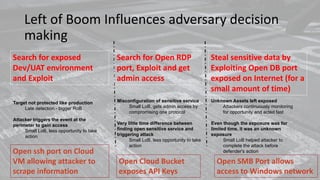
The document discusses the concept of 'left of boom,' a strategic framework in cybersecurity that emphasizes proactive measures to prevent cyber attacks before they occur, akin to military strategies for disrupting threats. It explores how adversaries exploit vulnerabilities quickly and emphasizes the importance of continuous monitoring, testing, and understanding attacker behavior to strengthen defenses. The approach aims to shift the mindset of defenders to anticipate and mitigate attacks effectively before the critical incident ('boom') happens.