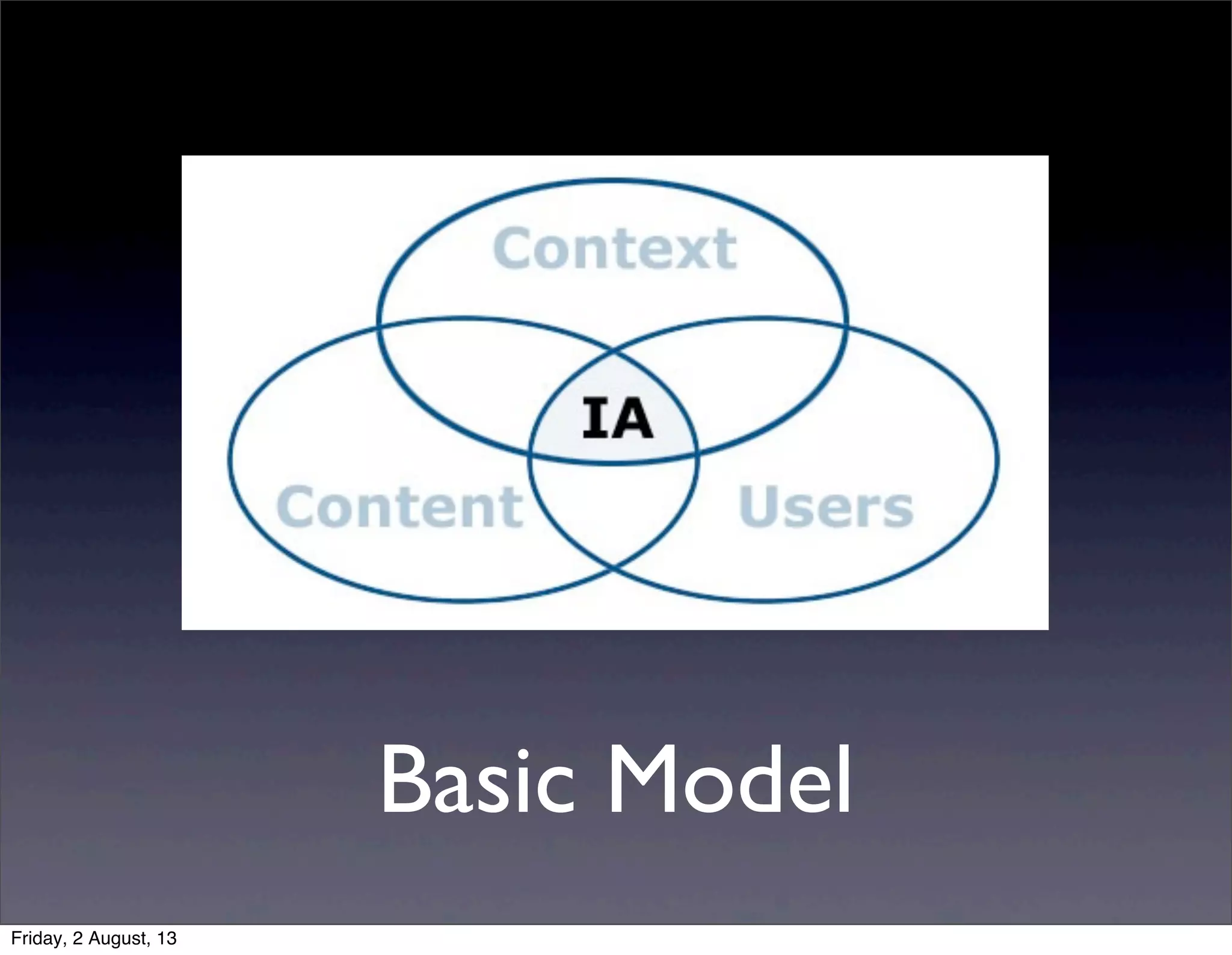
This document provides an overview of information architecture (IA) presented by KeroYu. IA is defined as the structural design of shared information environments, combining organization, labeling, search, and navigation systems. The presentation discusses the basics of IA, including structuring, organizing and labeling content. It emphasizes understanding user needs and information-seeking behaviors to inform the design of navigation, search and other systems. Effective IA can save time and money by helping users efficiently find needed information.