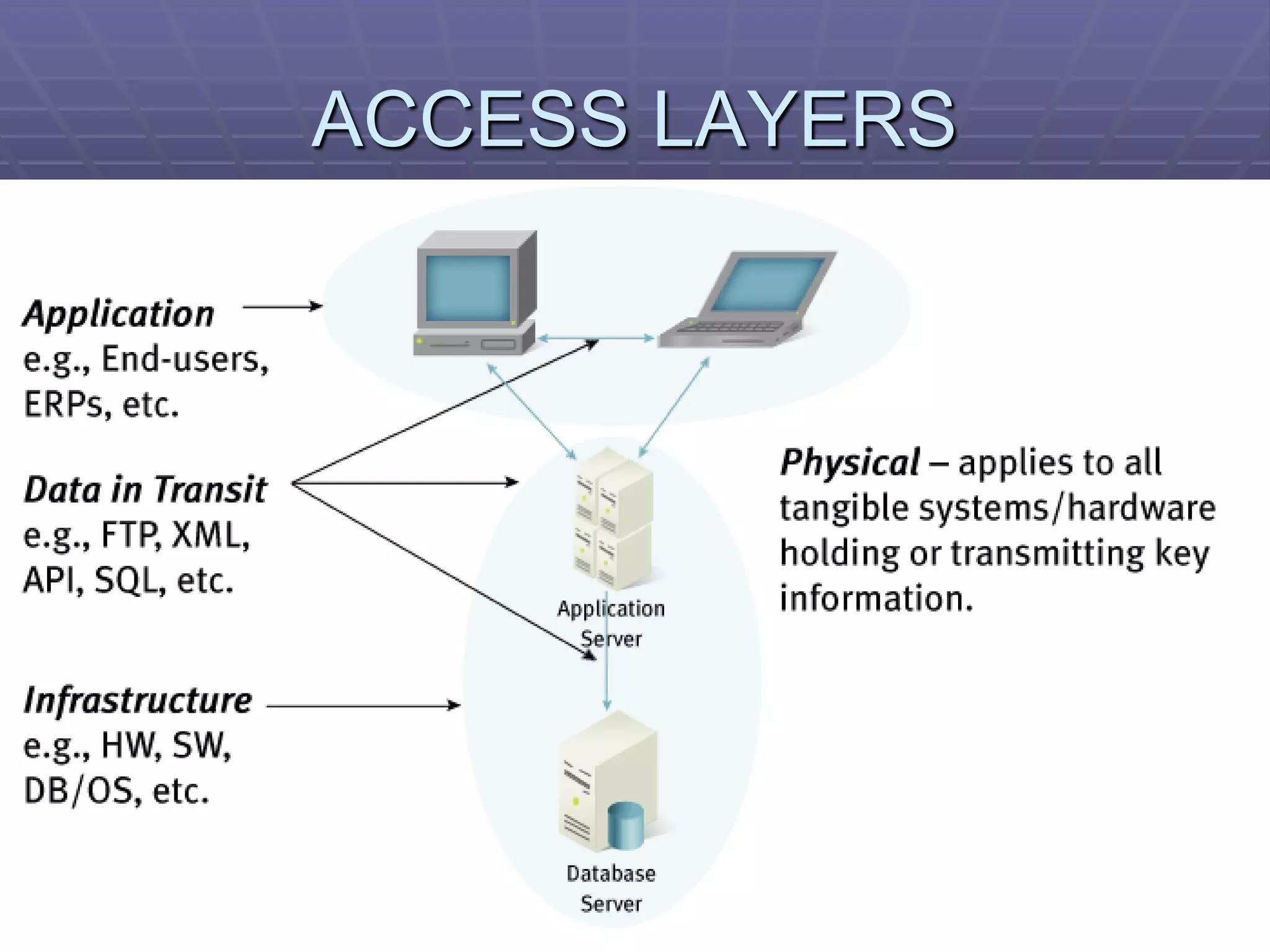
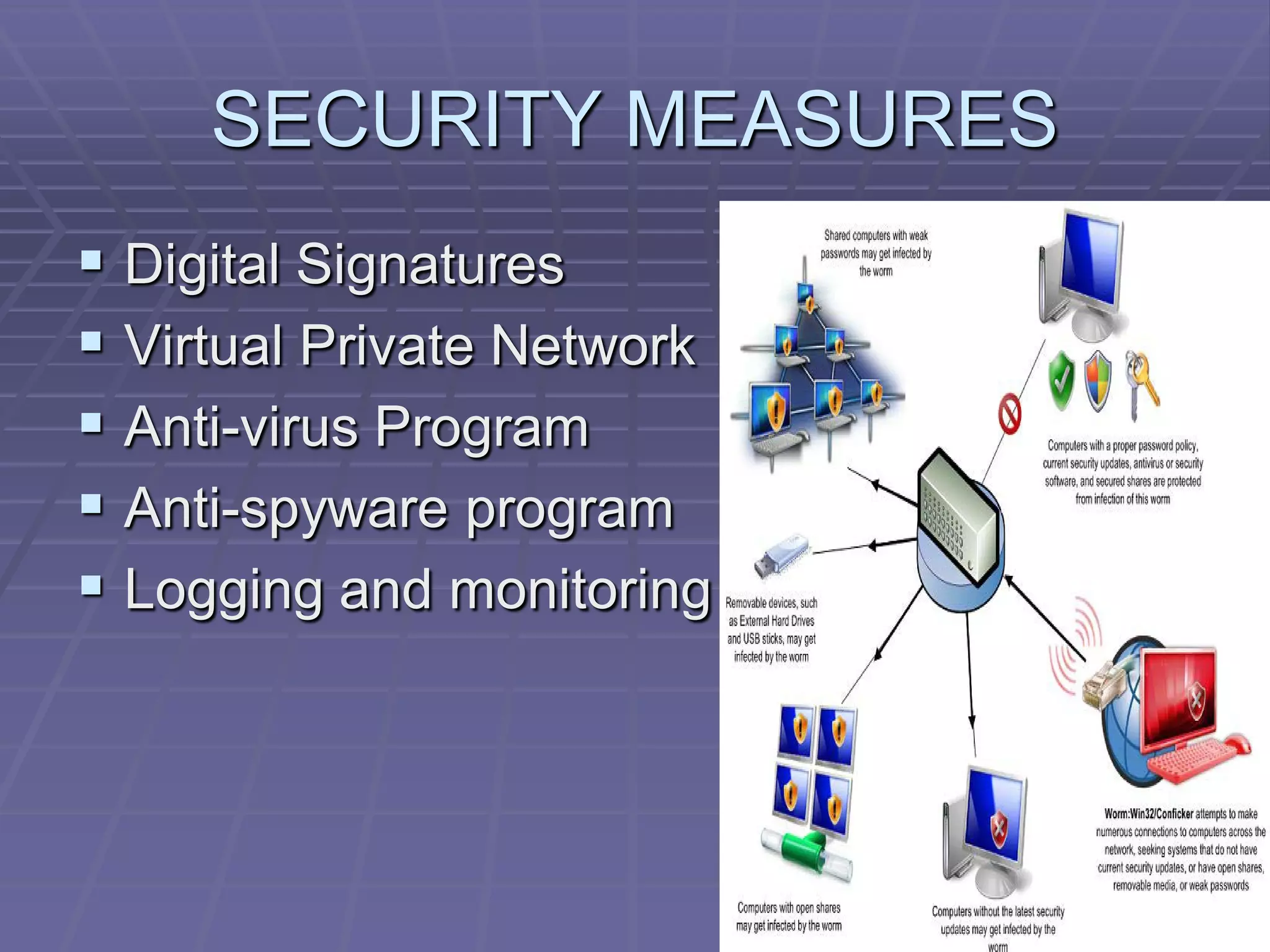
