How to Secure Your Mobile Commerce App.pdf
•
0 likes•32 views
M-commerce (mobile commerce) is the buying and selling of goods and services through wireless handheld devices such as smartphones and tablets. Basically, transactions that happen online via a mobile or tablet are known as mobile commerce.
Report
Share
Report
Share
Download to read offline
Recommended
Are Mobile Banking Apps Safe?

Mobile phones are a quintessential part of our lives; they keep us connected with friends and family and make our lives more convenient every day. As the global Covid-19 pandemic encouraged people to remain safely indoors, there was a large increase in the number of Mobile Banking users. From depositing checks remotely to having 24*7 access to your bank account, the convenience and the utility of Mobile Banking are the reasons behind this popularity. And yet many people still wonder if Mobile Banking is Safe. If you are someone who is undecided about adopting Mobile Banking because of concerns about the security of Mobile Banking then here is the answer to your question ‘Are Mobile Banking Apps really safe?’ covered in this article. The best way to do this is to look at the risks involved with Mobile Banking and what organizations and customers can do about it.
Mobile App Security Protecting Your App from Cyber Threats.edited.docx

This has the potential to deceive individuals into downloading the mobile app to obtain absolutely nothing and enable the provider another opportunity to turn individuals into loyal customers. The use of in-app advertising is another prevalent strategy that lets you showcase relevant advertisements from within the application.
The 10 Commandments Security Of Mobile App Development

Ensure the security of your mobile apps with our "10 Commandments of Mobile App Security". From ideation to launch, we emphasize incorporating robust security measures, utilizing advanced encryption techniques, and minimizing data storage for utmost protection. Get an insight into how we craft secure, functional, and user-friendly mobile applications at Mobio Solutions.
Top Practices You Need To Develop Secure Mobile Apps.

Developers prefer to store sensitive data in the device’s local memory to protect users’ data. However, it is best not to store sensitive data, as it could increase security risks. You have two options: keep the data in encrypted containers or key chains, but if you don’t have any other choice, it is best to do so. You can also reduce the log by using the auto-delete option, which deletes data automatically after a set time.
With the growing risk of malicious activity, mobile app security has become a top concern for developers. Users are less likely to trust unreliable apps. The above best practices will answer your concerns about creating a secure mobile application by the top mobile app development company in South Africa for your customers.
Mobile App Security Best Practices Protecting User Data.pdf

Mobile application development is the process of creating software applications that run on a mobile device. If You want to expand your business just choose GMA Technologies as a top mobile application development services Company. Build yours, worry-free. Get award-winning tech, with a fixed price and delivery date before you start. Visit us: https://www.gmatechnology.com/
Top Cybersecurity Challenges Faced By Fintech Applications! .pdf

When developing a fintech application, the essential thing to consider is security of the users. Unfortunately, creating a secure fintech application is not an easy task. It is time-consuming, complicated & expensive work to perform. Read more... https://www.best7.io/top-cybersecurity-challenges-faced-by-fintech-applications/
7 Steps to Boosting Your App Security in 2022

Mobile apps are the primary cause behind this rise in mobile productivity. These virtual technologies connect servers and APIs all over the world to provide users with services, data, convenience, and value. For information, visit our website :
https://www.cerebruminfotech.com/
Recommended
Are Mobile Banking Apps Safe?

Mobile phones are a quintessential part of our lives; they keep us connected with friends and family and make our lives more convenient every day. As the global Covid-19 pandemic encouraged people to remain safely indoors, there was a large increase in the number of Mobile Banking users. From depositing checks remotely to having 24*7 access to your bank account, the convenience and the utility of Mobile Banking are the reasons behind this popularity. And yet many people still wonder if Mobile Banking is Safe. If you are someone who is undecided about adopting Mobile Banking because of concerns about the security of Mobile Banking then here is the answer to your question ‘Are Mobile Banking Apps really safe?’ covered in this article. The best way to do this is to look at the risks involved with Mobile Banking and what organizations and customers can do about it.
Mobile App Security Protecting Your App from Cyber Threats.edited.docx

This has the potential to deceive individuals into downloading the mobile app to obtain absolutely nothing and enable the provider another opportunity to turn individuals into loyal customers. The use of in-app advertising is another prevalent strategy that lets you showcase relevant advertisements from within the application.
The 10 Commandments Security Of Mobile App Development

Ensure the security of your mobile apps with our "10 Commandments of Mobile App Security". From ideation to launch, we emphasize incorporating robust security measures, utilizing advanced encryption techniques, and minimizing data storage for utmost protection. Get an insight into how we craft secure, functional, and user-friendly mobile applications at Mobio Solutions.
Top Practices You Need To Develop Secure Mobile Apps.

