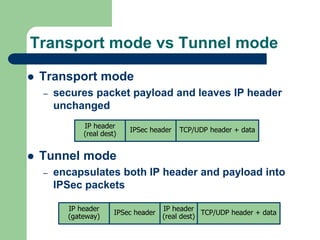
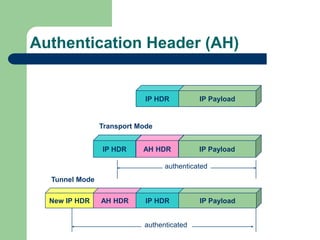
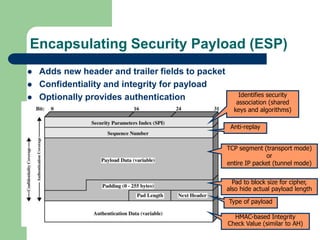
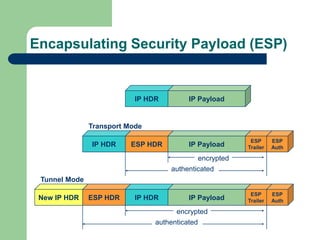
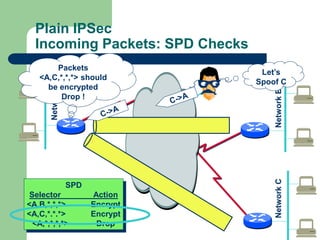
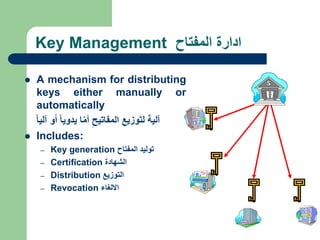
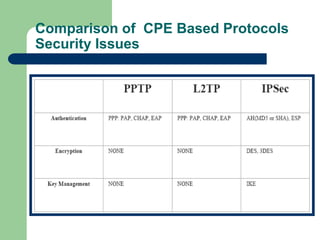
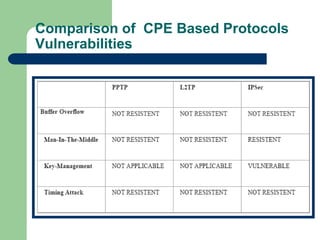
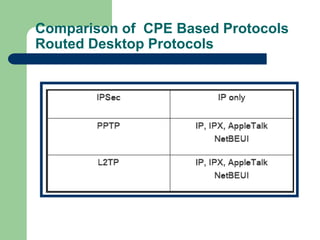
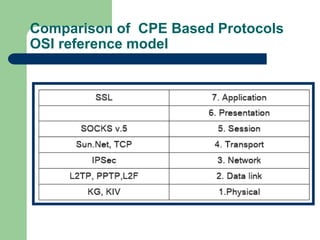
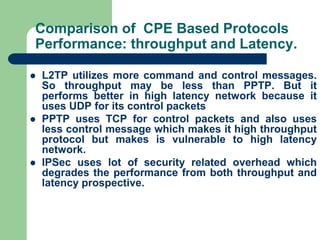
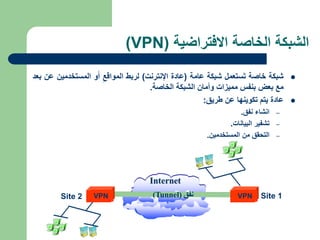
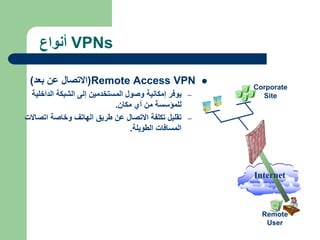
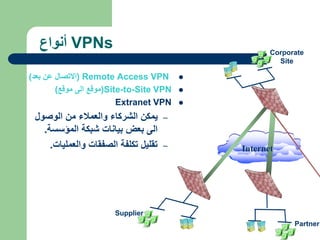
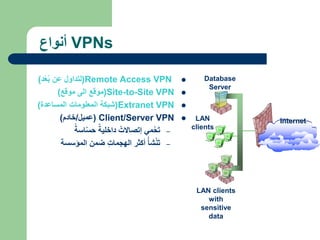
The document discusses virtual private networks (VPNs), highlighting two main types: remote access VPNs, which provide users secure access to internal networks from any location, and site-to-site VPNs, which connect different branches of an organization. It emphasizes the cost-effectiveness and flexibility of VPNs compared to traditional leased lines, along with their security features such as data encryption and user authentication. The document also outlines the concepts of tunneling and various types of VPN setups, including extranet and client/server configurations.













