Embed presentation
Downloaded 20 times



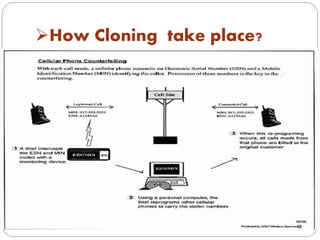




This document discusses mobile phone cloning, including how it works by capturing and cloning a phone's SIM/IMEI pair using scanning devices, and then reprogramming the phone's microchips. It notes that cloned phones can be detected through methods like duplicate detection, velocity traps, radio frequency monitoring, checking PIN codes, and usage profiling. While cloned phones can benefit users if their original phone is lost or damaged, the document also explains cloning has disadvantages like enabling illegal money transfers and use by terrorists for criminal activities.