Developers prefer to store sensitive data in the device’s local memory to protect users’ data. However, it is best not to store sensitive data, as it could increase security risks. You have two options: keep the data in encrypted containers or key chains, but if you don’t have any other choice, it is best to do so. You can also reduce the log by using the auto-delete option, which deletes data automatically after a set time.
With the growing risk of malicious activity, mobile app security has become a top concern for developers. Users are less likely to trust unreliable apps. The above best practices will answer your concerns about creating a secure mobile application by the top mobile app development company in South Africa for your customers.
Mobile App Security Best Practices Protecting User Data.pdf

Mobile application development is the process of creating software applications that run on a mobile device. If You want to expand your business just choose GMA Technologies as a top mobile application development services Company. Build yours, worry-free. Get award-winning tech, with a fixed price and delivery date before you start. Visit us: https://www.gmatechnology.com/
Top Cybersecurity Challenges Faced By Fintech Applications! .pdf

When developing a fintech application, the essential thing to consider is security of the users. Unfortunately, creating a secure fintech application is not an easy task. It is time-consuming, complicated & expensive work to perform. Read more... https://www.best7.io/top-cybersecurity-challenges-faced-by-fintech-applications/
7 Steps to Boosting Your App Security in 2022

Mobile apps are the primary cause behind this rise in mobile productivity. These virtual technologies connect servers and APIs all over the world to provide users with services, data, convenience, and value. For information, visit our website :
https://www.cerebruminfotech.com/
How to Improve Your Mobile App Security Knowledge

With the increasing use of smart phones all across the world has created demands of high-end functionality, an uncompromising handiness and extra ease with less effort by its users which has boosted demand of more innovative mobile apps.
Security in Mobile App Development Protecting User Data and Preventing Cybera...

In the era of digitalization, mobile apps have become an integral part of our daily lives. From banking and shopping to social networking and entertainment, we rely on mobile apps for convenience and accessibility. However, with the increase in cyber threats and data breaches, ensuring the security of user data has become a paramount concern for both app developers and users.
How to build a highly secure fin tech application

Indeed, The FinTech industry is a specific sector where developing a successful mobile solution necessitates some extraordinary measures to capture clients’ loyalty. The takeaway is that a good FinTech app is more than simply an excellent companion.
Tips To Protect Your Mobile App from Hackers.pdf

Given this, it's imperative for companies to think about mobile app security for both themselves and their customers. To do this, you must collaborate with the best mobile app development company in Bangalore that is familiar with cybersecurity.
The Importance of Mobile App Security

Without proper security measures, users can become victims of identity theft, financial fraud, and other cyberattacks. Learn the importance of mobile app security here. Also, our expert app developers can build you a mobile app for your business implementing the security measures to keep you from danger.
Connect today to partner with us- https://oprim.ca/application-development/ | info@oprim.ca | +18335567746
Tips of Mobile Application Security

Mobile app security is not dependent on a single factor but on several interdependent factors. so some tips for mobile application security.
OWASP Mobile Security: Top 10 Risks for 2017

The OWASP Mobile Top 10 is a nice start for any developer or a security professional, but the road is still ahead and there is so much to do to destroy most of the possible doors that hackers can use to find out about app’s vulnerabilities. We look forward to the OWASP to continue their work, but let’s not stay on the sidelines!
Overcome Security Threats Affecting Mobile Financial Solutions 2020

The financial services industry, like most businesses and consumers, has become dependent on mobile communications as a way to conduct business, manage customer information, exchange data, and work with customers. Due to its convenience, speed and ease, the electronic form of money has gained tremendous popularity among ordinary people and businesses
How to Build Secure Mobile Apps.pdf

Hyena has built-in security, user authentication, and automated upgrades, among other features. Hyena has built-in security, user authentication, and automated upgrades, among other features. This is probably all you need to create a secure mobile app from scratch. The Hyena app includes security cover for DIY apps, enterprise apps, business apps, in-house employee apps, and more.
Running head mobile application security1mobile application se.docx

