The document is a dissertation submitted by Mahato Lipika for the degree of Master of Science in Computer Control and Automation in 2016. It discusses leak location detection in gas pipeline networks. Chapter 1 introduces the background of gas pipeline networks in Singapore and the motivation for leak detection. The objective is to analyze pressure profile data using different methods to locate leaks in the network. Chapter 2 reviews literature on gas pipeline networks, leak detection techniques, and computational fluid dynamics modeling. Chapter 3 describes initial calculations, experiments conducted to collect pressure profile data from a test network setup under different leak conditions. Chapter 4 presents results of analyzing the data using various methods to locate leaks. Chapter 5 provides conclusions and suggestions for future work.








![1
Chapter 1
Introduction
In this chapter, the background and motivation for this project is presented. It also
describes the project scope and objective of the thesis followed by the organisation of
this work.
1.1 Background
At present there are two gas systems in Singapore: the natural gas system and the
manufactured town gas system. Town gas is produced and supplied to over 500,000
domestic, commercial and industrial consumers. Also there are two broad networks
of gas pipelines. Transmission line, carrying gas from coastal area to regional area
has high pressure whereas the distribution line, carrying gas from regional area to
customers which has medium or low pressure. Singapore itself has 180 km of high
pressure transmission line and 2900 km of underground distribution line.
Since 1992, Singapore has been importing natural gas from Malaysia. The second
source of natural gas is West Natuna, Indonesia. Singapore has been using it since
January 2001 and is available for reticulation for users comprising power stations
and large industrial customers. The third source of natural gas is Sumatra, Indonesia.
Singapore has been importing from there since end 2003[1].
Natural gas from the Grissik gas field in South Sumatra is transported to
Singapore/Indonesia border via Batam through 480km of high pressure pipelines.
More than 200 km of these pipelines are submarine pipelines maintained by
Indonesian government. The gas flows another 9km from the international border of
submarine pipelines to arrive at the Sakra Natural Gas Station on Jurong Island.
These pipelines are maintained by SP PowerGrid, Singapore. In order to link the](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-9-320.jpg)
![2
natural gas receiving facilities at the Sakra Natural Gas Station to the existing
transmission network on the mainland, the twin 11 km transmission pipelines were
built from Sakra on Jurong Island to Jurong Pier on the mainland. An additional 7.5
km extension was also constructed from Jurong Pier to Toh Tuck [2].
The production and distribution of town gas is the main business of City Gas in
Singapore. City Gas is the key retailer of natural gas and town gas to industrial and
commercial customers. Town gas is supplied to most residential households across
the Island. The consumption of gas has rapidly increased in the last few decades.
City gas is an ISO 9001 certified company which has been supplying town gas to
almost all the people dwelling across Singapore in private houses, condominiums
and new Housing Development Board estates. It also meets the demands of industrial
and commercial firms such, restaurants, hawker centres, hotels, laundries, electronics
and printing, hospitals, etc. It provides very high satisfactory services to all its
customers. Some of these facilities include 24-hour customer service, safe and
reliable gas supply, 24*7 maintenance, regular safety inspections, gas appliance
servicing and consultancy services [1].
City Gas in collaboration with Power Gas Limited, supplies town gas and natural gas
to its clients through the underground gas transmission and distribution networks. SP
Power Grid is a member of Singapore Power Group which manages Singapore’s gas
transmission and distribution networks of more than 2,900 km [3]. The entire
network is mostly underground except where the pipes enter into buildings or cross
over canals. The network operates at a three-pressure regime
high-pressure transmission at 28 / 40 barg
medium-pressure distribution at 3 barg
low-pressure distribution at 50 / 20 / 2KPa [4]
Customers whose premises are located within these networks may request for the
setup required for the supply of town gas or natural gas subject to the availability of](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-10-320.jpg)
![3
gas and technical /financial viability in that region. The supply pressure for low
pressure retail consumers ranges from 10mbars to 20mbars for town gas and
15mbars to 25mbars for natural gas at the gas service isolation valve. The gas
retailer, transporter and the consumer can demand for higher gas supply pressure
which can be met depending upon the availability and feasibility of the gas subjected
to a legal agreement between the two parties [1].
Leakage of gas in the pipelines can cause hazardous effects on the environment and
can be fatal for human life. Manual detection and rectification is very operational
intensive with huge man power requirement and time consumption.
1.2 Motivation
The efficiency of the transportation of gas can cause an influence to the domestic
economy of Singapore. The pipeline network is the most economic, cost efficient and
safest mode of transportation of natural gas. Gas leakage causes financial loses as
well as major accidents. Due to the underground infrastructure of the network of
pipeline, the manual detection of leak is very complex.
The broader project focuses on developing reliable leak detection techniques and
hence the project is organized into three sub-projects. Multi-sensor anomaly
detection is followed by location identification and advanced data analytics-based on
predictive maintenance. To detect the problems in the pipeline, dominant signature
parameters like the temperature, flow rate and pressure are monitored using
distributed temperature sensor (DTS), flow transmitter and pressure transmitter
respectively. For assessing third party damage, RFID traceability sensors are useful.
Therefore, complementary parameters are proposed using multiple sensors,
providing accurate physical measurement, carrying the signature of the problems.
Using the physical parameters, RFID traceability information and historical data as
well as advanced data analytics would be performed for location identification.
Analytics would be extended to predictive maintenance to identify future failure-
prone zones.](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-11-320.jpg)


![6
Chapter 2
Literature Review
In this section, a brief overview and background on modelling and complex network
analysis in gas distribution system is provided. It also provides a literature review on
the recent developments in leak detection techniques to understand the relative
importance of this research work.
2.1 The gas pipeline network
The gas network is a widely distributed system of pipelines to carry natural gas from
the source to the customer line. It also provides engineering services and facilities for
them.
Gas flows from the high pressure gas network from the gas trunk line through a gas
transmission station, into the medium and low pressure gas distribution network
through gas distribution points. These external pipelines are underground, above
ground or overhead pipelines laid outside of a building. Figure 1 shows the overall
transportation system of natural gas from coastal areas to consumers [5].](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-14-320.jpg)
![7
Figure 1: Gas transportation system, source IEEE
2.2 Leak Detection Techniques
Different methods to detect the leak have been broadly classified into three, namely
biological, hardware based and software based techniques [7]. On bases of human
intervention, the detection methods are classified into manual detection semi-
automated and automated detection [7]. Experienced and trained dogs can be used to
detect leaks by odour, sound or visual inspection. Manual detection is direct method
by patrolling along the pipeline with hand hold devices. For large network these
techniques are uneconomical, labour and time intense. Because this method is
inefficient, it is hardly preferred.
