Infographic Protecting Patient Data
•
0 likes•68 views
Learn the security risks of digital healthcare technology and how healthcare organizations can protect their patients’ data with Fortinet’s Security Fabric.
Report
Share
Report
Share
Download to read offline
Recommended
An Ounce of Prevention: How Healthcare Organizations Can Stop Cybercrime in I...

Healthcare regularly tops the list of most cyberattacked industries thanks to the extremely valuable patient information it retains. And as healthcare becomes more digitally connected than ever before, it’s imperative that these organizations invest in top-notch IT security.
More: http://ms.spr.ly/6001pYtz3
Why shaWHY SHARE CYBER THREAT INFORMATIONre cyber threat information

Cyber threat information sharing is essential to thwarting successful hacks and minimizing consequences should a breach occur. For many years large organizations have had opportunities to work with the Department of Homeland Security (DHS) to share indicators of compromise to ensure the protection of critical infrastructure and major business entities.
https://mikeechols.com/why-share-cyber-threat-information
Mha690 wk1 dis2

The document discusses the Health Insurance Portability and Accountability Act (HIPAA) and its requirements for protecting private health information. It notes that HIPAA was established in 1996 and outlines its privacy and security rules. It also provides recommendations for HIPAA compliance, including training employees, implementing access controls, conducting security audits, and logging system activity. Finally, it discusses the civil and criminal penalties for violating HIPAA regulations.
Data integrity, security and privacy

Data integrity refers to data accuracy and is a vital concern for organizations. Data security protects data from destruction and misuse, both intentional and accidental, and is a growing challenge as organizations grant database access. A database activity monitoring program continually monitors databases to detect and report possible intrusions and other threats in real time.
Defending Your Institution Against Ransomware Attacks

This article was published in Education Technology Insights in June 2019. Because the publisher didn’t include my references, this document is shared to provide the article’s references cited.
https://education-security.educationtechnologyinsights.com/cxoinsights/defending-your-institution-against-ransomware-attacks-nid-646.html
Handling information Standard by Skills for Care

This document discusses handling information in health and social care. It states that information about an individual's care is private and must be kept confidential, only sharing with those who need to know. It provides examples of who would need to know, such as care workers involved in an individual's care but not neighbors or unrelated care workers. The document also discusses risks of sharing on social media and legal requirements regarding data protection and freedom of information. Policies around secure storage, passwords, and filing are outlined. Concerns about improper information handling should be reported to managers.
The CIA Triad - Assurance on Information Security

Confidentiality, Integrity and Availability of Data are the basis for providing assurance on IS Security. This document gives a small overview of the impact of confidentiality, integrity and availability on the data and the need of securing the CIA.
Infographic Protecting Patient Data 

Learn the security risks of digital healthcare technology and how healthcare organizations can protect their patients’ data with Fortinet’s Security Fabric.
Recommended
An Ounce of Prevention: How Healthcare Organizations Can Stop Cybercrime in I...

Healthcare regularly tops the list of most cyberattacked industries thanks to the extremely valuable patient information it retains. And as healthcare becomes more digitally connected than ever before, it’s imperative that these organizations invest in top-notch IT security.
More: http://ms.spr.ly/6001pYtz3
Why shaWHY SHARE CYBER THREAT INFORMATIONre cyber threat information

Cyber threat information sharing is essential to thwarting successful hacks and minimizing consequences should a breach occur. For many years large organizations have had opportunities to work with the Department of Homeland Security (DHS) to share indicators of compromise to ensure the protection of critical infrastructure and major business entities.
https://mikeechols.com/why-share-cyber-threat-information
Mha690 wk1 dis2

The document discusses the Health Insurance Portability and Accountability Act (HIPAA) and its requirements for protecting private health information. It notes that HIPAA was established in 1996 and outlines its privacy and security rules. It also provides recommendations for HIPAA compliance, including training employees, implementing access controls, conducting security audits, and logging system activity. Finally, it discusses the civil and criminal penalties for violating HIPAA regulations.
Data integrity, security and privacy

Data integrity refers to data accuracy and is a vital concern for organizations. Data security protects data from destruction and misuse, both intentional and accidental, and is a growing challenge as organizations grant database access. A database activity monitoring program continually monitors databases to detect and report possible intrusions and other threats in real time.
Defending Your Institution Against Ransomware Attacks

This article was published in Education Technology Insights in June 2019. Because the publisher didn’t include my references, this document is shared to provide the article’s references cited.
https://education-security.educationtechnologyinsights.com/cxoinsights/defending-your-institution-against-ransomware-attacks-nid-646.html
Handling information Standard by Skills for Care

