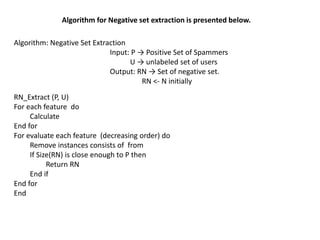
The document is a presentation on detecting fake user reviews. It discusses introducing the topic, reviewing literature on fake review detection, identifying problems with fake reviews, the proposed methodology, and future work. The methodology section discusses using features like star ratings, review similarity, content length and an Expectation Maximization algorithm to classify users as spammers or genuine. It compares results from using 6 features to an existing approach using more features, finding 49% of users were classified as spammers in the dataset. Future work could involve analyzing multiple websites to identify attacker patterns across different domains.







![Types of Review Spams
Basically three types of review spams exist[6]. These are:
Type 1 (Untruthful Review Spams): Fictitious positive reviews are rewarded to
products in order to promote them and also unreasonable negative reviews
are given to the competing products to harm their reputations among the
consumers.This is how untruthful reviews mislead the consumers into
believing their spam reviews.
Type 2 (Reviews with brand mentions): These spams have only brands as their prime
focus. They comment about the manufacturer or seller or the brand name
alone.These reviews are biased and can easily b figured out as they do not
talk about the product and rather only mention the brand names.
Type 3 (Non-reviews): These reviews are either junk, as in, have no relation with the
product or are purely used for advertisement purposes. They have these
two forms:
i. marketing purposes, and
ii. irrelevant text or reviews having random write-ups.](https://image.slidesharecdn.com/mahendranath-200204080557/85/Mahendra-nath-8-320.jpg)