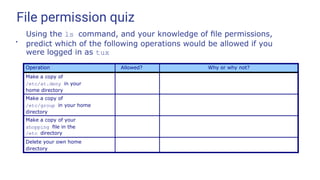
Here are the permissions for the given files/directories:
drwxr-xr-x 2 root root 4096 Apr 16 11:48 dir1
-rw-r--r-- 1 root root 0 Apr 16 11:48 file1
1. cp file1 dir1/file2
- This would be allowed. You have r permission on file1 and w permission on dir1 to create file2.
2. rm file1
- This would not be allowed. You do not have w permission on the directory containing file1.
3. ln file1 link
- This would not be allowed. You do not have w permission on the current directory to create the link.
4





















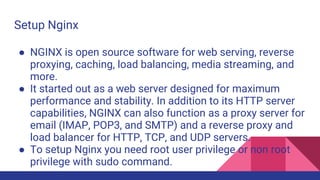
![Updating files with the touch command
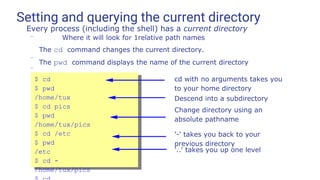
●
The command touch updates the access and modification
timestamps on a file to the current time
– Makes it appear that the file has just been modified
– If the file does not exist it is created with zero length
$ touch file1 file 2 ...
●
Options for touch include:
Option Meaning
-a Update only the access timestamp
-m Update only the modification timestamp
-r file Update the timestamps to match those of file, not the current time
-t time Update the timestamps to the specified time, in the format
[[CC]YY]MMDDhhmm[.ss]](https://image.slidesharecdn.com/linuxtraining3-220818134639-353dd21c/85/LinuxTraining_3-pptx-28-320.jpg)
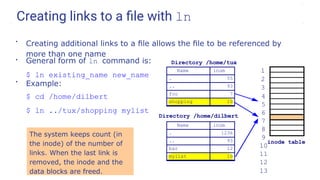



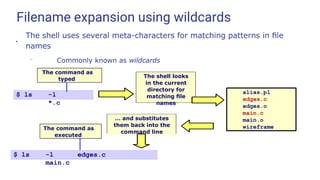
![Filename expansion using wildcards (continued)
* Matches zero or more characters
? Matches exactly one character
[ ] Matches any one of the enclosed characters, e.g. [AaTt]
[x-y] Matches any character in range
e.g. [a-m] [A-Z] [0-9]
●
Linux has no notion of filename “extensions”
– * matches all names, like *.* in DOS
Multiple wildcards can be used
– E.g. rm [A-Z]*.html
Wildcards can be used in multiple components of a pathname
– E.g. rm backups/*.199[7-9]/expenses??
●
●](https://image.slidesharecdn.com/linuxtraining3-220818134639-353dd21c/85/LinuxTraining_3-pptx-37-320.jpg)
![Wildcard quiz
410-chap1.doc
410-chap2.doc
410-chap3.doc
410-chap4.doc
410-chap5.doc
410-CHAPS.doc
display
display.c
display.h
display.object
ideas
ideas.old
ideas.older
index
intro
intro.old
meetings.June
meetings.July
meetings.Aug
oldstuff
opensource
openwindows
project6
project45
project46
project346
training
venues
windows
x-windows
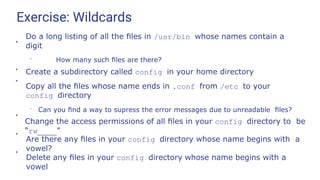
Given these files in the current directory What do these commands do?
A directory
rm *.old
ls -l 410-chap?.doc
less 410-chap[2-5].doc
mv ideas* training
mv ideas.* training
rm *old*
rm *
cp [v-z]* training
cp [a-z]* training
ls display.?
rm proj*6](https://image.slidesharecdn.com/linuxtraining3-220818134639-353dd21c/85/LinuxTraining_3-pptx-38-320.jpg)






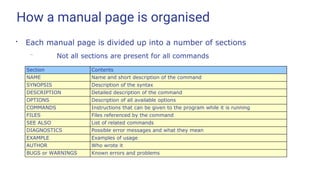
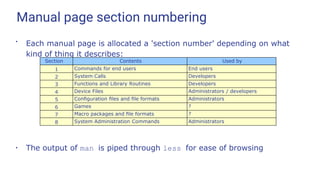
![Manual pages
●
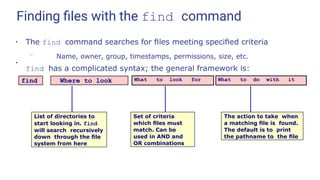
The traditional way of providing online help is the “manual page”
– accessed via the man command
tux@earth:~> man mount
MOUNT(8) Linux Programmer's Manual
MOUNT(8)
NAME
mount - mount a file system
SYNOPSIS
mount [-lhV]
mount -a [-fFnrsvw] [-t vfstype] [-O optlist] mount [-
fnrsvw] [-o options [,...]] device | dir
mount [-fnrsvw] [-t vfstype] [-o options] device dir
DESCRIPTION
All files accessible in a Unix system are arranged in one big tree,
the file hierarchy, rooted at /. These files can be spread out over
several devices. The mount command serves to attach the file system](https://image.slidesharecdn.com/linuxtraining3-220818134639-353dd21c/85/LinuxTraining_3-pptx-52-320.jpg)


![Built-in Help
●
Most of the GNU command line tools have built-in help, using the
--help option
tux@earth:~> cat --help Usage: cat
[OPTION] [FILE]...
Concatenate FILE(s), or standard input, to standard output.
-A, --show-all equivalent to -vET
-b,
-e
-E,
--number-nonblank
--show-ends
number nonblank output lines
equivalent to -vE
display $ at end of each line
-n, --number number all output lines
-s,
-t
-T,
-u
--squeeze-blank
--show-tabs
never more than one single blank line
equivalent to -vT
display TAB characters as ^I (ignored)
-v, --show-nonprinting
--help display
use ^ and M- notation, except for LFD and TAB
this help and exit
--version output version information and exit
With no FILE, or when FILE is -, read standard input.](https://image.slidesharecdn.com/linuxtraining3-220818134639-353dd21c/85/LinuxTraining_3-pptx-58-320.jpg)





![Disk management commands
Linux disk management includes several important tasks such as adding or removing storage devices, creating and
deleting partitions, mounting partitions on appropriate directories and making file system in partitions.
On Linux and Unix operating systems, you can use the df command to get a detailed report on the system’s disk space
usage.
● The general syntax for the df command is as follows:
○ # df [OPTIONS]... FILESYSTEM…
● Show Disk Space Usage in Human Readable Format
○ # df -h
● File System Types
○ # df -t
● To limit the output to file systems
○ # df -x filesystem](https://image.slidesharecdn.com/linuxtraining3-220818134639-353dd21c/85/LinuxTraining_3-pptx-74-320.jpg)