This document discusses handling information in health and social care. It states that information about an individual's care is private and must be kept confidential, only sharing with those who need to know. It provides examples of who would need to know, such as care workers involved in an individual's care but not neighbors or unrelated care workers. The document also discusses risks of sharing on social media and legal requirements regarding data protection and freedom of information. Policies around secure storage, passwords, and filing are outlined. Concerns about improper information handling should be reported to managers.
The CIA Triad - Assurance on Information Security

Confidentiality, Integrity and Availability of Data are the basis for providing assurance on IS Security. This document gives a small overview of the impact of confidentiality, integrity and availability on the data and the need of securing the CIA.
Infographic Protecting Patient Data 

Learn the security risks of digital healthcare technology and how healthcare organizations can protect their patients’ data with Fortinet’s Security Fabric.
Cybersecurity

ybersecurity is an increasing
concern for many in the
medical cybersecurity and
information technology
professions. As computerized
devices in medical facilities
become increasingly networked
within their own walls and
with external facilities, the risk
of cyberattacks also increases,
threatening confidentiality,
safety, and well-being. This
article describes what health
care organizations and
imaging professionals should
do to minimize the risks.
Systems Thinking on a National Level, Part 2Drew David.docx

This document discusses various cybersecurity threats faced by the healthcare industry, including phishing emails, SQL injection attacks, eavesdropping, and viruses. Phishing emails are a major issue, accounting for 93% of breached healthcare data. Hackers use phishing emails that appear legitimate to trick staff into revealing sensitive information. The document also examines ways to better protect against these threats, such as password protection, data loss prevention, access controls, and staff training. Overall, the document analyzes the cybersecurity risks healthcare organizations face and ways to decrease breaches through education and prevention methods.
Privacy and Security by Design

Privacy and Security by Design Spotlight Presentation at HIMMS Privacy and Security Forum, December 5th 2016. Presented by Jeff R. Livingstone, PhD, Vice President and Global Lead, Life Sciences & Healthcare, Unisys Corporation.
Why healthcare is the biggest target for cyberattacks-converted.pdf

Sparity provides the Top Custom healthcare Software and Application development services for healthcare industries in USA and Across the Globe. We can help you build a leading-edge tech platform with the right UI/UX framework and functionalities. We Make a positive impact with modern healthcare services
Healthcare Cybercrime

Healthcare organizations will increasingly be targeted by cybercriminals in 2017, as hackers expand from health insurers to hospital networks, which can be more difficult to secure. Ransomware presents low-risk opportunities for attackers to obtain money from victims. This funding supports further research and development of more advanced attacks that may evade existing security systems. Proper security measures, contingency planning, and staff training are recommended to help organizations respond to emerging ransomware and other sophisticated cyber threats.
Digital Security 

This document discusses digital security and the importance of protecting personal information online. It defines digital security as electronic precautions to guarantee safety and protect digital identities. Examples of security measures include home alarm systems that notify of dangers and technology firewalls and Wi-Fi protections. Statistics show data breaches are common, with 43% of companies experiencing one in the past year, costing the global and US economies billions. The document urges vigilance in protecting personal information and provides tips to prevent security breaches like using unique passwords and antivirus software.
Digital security

This document discusses digital security and the importance of protecting personal information online. It defines digital security as electronic precautions to guarantee safety and protect digital identities. Examples of security measures include home alarm systems that notify of dangers and technology firewalls and Wi-Fi protections. Statistics show data breaches are common, with 43% of companies experiencing one in the past year, costing the global economy hundreds of billions annually. The document urges readers to take security seriously by using different passwords, antivirus software, and avoiding public Wi-Fi to prevent hacking and protect themselves from financial losses.
Cyber security threats and its solutions

There are a lot of cyber threats in the cyber world, but some of them are really disastrous for your system and data. Cyber threats are increasing rapidly so it is important to know how to prevent them.
Cyber Security Intelligence

This document summarizes a research paper on cyber security intelligence. It discusses the growth of cybercrimes and how the internet is insecure for transmitting confidential information. Various cyber attack methods in India and worldwide are presented. The document also examines cyber security technologies, issues, and challenges. It provides details on cyber defamation law, the evolution of cyber security, and the importance of managing cyber security risks.
How Vulnerable Is Your Industry to Cyber Crime?

