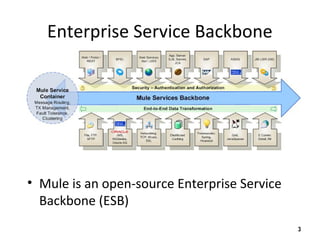
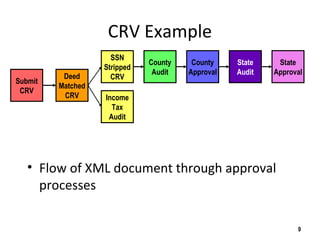
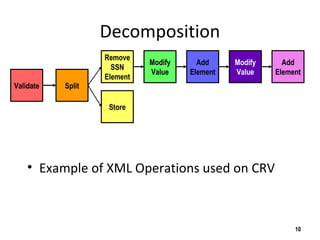
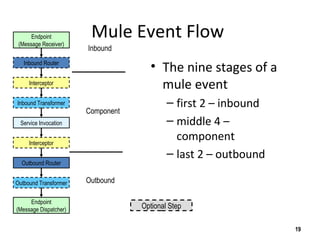
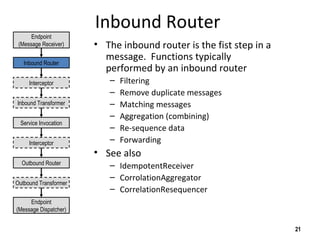
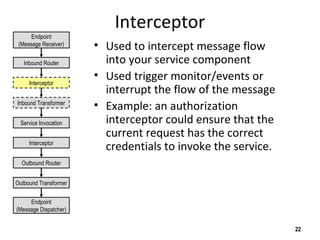
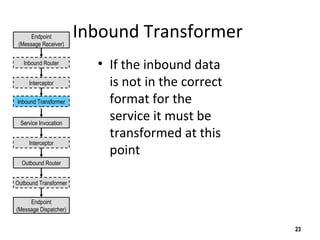
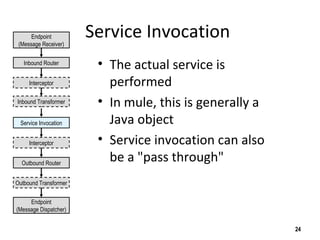
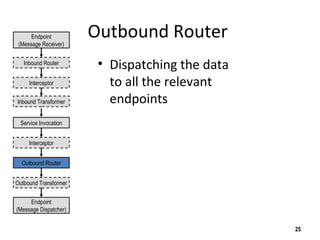
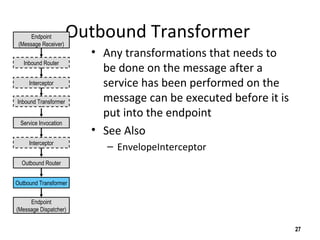
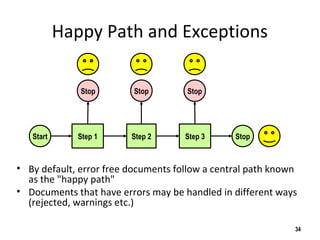
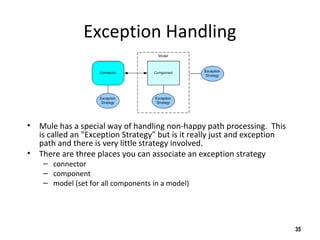
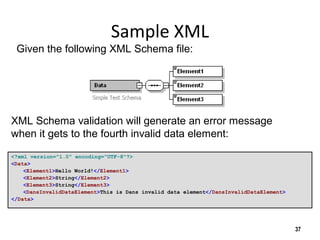
The document discusses the open-source enterprise service bus Mule, including what Mule is, its core concepts like the universal message object and endpoints, and how Mule uses technologies like staged event-driven architecture and non-blocking I/O to move data between different systems and formats in a flexible way. It also provides examples of using Mule to move XML files between directories and handling exceptions.













![Keeping the Name The Same
<outbound-router>
<router
className="org.mule.routing.outbound.OutboundPassThroughRouter">
<endpoint
address=
"file:///c:/mule-class/out?outputPattern=$[ORIGINALNAME]"
/>
</router>
</outbound-router>
33
Add the outputPattern parameter to keep the output
name the same as the input.](https://image.slidesharecdn.com/mule-overview-151001082037-lva1-app6891/85/Mule-overview-33-320.jpg)

![Validating against an XML Schema
<outbound-router>
<router className="org.mule.routing.outbound.FilteringXmlMessageSplitter">
<endpoint
address="file:///c:/mule-class/out?outputPattern=$[ORIGINALNAME]"/>
<properties>
<property name="validateSchema" value="true"/>
<property name="externalSchemaLocation"
value="file:///c:/mule-class/labs/07-validate/my-
schema.xsd"/>
</properties>
</router>
</outbound-router>
38
To validate the XML Schema, just add two properties:
1) tell it to validate the document
2) tell it what file to use and where to find it](https://image.slidesharecdn.com/mule-overview-151001082037-lva1-app6891/85/Mule-overview-38-320.jpg)