The other two efficient techniques are Hardware and Software techniques.](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-15-320.jpg)

![9
2.2.1.1 Acoustic Leak detection
The method is based on the principle that when a leak if occurred it will produce
acoustic noise. The sensors installed outside the pipe track will detect the noise and
generate the threshold with features. If the features vary from the threshold, alarm is
activated. The received signal is strong where the leak occurred and detecting it
involves cross- correlation.
Acoustic sensors are artificial neural networks based computational systems used for
leak detection. According to Furness and van. Reet,2009[8], the data from the
sensors are filtered to extract 9 kHz, 5 kHz and 1 kHz frequencies. The input to the
neural network is the dynamic of these noises. The network is trained both in non -
leak and leak conditions in stationary and transient steady. The study was efficient
for short pipelines up to 100 metres. This method is good for leak localization and
also estimating leak’s size. However high background or flow noise generated by
pump, valve or vehicle can cover the actual signal from the leak. This is also
comparatively an expensive technique [9].
2.2.1.2 Fibre optic sensors
The fibre optic cables are laid all over the pipelines. The principle of working is
Raman Effect or Optical Time Domain Reflectometry(OTDR). When the gas is
leaked and touches the fibre cable, temperature of the cable changes due to the
contact. Leak is detected by measuring the temperature change [10]. There are two
frequency shifted component: The Stokes and Anti – Stokes component. The
amplitude of Stoke‘s component is not affected by temperature but Anti –Stokes
amplitude varies drastically with temperature. Filtering methods are applied to
separate the two. The problem with the method is the backscattered light is of low
magnitude. It works well only for a range of 10km.
Brilloin scattering occurs because of the interaction between thermally acoustic
waves and propagation optical signals which lead to frequency shifted components
thus carrying strain and temperature information [11].](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-17-320.jpg)
![10
Figure 3: Raman - Rayleigh technique, source Bernett C Carter’s paper [11]
Figure 3 shows the spectrum of the scattered light in optical fibre for a single
wavelength demonstrating the Raman and Brillouin based methods. Raman
technique changes the back scattering intensity. Since Brillouin has no intensity
based system, it does not suffer any sensitivity to drifts and hence is more stable and
accurate.
Main advantage of fibre optic is its insensitiveness to electromagnetic interference.
However, this does not work for buried pipelines. Moreover, its highly cost effective
and has limited wide range applications for gas pipeline monitoring.
2.2.1.3 Vapour or liquid sensing tubes:
The leak detection technique by this method involves installation of these tubes all
over the pipelines. During the occurrence of the leak, the contents of the pipe gets in
contact with the tube. The concentration distribution is measured by forcing a
column of air into the tube with constant speed. Gas sensors are placed at the end of
each tube. The size of the leak is indicated by the peak in gas concentration caused
by every increase in gas concentration.](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-18-320.jpg)
![11
Figure 4: Liquid sensing technique, source Comini’s journal [12]
Figure 4 defines the technique of liquid sensing tubes. The electrolytic cell placed at
the detecting line constantly diffuses test gas into the tube. When the test gas passes
through the detector an end peak is produced which indicates the whole length of the
sensor tube [12]. Localization of the leak is nothing but the inverse ratio of leak peak
arrival to end peak arrival,
Although the method is very simple and appropriate for underground pipelines,
applying it to huge network is cost effective. Moreover, speed of detection of leak is
very low.
2.2.1.4 Liquid Sensing Cables.
In these cables energy pulses are sent out constantly throughout the length. As the
energy pulses travels, the reflected energy are stored in memory. The electrical
properties will be altered by the presence of liquids in the sensor which will wet the](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-19-320.jpg)
![12
cable if sufficiently present [13]. The alteration is used to determine the leak. This
method works well for short pipelines.
2.2.1.5 Soil Monitoring:
This method uses a tracer inside the pipeline [14]. Tracers are nothing but
inexpensive non-hazardous gas. The tracer is featured as a volatile gas which get
released at the exact location of the leak. By monitoring the soil above the pipeline,
the presence of leak can be localised. By this method, false alarm is very low and
small leaks can be detected easily. However, the method is expensive as tracer has to
be injected in the pipe which is not possible for uncovered pipelines.
Hardware based methods like acoustic, optical, cable sensor etc are less reliable
because they are noise sensitive
2.2.2 Software Based Systems
The project uses software techniques. The pipeline parameters like pressure, flow
and temperature are closely monitored. Some of these techniques are discussed
below.
2.2.2.1 Mass- Volume balance
This method has the principle of conservation of mass. Leak is determined by the
difference between the upstream and downstream flow [15]. This method is widely
used in oil pipelines The main drawback is that by this method the actual position of
the leak is unknown., hence, other methods are applied after the mass balance
method to localise the leak position soon after the leak is detected [19].](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-20-320.jpg)
![13
2.2.2.2 Real time transient modelling
This method of leak detection uses pipe flow models which are constructed by using
equations of conservation of mass, momentum and energy. The difference between
the measured and the estimated value is used to determine the leak. Billman and
Isermann[16] ,used this approach for leak detection and localization. In the study for
single leak, an algorithm for determining the leak location and finite estimation of
leak flow is developed. This method is very efficient because it can not only detect
the position of the leak accurately but also locate leaks as small as 1 percent of flow
[17]. However, the method is cost effective as it deals with huge data processing in
real.
2.2.2.3 Negative pressure wave
This method locates the leak by finding out the time difference taken by the negative
waves to arrive at the pressure sensors installed at the start and end of the pipeline.
These negative waves are nothing but pressure waves that are generated due to leaks
which cause sudden pressure drops which propagates with certain speed towards
both downstream and upstream in the pipeline. According to H. Chen, H. Ye. L.
Chen and H. Su [18] study, support vector machine learning is used to analyse the
pressure sensor data and locate the location of the leak. A nonlinear classifier is
trained using supervised learning to automatically detect the presence of leak in the
pressure curve. This study would locate small and slow leak out of noise. The
negative pressure wave along with signal processing technique is studies by Li yo bi.