The truth is that any company harboring sensitive customer information could become the target of a sophisticated cyber criminal. That being said, there are certainly industries that are more vulnerable to attacks. Let’s take a closer look at four of the most vulnerable industries—financial services, healthcare, insurance and retail.
[Infographic] 5 Security Threats in Healthcare Industry ![[Infographic] 5 Security Threats in Healthcare Industry](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] 5 Security Threats in Healthcare Industry](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Ransomware was the top security threat in healthcare in 2016, accounting for 72% of malware attacks. Insiders and advanced persistent threats were also significant risks. Mobile devices posed a threat as 68% of healthcare breaches were due to lost or stolen devices. While cyberattacks were a leading cause of breaches, employee negligence through actions like clicking phishing emails or using infected USB devices also contributed to 91% of incidents starting with a phishing attack. Ransomware demands, lost productivity from downtime, and costs per leaked record added up to huge financial impacts for healthcare organizations from these top 5 security threats.
mHealth Security: Stats and Solutions

While mobile devices have improved efficiency and patient engagement while lowering costs, they’ve dramatically increased security risks. How can mHealth be safely implemented? View this slide show and learn:
• How mHealth increases security risks
• Where the greatest vulnerabilities lie
• How to improve mHealth security
mHealth Security: Stats and Solutions

While mobile devices have improved efficiency and patient engagement while lowering costs, they’ve dramatically increased security risks. How can mHealth be safely implemented? View this slide show and learn:
• How mHealth increases security risks
• Where the greatest vulnerabilities lie
• How to improve mHealth security
Cybercrime and the Healthcare Industry

This white paper discusses the various cyber threats targeting healthcare organizations and the challenges security professionals face in securing access to protected health information.
Cybercrime and the Healthcare Industry

This white paper discusses the various cyber threats targeting healthcare organizations and the challenges security professionals face in securing access to protected health information.
CYBER SECURITY : NEED OF THE HOUR

The document discusses the need for cyber security. It notes that while information and communication technology has enabled transformation, the growth of digital infrastructure and data also increases vulnerabilities to cyber attacks and threats. Ensuring the confidentiality, integrity and availability of digital systems and data is important. The objectives of cyber security include understanding principles, risks, threats, measures to prevent harm, and creating awareness. Cyber security is crucial for protecting sensitive information in governments, businesses and organizations from hackers.
Best 3 Cyber Threats in Healthcare Organizations Today | The Lifesciences Mag...

Best 3 Cyber Threats in Healthcare Organizations Today | The Lifesciences Mag...The Lifesciences Magazine
Ryan Witt, who is in charge of cyber threats in healthcare at Proofpoint, says that this is why U.S. hospital defenses have always been weak. Since attackers learned this, hospitals in the United States have been a top target. Cybercriminals continue to focus on U.S. health care, and hospital information security is always trying to catch up.Ethical Hacker Jobs Top 7 Industries Hiring Right Now.pdf

Ethical hackers are among the most recruited candidates in the job market today. Rising incidents of cyber attacks have led to a huge rise in ethical hacker jobs. Almost all the major industries, ranging from tech to e-commerce to education to finance, are increasingly looking for cybersecurity professionals who can help to detect their network and system vulnerabilities as well as enable them to create a strong line of cyber defense. The blog here offers a guide on the top industries that are hiring ethical hackers.
Cybersecurity Challenges in the Healthcare Industry.pdf

The healthcare enterprise has gone through a virtual transformation in recent years, with digital health information and IoT devices turning into integral parts of affected personal care. While these technological improvements have revolutionized healthcare transport, they have also uncovered the enterprise to a myriad of cybersecurity challenges.
Hot Topics in Privacy and Security

PYA Principal Barry Mathis presented “Hot Topics in Privacy and Security,” at the Florida Hospital Association's 14th Annual Health Care Corporate Compliance Education Retreat.
The presentation explored:
• Changes in the privacy and security ecosystem.
• Emerging technology risks and hot topics.
• What happens to hacked data.
• How to best protect data.
More Related Content
Similar to Infographic Protecting Patient Data
Cybersecurity

ybersecurity is an increasing
concern for many in the
medical cybersecurity and
information technology
professions. As computerized
devices in medical facilities
become increasingly networked
within their own walls and
with external facilities, the risk
of cyberattacks also increases,
threatening confidentiality,
safety, and well-being. This
article describes what health
care organizations and
imaging professionals should
do to minimize the risks.
Systems Thinking on a National Level, Part 2Drew David.docx

This document discusses various cybersecurity threats faced by the healthcare industry, including phishing emails, SQL injection attacks, eavesdropping, and viruses. Phishing emails are a major issue, accounting for 93% of breached healthcare data. Hackers use phishing emails that appear legitimate to trick staff into revealing sensitive information. The document also examines ways to better protect against these threats, such as password protection, data loss prevention, access controls, and staff training. Overall, the document analyzes the cybersecurity risks healthcare organizations face and ways to decrease breaches through education and prevention methods.
Privacy and Security by Design

