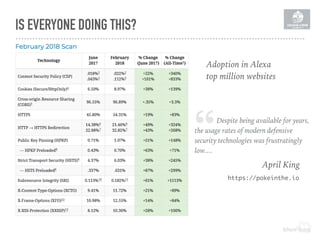
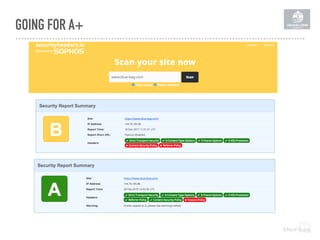
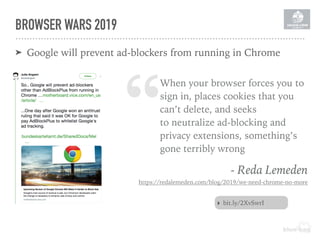
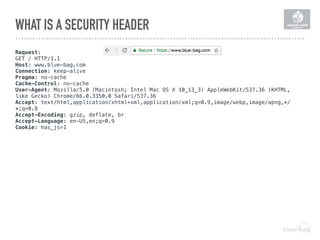
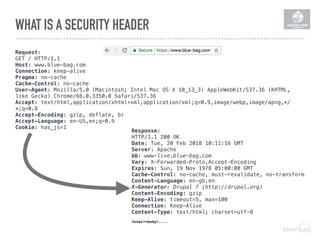
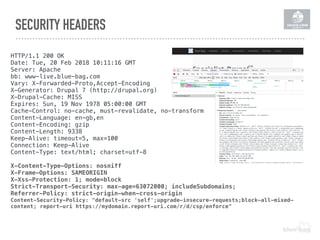
The document discusses the importance of implementing a Content Security Policy (CSP) to protect websites against various security threats including cross-site scripting (XSS), clickjacking, and cross-site request forgery (CSRF). It covers the history of browser wars, the evolution of security headers, and the effectiveness of CSP in mitigating risks associated with web development. The document also highlights practical steps to create and monitor a CSP, along with specific considerations for Drupal users.





























![WHAT IF I AM USING A PAAS
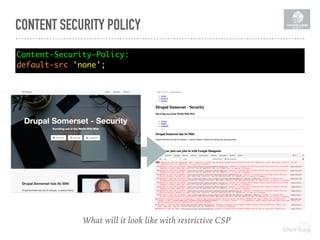
Content-Security-Policy: default-src 'self'; upgrade-insecure-requests; report-uri https://
yourdomain.report-uri.com/r/d/csp/enforce
➤ I can't set headers on my platform!
<meta http-equiv="Content-Security-Policy" content="default-src 'self';script-src cdn.report-uri.com
connect-src yourdomain.report-uri.com; upgrade-insecure-requests">
<script type="text/json" id="csp-report-uri">
{"keys" : ["blockedURI", "columnNumber", "disposition", "documentURI", "effectiveDirective", "lineNumber",
"originalPolicy", "referrer", "sample", "sourceFile", "statusCode", "violatedDirective"],
"reportUri" : "https://yourdomain.report-uri.com/r/d/csp/enforce"}
</script>
<script src="https://cdn.report-uri.com/libs/report-uri-js/1.0.1/report-uri-js.min.js"
integrity="sha256-Cng8gUe98XCqh5hc8nAM3y5I1iQHBjzOl8X3/iAd4jE=" crossorigin="anonymous"></script>
➤ No frame-ancestors directive
➤ Unfortunately no reporting! - Use report-uri-js
<meta http-equiv="Content-Security-Policy" content="default-src 'self';
upgrade-insecure-requests">
➤ Set CSP using metatags (set them early)](https://image.slidesharecdn.com/dclondon2019-190304164123/85/Browser-Wars-2019-Implementing-a-Content-Security-Policy-43-320.jpg)