By this method, the reported time delay is 2 minutes and the estimated error is 2%.
2.2.2.4 Pressure point analysis method
This method is based on the fact that pressure drops because of leak. It detects leak
by comparing the on running statistical trend and the current pressure value. By the
statistical analysis, the mean value of the pressure measurement of the new data and
the old data is compared. If the mean of the old data is larger than the mean of the](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-21-320.jpg)
![14
current data, the leak alarm is triggered [20]. This method is installation inexpensive
and can accurately identify the occurrence of leak. However false alarm is triggered
at times because pressure drop is not unique to leak occurrence.
2.2.2.5 Statistical Method
This method is implemented to reduce the rate of false alarm. This method is suitable
for oil pipeline systems. It uses advance statistical analysis to study the flow rate,
temperature and pressure values of a pipeline [21]. This method continuously
monitors for changes in the pipeline and relocation of pressure /flow instruments,
hence this method is an approximation for complex networks of pipeline. Detection
of 0.5% leaks was reported by Zhang and Mauro ‘s study [22].
2.2.26 Digital signal processing
The method compares the response to a known input over a period of time with the
measurements taken at later time and based on their wavelet transform or coefficient
frequency response, leak alarm is triggered [23]. The disadvantage of this method is
that, leak cannot be detected unless the size of the leak is not considerably large.
Hardware based leak detection methods are cost effective in terms of installation and
maintenance like service and repair. On the other hand, software based techniques
deal with implementation of algorithms to continuously monitor flow rate,
temperature and pressure of other pipeline parameters based on future study.
Software method is more popular because it is cost efficient.
The most common softwares used are COMSOL and Open foam. COMSOL is widely
used and encouraged because it works on the principle of finite element method.](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-22-320.jpg)
![15
2.3 Computational Fluid dynamics
CFD is a branch of fluid mechanics that solves fluid flow problems by using
algorithm based techniques. Turbulent or transonic flow requires high speed
computers that provide better solutions. The interaction between the liquids /gases
with surfaces defined by boundary conditions is performed by high speed computers
that simulate this interaction between them [24]. The Navier –Stokes equation is the
fundamental of all CFD problems.
ꝭ (
𝒅𝒖
𝒅𝒕
+ 𝒖. 𝛁𝒖)= -𝛁p+ F
The above equation holds true for incompressible Newtonian Fluid whose Mac
number is less than 0.3
p is the fluid pressure,
ꝭ is the fluid density, and
u is the fluid velocity and f is the sum of the inertial forces pressure forces and
viscous forces [25].
The finite element method (FEM) is a numerical method for finding approximate
solutions to boundary value problems for partial differential equations. The domain
of the problem is divided into a collection of sub domains, each sub domain
represented by a set of equations. Finally, these set of element equations are
recombined into a global system of equations for the final calculations [24].
The COMSOL software was introduced in 1986 that uses Finite element analysis
method, solver and Software packages for engineering and mathematical problems.
The partial differential equations are directly fed into the coupled systems to solve
problems related to different modules. Amongst the different modules available in
COMSOL, the pipe flow for both steady state and transient study of the town gas
mixture [26] is focussed as it satisfies the conditions of the type of fluid to be
analysed in this project.](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-23-320.jpg)
![16
Pipe Flow Module
The module is used in pipe systems in the oil and gas industry and chemical
processes. It is used for simulating flow in incompressible fluids in pipes and also
compressible hydraulic transients. The simulations provide velocity, temperature and
pressure variations in pipes. The physics uses the conservation of energy, momentum
and mass [26].
The pressure, flow and concentration across the cross sections of the pipe are
modelled as cross section averaged quantities varying along the length of the pipe
lines. The friction factors describe the pressure losses that occur along the length of
the pipe by the friction factor expressions. There is frictional pressure loss along the
pipe due to momentum change because of T joints, bends and valves. A broad range
of Darcy Friction factors cover the entire range from non-Newtonian and Newtonians
fluids, turbulent to laminar flow, geometries of different cross section and surfaces
with range of relative roughness values [26].
The module has 7 physics amongst which the following are of utmost utility.
Pipe Flow: It simulates velocity and pressure fields in isothermal pipelines.
Heat Transfer in Pipes: It computes the mass balance equation including the wall
heat transfer to the surroundings
Transport of Diluted Species in Pipes: It simulates the mass balance equation in
order to compute the dispersion, diffusion and convection of the solute in terms of
the concentration distribution.](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-24-320.jpg)
![17
Chapter 3
Initial calculation and experiments for Data Collection
3.1 Calculation of dynamic viscosity and density of the gas mixture
The dynamic viscosity and the density of the gas mixture is evaluated by the
composition details provided by of the town gas data sheet handed over by the
Singapore Power Limited [1] is as follows
Components Low Range High Range
Hydrogen 41 65
Methane 4 33
Ethane 0 2.6
Propane 0 1.3
Butane 0 1.7
Pentane 0 5
Carbon Monoxide 2 6
Carbon Dioxide 9 20
Nitrogen 2 10
Oxygen 0.5 2.5
Assumption: The dynamic viscosity of the gas mixture is found out by considering
the low range of the components of the gas mixture. Below formula is used for
calculating the dynamic viscosity
µga=
∑ 𝑦𝑖µ𝑖√𝑀𝑔𝑖𝑁
𝑖=1
∑ 𝑦𝑖√𝑀𝑔𝑖𝑁
𝑖=1
where
µga= Dynamic viscosity of gas mixture.
yi = Mole fraction of the ith component of the gas mixture.
µi = Dynamic viscosity of ith component of the gas mixture.
Mgi = Molecular weight of ith component of the gas mixture[27].](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-25-320.jpg)












![32
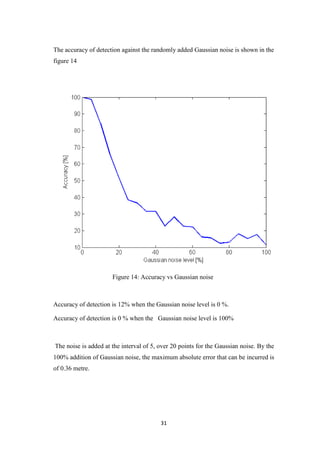
The standard deviation is calculated at an interval of 5 over 20 points by adding
hundred Gaussian noise and output is showed as in figure 15.