Privacy and Security by Design Spotlight Presentation at HIMMS Privacy and Security Forum, December 5th 2016. Presented by Jeff R. Livingstone, PhD, Vice President and Global Lead, Life Sciences & Healthcare, Unisys Corporation.
Why healthcare is the biggest target for cyberattacks-converted.pdf

Sparity provides the Top Custom healthcare Software and Application development services for healthcare industries in USA and Across the Globe. We can help you build a leading-edge tech platform with the right UI/UX framework and functionalities. We Make a positive impact with modern healthcare services
Healthcare Cybercrime

Healthcare organizations will increasingly be targeted by cybercriminals in 2017, as hackers expand from health insurers to hospital networks, which can be more difficult to secure. Ransomware presents low-risk opportunities for attackers to obtain money from victims. This funding supports further research and development of more advanced attacks that may evade existing security systems. Proper security measures, contingency planning, and staff training are recommended to help organizations respond to emerging ransomware and other sophisticated cyber threats.
Digital Security 

This document discusses digital security and the importance of protecting personal information online. It defines digital security as electronic precautions to guarantee safety and protect digital identities. Examples of security measures include home alarm systems that notify of dangers and technology firewalls and Wi-Fi protections. Statistics show data breaches are common, with 43% of companies experiencing one in the past year, costing the global and US economies billions. The document urges vigilance in protecting personal information and provides tips to prevent security breaches like using unique passwords and antivirus software.
Digital security

This document discusses digital security and the importance of protecting personal information online. It defines digital security as electronic precautions to guarantee safety and protect digital identities. Examples of security measures include home alarm systems that notify of dangers and technology firewalls and Wi-Fi protections. Statistics show data breaches are common, with 43% of companies experiencing one in the past year, costing the global economy hundreds of billions annually. The document urges readers to take security seriously by using different passwords, antivirus software, and avoiding public Wi-Fi to prevent hacking and protect themselves from financial losses.
Cyber security threats and its solutions

There are a lot of cyber threats in the cyber world, but some of them are really disastrous for your system and data. Cyber threats are increasing rapidly so it is important to know how to prevent them.
Cyber Security Intelligence

This document summarizes a research paper on cyber security intelligence. It discusses the growth of cybercrimes and how the internet is insecure for transmitting confidential information. Various cyber attack methods in India and worldwide are presented. The document also examines cyber security technologies, issues, and challenges. It provides details on cyber defamation law, the evolution of cyber security, and the importance of managing cyber security risks.
How Vulnerable Is Your Industry to Cyber Crime?

The truth is that any company harboring sensitive customer information could become the target of a sophisticated cyber criminal. That being said, there are certainly industries that are more vulnerable to attacks. Let’s take a closer look at four of the most vulnerable industries—financial services, healthcare, insurance and retail.
[Infographic] 5 Security Threats in Healthcare Industry ![[Infographic] 5 Security Threats in Healthcare Industry](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] 5 Security Threats in Healthcare Industry](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Ransomware was the top security threat in healthcare in 2016, accounting for 72% of malware attacks. Insiders and advanced persistent threats were also significant risks. Mobile devices posed a threat as 68% of healthcare breaches were due to lost or stolen devices. While cyberattacks were a leading cause of breaches, employee negligence through actions like clicking phishing emails or using infected USB devices also contributed to 91% of incidents starting with a phishing attack. Ransomware demands, lost productivity from downtime, and costs per leaked record added up to huge financial impacts for healthcare organizations from these top 5 security threats.
mHealth Security: Stats and Solutions

While mobile devices have improved efficiency and patient engagement while lowering costs, they’ve dramatically increased security risks. How can mHealth be safely implemented? View this slide show and learn:
• How mHealth increases security risks
• Where the greatest vulnerabilities lie
• How to improve mHealth security
mHealth Security: Stats and Solutions

While mobile devices have improved efficiency and patient engagement while lowering costs, they’ve dramatically increased security risks. How can mHealth be safely implemented? View this slide show and learn:
• How mHealth increases security risks
• Where the greatest vulnerabilities lie
• How to improve mHealth security
Cybercrime and the Healthcare Industry

This white paper discusses the various cyber threats targeting healthcare organizations and the challenges security professionals face in securing access to protected health information.
Cybercrime and the Healthcare Industry

This white paper discusses the various cyber threats targeting healthcare organizations and the challenges security professionals face in securing access to protected health information.
CYBER SECURITY : NEED OF THE HOUR

The document discusses the need for cyber security. It notes that while information and communication technology has enabled transformation, the growth of digital infrastructure and data also increases vulnerabilities to cyber attacks and threats. Ensuring the confidentiality, integrity and availability of digital systems and data is important. The objectives of cyber security include understanding principles, risks, threats, measures to prevent harm, and creating awareness. Cyber security is crucial for protecting sensitive information in governments, businesses and organizations from hackers.
Best 3 Cyber Threats in Healthcare Organizations Today | The Lifesciences Mag...

