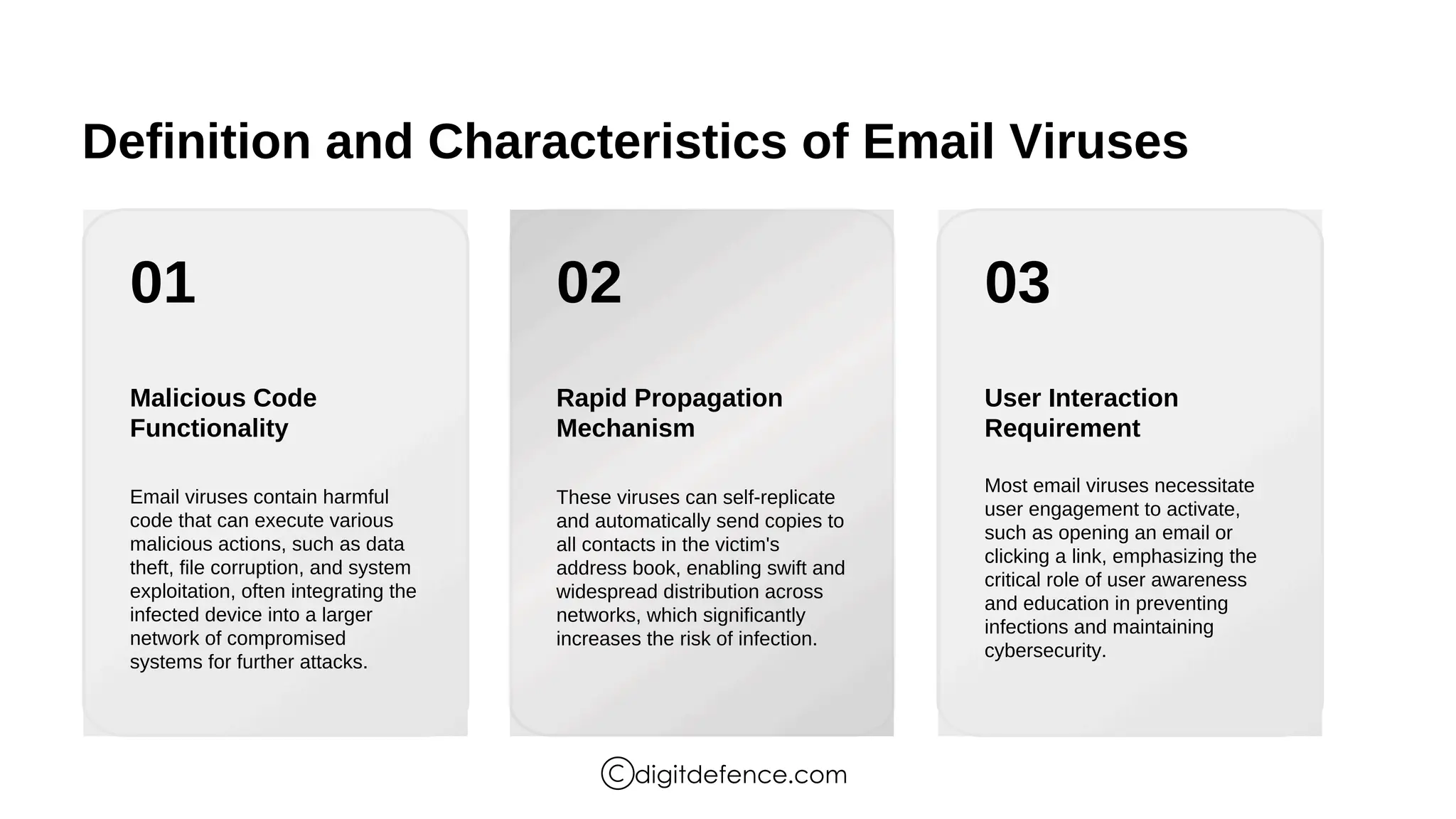
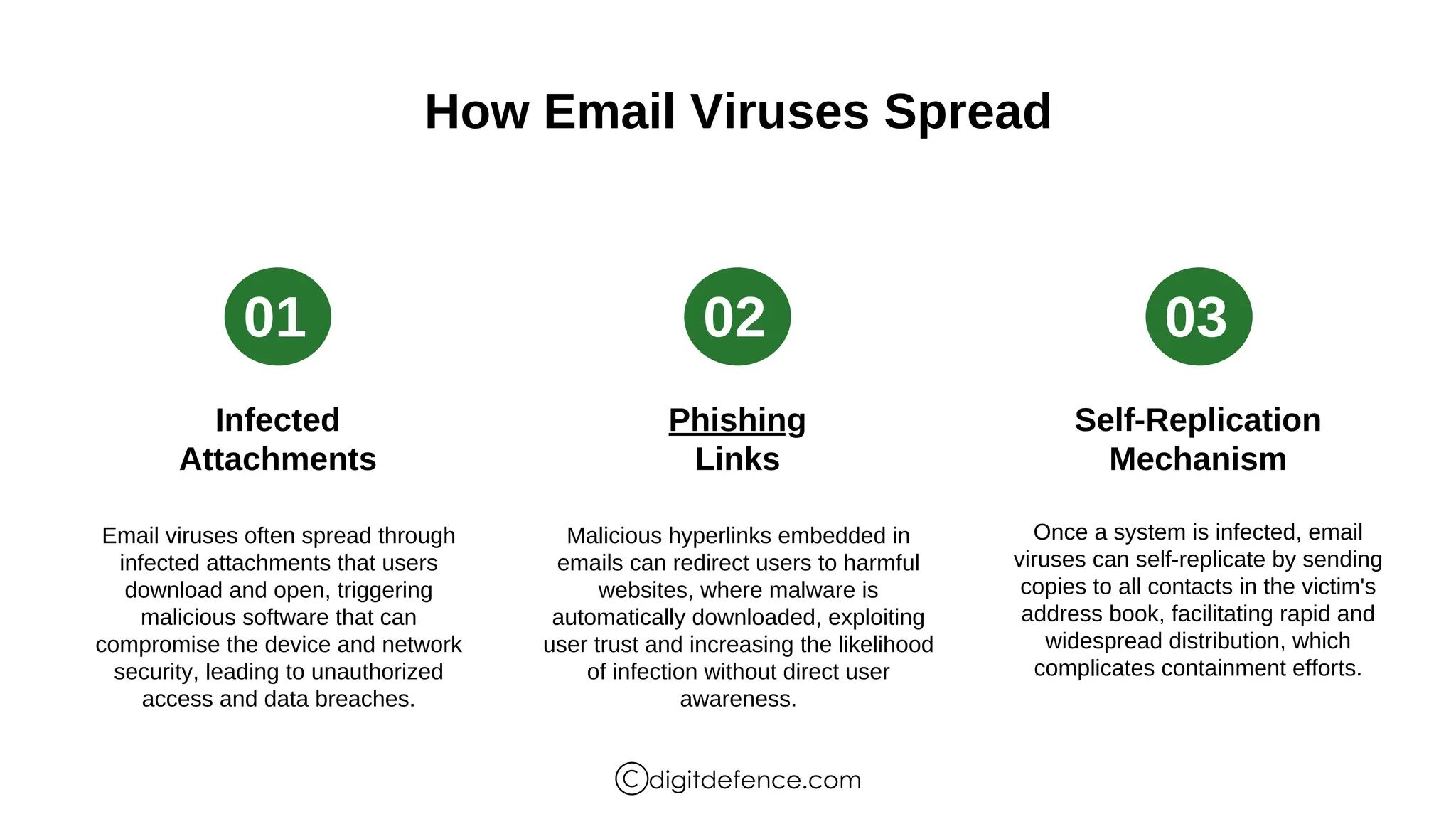
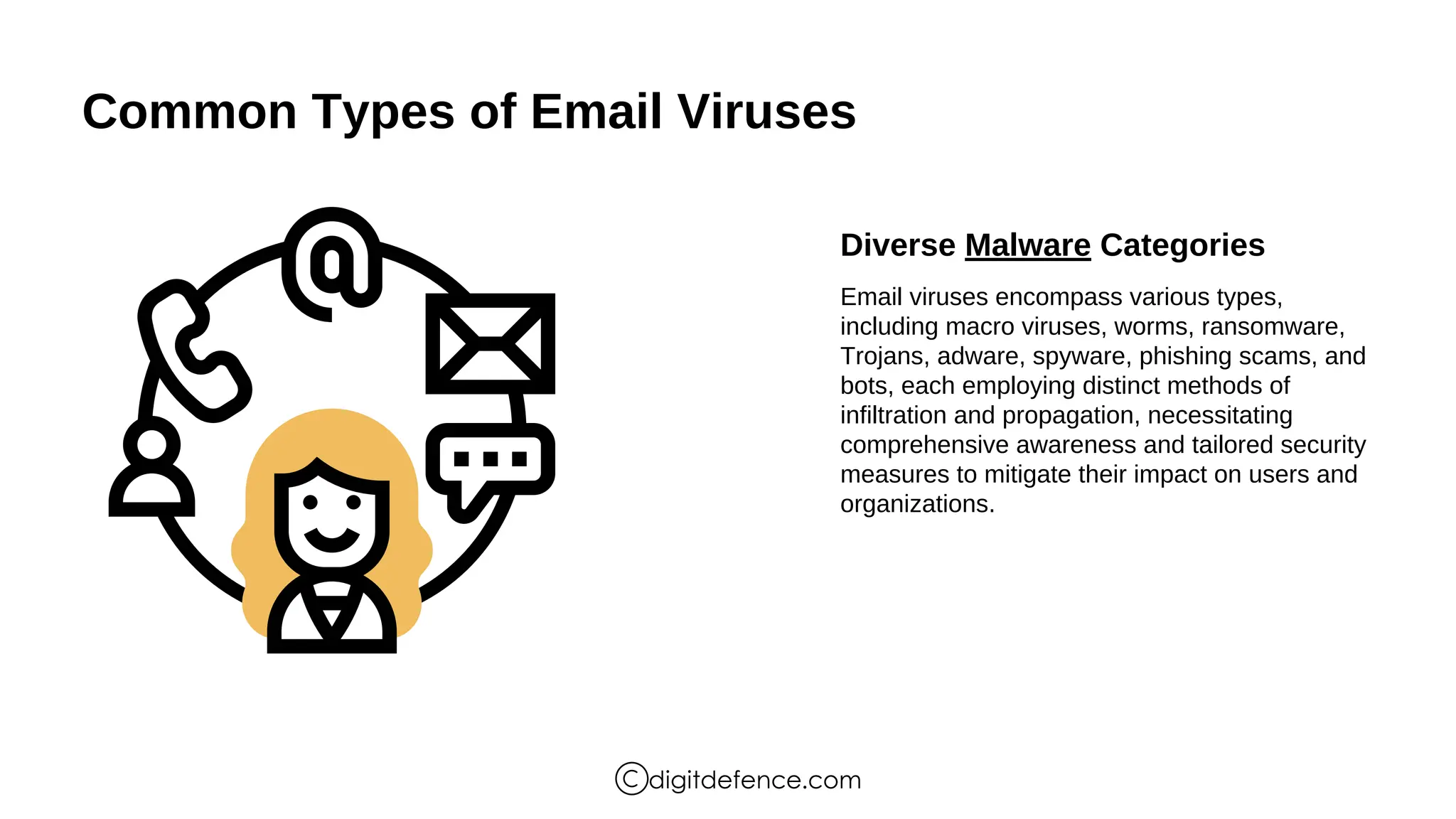
The document provides an overview of email viruses, including their characteristics, propagation methods, types, signs of infection, and best practices for prevention. Email viruses often require user interaction for activation, spread through infected attachments or phishing links, and can lead to data breaches and compromised systems. Users should verify sender authenticity, scrutinize subject lines, and assess email content to recognize potential threats.