Figure 15: Error bar for mean square method
4.1.2 Knn Approach
K nearest neighbour is a simple algorithm that classifies different cases based on
distance function. Distance can be Euclidean, Manhattan or Minkowski distance. A
case is classified by the majority votes given by the neighbours with the case being
assigned to the class which is most common among its k nearest neighbours.
Following are the steps that are taken to calculate MAE using knn method.
Gaussian noise level [%]
Meanabsoluteerror[m]](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-40-320.jpg)

![34
Table 3: MSE values for k=1 to k=5 for Gaussian noise levels
Figure 16: Error bar for Knn Method
Gaussian Noise level [%]
Meanabsoluteerror[m]](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-42-320.jpg)




![40
Chapter 5
Conclusion and future work
5.1 Conclusion
The detection of leak is a very critical problem for the whole underground gas
network in Singapore. Currently implemented methods are cost and labour intensive.
To ensure reliability, real time monitoring of the network is demanded and hence the
project comes into the picture [28].
The conclusion can be drawn from the results as seen in section 3.3 in chapter 3 and
chapter 4. In this thesis, it is verified how the leak location is affected by the position
of the inlet source. It is also found out how the pressure at a point varies when there
is a leak condition and no leak condition which would help to build predictive
maintenance models, so that it could avoid leaks to facilitate better localisation
system. It is observed that nearer the leak to the source inlet better is its detection.
It is also clearly observed that the effect of the noise tend to decrease the accuracy of
detection of leak in the pipelines. Also the different methods of analysis like mean
square and k nearest neighbour is studied and how the Gaussian noise affect the
mean absolute error is depicted through graphs. The standard deviation on addition
of hundred random Gaussian noises can be clearly observed through the graphs.
More the noise more is the deviation and hence more is the mean absolute error.
It has also been clearly shown that the leak pipe can be located accurately by the
good spacing between the pipelines shown by the multi dimensional spacing graph
for multiple inlet values.
By performing different analysis, it can be clearly demonstrated how the noise
percentage impacts the detection of leak. Hence the observation can be incorporated
in the advance predictive models in order to avoid leakages in pipeline networks.](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-48-320.jpg)

![42
Appendix
1.Reference code for mean square method
close all;
clear all;
clc;
res_1 = [];
res_2 = [];
xx=100*[0:0.05:1];
%the same with LOO without and with noise
for i=1:21
noise_level = i*0.05-0.05;
clear aa bb;
for j=1:100
[aa,bb]=skrypt_LOO_std(noise_level, j);
%with noise
res_2(i,j) = mean(abs(bb(:,3)-bb(:,4))); %mean absolute error of the leak location
end
end
res_3(:,1) = mean(res_2');
res_3(:,2) = std(res_2');
figure(1);
errorbar(xx,res_3(:,1),res_3(:,2),'LineWidth',1.5);
function [odp_1, odp_2] = skrypt_LOO(noise_level,r_seed);
%close all;
%clear all;
%clc;
%noise_level = 0.05;
rng(r_seed);
load pipedata;
clear p p_err loc locloc;
p=[p1,p2,p3,p4];
loc=[loc1,loc2,loc3,loc4];
locloc(1:99)=1;
locloc(100:198)=2;
locloc(199:207)=3;
locloc(208:216)=4;
p_err = zeros(216,216);](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-50-320.jpg)
![43
%%for clean data
for i=1:216
for j=1:216
p_err(i,j)=sum((p(:,i)-p(:,j)).^2)/2200;
if(i==j)
p_err(i,j)=inf;
end
end
end
clear tmp1 tmp2;
for i=1:216
[tmp1(i),tmp2(i)]=min(p_err(i,:));
end
clear odp_1;
tmp_acc = [1:216];
odp_1 = [tmp_acc',tmp2',loc(tmp2)',loc',locloc(tmp2)',locloc'];
%%for data with noise
clear p_noise;
for i=1:216
clear tmp_noise;
tmp_noise = noise_level*(max(p(:,i))-min(p(:,i)))*randn(2200,1);
p_noise(:,i)=p(:,i)+tmp_noise;
end
clear p_noise_err;
for i=1:216
for j=1:216
p_noise_err(i,j)=sum((p_noise(:,i)-p(:,j)).^2)/2200;
if(i==j)
p_noise_err(i,j)=inf;
end
end
end
clear tmp1_noise tmp2_noise;
for i=1:216
[tmp1_noise(i),tmp2_noise(i)]=min(p_noise_err(i,:));
end
clear tmp_acc_noise acc_2 odp_2;
tmp_acc_noise = [1:216];
odp_2 = [tmp_acc_noise',tmp2_noise',loc(tmp2_noise)',loc',locloc(tmp2_noise)',locloc'];