Best 3 Cyber Threats in Healthcare Organizations Today | The Lifesciences Mag...The Lifesciences Magazine
Ryan Witt, who is in charge of cyber threats in healthcare at Proofpoint, says that this is why U.S. hospital defenses have always been weak. Since attackers learned this, hospitals in the United States have been a top target. Cybercriminals continue to focus on U.S. health care, and hospital information security is always trying to catch up.Ethical Hacker Jobs Top 7 Industries Hiring Right Now.pdf

Ethical hackers are among the most recruited candidates in the job market today. Rising incidents of cyber attacks have led to a huge rise in ethical hacker jobs. Almost all the major industries, ranging from tech to e-commerce to education to finance, are increasingly looking for cybersecurity professionals who can help to detect their network and system vulnerabilities as well as enable them to create a strong line of cyber defense. The blog here offers a guide on the top industries that are hiring ethical hackers.
Cybersecurity Challenges in the Healthcare Industry.pdf

The healthcare enterprise has gone through a virtual transformation in recent years, with digital health information and IoT devices turning into integral parts of affected personal care. While these technological improvements have revolutionized healthcare transport, they have also uncovered the enterprise to a myriad of cybersecurity challenges.
Hot Topics in Privacy and Security

PYA Principal Barry Mathis presented “Hot Topics in Privacy and Security,” at the Florida Hospital Association's 14th Annual Health Care Corporate Compliance Education Retreat.
The presentation explored:
• Changes in the privacy and security ecosystem.
• Emerging technology risks and hot topics.
• What happens to hacked data.
• How to best protect data.
Similar to Infographic Protecting Patient Data (20)
Systems Thinking on a National Level, Part 2Drew David.docx

Systems Thinking on a National Level, Part 2Drew David.docx
Why healthcare is the biggest target for cyberattacks-converted.pdf

Why healthcare is the biggest target for cyberattacks-converted.pdf
[Infographic] 5 Security Threats in Healthcare Industry ![[Infographic] 5 Security Threats in Healthcare Industry](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] 5 Security Threats in Healthcare Industry](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Infographic] 5 Security Threats in Healthcare Industry
Best 3 Cyber Threats in Healthcare Organizations Today | The Lifesciences Mag...

Best 3 Cyber Threats in Healthcare Organizations Today | The Lifesciences Mag...
Ethical Hacker Jobs Top 7 Industries Hiring Right Now.pdf

Ethical Hacker Jobs Top 7 Industries Hiring Right Now.pdf
Cybersecurity Challenges in the Healthcare Industry.pdf

Cybersecurity Challenges in the Healthcare Industry.pdf
Recently uploaded
2024 Media Preferences of Older Adults: Consumer Survey and Marketing Implica...

When it comes to creating marketing strategies that target older adults, it is crucial to have insight into their media habits and preferences. Understanding how older adults consume and use media is key to creating acquisition and retention strategies. We recently conducted our seventh annual survey to gain insight into the media preferences of older adults in 2024. Here are the survey responses and marketing implications that stood out to us.
The Ultimate Guide in Setting Up Market Research System in Health-Tech

How to effectively start market research in the health tech industry by defining objectives, crafting problem statements, selecting methods, identifying data collection sources, and setting clear timelines. This guide covers all the preliminary steps needed to lay a strong foundation for your research.
"Market Research it too text-booky, I am in the market for a decade, I am living research book" this is what the founder I met on the event claimed, few of my colleagues rolled their eyes. Its true that one cannot over look the real life experience, but one cannot out beat structured gold mine of market research.
Many 0 to 1 startup founders often overlook market research, but this critical step can make or break a venture, especially in health tech.
But Why do they skip it?
Limited resources—time, money, and manpower—are common culprits.
"In fact, a survey by CB Insights found that 42% of startups fail due to no market need, which is like building a spaceship to Mars only to realise you forgot the fuel."
Sudharsan Srinivasan
Operational Partner Pitchworks VC Studio
Overconfidence in their product’s success leads founders to assume it will naturally find its market, especially in health tech where patient needs, entire system issues and regulatory requirements are as complex as trying to perform brain surgery with a butter knife. Additionally, the pressure to launch quickly and the belief in their own intuition further contribute to this oversight. Yet, thorough market research in health tech could be the key to transforming a startup's vision into a life-saving reality, instead of a medical mishap waiting to happen.
Example of Market Research working
Innovaccer, founded by Abhinav Shashank in 2014, focuses on improving healthcare delivery through data-driven insights and interoperability solutions. Before launching their platform, Innovaccer conducted extensive market research to understand the challenges faced by healthcare organizations and the potential for innovation in healthcare IT.
Identifying Pain Points: Innovaccer surveyed healthcare providers to understand their difficulties with data integration, care coordination, and patient engagement. They found widespread frustration with siloed systems and inefficient workflows.
Competitive Analysis: Analyzed competitors offering similar solutions in healthcare analytics and interoperability. Identified gaps in comprehensive data aggregation, real-time analytics, and actionable insights.
Regulatory Compliance: Ensured their platform complied with HIPAA and other healthcare data privacy regulations. This compliance was crucial to gaining trust from healthcare providers wary of data security issues.
Customer Validation: Conducted pilot programs with several healthcare organizations to validate the platform's effectiveness in improving care outcomes and operational efficiency. Gathered feedback to refine features and user interface.
Faridkot ℂ𝕒𝕝𝕝 𝔾𝕚𝕣𝕝𝕤 7742996321 ℂ𝕒𝕝𝕝 𝔾𝕚𝕣𝕝𝕤 Faridkot

