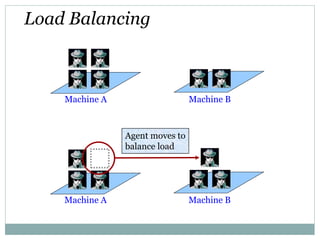
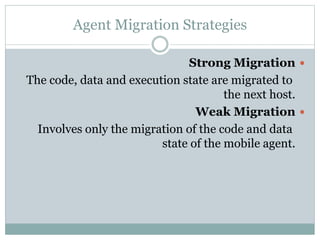
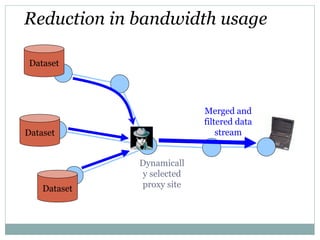
This document presents an overview of mobile agents. It defines a mobile agent as an object capable of autonomously migrating from one host to another in a distributed system to perform actions on behalf of its creator. The document outlines the life cycle of a mobile agent, which includes creation, dispatch, cloning, deactivation, activation, retraction, and disposal. It also discusses agent migration strategies, properties, applications, advantages and disadvantages of using mobile agents, including security risks.

















![Reduction in latency
Sumatra chat server
[RASS97]
1. Observe
high average
latency to
clients
2. Move to
better location
2 to 4 times
smaller latency
in trial runs](https://image.slidesharecdn.com/newmicrosoftpowerpointpresentation-161227144737/85/Mobile-Agents-20-320.jpg)