Running head: mobile application security 1
mobile application security 8
Project Report On Mobile Application Security
ISOL534 Application Security
Submitted By
Guided By Dr. Suanu Bliss Wikina
Contents
Executive Summary……………………………………………………………………...3
Introduction………………………………………………………………………..……..4
Types of Mobile Applications……………………………………………………..……..5
Importance of Mobile Application Security…………………………………..………..7
Recommendations for Using Mobile Applications……………………………..………9
Top Three Best Mobile Security Applications…………………………………..…….10
Conclusion………………………………………………………………………………12
References……………………………………………………………………………….13
Executive Summary
This report is about the mobile application security and importance to have installed the mobile application security in the mobile gadgets like the Smartphones or the tablet computers. The use of mobile gadgets have increased in the recent past and it has also brought danger to our personal information as well which are generally saved in our mobiles like the credit card information, contacts, business particulars, etc. Therefore, the importance of mobile application security shall be discussed in detail in the report so that ho we can save our personal data from the external threats in the shape of malwares.
Keywords: Types of Mobile Applications, Importance of Mobile Application Security, Recommendations for using Mobile Applications, Best Mobile Security Applications.
Introduction:
The mobile applications play an important role in our daily life and they are helpful in managing our day to day needs like online banking, chatting to other friends and family, share of online information including photos, banking transactions, codes, etc. However, we are not aware of one thing and that is threats in the shape of malware. The malware are the online threats that can put your personal information and data on risk and you may suffer in various manners like monetary losses, bad repute, etc.
The mobile applications allow users to have mini computers in their mobile phones and enjoy the services. The smart phones allows many built-in applications in their mobile phones which are basic in nature like calculator, calendar, camera, libraries, etc. and the users may download unlimited applications in their mobile phones like emails, video recorders, MP3 players, Medical apps, online organizational applications for sale & purchase of good online, banking applications and most importantly the games. The main advantage is that you can avail functions of such applications without any computer at anywhere with the help of mobile phone and internet.
The previous approach for developing applications were for the desktop computers and laptops but now the trend has changed and the developers are following the approach “Mobile-First” and they are developing such applications that can easily be downloaded on the mobile phones. It is also reported that about 197 Billion different mobile applications are .
Running head mobile application security1mobile application se.docx

Running head: mobile application security 1
mobile application security 8
Project Report On Mobile Application Security
ISOL534 Application Security
Submitted By
Guided By Dr. Suanu Bliss Wikina
Contents
Executive Summary……………………………………………………………………...3
Introduction………………………………………………………………………..……..4
Types of Mobile Applications……………………………………………………..……..5
Importance of Mobile Application Security…………………………………..………..7
Recommendations for Using Mobile Applications……………………………..………9
Top Three Best Mobile Security Applications…………………………………..…….10
Conclusion………………………………………………………………………………12
References……………………………………………………………………………….13
Executive Summary
This report is about the mobile application security and importance to have installed the mobile application security in the mobile gadgets like the Smartphones or the tablet computers. The use of mobile gadgets have increased in the recent past and it has also brought danger to our personal information as well which are generally saved in our mobiles like the credit card information, contacts, business particulars, etc. Therefore, the importance of mobile application security shall be discussed in detail in the report so that ho we can save our personal data from the external threats in the shape of malwares.
Keywords: Types of Mobile Applications, Importance of Mobile Application Security, Recommendations for using Mobile Applications, Best Mobile Security Applications.
Introduction:
The mobile applications play an important role in our daily life and they are helpful in managing our day to day needs like online banking, chatting to other friends and family, share of online information including photos, banking transactions, codes, etc. However, we are not aware of one thing and that is threats in the shape of malware. The malware are the online threats that can put your personal information and data on risk and you may suffer in various manners like monetary losses, bad repute, etc.
The mobile applications allow users to have mini computers in their mobile phones and enjoy the services. The smart phones allows many built-in applications in their mobile phones which are basic in nature like calculator, calendar, camera, libraries, etc. and the users may download unlimited applications in their mobile phones like emails, video recorders, MP3 players, Medical apps, online organizational applications for sale & purchase of good online, banking applications and most importantly the games. The main advantage is that you can avail functions of such applications without any computer at anywhere with the help of mobile phone and internet.
The previous approach for developing applications were for the desktop computers and laptops but now the trend has changed and the developers are following the approach “Mobile-First” and they are developing such applications that can easily be downloaded on the mobile phones. It is also reported that about 197 Billion different mobile applications are .
Staying Ahead of Online Threats How PayWithRING Protects Users from Fraud and...