Faridkot ℂ𝕒𝕝𝕝 𝔾𝕚𝕣𝕝𝕤 7742996321 ℂ𝕒𝕝𝕝 𝔾𝕚𝕣𝕝𝕤 Faridkot
一比一原版布里斯托大学毕业证(Bristol毕业证书)学历如何办理

补办文凭【微信号:176555708】【(Bristol毕业证书)】【微信号:176555708】《成绩单、外壳、offer、真实留信官方学历认证(永久存档/真实可查)》采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
【我们承诺采用的是学校原版纸张(纸质、底色、纹路)我们拥有全套进口原装设备,特殊工艺都是采用不同机器制作,仿真度基本可以达到100%,所有工艺效果都可提前给客户展示,不满意可以根据客户要求进行调整,直到满意为止!】
【业务选择办理准则】
一、工作未确定,回国需先给父母、亲戚朋友看下文凭的情况,办理一份就读学校的毕业证【微信号:176555708】文凭即可
二、回国进私企、外企、自己做生意的情况,这些单位是不查询毕业证真伪的,而且国内没有渠道去查询国外文凭的真假,也不需要提供真实教育部认证。鉴于此,办理一份毕业证【微信号:176555708】即可
三、进国企,银行,事业单位,考公务员等等,这些单位是必需要提供真实教育部认证的,办理教育部认证所需资料众多且烦琐,所有材料您都必须提供原件,我们凭借丰富的经验,快捷的绿色通道帮您快速整合材料,让您少走弯路。
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
留信网服务项目:
1、留学生专业人才库服务(留信分析)
2、国(境)学习人员提供就业推荐信服务
3、留学人员区块链存储服务
【关于价格问题(保证一手价格)】
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
选择实体注册公司办理,更放心,更安全!我们的承诺:客户在留信官方认证查询网站查询到认证通过结果后付款,不成功不收费!
Exosome Therapy’s Regenerative Effects on Skin and Hair Rejuvenation

Explore the transformative effects of exosome therapy on skin and hair rejuvenation. Learn how these tiny vesicles deliver essential growth factors and stimulate cellular repair, offering natural solutions for aging skin and hair loss. Discover the science behind exosomes and their benefits in aesthetic dermatology.
Sunscreens, IP-I, Dr. M.N.CHISHTI, Asst Prof. Dept of Pharmaceutics, YBCCPA

Industrial Pharmacy -I, PCI syllabus
PRESSURE INJURY CARE AND MANAGEMENT FOR HCW

Cme on pressure injury care.
Credit to : PPP Abdul Manan Bin Othman.
UNIT PERKEMBANGAN PROFESYEN PPP
BAHAGIAN PEMBANGUNAN KESIHATAN KELUARGA
Solution manual for managerial accounting 18th edition by ray garrison eric n...

Solution manual for managerial accounting 18th edition by ray garrison eric n...rightmanforbloodline
Solution manual for managerial accounting 18th edition by ray garrison eric noreen and peter brewer_compressed
Solution manual for managerial accounting 18th edition by ray garrison eric noreen and peter brewer_compressedEmotional and Behavioural Problems in Children - Counselling and Family Thera...

