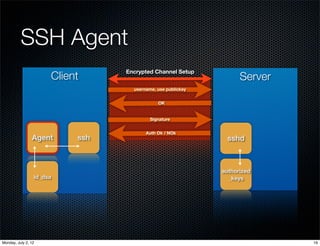
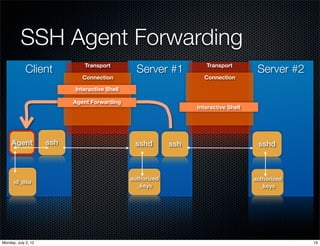
The document discusses various SSH features and tips for penetration testers and system administrators, emphasizing secure communications and user authentication methods. It covers session multiplexing, public key authentication, and the use of SSH agent forwarding while highlighting potential vulnerabilities associated with compromised servers. The authors provide practical advice on safely managing SSH keys and configurations to enhance security.