2. Reference code for knn method
close all;
clear all;
clc;
res_21 = [];
res_22 = [];
res_23 = [];
res_24 = [];](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-51-320.jpg)
![44
res_25 = [];
xx=100*[0:0.05:1];
K_max = 5;
%the same with LOO without and with noise
%for j=1:K_max %K parameter
for i=1:21
noise_level = i*0.05-0.05;
clear a;
for h=1:100
clear a;
a=skrypt_LOO_knn_std(noise_level,1,h);
res_21(i,h) = mean(abs(a(:,1)-a(:,2)));
clear a;
a=skrypt_LOO_knn_std(noise_level,2,h);
res_22(i,h) = mean(abs(a(:,1)-a(:,2)));
clear a;
a=skrypt_LOO_knn_std(noise_level,3,h);
res_23(i,h) = mean(abs(a(:,1)-a(:,2)));
clear a;
a=skrypt_LOO_knn_std(noise_level,4,h);
res_24(i,h) = mean(abs(a(:,1)-a(:,2)));
clear a;
a=skrypt_LOO_knn_std(noise_level,5,h);
res_25(i,h) = mean(abs(a(:,1)-a(:,2)));
end
end
%end
%%%%%%%%%%%%%%%%%%%
res_31(:,1) = mean(res_21');
res_31(:,2) = std(res_21');
res_32(:,1) = mean(res_22');
res_32(:,2) = std(res_22');
res_33(:,1) = mean(res_23');
res_33(:,2) = std(res_23');
res_34(:,1) = mean(res_24');
res_34(:,2) = std(res_24');
res_35(:,1) = mean(res_25');
res_35(:,2) = std(res_25');
color_list = ['r' 'g' 'b' 'k' 'm' 'c' 'y'];
figure(1);
hold on;
clear legend_txt;
legend_txt = {};
errorbar(xx,res_31(:,1),res_31(:,2),'LineWidth',1.5,'Color',color_list(1));
errorbar(xx,res_32(:,1),res_32(:,2),'LineWidth',1.5,'Color',color_list(2));
errorbar(xx,res_33(:,1),res_33(:,2),'LineWidth',1.5,'Color',color_list(3));
errorbar(xx,res_34(:,1),res_34(:,2),'LineWidth',1.5,'Color',color_list(4));
errorbar(xx,res_35(:,1),res_35(:,2),'LineWidth',1.5,'Color',color_list(5));
legend_txt{1} = strcat('K=',num2str(1));
legend_txt{2} = strcat('K=',num2str(2));
legend_txt{3} = strcat('K=',num2str(3));](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-52-320.jpg)
![45
legend_txt{4} = strcat('K=',num2str(4));
legend_txt{5} = strcat('K=',num2str(5));
box on;
xlabel('Gaussian noise level [%]');
ylabel('Mean absolute error [m]');
legend(legend_txt,'Location','NorthWest');
%Table_2: WITH_LOO; first column - noise_level, then MAE for K=1...K_max
[xx',mean(res_21')',mean(res_22')',mean(res_23')',mean(res_24')',mean(res_25')']
unction [loc_err] = skrypt_LOO_knn_std(noise_level,K,r_seed);
%close all;
%clear all;
%clc;
%noise_level = 0.05;
rng(r_seed);
load pipedata;
clear p p_err loc locloc loc_err pred_loc;
p=[p1,p2,p3,p4];
loc=[loc1,loc2,loc3,loc4];
locloc(1:99)=1;
locloc(100:198)=2;
locloc(199:207)=3;
locloc(208:216)=4;
%%for data with noise
clear p_noise;
for i=1:216
clear tmp_noise;
tmp_noise = noise_level*(max(p(:,i))-min(p(:,i)))*randn(2200,1);
p_noise(:,i)=p(:,i)+tmp_noise;
end
for i=1:216
clear idx_knn idx_data loc_tmp;
idx_data = [1:216];
idx_data = idx_data(find(idx_data~=i));
loc_tmp = loc(idx_data);
idx_knn=knnsearch(p(:,idx_data)',p_noise(:,i)','K',K);
pred_loc(i) = mean(loc_tmp(idx_knn));
end
loc_err = [loc',pred_loc'];
3. Reference Code for classification methods
close all;](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-53-320.jpg)
![46
clear all;
clc;
res_1 = [];
res_2 = [];
xx=100*[0:0.05:1];
%just after adding the noise; NO LOO!
%for i=1:21
% i
% noise_level = i*0.05-0.05;
% clear a;
% a=skrypt_classification(noise_level);
% res_1(i) = mean(abs(a(:,1)-a(:,2))); %mean absolute error of the leak location
%end
%the same with LOO without and with noise
for i=1:21
i
noise_level = i*0.05-0.05;
for j=1:10
clear a;
a=skrypt_LOO_classification_std(noise_level,j);
res_2(i,j) = mean(abs(a(:,1)-a(:,2)));
end
end
res_3(:,1) = mean(res_2');
res_3(:,2) = std(res_2');
color_list = ['r' 'g' 'b' 'k' 'm' 'c' 'y'];
figure(1);
hold on;
clear legend_txt;
legend_txt = {};
errorbar(xx,res_3(:,1),res_3(:,2),'LineWidth',1.5,'Color',color_list(3));
box on;
xlabel('Gaussian noise level [%]');
ylabel('Mean absolute error [m]');
%noise_level, MAE
[xx',mean(res_2')']
function [loc_err] = skrypt_LOO_classification_std(noise_level,r_seed);
%close all;
%clear all;
%clc;
%noise_level = 0.05;
rng(r_seed);](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-54-320.jpg)
![47
load pipedata;
clear p p_err loc locloc loc_err pred_loc;
p=[p1,p2,p3,p4];
loc=[loc1,loc2,loc3,loc4];
locloc(1:99)=1;
locloc(100:198)=2;
locloc(199:207)=3;
locloc(208:216)=4;
% STANDARDIZATION
p=zscore(p);
%%for data with noise
clear p_noise;
for i=1:216
clear tmp_noise;
