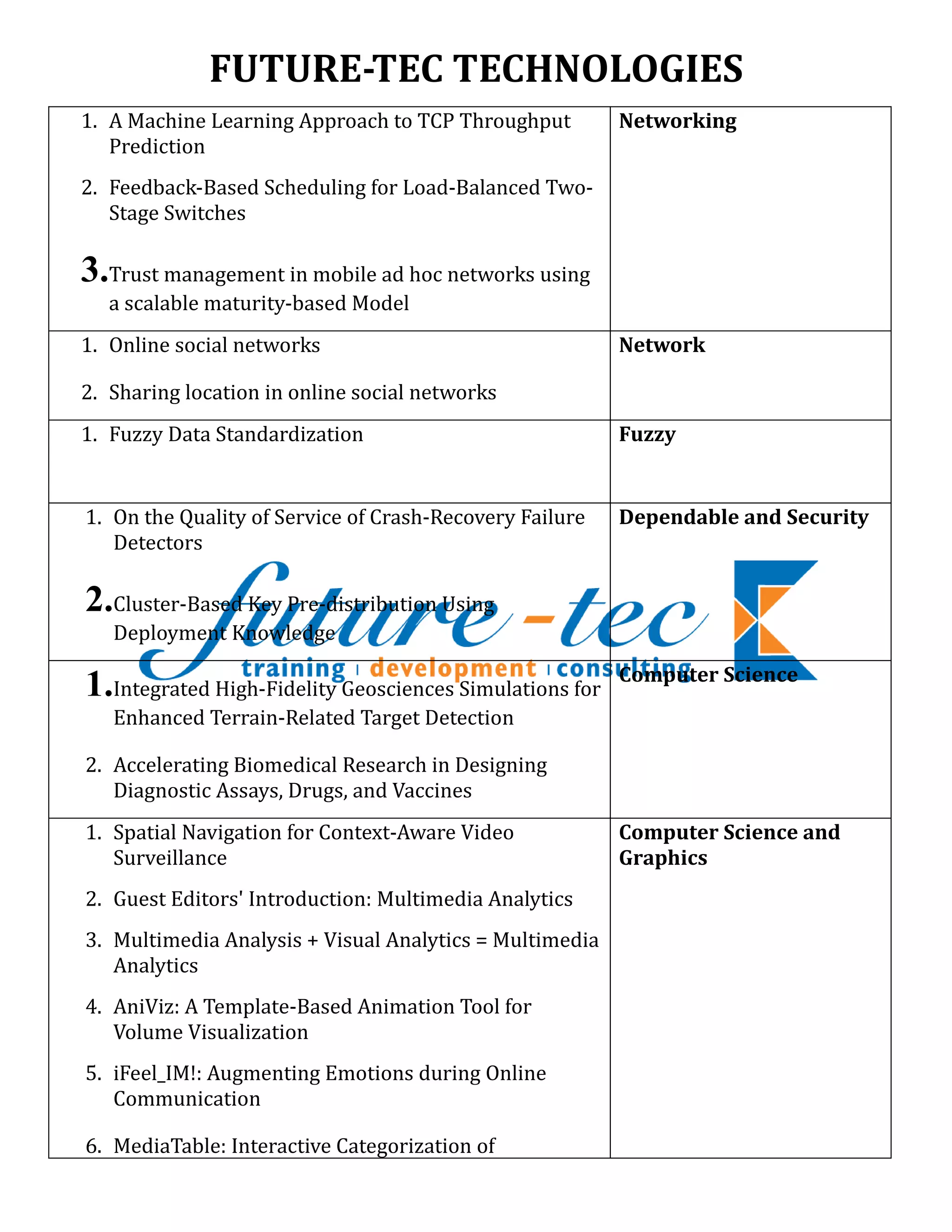
Future-Tec Technologies provides expertise in a wide range of technical areas including machine learning, networking, security, multimedia, wireless communications, software engineering, pattern analysis, signal processing, cloud computing, and learning technologies. They have experts available to discuss projects involving machine learning approaches to network throughput prediction, trust management in mobile ad hoc networks, social media analysis, fuzzy data standardization, multimedia analytics, software quality improvement, and more. For more information, contact Asha or Sharanya.
![Multimedia Collections
1. Classification of Protein-Protein Interaction Full-Text Computational Biology
Documents Using Text and Citation Network and Bioinformatics
Features
2. Exploring Species-Based Strategies for Gene
Normalization
1. Automatic Generation of Game Level Solutions as Computational
Storyboards Intelligence and AI in
Games
2. Game Bot Detection via Avatar Trajectory Analysis
3. The Parametrized Probabilistic Finite-State
Transducer Probe Game Player Fingerprint Model
1. Full-Reference Video Quality Metric for Fully Broadcasting
Scalable and Mobile SVC Content
1. Understanding Wi-Fi 2.0: from the economical Wireless Communications
perspective of wireless service providers [Dynamic
Spectrum Management]
2. Efficient routing for international mobile call setup
[Accepted from Open Call]
3. IEEE 802.11E QoS and power saving features
overview and analysis of combined performance
[Accepted from Open Call]
4. Achieving Secret Communication for Fast Rayleigh
Fading Channels
1. Using a web-based tool to define and implement Software
software process improvement initiatives in a small
industrial setting
2. Including both static and dynamic typing in the
same programming language
3. Design principles of web-based distance education
system and sample application in Afyon Kocatepe
University
4. Component co-evolution and component](https://image.slidesharecdn.com/ieee2010projecttitles-101208073300-phpapp02/85/Ieee-2010-project-titles-2-320.jpg)




