Embed presentation
Downloaded 81 times



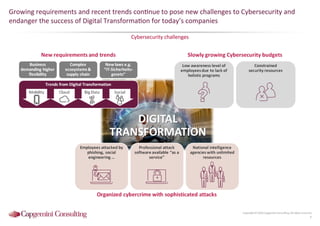

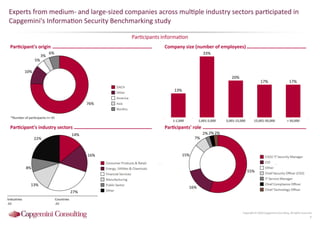

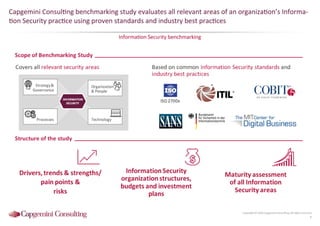
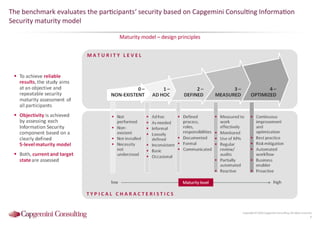

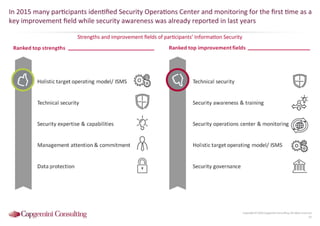
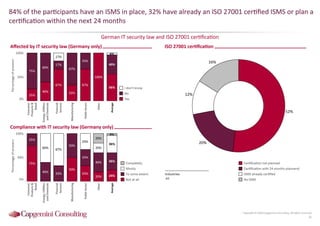
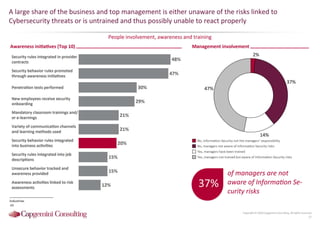
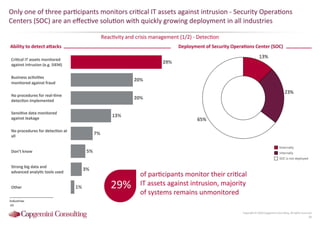
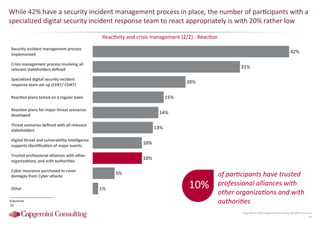

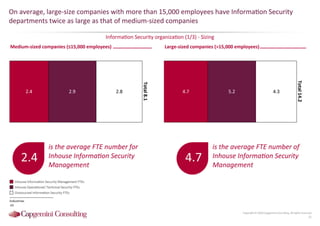

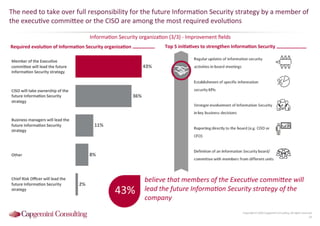
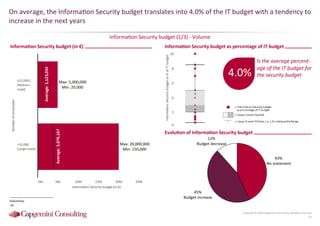
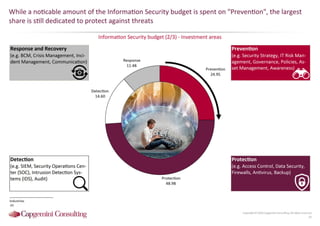
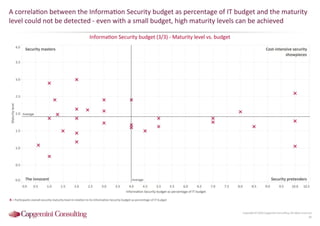

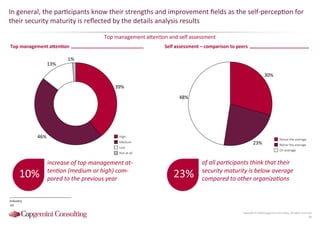
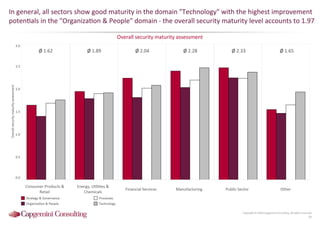

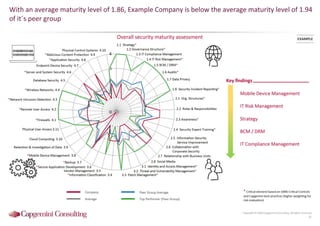
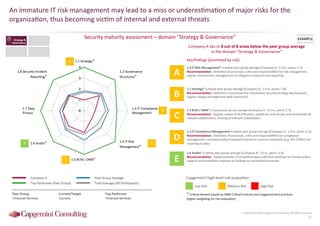
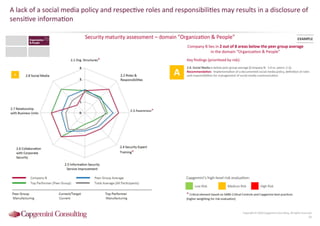
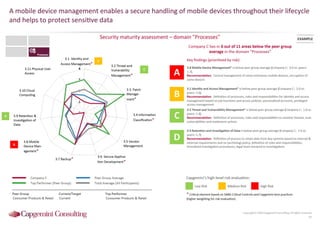
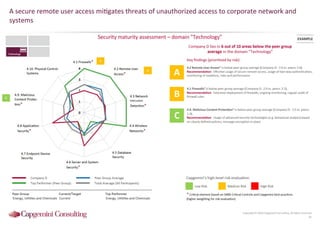







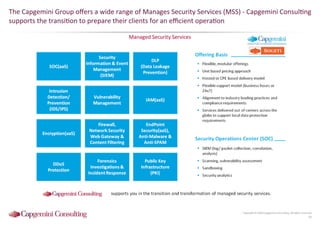




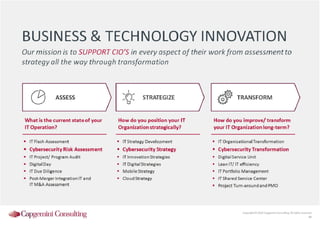
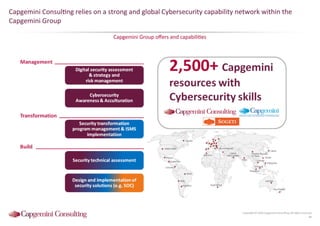



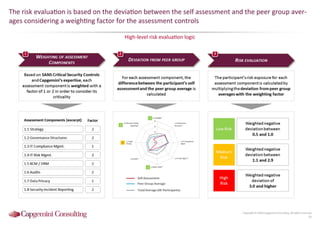

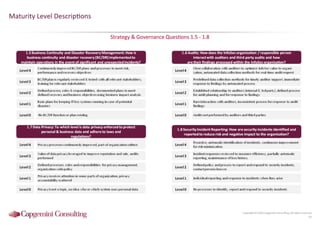









Information Security assessment of companies in Germany, Austria and Switzerland. Capgemini Consulting conducted a benchmarking study on Information Security to provide a thorough and balanced view of the current state of security.






























