Leading Fintech like the RING app strongly resonates with the centric approach and does not promote fraudulent activities. Hence, it is important to act against rumours like paywithRING Fraud or paywithRING scam that are created to damage the reputation.
Mobile App Security How Bahrain Development Companies Ensure Protection.edite...

Mobile apps have become integral to our daily lives. From ordering food and booking rides to managing finances and staying connected with loved ones, there seems to be an app for everything. Behind the scenes, however, a technological revolution is taking place, completely transforming the way mobile apps are developed. The introduction of artificial intelligence (AI) and machine learning has brought about a paradigm shift in the app development process, enhancing efficiency, personalization, and user experience like never before.
Mobile Development Service in Kerala | Mobile Application In Cochin | Best Mo...

Mobile App Developers in Cochin, We are expertise in Mobile Application Development, Browser based Mobile Application Development and Web based mobile applications .
Delivering secure mobile financial services (MFS) - "Frictionless" vs diligence

How do you balance UX and security for mobile banking apps? Check out the slides originally presented on May 2 sharing FFIEC guidance and a study of vulnerabilities 30 mobile banking apps (15 iOS and 15 Android) from 15 financial institutions.
Mobile banking issues in banking and insurance

please use this for learning not for coping this was done by me at the time my study of MBA in finance specialization and all this work was not copied
Top Mobile App Trends Changing Technology and Evolution of Customer's Expecta...

Top Mobile App Trends Changing Technology and Evolution of Customer's Expecta...Hepto Software Company
The rise of mobile apps has made life simpler, as customers can now purchase products from their favorite companies with a few taps on their phones. People are spending more time on mobile apps, with an average of 4.2 hours being spent on them daily, which is a 30% increase from two years prior.Some Mistakes in Marketing Strategy.pdf

With the emergence of covid norms and people strictly following the social distancing practices there is an increased amount of stores shifting to the ecommerce website and apps.
If you are looking for an expert ecommerce website development company in India connect with Ozonesoft Solutions.
How to Secure Your Mobile Commerce App?

Mobile commerce developers are constantly dealing with cyber-attacks and harmful viruses, thus security is a top priority. Hackers are always attempting to gain access to your mobile commerce app through security flaws and cause you harm.
More Related Content
Similar to How to Secure Your Mobile Commerce App.pdf
How to Improve Your Mobile App Security Knowledge

With the increasing use of smart phones all across the world has created demands of high-end functionality, an uncompromising handiness and extra ease with less effort by its users which has boosted demand of more innovative mobile apps.
Security in Mobile App Development Protecting User Data and Preventing Cybera...

In the era of digitalization, mobile apps have become an integral part of our daily lives. From banking and shopping to social networking and entertainment, we rely on mobile apps for convenience and accessibility. However, with the increase in cyber threats and data breaches, ensuring the security of user data has become a paramount concern for both app developers and users.
How to build a highly secure fin tech application

Indeed, The FinTech industry is a specific sector where developing a successful mobile solution necessitates some extraordinary measures to capture clients’ loyalty. The takeaway is that a good FinTech app is more than simply an excellent companion.
Tips To Protect Your Mobile App from Hackers.pdf

Given this, it's imperative for companies to think about mobile app security for both themselves and their customers. To do this, you must collaborate with the best mobile app development company in Bangalore that is familiar with cybersecurity.
The Importance of Mobile App Security

Without proper security measures, users can become victims of identity theft, financial fraud, and other cyberattacks. Learn the importance of mobile app security here. Also, our expert app developers can build you a mobile app for your business implementing the security measures to keep you from danger.
Connect today to partner with us- https://oprim.ca/application-development/ | info@oprim.ca | +18335567746
Tips of Mobile Application Security

Mobile app security is not dependent on a single factor but on several interdependent factors. so some tips for mobile application security.
OWASP Mobile Security: Top 10 Risks for 2017

