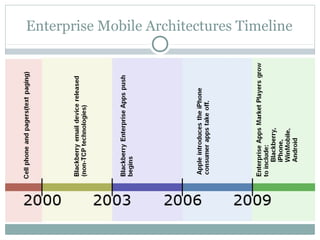
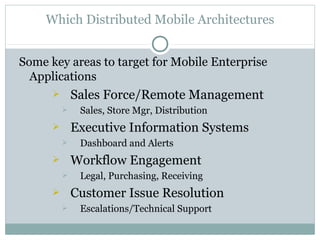
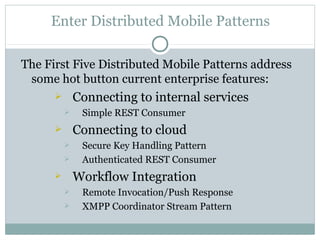
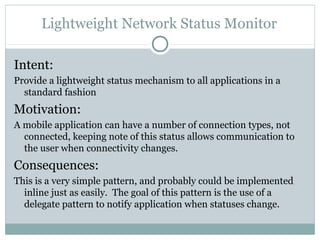
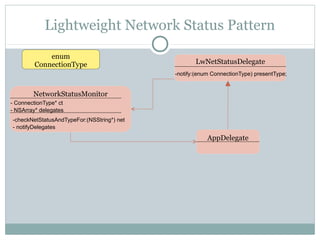
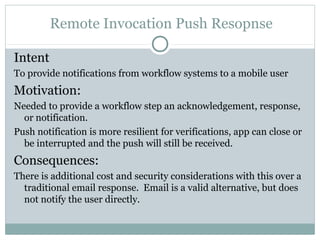
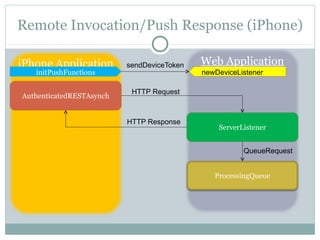
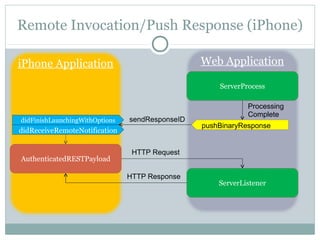
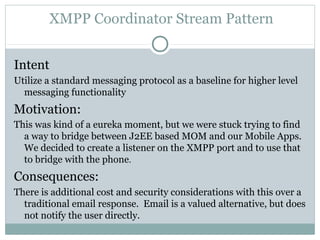
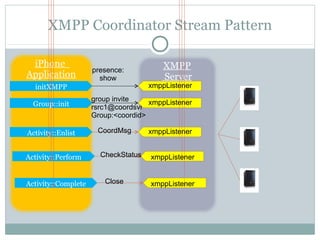
The document discusses design patterns for distributed mobile applications, particularly focusing on iPhone development for enterprise use. It covers key patterns like simple and authenticated REST consumers, lightweight network status monitoring, remote invocation with push responses, and an XMPP coordinator stream. The presentation emphasizes the need for these patterns to address current enterprise features and enhance mobile application enablement.