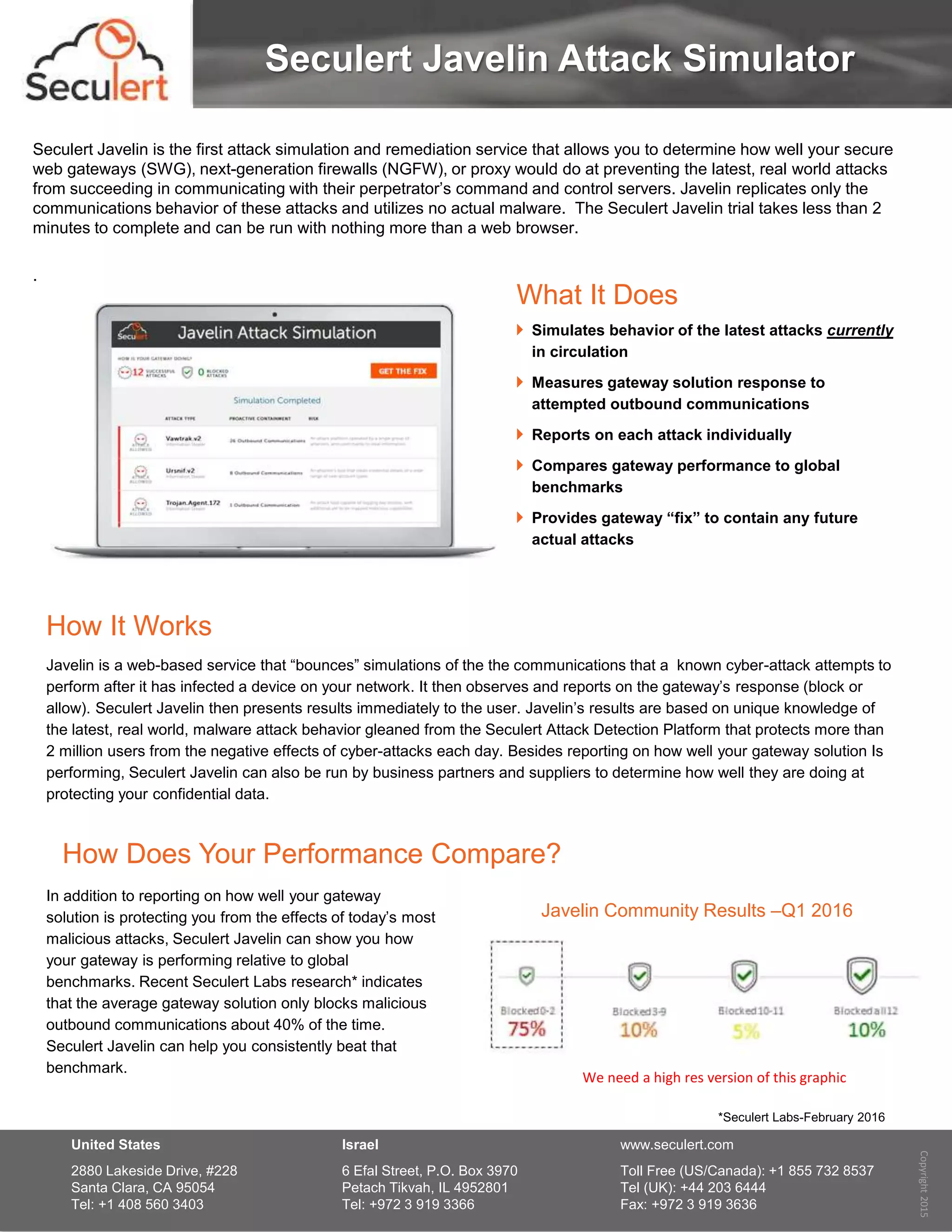
Seculert Javelin is a web-based attack simulation and remediation service that evaluates the effectiveness of secure web gateways and firewalls against real-world cyber-attacks. It simulates attack communications without using actual malware and reports on the gateway's response, allowing users to compare their security performance against global benchmarks. Additionally, it provides recommendations to enhance future protection and is designed to be completed in under two minutes using a web browser.