The OWASP Mobile Top 10 is a nice start for any developer or a security professional, but the road is still ahead and there is so much to do to destroy most of the possible doors that hackers can use to find out about app’s vulnerabilities. We look forward to the OWASP to continue their work, but let’s not stay on the sidelines!
Overcome Security Threats Affecting Mobile Financial Solutions 2020

The financial services industry, like most businesses and consumers, has become dependent on mobile communications as a way to conduct business, manage customer information, exchange data, and work with customers. Due to its convenience, speed and ease, the electronic form of money has gained tremendous popularity among ordinary people and businesses
How to Build Secure Mobile Apps.pdf

Hyena has built-in security, user authentication, and automated upgrades, among other features. Hyena has built-in security, user authentication, and automated upgrades, among other features. This is probably all you need to create a secure mobile app from scratch. The Hyena app includes security cover for DIY apps, enterprise apps, business apps, in-house employee apps, and more.
Running head mobile application security1mobile application se.docx

Running head: mobile application security 1
mobile application security 8
Project Report On Mobile Application Security
ISOL534 Application Security
Submitted By
Guided By Dr. Suanu Bliss Wikina
Contents
Executive Summary……………………………………………………………………...3
Introduction………………………………………………………………………..……..4
Types of Mobile Applications……………………………………………………..……..5
Importance of Mobile Application Security…………………………………..………..7
Recommendations for Using Mobile Applications……………………………..………9
Top Three Best Mobile Security Applications…………………………………..…….10
Conclusion………………………………………………………………………………12
References……………………………………………………………………………….13
Executive Summary
This report is about the mobile application security and importance to have installed the mobile application security in the mobile gadgets like the Smartphones or the tablet computers. The use of mobile gadgets have increased in the recent past and it has also brought danger to our personal information as well which are generally saved in our mobiles like the credit card information, contacts, business particulars, etc. Therefore, the importance of mobile application security shall be discussed in detail in the report so that ho we can save our personal data from the external threats in the shape of malwares.
Keywords: Types of Mobile Applications, Importance of Mobile Application Security, Recommendations for using Mobile Applications, Best Mobile Security Applications.
Introduction:
The mobile applications play an important role in our daily life and they are helpful in managing our day to day needs like online banking, chatting to other friends and family, share of online information including photos, banking transactions, codes, etc. However, we are not aware of one thing and that is threats in the shape of malware. The malware are the online threats that can put your personal information and data on risk and you may suffer in various manners like monetary losses, bad repute, etc.
The mobile applications allow users to have mini computers in their mobile phones and enjoy the services. The smart phones allows many built-in applications in their mobile phones which are basic in nature like calculator, calendar, camera, libraries, etc. and the users may download unlimited applications in their mobile phones like emails, video recorders, MP3 players, Medical apps, online organizational applications for sale & purchase of good online, banking applications and most importantly the games. The main advantage is that you can avail functions of such applications without any computer at anywhere with the help of mobile phone and internet.
The previous approach for developing applications were for the desktop computers and laptops but now the trend has changed and the developers are following the approach “Mobile-First” and they are developing such applications that can easily be downloaded on the mobile phones. It is also reported that about 197 Billion different mobile applications are .
Running head mobile application security1mobile application se.docx