tmp_noise = noise_level*(max(p(:,i))-min(p(:,i)))*randn(2200,1);
p_noise(:,i)=p(:,i)+tmp_noise;
end
for i=1:216
clear m1 m2 m3 m4 idx_data locloc_tmp;
idx_data = [1:216];
idx_data = idx_data(find(idx_data~=i));
loc_tmp = loc(idx_data);
locloc_tmp = locloc(idx_data);
p_tmp=p(:,idx_data);
clear c1 c2 c3 c4;
c1=find(locloc_tmp==1);
c2=find(locloc_tmp==2);
c3=find(locloc_tmp==3);
c4=find(locloc_tmp==4);
%NEURAL NETWORKS
%m1=feedforwardnet(10); %number of neural neurons in hidden layer
%m1.trainParam.showWindow = 0;
%m1 = train(m1,p_tmp(:,c1),loc_tmp(c1));
%m2=feedforwardnet(10);
%m2.trainParam.showWindow = 0;
%m2 = train(m2,p_tmp(:,c2),loc_tmp(c2));
%m3=feedforwardnet(10);
%m3.trainParam.showWindow = 0;
%m3 = train(m3,p_tmp(:,c3),loc_tmp(c3));
%m4=feedforwardnet(10);
%m4.trainParam.showWindow = 0;
%m4 = train(m4,p_tmp(:,c4),loc_tmp(c4));
%NONLINEAR REGRESSION
%m1=fitnlm(p_tmp(:,c1)',loc_tmp(c1)');
%m2=fitnlm(p_tmp(:,c2)',loc_tmp(c2)');
%m3=fitnlm(p_tmp(:,c3)',loc_tmp(c3)');
%m4=fitnlm(p_tmp(:,c4)',loc_tmp(c4)');
%LINEAR REGRESSION
%m1=fitlm(p_tmp(:,c1)',loc_tmp(c1)','quadratic');
%m2=fitlm(p_tmp(:,c2)',loc_tmp(c2)','quadratic');
%m3=fitlm(p_tmp(:,c3)',loc_tmp(c3)','quadratic');
%m4=fitlm(p_tmp(:,c4)',loc_tmp(c4)','quadratic');](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-55-320.jpg)
![48
%LINEAR REGRESSION
m1=fitlm(p_tmp(:,c1)',loc_tmp(c1)');
m2=fitlm(p_tmp(:,c2)',loc_tmp(c2)');
m3=fitlm(p_tmp(:,c3)',loc_tmp(c3)');
m4=fitlm(p_tmp(:,c4)',loc_tmp(c4)');
%SVR
%m1=svmtrain(loc_tmp(c1)',p_tmp(:,c1)','-s 3');
%m2=svmtrain(loc_tmp(c2)',p_tmp(:,c2)','-s 3');
%m3=svmtrain(loc_tmp(c3)',p_tmp(:,c3)','-s 3');
%m4=svmtrain(loc_tmp(c4)',p_tmp(:,c4)','-s 3');
%CART
%m1=fitrtree(p_tmp(:,c1)',loc_tmp(c1));
%m2=fitrtree(p_tmp(:,c2)',loc_tmp(c2));
%m3=fitrtree(p_tmp(:,c3)',loc_tmp(c3));
%m4=fitrtree(p_tmp(:,c4)',loc_tmp(c4));
if(locloc(i)==1)
%SVR
%pred_loc(i)=svmpredict(loc(i),p_noise(:,i)',m1);
pred_loc(i)=predict(m1,p_noise(:,i)');
%NEURAL NETWORKS
%pred_loc(i)=net(m1,p_noise(:,i));
end
if(locloc(i)==2)
%SVR
%pred_loc(i)=svmpredict(loc(i),p_noise(:,i)',m2);
pred_loc(i)=predict(m2,p_noise(:,i)');
%NEURAL NETWORKS
%pred_loc(i)=net(m2,p_noise(:,i));
end
if(locloc(i)==3)
%SVR
%pred_loc(i)=svmpredict(loc(i),p_noise(:,i)',m3);
pred_loc(i)=predict(m3,p_noise(:,i)');
%NEURAL NETWORKS
%pred_loc(i)=net(m3,p_noise(:,i));
end
if(locloc(i)==4)
%SVR
%pred_loc(i)=svmpredict(loc(i),p_noise(:,i)',m4);
pred_loc(i)=predict(m4,p_noise(:,i)');
%NEURAL NETWORKS
%pred_loc(i)=net(m4,p_noise(:,i));
end
end
loc_err = [loc',pred_loc'];
4. Reference code for multiple input values close all;
clear all;
clc;
p = [];
clear d;
d=xlsread('data_inlets (#MAHATO LIPIKA#).xlsx',1);
p1_1 = d(2:end,4:6);
clear d;](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-56-320.jpg)

![50
p4_5 = d(2:end,4:6);
%pressure; pipe; inlet; location
p = [p;p1_1(:,1),repmat(1,size(p1_1,1),1),repmat(1,size(p1_1,1),1),repmat(1,size(p1_1,1),1)];
p = [p;p1_1(:,2),repmat(1,size(p1_1,1),1),repmat(1,size(p1_1,1),1),repmat(2,size(p1_1,1),1)];
p = [p;p1_1(:,3),repmat(1,size(p1_1,1),1),repmat(1,size(p1_1,1),1),repmat(3,size(p1_1,1),1)];
p = [p;p1_2(:,1),repmat(1,size(p1_2,1),1),repmat(2,size(p1_2,1),1),repmat(1,size(p1_2,1),1)];
p = [p;p1_2(:,2),repmat(1,size(p1_2,1),1),repmat(2,size(p1_2,1),1),repmat(2,size(p1_2,1),1)];
p = [p;p1_2(:,3),repmat(1,size(p1_2,1),1),repmat(2,size(p1_2,1),1),repmat(3,size(p1_2,1),1)];
p = [p;p1_3(:,1),repmat(1,size(p1_3,1),1),repmat(3,size(p1_3,1),1),repmat(1,size(p1_3,1),1)];
p = [p;p1_3(:,2),repmat(1,size(p1_3,1),1),repmat(3,size(p1_3,1),1),repmat(2,size(p1_3,1),1)];
p = [p;p1_3(:,3),repmat(1,size(p1_3,1),1),repmat(3,size(p1_3,1),1),repmat(3,size(p1_3,1),1)];
p = [p;p1_4(:,1),repmat(1,size(p1_4,1),1),repmat(4,size(p1_4,1),1),repmat(1,size(p1_4,1),1)];
p = [p;p1_4(:,2),repmat(1,size(p1_4,1),1),repmat(4,size(p1_4,1),1),repmat(2,size(p1_4,1),1)];
p = [p;p1_4(:,3),repmat(1,size(p1_4,1),1),repmat(4,size(p1_4,1),1),repmat(3,size(p1_4,1),1)];
p = [p;p1_5(:,1),repmat(1,size(p1_5,1),1),repmat(5,size(p1_5,1),1),repmat(1,size(p1_5,1),1)];
p = [p;p1_5(:,2),repmat(1,size(p1_5,1),1),repmat(5,size(p1_5,1),1),repmat(2,size(p1_5,1),1)];
p = [p;p1_5(:,3),repmat(1,size(p1_5,1),1),repmat(5,size(p1_5,1),1),repmat(3,size(p1_5,1),1)];
p = [p;p2_1(:,1),repmat(2,size(p2_1,1),1),repmat(1,size(p2_1,1),1),repmat(1,size(p2_1,1),1)];