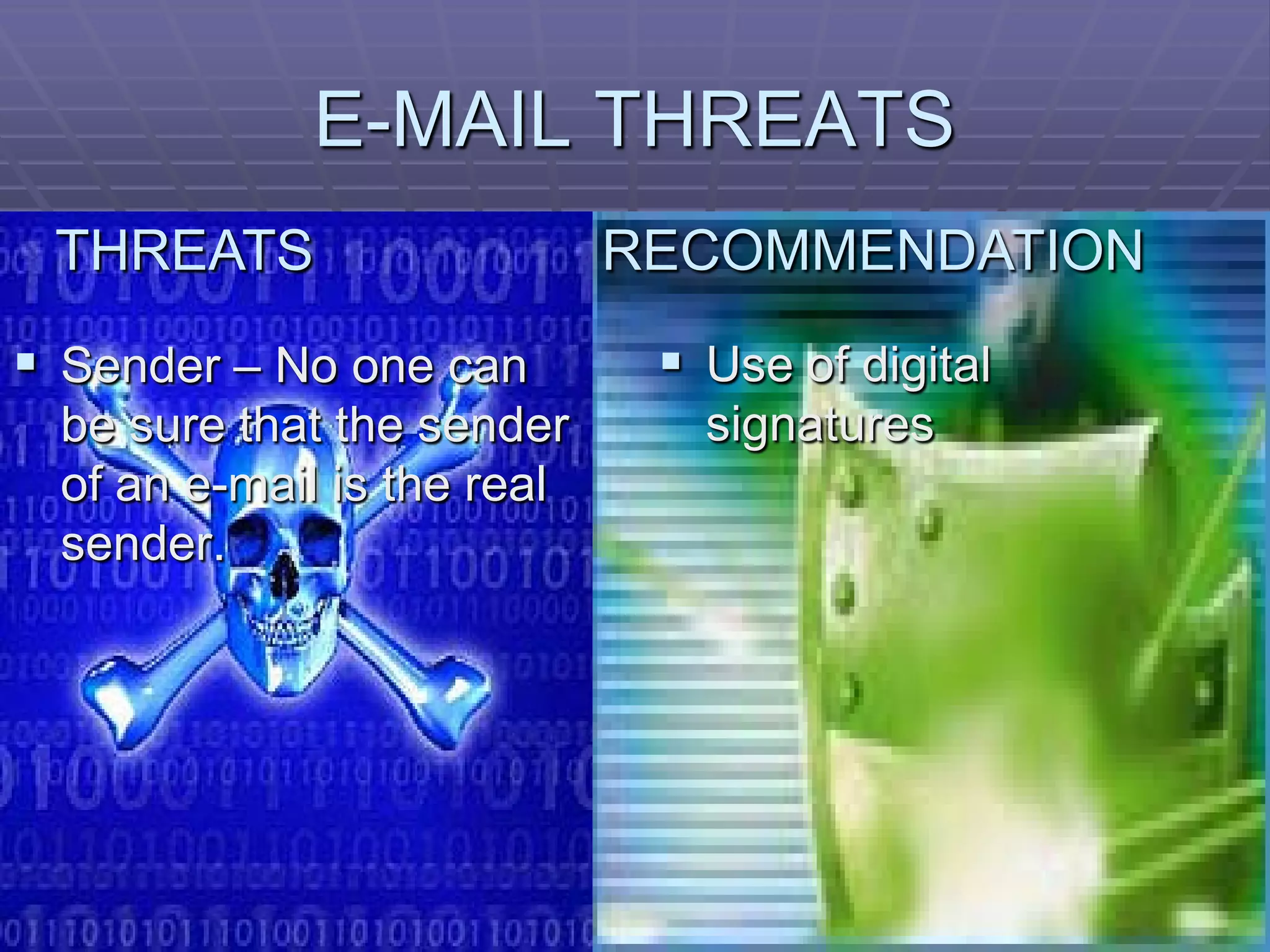
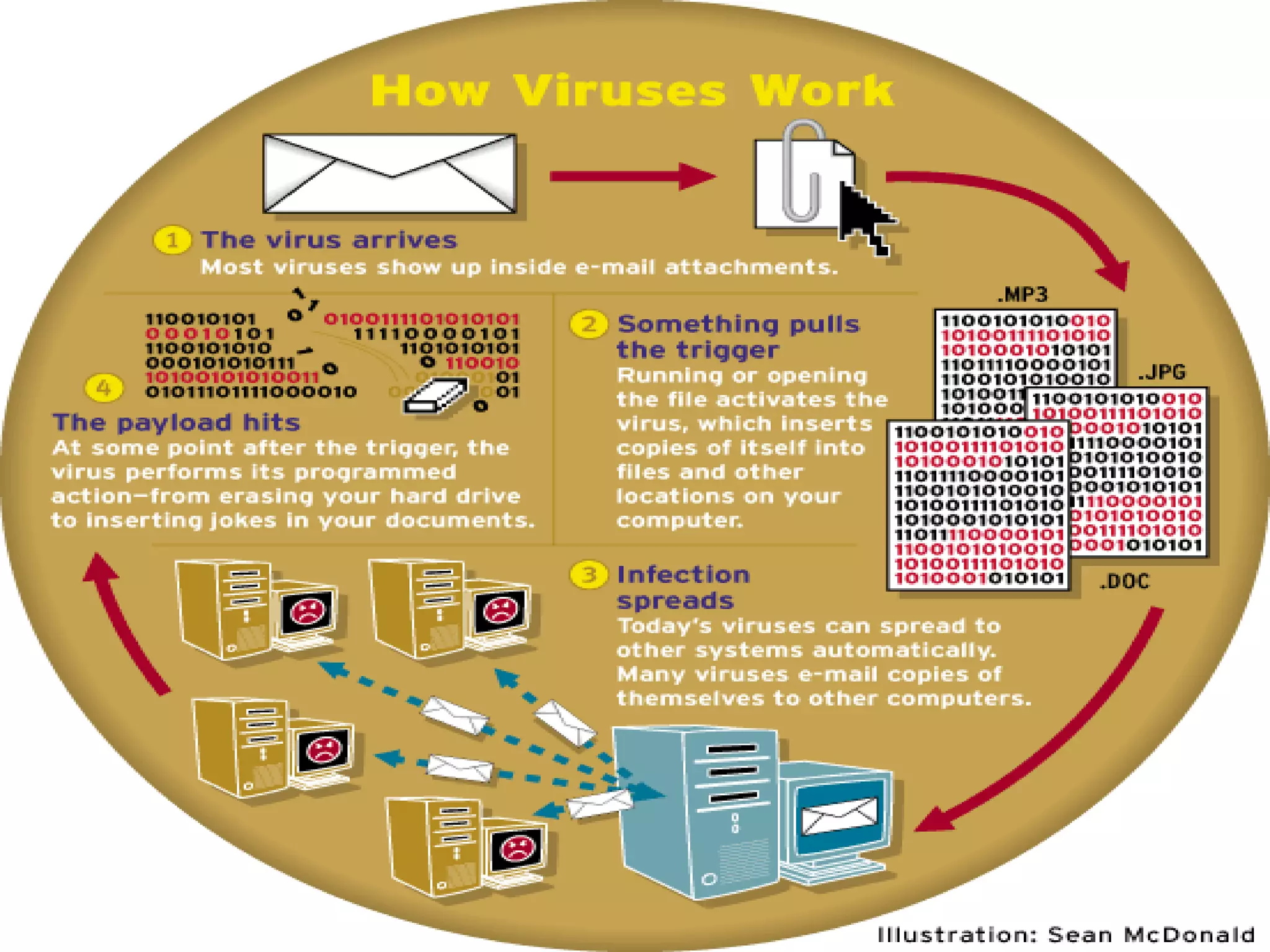
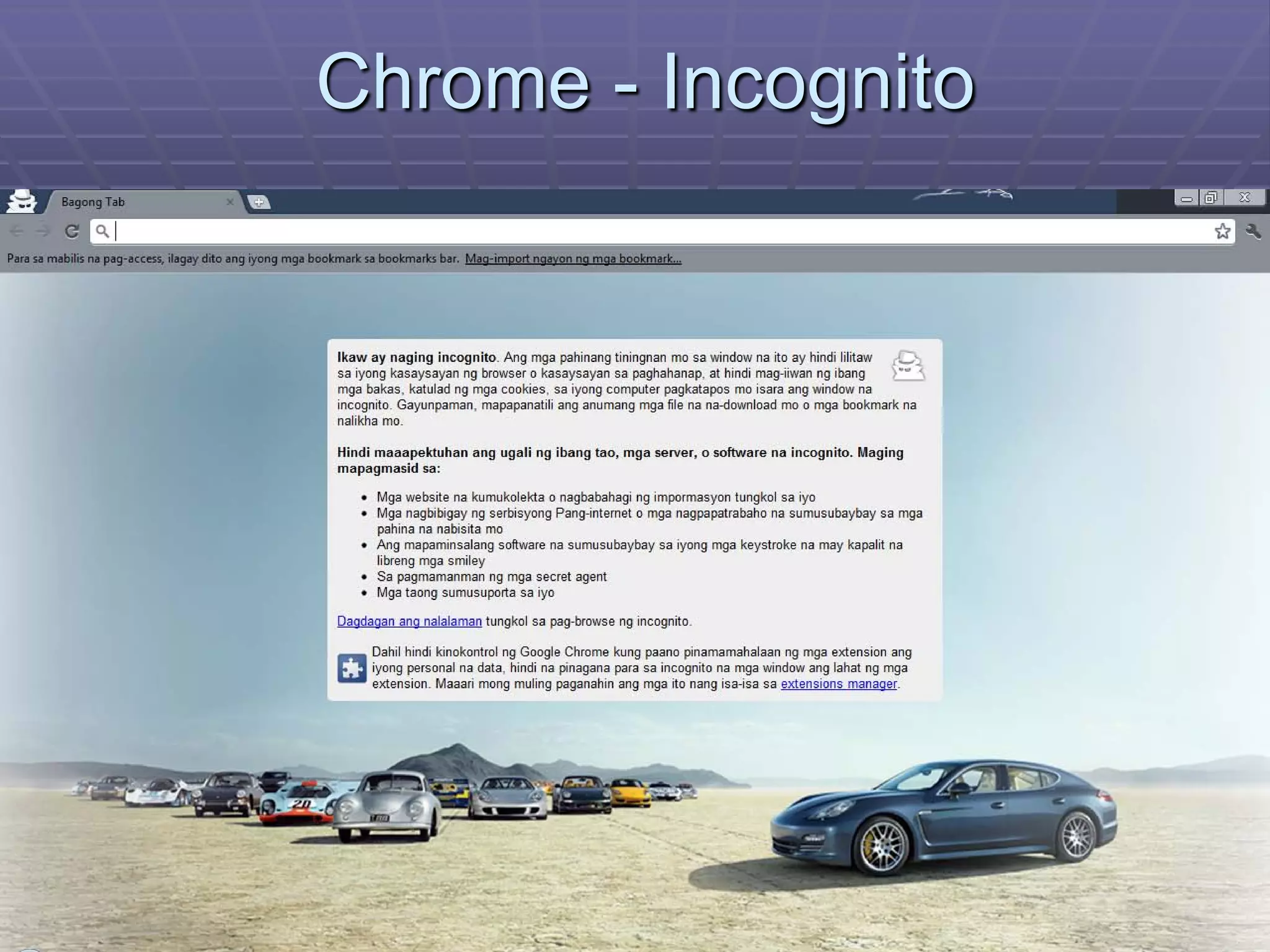