Running head: mobile application security 1
mobile application security 8
Project Report On Mobile Application Security
ISOL534 Application Security
Submitted By
Guided By Dr. Suanu Bliss Wikina
Contents
Executive Summary……………………………………………………………………...3
Introduction………………………………………………………………………..……..4
Types of Mobile Applications……………………………………………………..……..5
Importance of Mobile Application Security…………………………………..………..7
Recommendations for Using Mobile Applications……………………………..………9
Top Three Best Mobile Security Applications…………………………………..…….10
Conclusion………………………………………………………………………………12
References……………………………………………………………………………….13
Executive Summary
This report is about the mobile application security and importance to have installed the mobile application security in the mobile gadgets like the Smartphones or the tablet computers. The use of mobile gadgets have increased in the recent past and it has also brought danger to our personal information as well which are generally saved in our mobiles like the credit card information, contacts, business particulars, etc. Therefore, the importance of mobile application security shall be discussed in detail in the report so that ho we can save our personal data from the external threats in the shape of malwares.
Keywords: Types of Mobile Applications, Importance of Mobile Application Security, Recommendations for using Mobile Applications, Best Mobile Security Applications.
Introduction:
The mobile applications play an important role in our daily life and they are helpful in managing our day to day needs like online banking, chatting to other friends and family, share of online information including photos, banking transactions, codes, etc. However, we are not aware of one thing and that is threats in the shape of malware. The malware are the online threats that can put your personal information and data on risk and you may suffer in various manners like monetary losses, bad repute, etc.
The mobile applications allow users to have mini computers in their mobile phones and enjoy the services. The smart phones allows many built-in applications in their mobile phones which are basic in nature like calculator, calendar, camera, libraries, etc. and the users may download unlimited applications in their mobile phones like emails, video recorders, MP3 players, Medical apps, online organizational applications for sale & purchase of good online, banking applications and most importantly the games. The main advantage is that you can avail functions of such applications without any computer at anywhere with the help of mobile phone and internet.
The previous approach for developing applications were for the desktop computers and laptops but now the trend has changed and the developers are following the approach “Mobile-First” and they are developing such applications that can easily be downloaded on the mobile phones. It is also reported that about 197 Billion different mobile applications are .
Staying Ahead of Online Threats How PayWithRING Protects Users from Fraud and...

Leading Fintech like the RING app strongly resonates with the centric approach and does not promote fraudulent activities. Hence, it is important to act against rumours like paywithRING Fraud or paywithRING scam that are created to damage the reputation.
Mobile App Security How Bahrain Development Companies Ensure Protection.edite...

Mobile apps have become integral to our daily lives. From ordering food and booking rides to managing finances and staying connected with loved ones, there seems to be an app for everything. Behind the scenes, however, a technological revolution is taking place, completely transforming the way mobile apps are developed. The introduction of artificial intelligence (AI) and machine learning has brought about a paradigm shift in the app development process, enhancing efficiency, personalization, and user experience like never before.
Mobile Development Service in Kerala | Mobile Application In Cochin | Best Mo...

Mobile App Developers in Cochin, We are expertise in Mobile Application Development, Browser based Mobile Application Development and Web based mobile applications .
Delivering secure mobile financial services (MFS) - "Frictionless" vs diligence

How do you balance UX and security for mobile banking apps? Check out the slides originally presented on May 2 sharing FFIEC guidance and a study of vulnerabilities 30 mobile banking apps (15 iOS and 15 Android) from 15 financial institutions.
Mobile banking issues in banking and insurance

please use this for learning not for coping this was done by me at the time my study of MBA in finance specialization and all this work was not copied
Top Mobile App Trends Changing Technology and Evolution of Customer's Expecta...

Top Mobile App Trends Changing Technology and Evolution of Customer's Expecta...Hepto Software Company
The rise of mobile apps has made life simpler, as customers can now purchase products from their favorite companies with a few taps on their phones. People are spending more time on mobile apps, with an average of 4.2 hours being spent on them daily, which is a 30% increase from two years prior.Similar to How to Secure Your Mobile Commerce App.pdf (20)
Security in Mobile App Development Protecting User Data and Preventing Cybera...

Security in Mobile App Development Protecting User Data and Preventing Cybera...
Overcome Security Threats Affecting Mobile Financial Solutions 2020

Overcome Security Threats Affecting Mobile Financial Solutions 2020
Running head mobile application security1mobile application se.docx

Running head mobile application security1mobile application se.docx
Running head mobile application security1mobile application se.docx

Running head mobile application security1mobile application se.docx
Staying Ahead of Online Threats How PayWithRING Protects Users from Fraud and...

Staying Ahead of Online Threats How PayWithRING Protects Users from Fraud and...
Mobile App Security How Bahrain Development Companies Ensure Protection.edite...

Mobile App Security How Bahrain Development Companies Ensure Protection.edite...
Mobile Development Service in Kerala | Mobile Application In Cochin | Best Mo...

Mobile Development Service in Kerala | Mobile Application In Cochin | Best Mo...
Delivering secure mobile financial services (MFS) - "Frictionless" vs diligence

Delivering secure mobile financial services (MFS) - "Frictionless" vs diligence
Top Mobile App Trends Changing Technology and Evolution of Customer's Expecta...

