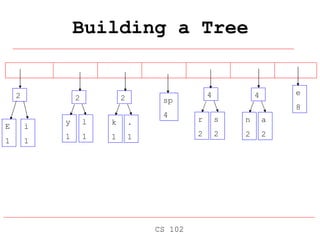
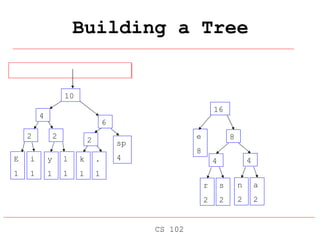
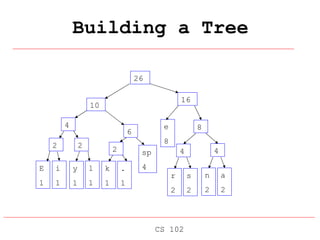
Huffman coding is a data compression technique that uses variable-length code words to encode characters based on their frequency of occurrence. It involves building a Huffman tree from the character frequencies, where more common characters are encoded with shorter code words. The tree is then traversed to assign each character a unique code, and the text is re-encoded using the new variable-length codes to achieve compression by replacing frequent short codes for less frequent longer codes.