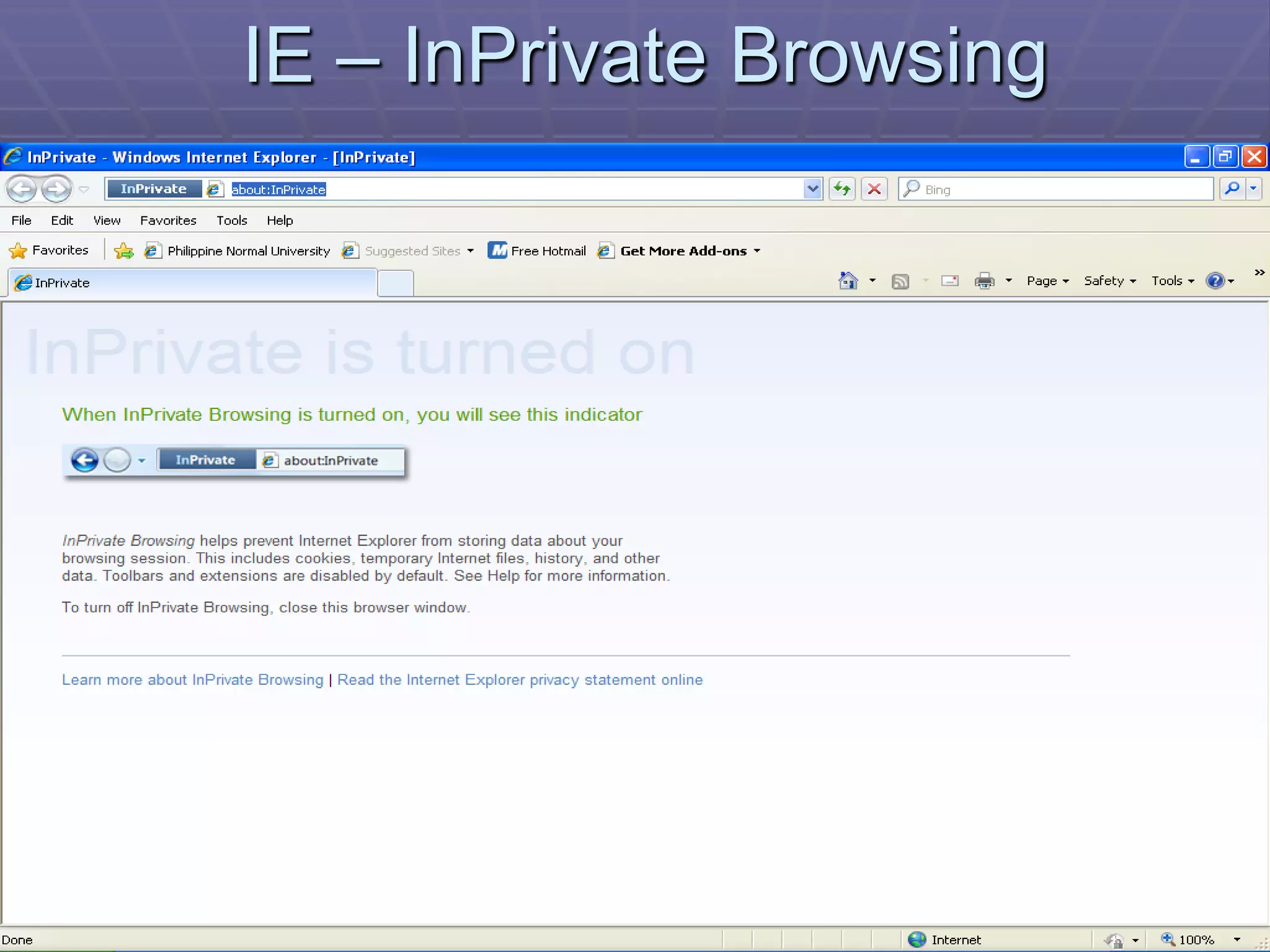
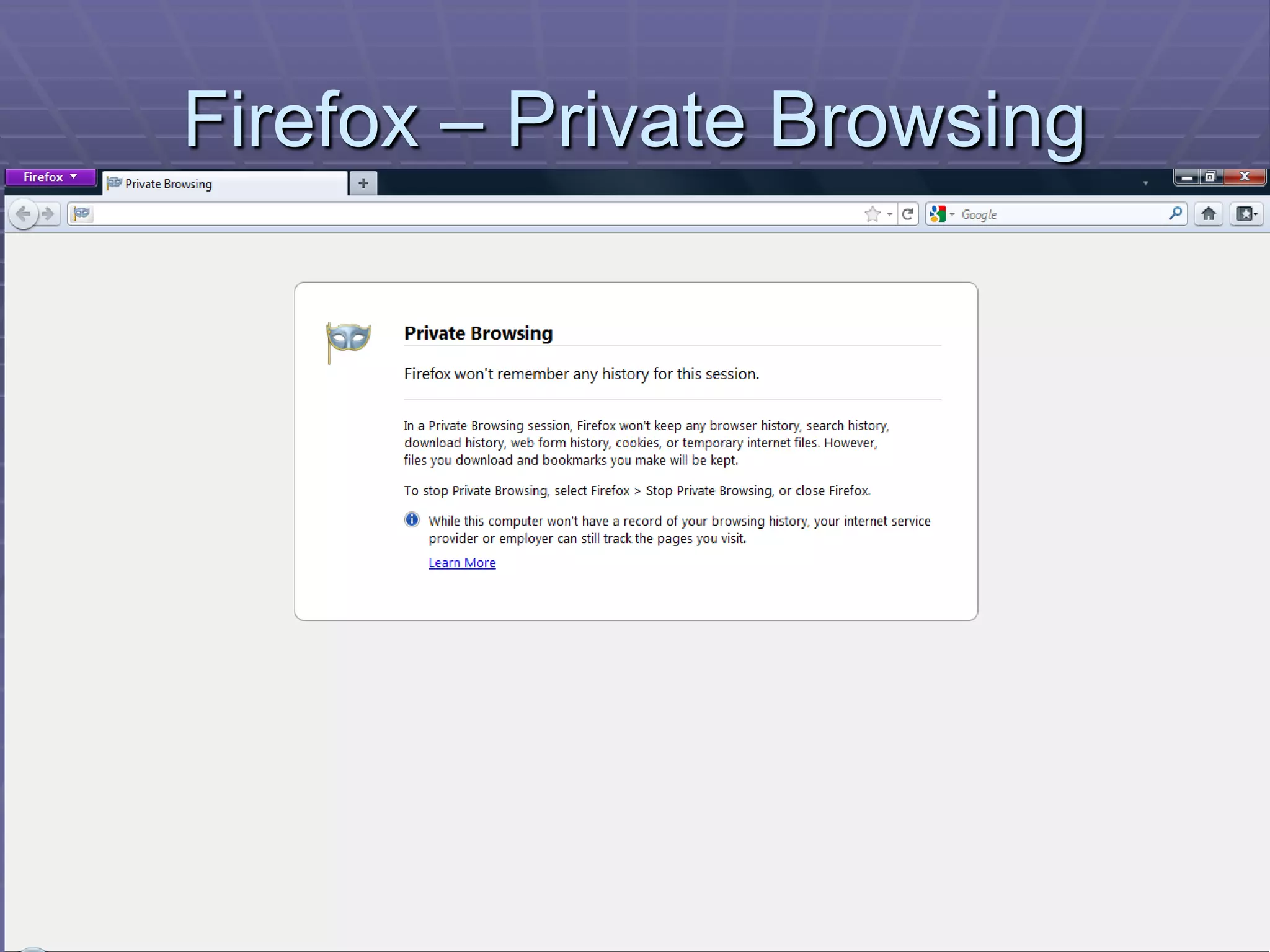
