizes NetWitness performance with no risk of oversubscription. Instead, NetWitness can reserve CPU and memory resources to perform patented methods for decapsulating protocols and applications. • Enhances the ability to keep pace with changing environments • Drives unparalleled performance, scalability and low latency • Increases security operations center agility
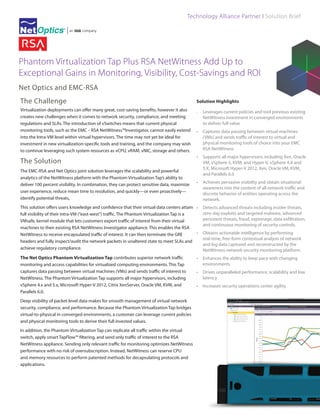
- 2. Technology Alliance Partner I Solution Brief Phantom Virtualization Tap Plus RSA NetWitness Add Up to Exceptional Gains in Monitoring, Visibility, Cost-Savings and ROI Hypervisor V Switch Phantom™ vm 1 vm 2 vm 3 Virtualization Tap Hypervisor Phantom™ Virtualization Tap Hypervisor V Switch Phantom™ Virtualization Tap V Switch Hypervisor V Switch Switch EMC RSA Netwitness The Phantom tap is deployed in any number of virtual environments to capture inter-vm (east west) traffic. That encapsulated traffic is then sent to the RSA NEtwitness which decapsulates the GRE header. This traffic can now be inspected by the for complete security in virtual environment. Net Optics RSA Net Optics is the leading provider of Total Application and Network Visibility solutions that deliver real-time network intelligence for peak performance in network monitoring and security. As a result, businesses achieve the scalable end-to-end visibility they need to optimize network performance of physical, virtual and private cloud environments, and remote branch offices. More than 7,500 enterprises, service providers and government organizations—including 85 percent of the Fortune 100—trust Net Optics’ comprehensive plug and play family of application-aware NPM, Network Packet Broker, Virtual/Cloud and Visibility Management System (VMS) solutions to deliver immediate results and quick time to value through an easy-to-use interface. Net Optics maintains a global presence through leading OEM partner and reseller networks. RSA, the security division of EMC, is the premier provider of security, risk and compliance management solutions for business acceleration. RSA helps the world’s leading organizations solve their most complex and sensitive security challenges. These challenges include managing organizational risk, safeguarding mobile access and collaboration, proving compliance and securing virtual and cloud environments. Combining business-critical controls in identity assurance, encryption & key management. SIEM, Data Loss Prevention, Continuous Network Monitoring, and Fraud Protection with industry-leading eGRC capabilities and robust consulting services, RSA brings visibility and trust to millions of user identities, the transactions that they perform and the data that is generated. For more information please visit www.RSA.com and www.EMC.com. 5303 Betsy Ross Drive Santa Clara, CA 95054, United States Main: +1 (408) 737-7777 www.netoptics.com KVM vm 1 vm 2 vm 3 Phantom™ Virtualization Tap V Switch ORACLE XEN With its customizable user interface and advanced analytics, RSA NetWitness allows users to perform free-form contextual analysis of their raw network data for complete situational awareness. The RSA NetWitness platform offers a scalable, distributed infrastructure with real-time fusion of global threat intelligence that adapts to changing operational requirements. The RSA NetWitness deploys a modular-capacity architecture, via direct-attached capacity or SAN, that adapts to customer security and data-retention demands. vm 1 vm 2 vm 3 Phantom™ Virtualization Tap Hypervisor HYPER-V RSA NetWitness is a revolutionary network security monitoring platform that provides enterprises with situational awareness of everything happening on the network to solve a wide range of information-security challenges. When you need clarity and definitive answers to the most challenging questions, this product delivers a level of fine-grained detail—plus the agility to quickly, efficiently examine network and application layer sessions in am easily comprehensible way. vm 1 vm 2 vm 3 ESX vm 1 vm 2 vm 3 Now, analysis that previously took days, now takes only minutes to perform. Users can easily conduct automated and interactive analysis of complex security problems now that they able to fully gain 100% visibility of environment—physical and virtual— with extensive network and application layer filtering (e.g., MAC, IP, User, Keywords) 174 Middlesex Turnpike Bedford, MA 01730, United States Main: +1 (571) 392-6000 www.rsa.com Net Optics® is a registered trademark of Net Optics, an Ixia company. Copyright 1996-2013 Net Optics, an Ixia company. All rights reserved. Additional company and product names may be trademarks or registered trademarks of the individual companies and are respectfully acknowledged. RSA and the RSA logo are trademarks or registered trademarks of RSA, Inc. in the United States and other countries.