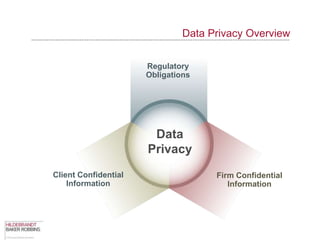
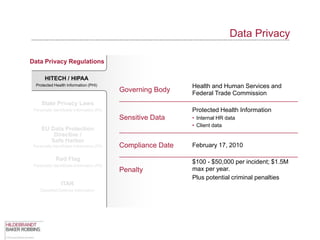
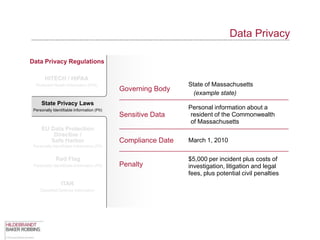
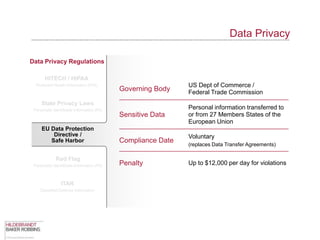
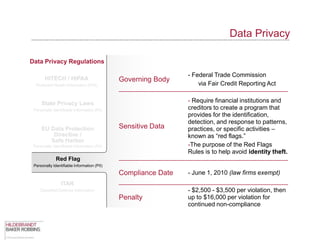
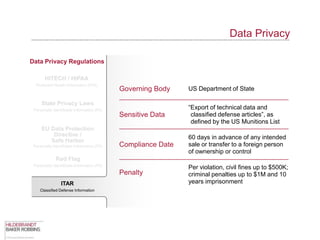
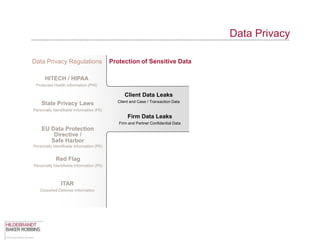
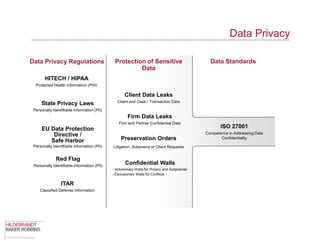
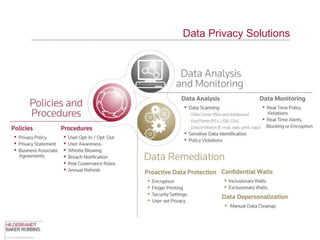
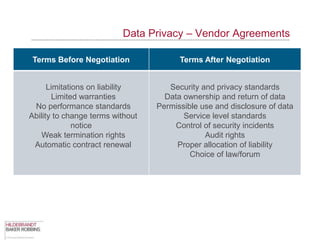
The document provides an overview of data privacy regulations and obligations for law firms. It discusses requirements around protecting client data, firm confidential information, and sensitive data. The presentation notes that firms must establish policies and controls around data collection, use, storage, and sharing to ensure compliance with various privacy laws and standards, including HIPAA, GDPR, and state privacy statutes. It also emphasizes the importance of training employees, conducting security audits, and establishing responsibilities and guidelines for handling personal information.