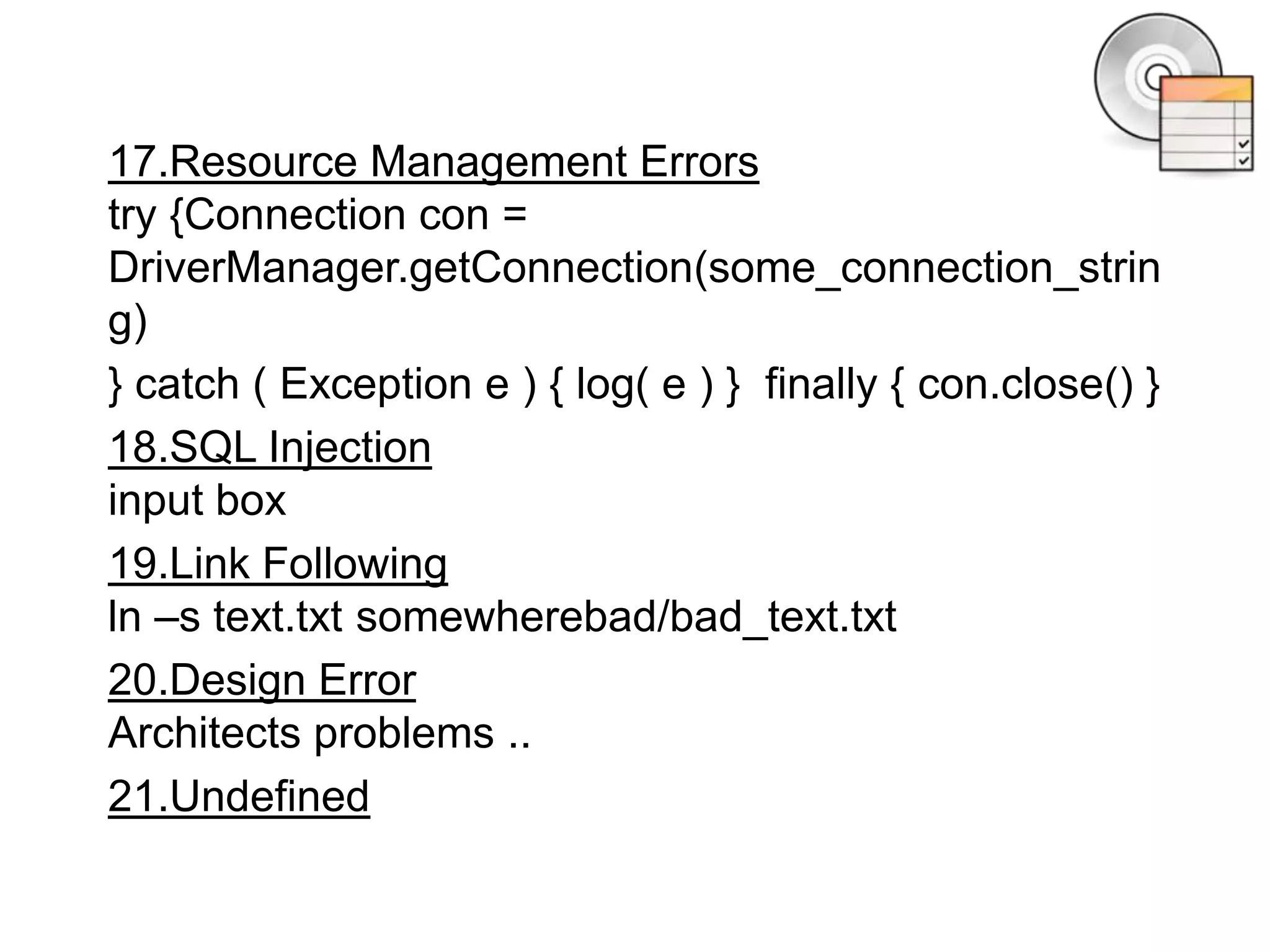
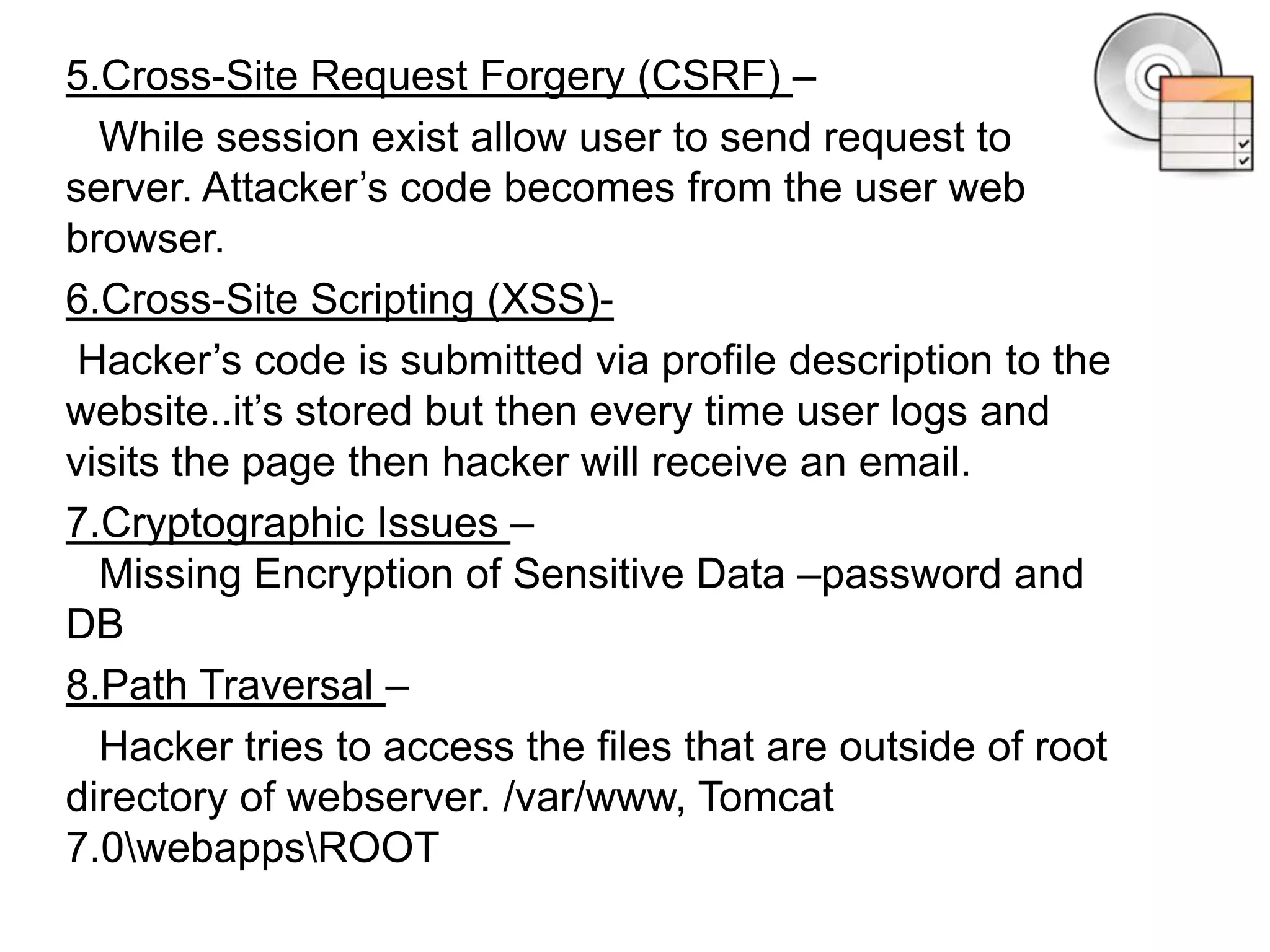
This document summarizes common software vulnerabilities and how to prevent them. It identifies 21 specific vulnerabilities including authentication issues, credential management problems, buffer errors, cross-site scripting, cryptographic issues, path traversal, code injection, format string vulnerabilities, configuration issues, information leaks, input validation errors, numeric errors, OS command injections, race conditions, resource management mistakes, SQL injection, link following vulnerabilities, design errors, and undefined vulnerabilities. It provides examples of each type of issue and recommends addressing them through strategies like access control, input validation, encryption, and avoiding race conditions.


![1.Authentication Issues
-log in, set cookie but third person sets the cookie
and by pass.
2. Credentials Management
Poor passwords, password aging too long , weak
password recovery etc.
2.Permissions, Privileges, and Access Control
Access control, ownership of user/passwords etc
3.Buffer Errors
char array[15];
for( int i = 0; i < 64; i++ )
array[i] = (char)i;](https://image.slidesharecdn.com/identifyingfixingthemostcommonsoftwarevulnerabilities-140210210216-phpapp02/75/Identifying-fixing-the-most-common-software-vulnerabilities-3-2048.jpg)