A proprietary approach developed by bringing together the best of learning theories from Psychology, design principles from the world of visualization, and pedagogical methods from over a decade of training experience, that enables you to: Learn better, faster!
Columbia毕业证书退学办理

哥伦比亚大学毕业证成绩单(留信网认证)【176555708微信】24小时办理学位证书编号怎么查
Columbia文凭毕业证学位证(176555708微信)加急制作哥伦比亚大学毕业证认证成绩单密封邮寄|Columbia研究生毕业证书学位证书|哥伦比亚大学Office Transcript美国I20修改|Columbia Office Transcript diploma 学历认证
Columbia毕业证【微信176555708】哥伦比亚大学毕业证书原版↑制作哥伦比亚大学学历认证文凭办理哥伦比亚大学留信网认证,留学回国办理毕业证成绩单文凭学历认证【微信176555708】专业为海外学子办理毕业证成绩单、文凭制作,学历仿制,回国人员证明、做文凭,研究生、本科、硕士学历认证、留信认证、结业证、学位证书样本、美国教育部认证百分百真实存档可查】
About CentiUP - Product Information Slide.pdf

A heightened child formula, with the trio of Nano Calcium, HMO, and DHA mixed in the golden ratio, combined with NANO technology to help nourish the body deeply and comprehensively, helps children increase height, boost brain power, and improve the immune system and overall well-being.
05 CLINICAL AUDIT-ORTHO done at a peripheral.pptx

Clinical audit on pain management done at peripheral health centre
Linga Mudra(Mark of Siva) generates excessive heat within the body

Benefits:
Linga mudra generates excessive heat within the body and is very useful for dealing with colds.
It also helps in boosting the immune system and makes the body more resistant to colds and similar infections.
The benefits of penis posture also extend to the respiratory system and it can help loosen the phlegm accumulated from the throat.
This posture also helps in weight loss.
Discomfort experienced in an air conditioned room is relieved by this mudra.
Difficulty in breathing can be relieved by this mudra.
Congested nose can be relieved by this mudra immediately and one can get good sleep.
It controls the flow of the menstrual cycle. Performing the Linga mudra with the Sun Mudra gives better results – both 15 minutes each, one after the other.
When navel center is shifted from its original place, comes back to its place by this mudra.
Dr. Sherman Lai, MD — Guelph's Dedicated Medical Professional

Guelph native Dr. Sherman Lai, MD, is a committed medical practitioner renowned for his thorough medical knowledge and caring patient care. Dr. Lai guarantees that every patient receives the best possible medical care and assistance that is customized to meet their specific needs. She has years of experience and is dedicated to providing individualized health solutions.
Digital Health in India_Health Informatics Trained Manpower _DrDevTaneja_15.0...

Digital India will need a big trained army of Health Informatics educated & trained manpower in India.
Presently, generalist IT manpower does most of the work in the healthcare industry in India. Academic Health Informatics education is not readily available at school & health university level or IT education institutions in India.
We look into the evolution of health informatics and its applications in the healthcare industry.
HIMMS TIGER resources are available to assist Health Informatics education.
Indian Health universities, IT Education institutions, and the healthcare industry must proactively collaborate to start health informatics courses on a big scale. An advocacy push from various stakeholders is also needed for this goal.
Health informatics has huge employment potential and provides a big business opportunity for the healthcare industry. A big pool of trained health informatics manpower can lead to product & service innovations on a global scale in India.
About CentiUP - Introduction and Products.pdf

A heightened child formula, with the trio of Nano Calcium, HMO, and DHA mixed in the golden ratio, combined with NANO technology to help nourish the body deeply and comprehensively, helps children increase height, boost brain power, and improve the immune system and overall well-being.
Recently uploaded (20)
HEALTH ASSESSMENT IN NURSING USING THE NURSING PROCESSpptx

HEALTH ASSESSMENT IN NURSING USING THE NURSING PROCESSpptx
2024 Media Preferences of Older Adults: Consumer Survey and Marketing Implica...

2024 Media Preferences of Older Adults: Consumer Survey and Marketing Implica...
The Ultimate Guide in Setting Up Market Research System in Health-Tech

The Ultimate Guide in Setting Up Market Research System in Health-Tech
Faridkot ℂ𝕒𝕝𝕝 𝔾𝕚𝕣𝕝𝕤 7742996321 ℂ𝕒𝕝𝕝 𝔾𝕚𝕣𝕝𝕤 Faridkot

Faridkot ℂ𝕒𝕝𝕝 𝔾𝕚𝕣𝕝𝕤 7742996321 ℂ𝕒𝕝𝕝 𝔾𝕚𝕣𝕝𝕤 Faridkot
Exosome Therapy’s Regenerative Effects on Skin and Hair Rejuvenation

Exosome Therapy’s Regenerative Effects on Skin and Hair Rejuvenation
Footfalls & Heartbeats X Wearable X Breathing Survey (2).pdf

Footfalls & Heartbeats X Wearable X Breathing Survey (2).pdf
Sunscreens, IP-I, Dr. M.N.CHISHTI, Asst Prof. Dept of Pharmaceutics, YBCCPA

Sunscreens, IP-I, Dr. M.N.CHISHTI, Asst Prof. Dept of Pharmaceutics, YBCCPA
Solution manual for managerial accounting 18th edition by ray garrison eric n...