Top Mobile App Trends Changing Technology and Evolution of Customer's Expecta...
More from OZONESOFT Solutions
Some Mistakes in Marketing Strategy.pdf

With the emergence of covid norms and people strictly following the social distancing practices there is an increased amount of stores shifting to the ecommerce website and apps.
If you are looking for an expert ecommerce website development company in India connect with Ozonesoft Solutions.
How to Secure Your Mobile Commerce App?

Mobile commerce developers are constantly dealing with cyber-attacks and harmful viruses, thus security is a top priority. Hackers are always attempting to gain access to your mobile commerce app through security flaws and cause you harm.
How Can I Rank My Website On Google.pdf

SEO is a huge procedure which requires many different activities and thus needs to be performed by a specialist. Currently there is a myth in the market that SEO can be done by one out there and that if you are not capable of performing any technical work you can start your career in digital marketing from the next day without any knowledge about the same.
Social Media Trends In 2022.pdf

A news which once became viral through news channels now becomes viral due to updates in social media platforms and thus every big industry has now shifted their concentration from google to social media.
Here shifting the concentration doesn’t mean that google has lost the place it had but it just means that now people are concentrating on attracting an audience through social media platforms as well like facebook, instagram, youtube etc.
Rising Trends in Mobile Application Development (2022).pdf

With the updates in technology and all the newly developed trends the mobile application development has become very technical and upgraded.
Now there is a need to have expert knowledge in the latest trends in mobile application to develop a better user experience app and to keep your app running in the market.
Laravel vs CodeIgniter_ Which One Is Better_.pdf

Two of the most commonly used frameworks are Laravel and CodeIgniter. And developers keep on searching about which one is better: Laravel or CodeIgniter? Keep reading and you will get to know some amazing facts.
List Of The Best And Most Commonly Used Code Editors.pdf

Are you a developer, if yes then code editor might definitely appear to you as your core field of work. There are many different code editors out there with multiple features and you can use the one which suits you the most.
10 Steps To Build A Successful Mobile Application.pdf

People spend a lot of time and money in developing an app and thus its success is the fruit they all wish for but many of them might not have tasted it yet. So here is a quick guide on the development of a mobile application which might help you to come up with a successful one.
Laravel vs CodeIgniter Which One Is Better.pdf

Two of the most commonly used frameworks are Laravel and CodeIgniter. And developers keep on searching about which one is better: Laravel or CodeIgniter? Keep reading and you will get to know some amazing facts.
How To Become A Successful Developer (1).pdf

There are several important qualities that a developer needs or they must develop. If you are a great developer, you will be able to compete and the market will always be available for you. Here are some of the tips that will help you to be a successful developer.
For more details contact https://ozonesoftsolutions.com/
Most Commonly Seen API Errors (2022)

With increasing software updates and complications the software projects more oftenly rely on API integrations to run. API failures are inevitable; the important part is how quickly you can react.
The most common thought of every developer, QA analyst, and project manager is preventing and reacting to problems in your web services.
Which Programming Languages To Choose.pdf

Are you aware of the fact that how many million times you view your mobile phone in a day?
And what is the reason for spending so much time on mobile phones? Its the amazing features you get on the phone and thus the day by day improvement in the user experience make it more and more useful and handy. And thus apps play a very important role in our day to day life and have become an integral part of our lives. Most people from the age group of 13 to 40 are the ones who can’t spend a day without using Instagram, Facebook etc.
Which Programming Languages To Choose For Android App Development_.pdf

Are you aware of the fact that how many million times you view your mobile phone in a day?
And what is the reason for spending so much time on mobile phones? Its the amazing features you get on the phone and thus the day by day improvement in the user experience make it more and more useful and handy. And thus apps play a very important role in our day to day life and have become an integral part of our lives. Most people from the age group of 13 to 40 are the ones who can’t spend a day without using Instagram, Facebook etc.
Top Educational App Trends For 2022.pdf

The pace of digital transformation in the education sector has increased a lot since the pandemic. This fast-tracked growth is expected to expand the digital learning opportunities more in the coming years.
Every stage of education, whether its primary or higher education as well as professional and workplace training, has shifted towards the online platforms.
Importance Of API Development