![9. Code Injection$userTyped = $_GET[“userInputInfo"];
$handle = fopen($someFile, "a+");
fwrite($handle, '$ userTyped '<hr>n");
fclose($handle);
%3C?php%20system(%22/bin/rm%20*%22);?%3E
10.Format String Vulnerabilitysnprintf(buf,128,argv[1]); ,printf(lastname);
11.ConfigurationServer Misconfiguration , Application Misconfiguration
12.Information Leak / Disclosure-](https://image.slidesharecdn.com/identifyingfixingthemostcommonsoftwarevulnerabilities-140210210216-phpapp02/75/Identifying-fixing-the-most-common-software-vulnerabilities-5-2048.jpg)
![13.Input Validation
public static final double cost = 100.00;
int orderedCount =
currentUser.getAttribute(“countUserOrderNum");
double total = price * orderedCount;
chargeCreditCard(total);
14.Numeric Errors
System.out.println( " averages " + total/count );
15.OS Command Injections
$clientName = $_POST[“client"];
$command = 'ls -l /home/' . $clientName;
system($command); //;rm -rf /
16.Race Conditions
Thread1
Thread 2](https://image.slidesharecdn.com/identifyingfixingthemostcommonsoftwarevulnerabilities-140210210216-phpapp02/75/Identifying-fixing-the-most-common-software-vulnerabilities-6-2048.jpg)