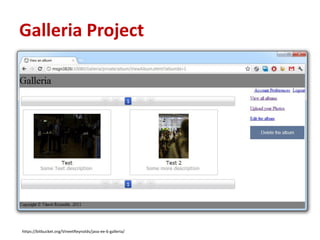
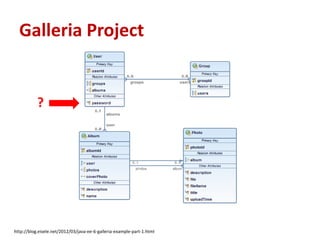
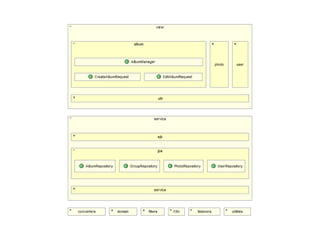
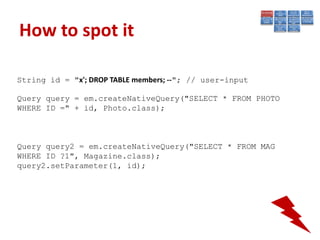
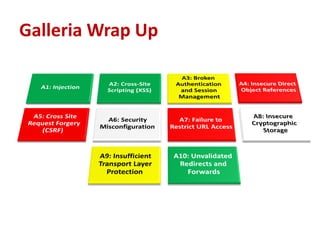
This document summarizes a presentation on Java EE 6 security best practices using the GlassFish application server. It discusses the OWASP Top 10 security risks and provides recommendations for how to address each one when developing applications on the Java EE 6 platform. Specific topics covered include injection, cross-site scripting, authentication and session management, insecure direct object references, cross-site request forgery, security misconfiguration, failure to restrict URL access, insecure cryptographic storage, insufficient transport layer protection, and unvalidated redirects/forwards.