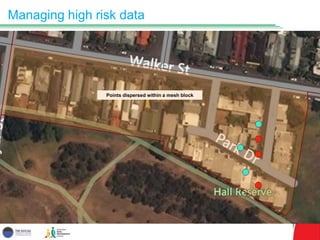
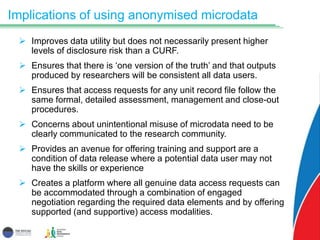
The document discusses the balance between disclosure risks and data utility in the context of microdata management, specifically focusing on the Australian Early Development Census (AEDC) conducted by the Social Research Centre. It outlines traditional and alternative approaches to risk management, emphasizing the need for shared responsibility between data custodians and researchers while ensuring data protection and professional conduct. Additionally, it highlights the potential for enhanced data utility through anonymization techniques while addressing concerns about misuse and the importance of proper training and access protocols.