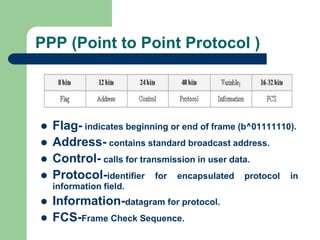




![Point-to-Point Tunneling Protocol (PPTP)
Mainly implemented and used (
طبقت
و
استخدمت
) by Microsoft [RFC
2637]
– Extension (
امتداد
) of PPP.
– Easy to use and to implement (
سهولة
االستخدام
و
التطبيق
) .
Allows tunnelling (
حفر
نفق
) of PPP datagrams between PPTP
Client (
عميل
) , and PPTP server (
خادم
) , يقوم
بفصل NAS الموجود
في PPP الى
– PPTP Access Concentrator (PAC)
Network access device supporting PPTP
– PPTP Network Server (PNS)
Corporate (VPN) gateway.
Authentication
– Uses PPP authentication.
Encryption
– MPPE (Microsoft Point-to-point encryption).
Many sessions multiplexed on a single tunnel.
(
عدة
جلسات
على
نفق
وحيد
)](https://image.slidesharecdn.com/random-240630172432-1335a493/85/Introduction-to-Virtual-Private-Network-VPN-ppt-26-320.jpg)


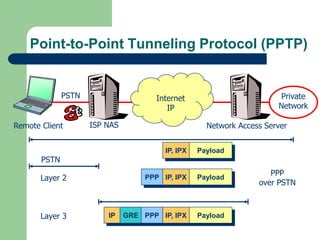


![Layer 2 Forwarding Protocol (L2F)
Developed (
تم
ت
طو
ي
ر
ه
بواسطة
) by Cisco [RFC 2341]
L2F provides tunneling between an ISP’s dial-up
server and the network. User connects to the ISP
using PPP.
The PPP frames are then encapsulated inside an
L2F frame which is then forwarded to a router for
transmission across the Internet.
Authentication
– Like PPTP, Uses PPP authentication.
Encryption
– does not provide any data encryption.
ال
ُدّزوُي
ّأي
تشفير
بيانات
) )
Allows multiple tunnels and multiple connections
on tunnel (
أنفاق
متعددة
و
جلسات
متعددة
لكل
نفق
)](https://image.slidesharecdn.com/random-240630172432-1335a493/85/Introduction-to-Virtual-Private-Network-VPN-ppt-32-320.jpg)
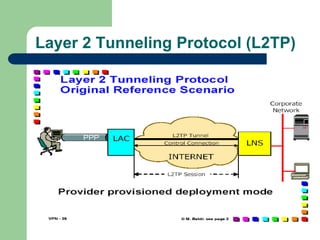
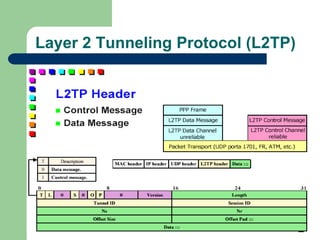
![Layer 2 Tunneling Protocol (L2TP)
Combines best features of L2F and PPTP تدمج
أفضل
ميزات
) )
– Developed by IETF [RFC 2661]
Allows tunnelling of PPP datagrams between L2TP Client, and
L2TP server , يقوم
بفصل NAS الموجود
في PPP الى
– L2TP Access Concentrator (LAC)
Network access device supporting L2TP
– L2TP Network Server (LNS)
Corporate (VPN) Gateway
Allows multiple tunnels with multiple sessions inside every
tunnel (
أنفاق
متعددة
و
جلسات
متعددة
لكل
نفق
)
CPE based deployment mode by including LAC functionalities
within user terminal
Commonly used with IPSec -> L2TP/IPSec](https://image.slidesharecdn.com/random-240630172432-1335a493/85/Introduction-to-Virtual-Private-Network-VPN-ppt-34-320.jpg)