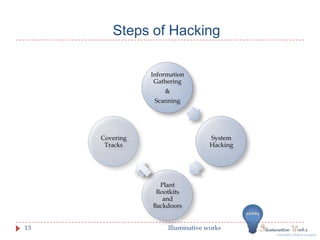
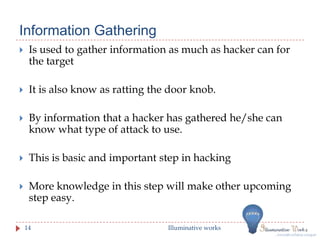
This document provides an introduction to ethical hacking. It discusses the differences between ethical hackers and malicious hackers, outlining the typical steps an ethical hacker takes including information gathering, scanning, system hacking, maintaining access, and covering tracks. The document also discusses how ethical hackers conduct research on vulnerabilities and how they test systems, preparing documentation and reports to deliver to clients. Regular testing is recommended to ensure security as software and systems change over time.