Solution manual for managerial accounting 18th edition by ray garrison eric n...
Emotional and Behavioural Problems in Children - Counselling and Family Thera...

Emotional and Behavioural Problems in Children - Counselling and Family Thera...
Linga Mudra(Mark of Siva) generates excessive heat within the body

Linga Mudra(Mark of Siva) generates excessive heat within the body
Dr. Sherman Lai, MD — Guelph's Dedicated Medical Professional

Dr. Sherman Lai, MD — Guelph's Dedicated Medical Professional
Digital Health in India_Health Informatics Trained Manpower _DrDevTaneja_15.0...

Digital Health in India_Health Informatics Trained Manpower _DrDevTaneja_15.0...
Infographic Protecting Patient Data
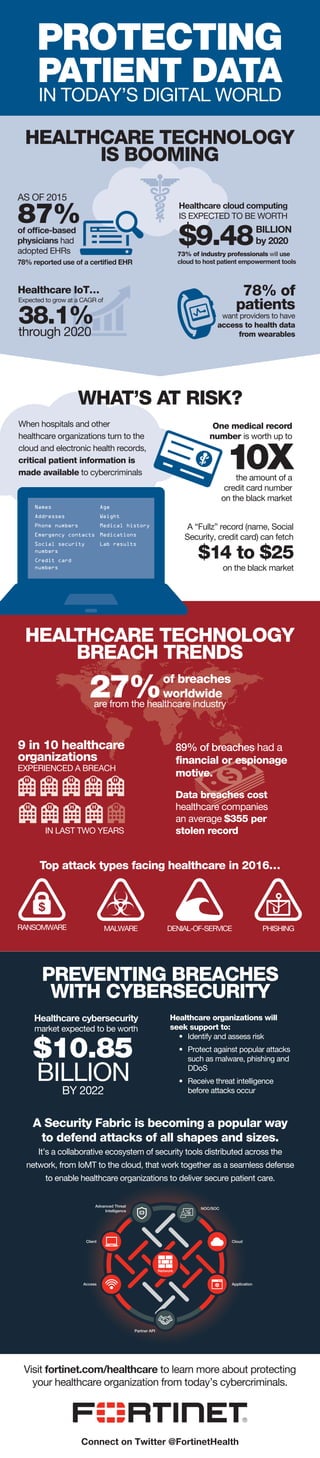
- 1. PROTECTING PATIENT DATA IN TODAY’S DIGITAL WORLD HEALTHCARE TECHNOLOGY IS BOOMING WHAT’S AT RISK? PREVENTING BREACHES WITH CYBERSECURITY HEALTHCARE TECHNOLOGY BREACH TRENDS When hospitals and other healthcare organizations turn to the cloud and electronic health records, critical patient information is made available to cybercriminals One medical record number is worth up to A “Fullz” record (name, Social Security, credit card) can fetch 89% of breaches had a financial or espionage motive. Top attack types facing healthcare in 2016… Data breaches cost healthcare companies an average $355 per stolen record Healthcare cybersecurity market expected to be worth Healthcare organizations will seek support to: • Identify and assess risk • Protect against popular attacks such as malware, phishing and DDoS • Receive threat intelligence before attacks occur A Security Fabric is becoming a popular way to defend attacks of all shapes and sizes. It’s a collaborative ecosystem of security tools distributed across the network, from IoMT to the cloud, that work together as a seamless defense to enable healthcare organizations to deliver secure patient care. Visit fortinet.com/healthcare to learn more about protecting your healthcare organization from today’s cybercriminals. AS OF 2015 87%of office-based physicians had adopted EHRs 78% reported use of a certified EHR Healthcare cloud computing IS EXPECTED TO BE WORTH BILLION by 2020 73% of industry professionals will use cloud to host patient empowerment tools $9.48 Healthcare IoT… Expected to grow at a CAGR of 38.1%through 2020 78% of patients want providers to have access to health data from wearables 10Xthe amount of a credit card number on the black market $14 to $25 on the black market Names Addresses Phone numbers Emergency contacts Social security numbers Credit card numbers Age Weight Medical history Medications Lab results 9 in 10 healthcare organizations EXPERIENCED A BREACH IN LAST TWO YEARS RANSOMWARE MALWARE DENIAL-OF-SERVICE PHISHING $10.85 BILLION BY 2022 NOC/SOC Cloud Partner API Access Client Advanced Threat Intelligence Application Network 27%are from the healthcare industry of breaches worldwide Connect on Twitter @FortinetHealth
