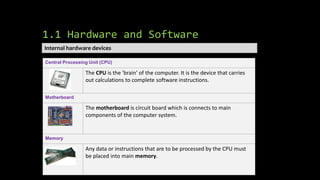
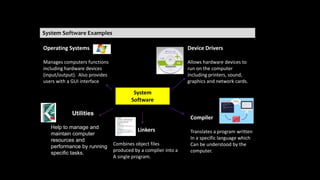
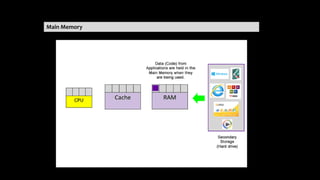
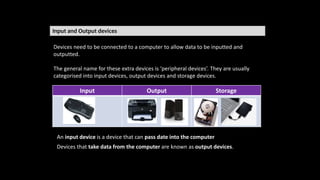
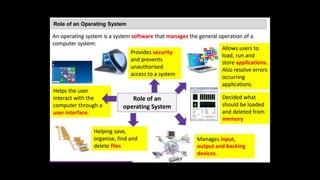
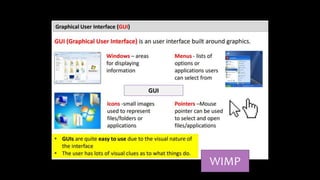
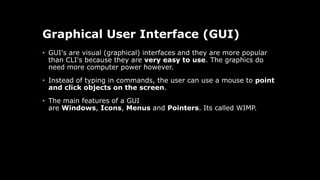
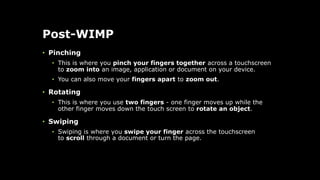
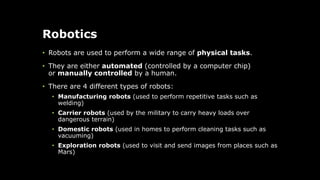
The document provides an overview of hardware components of a computer system including internal components like the CPU, motherboard, and memory as well as external components like input, output, and storage devices. It also discusses system and application software. The summary discusses the roles of the CPU, motherboard, and different types of memory in a computer system.