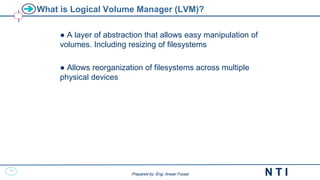
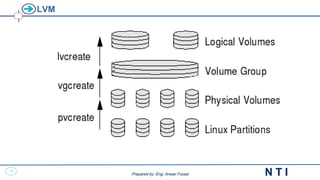
This document provides an overview of Linux backup and restore methods. It discusses the importance of regular backups to prevent data loss from hardware failures, crashes, or other issues. Common backup methods include full, partial, and incremental backups. Tools like tar and dump/restore can be used to archive and backup files and file systems to tape or other storage. The restore process mounts the file system and uses the restore command to recover files and directories from backups. Maintaining regular backups and being able to restore data is a crucial system administration task.






![8
N T I
Prepared by: Eng. Anwar Fouad
Prepared by: Eng. Anwar Fouad
Syntax Of Basic Commands
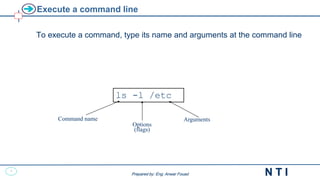
<command name> [<options>] [<arg1> <arg2> ... <arg n>]
Expressions between brackets [ ] are optional.
<options>: sequence of letters preceded by ‘-’ character.
each letter represents one option.
the order of the options has no importance.
<arg i>: string of characters
its meaning depends on the current command
(usually, they are file pathnames)
<command name>: command name
usually an executable filename.
Different command elements are delimited by at least one space
character.
Linux/Unix is case-sensitive.](https://image.slidesharecdn.com/linuxfundamentals-extra-231220104830-9df15013/85/Linux-Fundamentals-Extra-pdf-9-320.jpg)




![14
N T I
Prepared by: Eng. Anwar Fouad
Prepared by: Eng. Anwar Fouad
find
● find [directory...] [criteria...]
● Searches directory trees in real-time
Slower but more accurate than locate
CWD is used if no starting directory given
All files are matched if no criteria given
● May only search directories where the user has read and execute
permission](https://image.slidesharecdn.com/linuxfundamentals-extra-231220104830-9df15013/85/Linux-Fundamentals-Extra-pdf-15-320.jpg)














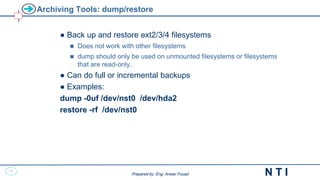


![37
N T I
Prepared by: Eng. Anwar Fouad
Prepared by: Eng. Anwar Fouad
Restoring File Systems
Command Format
restore options [ arguments ] [ filesystem ]
restore options [ arguments ] [ filenames . . . ]
Common Options
The following describes the some options for the restore command:
• t – Lists the table of contents of the backup media.
• r – Restores the entire file system from the backup media.
• x – Restores only the files named on the command line.
• i – Invokes an interactive restore.
• v – Specifies Verbose mode. Displays pathnames to the terminal
screen as each file is being restored.
• f – Specifies the tape device name.](https://image.slidesharecdn.com/linuxfundamentals-extra-231220104830-9df15013/85/Linux-Fundamentals-Extra-pdf-38-320.jpg)
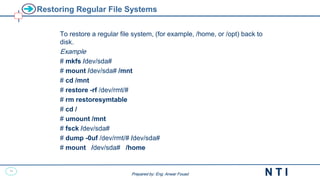
![39
N T I
Prepared by: Eng. Anwar Fouad
Prepared by: Eng. Anwar Fouad
Command: at
at -f script [m] <arg_hour> [<arg_date>] [+arg_increment>]
Executes a command file at a given date
<arg_temps> : hh:mm | now | noon | midnight
<arg_date> : <month> <day> or today | tomorrow
<arg_increment> : <number> minutes | hours | days | weeks | months
$ at -f myscript.sh 17:30 mar 22 2014 +2 hours
job 24 at 2014-03-22 19:30
at –l / atq : list the number of registered commands
at -d / atrm : cancels a registered command
Authorized users (respectively non-authorized users ) to use
this command are declared in a system file at.allow
(respectively at.deny).](https://image.slidesharecdn.com/linuxfundamentals-extra-231220104830-9df15013/85/Linux-Fundamentals-Extra-pdf-40-320.jpg)