p = [p;p2_1(:,2),repmat(2,size(p2_1,1),1),repmat(1,size(p2_1,1),1),repmat(2,size(p2_1,1),1)];
p = [p;p2_1(:,3),repmat(2,size(p2_1,1),1),repmat(1,size(p2_1,1),1),repmat(3,size(p2_1,1),1)];
p = [p;p2_2(:,1),repmat(2,size(p2_2,1),1),repmat(2,size(p2_2,1),1),repmat(1,size(p2_2,1),1)];
p = [p;p2_2(:,2),repmat(2,size(p2_2,1),1),repmat(2,size(p2_2,1),1),repmat(2,size(p2_2,1),1)];
p = [p;p2_2(:,3),repmat(2,size(p2_2,1),1),repmat(2,size(p2_2,1),1),repmat(3,size(p2_2,1),1)];
p = [p;p2_3(:,1),repmat(2,size(p2_3,1),1),repmat(3,size(p2_3,1),1),repmat(1,size(p2_3,1),1)];
p = [p;p2_3(:,2),repmat(2,size(p2_3,1),1),repmat(3,size(p2_3,1),1),repmat(2,size(p2_3,1),1)];
p = [p;p2_3(:,3),repmat(2,size(p2_3,1),1),repmat(3,size(p2_3,1),1),repmat(3,size(p2_3,1),1)];
p = [p;p2_4(:,1),repmat(2,size(p2_4,1),1),repmat(4,size(p2_4,1),1),repmat(1,size(p2_4,1),1)];
p = [p;p2_4(:,2),repmat(2,size(p2_4,1),1),repmat(4,size(p2_4,1),1),repmat(2,size(p2_4,1),1)];
p = [p;p2_4(:,3),repmat(2,size(p2_4,1),1),repmat(4,size(p2_4,1),1),repmat(3,size(p2_4,1),1)];
p = [p;p2_5(:,1),repmat(2,size(p2_5,1),1),repmat(5,size(p2_5,1),1),repmat(1,size(p2_5,1),1)];
p = [p;p2_5(:,2),repmat(2,size(p2_5,1),1),repmat(5,size(p2_5,1),1),repmat(2,size(p2_5,1),1)];
p = [p;p2_5(:,3),repmat(2,size(p2_5,1),1),repmat(5,size(p2_5,1),1),repmat(3,size(p2_5,1),1)];
p = [p;p3_1(:,1),repmat(3,size(p3_1,1),1),repmat(1,size(p3_1,1),1),repmat(1,size(p3_1,1),1)];
p = [p;p3_1(:,2),repmat(3,size(p3_1,1),1),repmat(1,size(p3_1,1),1),repmat(2,size(p3_1,1),1)];
p = [p;p3_1(:,3),repmat(3,size(p3_1,1),1),repmat(1,size(p3_1,1),1),repmat(3,size(p3_1,1),1)];
p = [p;p3_2(:,1),repmat(3,size(p3_2,1),1),repmat(2,size(p3_2,1),1),repmat(1,size(p3_2,1),1)];
p = [p;p3_2(:,2),repmat(3,size(p3_2,1),1),repmat(2,size(p3_2,1),1),repmat(2,size(p3_2,1),1)];
p = [p;p3_2(:,3),repmat(3,size(p3_2,1),1),repmat(2,size(p3_2,1),1),repmat(3,size(p3_2,1),1)];
p = [p;p3_3(:,1),repmat(3,size(p3_3,1),1),repmat(3,size(p3_3,1),1),repmat(1,size(p3_3,1),1)];
p = [p;p3_3(:,2),repmat(3,size(p3_3,1),1),repmat(3,size(p3_3,1),1),repmat(2,size(p3_3,1),1)];
p = [p;p3_3(:,3),repmat(3,size(p3_3,1),1),repmat(3,size(p3_3,1),1),repmat(3,size(p3_3,1),1)];
p = [p;p3_4(:,1),repmat(3,size(p3_4,1),1),repmat(4,size(p3_4,1),1),repmat(1,size(p3_4,1),1)];
p = [p;p3_4(:,2),repmat(3,size(p3_4,1),1),repmat(4,size(p3_4,1),1),repmat(2,size(p3_4,1),1)];
p = [p;p3_4(:,3),repmat(3,size(p3_4,1),1),repmat(4,size(p3_4,1),1),repmat(3,size(p3_4,1),1)];
p = [p;p3_5(:,1),repmat(3,size(p3_5,1),1),repmat(5,size(p3_5,1),1),repmat(1,size(p3_5,1),1)];
p = [p;p3_5(:,2),repmat(3,size(p3_5,1),1),repmat(5,size(p3_5,1),1),repmat(2,size(p3_5,1),1)];
p = [p;p3_5(:,3),repmat(3,size(p3_5,1),1),repmat(5,size(p3_5,1),1),repmat(3,size(p3_5,1),1)];
p = [p;p4_1(:,1),repmat(4,size(p4_1,1),1),repmat(1,size(p4_1,1),1),repmat(1,size(p4_1,1),1)];
p = [p;p4_1(:,2),repmat(4,size(p4_1,1),1),repmat(1,size(p4_1,1),1),repmat(2,size(p4_1,1),1)];
p = [p;p4_1(:,3),repmat(4,size(p4_1,1),1),repmat(1,size(p4_1,1),1),repmat(3,size(p4_1,1),1)];
p = [p;p4_2(:,1),repmat(4,size(p4_2,1),1),repmat(2,size(p4_2,1),1),repmat(1,size(p4_2,1),1)];
p = [p;p4_2(:,2),repmat(4,size(p4_2,1),1),repmat(2,size(p4_2,1),1),repmat(2,size(p4_2,1),1)];
p = [p;p4_2(:,3),repmat(4,size(p4_2,1),1),repmat(2,size(p4_2,1),1),repmat(3,size(p4_2,1),1)];
p = [p;p4_3(:,1),repmat(4,size(p4_3,1),1),repmat(3,size(p4_3,1),1),repmat(1,size(p4_3,1),1)];](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-58-320.jpg)
![51
p = [p;p4_3(:,2),repmat(4,size(p4_3,1),1),repmat(3,size(p4_3,1),1),repmat(2,size(p4_3,1),1)];
p = [p;p4_3(:,3),repmat(4,size(p4_3,1),1),repmat(3,size(p4_3,1),1),repmat(3,size(p4_3,1),1)];
p = [p;p4_4(:,1),repmat(4,size(p4_4,1),1),repmat(4,size(p4_4,1),1),repmat(1,size(p4_4,1),1)];
p = [p;p4_4(:,2),repmat(4,size(p4_4,1),1),repmat(4,size(p4_4,1),1),repmat(2,size(p4_4,1),1)];
p = [p;p4_4(:,3),repmat(4,size(p4_4,1),1),repmat(4,size(p4_4,1),1),repmat(3,size(p4_4,1),1)];
p = [p;p4_5(:,1),repmat(4,size(p4_5,1),1),repmat(5,size(p4_5,1),1),repmat(1,size(p4_5,1),1)];
p = [p;p4_5(:,2),repmat(4,size(p4_5,1),1),repmat(5,size(p4_5,1),1),repmat(2,size(p4_5,1),1)];
p = [p;p4_5(:,3),repmat(4,size(p4_5,1),1),repmat(5,size(p4_5,1),1),repmat(3,size(p4_5,1),1)];
pp=[p1_1,p1_2,p1_3,p1_4,p1_5,p2_1,p2_2,p2_3,p2_4,p2_5,p3_1,p3_2,p3_3,p3_4,p3_5,p4_1,p4_2,p
4_3,p4_4,p4_5];