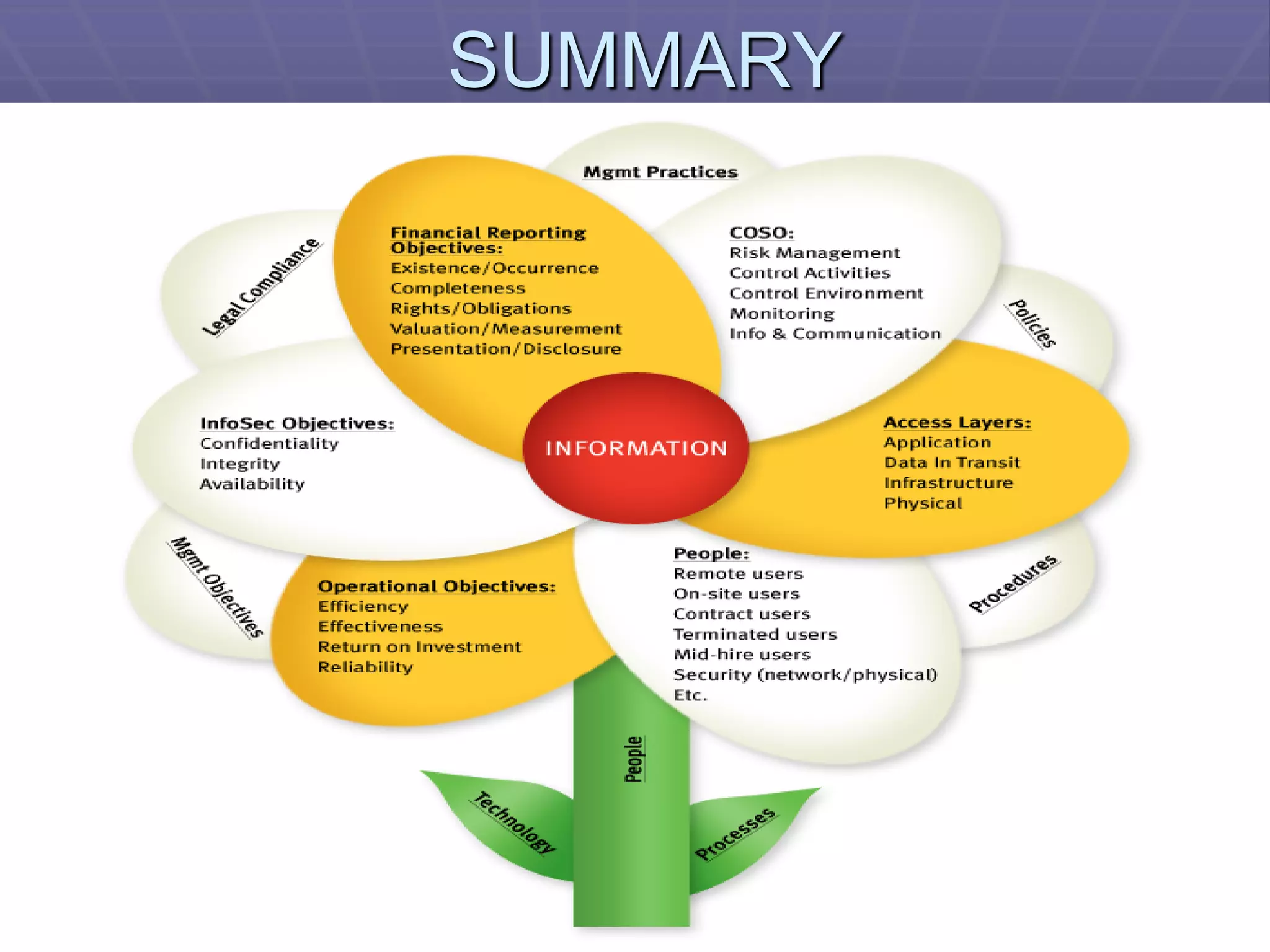
The document discusses information system security controls and risks. It outlines 7 criteria that information systems should meet, including effectiveness, efficiency, confidentiality and integrity. It also describes different business risks to information systems like strategic risk, security risk and legal risk. Finally, it discusses various security measures that can be implemented like policies, firewalls, passwords and encryption to protect information systems and mitigate risks.