%pipe; location; inlet;
pp_2=[
1,1,1;1,2,1;1,3,1;
1,1,2;1,2,2;1,3,2;
1,1,3;1,2,3;1,3,3;
1,1,4;1,2,4;1,3,4;
1,1,5;1,2,5;1,3,5;
2,1,1;2,2,1;2,3,1;
2,1,2;2,2,2;2,3,2;
2,1,3;2,2,3;2,3,3;
2,1,4;2,2,4;2,3,4;
2,1,5;2,2,5;2,3,5;
3,1,1;3,2,1;3,3,1;
3,1,2;3,2,2;3,3,2;
3,1,3;3,2,3;3,3,3;
3,1,4;3,2,4;3,3,4;
3,1,5;3,2,5;3,3,5;
4,1,1;4,2,1;4,3,1;
4,1,2;4,2,2;4,3,2;
4,1,3;4,2,3;4,3,3;
4,1,4;4,2,4;4,3,4;
4,1,5;4,2,5;4,3,5;
];](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-59-320.jpg)
![52
References
[1] “City Gas “2009(May)
[2] www.powergas.com.sg
[3] www.brightminds.com.sg
[4] (Szoplik, The Gas Transportation in a Pipeline Network)
[5] (Payal & Kar, 2016)advanced multisensor anamolymonitoring and analytics for
gas pipeline
[6]Murvay, Pal Stefan A survey on gas leak detection and localization tecniques
2012
[7] Zhao Yang, Mingliang Liu, Min Shao, Yingie Ji Research on Leakage Detection
and Analysis of Leakage Point in the Gas Pipeline System September 15, 2011
[8] Furness, R. A., van Reet, J., 2009. Pipeline leak detection techniques. In: E.W.,
M. (Ed.), Pipeline Rules of Thumb Handbook. Elsevier, pp. 606–614.
[9] Brodetsky, I., Savic, M., 1993. Leak monitoring system for gas pipelines. In:
Acoustics, Speech, and Signal Processing, 1993. ICASSP-93., 1993 IEEE
International Conference on. Vol. 3. IEEE, pp. 17–20.
[10] Weil, G., 1993. Non contract, remote sensing of buried water pipeline leaks
using infrared thermography. ASCE, New York, NY(USA)., 404–407.
[11] Bennett, C., Carter, M., Fields, D., 1995. Hyperspectral imaging in the infrared
using liftirs. In: Proceedings of SPIE. Vol. 2552. p. 274.
[12] Comini, E., Faglia, G., Sberveglieri, G., 2009. Solid state gas sensing. Springer
Verlag.
[13] Sandberg, C., Holmes, J., McCoy, K., Koppitsch, H., sep/oct 1989. The
application of a continuous leak detection system topipelines and associated
equipment. Industry Applications, IEEE Transactions on 25 (5), 906–909.](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-60-320.jpg)
![53
[14] Lowry, W., Dunn, S., Walsh, R., Merewether, D., Rao, D., March 2000. Method
and system to locate leaks in subsurface containment structures using tracer gases.
US Patent 6,035,701
[15] Parry, B., Mactaggart, R., Toerper, C., 1992. Compensated volume balance leak
detection on a batched LPG pipeline. In:Proceedings of the International Conference
on Offshore Mechanics and Arctic Engineering. American Society of Mechanical
Engineers, pp. 501–501
[16] Billmann, L., Isermann, R., 1987. Leak detection methods for pipelines.
Automatica 23 (3), 381–385.
[17] Scott, S., Barrufet, M., 2003. Worldwide Assessment of Industry Leak Detection
Capabilities for Single & Multiphase Pipelines.Tech. rep., Dept. of Petroleum
Engineering, Texas A&M University.
[18] Chen, H., Ye, H., Chen, L., Su, H., 2004. Application of support vector machine
learning to leak detection and location inpipelines. In: Instrumentation and
Measurement Technology Conference, 2004. IMTC 04. Proceedings of the 21st
IEEE.Vol. 3. IEEE, pp. 2273–2277.
[19] Liu, A. E., February 2008. Overview: Pipeline Accounting and Leak Detection
by Mass Balance, Theory and Hardware Implementation.
[20] Farmer, E., et al., 1989. A new approach to pipe line leak detection. Pipe Line
Industry;(USA) 70 (6), 23–27.
[21] Zhang, X., 1993. Statistical leak detection in gas and liquid pipelines. Pipes &
pipelines international 38 (4), 26–29.
[22] Zhang, J., Di Mauro, E., 1998. Implementing a Reliable Leak Detection System
on a Crude Oil Pipeline. In: Advances inPipeline Technology, Dubai, UAE.
[23] Golby, J., Woodward, T., 1999. Find that leak [digital signal processing
approach]. IEE review 45 (5), 219–221
[24]Book J anderson , E Dick, Computational Fluid Dynamics, 3rd
Edison.](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-61-320.jpg)
![54
[25] Online What is Navier Stoke’s Equation
[26]Book Comsol Multipysics User Guide version 4.3
[27]Time-dependent mathematical modelling of binary gas mixture in facilitated
transport membranes (FTMs): A real condition for single-reaction mechanism.
[28] R. Sugunakar Reddy, Gupta Payal, Pugalenthi Karkulali, Mishra Himanshu
Leak detection in low pressure gas pipeline using pressure and flow variation](https://image.slidesharecdn.com/6303acd1-529e-41e6-b050-232b1d239ddf-161124062302/85/Master-Thesis-62-320.jpg)