API (Application Programming Interface) is the intermediary software that establishes communication between two different applications. It allows developers to access an app’s library having all its existing code information using a key. People often search for API development processes and thus here is a short introduction to that.
Flutter Vs. React Native Which One to Choose

Mobile app development is at a boom due the increased zero contact needs of people. The top contenders who are fighting to build their space in mobile app development across platforms are Flutter and React Native. These are the leading market players and development frameworks. The one who are scratching their heads are the People looking to develop apps and are looking for something which will cost them less and is a quicker way.
Top 5 Web Development Trends in 2022

Failing to keep up with new trends can result in serious consequences for your website performance and user experience. You can even fall behind your competitors and lose traffic to websites offering better experiences.
So, developing and maintaining your website according to ongoing trends is the best way to remain competitive in your business.
Flutter Vs. React Native: Which One to Choose?

Mobile app development was really challenging for developers but those days are gone. The two powerful platforms that create confusion are Android and IOS. But the industry has changed upside down with the time and advanced technology. More so, many web-based tools came into existence to create a hybrid mobile application that includes PhoneGap from Adobe, React Native from Facebook, and Xamarin from Microsoft. So here is a comparision among the top contenders who are fighting to build their space in mobile app development across platforms: Flutter and React Native.
Top Educational App Trends For 2022

Every stage of education, whether its primary or higher education as well as professional and workplace training, has shifted towards the online platforms.
We are living in a world where everything is constantly changing. Be it education, e-retail or even banking, we continuously see progression in every sector.
More from OZONESOFT Solutions (20)
Rising Trends in Mobile Application Development (2022).pdf

Rising Trends in Mobile Application Development (2022).pdf
List Of The Best And Most Commonly Used Code Editors.pdf

List Of The Best And Most Commonly Used Code Editors.pdf
10 Steps To Build A Successful Mobile Application.pdf

10 Steps To Build A Successful Mobile Application.pdf
Which Programming Languages To Choose For Android App Development_.pdf

Which Programming Languages To Choose For Android App Development_.pdf
Recently uploaded
SOCRadar Research Team: Latest Activities of IntelBroker

The European Union Agency for Law Enforcement Cooperation (Europol) has suffered an alleged data breach after a notorious threat actor claimed to have exfiltrated data from its systems. Infamous data leaker IntelBroker posted on the even more infamous BreachForums hacking forum, saying that Europol suffered a data breach this month.
The alleged breach affected Europol agencies CCSE, EC3, Europol Platform for Experts, Law Enforcement Forum, and SIRIUS. Infiltration of these entities can disrupt ongoing investigations and compromise sensitive intelligence shared among international law enforcement agencies.
However, this is neither the first nor the last activity of IntekBroker. We have compiled for you what happened in the last few days. To track such hacker activities on dark web sources like hacker forums, private Telegram channels, and other hidden platforms where cyber threats often originate, you can check SOCRadar’s Dark Web News.
Stay Informed on Threat Actors’ Activity on the Dark Web with SOCRadar!
TROUBLESHOOTING 9 TYPES OF OUTOFMEMORYERROR

Even though at surface level ‘java.lang.OutOfMemoryError’ appears as one single error; underlyingly there are 9 types of OutOfMemoryError. Each type of OutOfMemoryError has different causes, diagnosis approaches and solutions. This session equips you with the knowledge, tools, and techniques needed to troubleshoot and conquer OutOfMemoryError in all its forms, ensuring smoother, more efficient Java applications.
First Steps with Globus Compute Multi-User Endpoints

In this presentation we will share our experiences around getting started with the Globus Compute multi-user endpoint. Working with the Pharmacology group at the University of Auckland, we have previously written an application using Globus Compute that can offload computationally expensive steps in the researcher's workflows, which they wish to manage from their familiar Windows environments, onto the NeSI (New Zealand eScience Infrastructure) cluster. Some of the challenges we have encountered were that each researcher had to set up and manage their own single-user globus compute endpoint and that the workloads had varying resource requirements (CPUs, memory and wall time) between different runs. We hope that the multi-user endpoint will help to address these challenges and share an update on our progress here.
Exploring Innovations in Data Repository Solutions - Insights from the U.S. G...

The U.S. Geological Survey (USGS) has made substantial investments in meeting evolving scientific, technical, and policy driven demands on storing, managing, and delivering data. As these demands continue to grow in complexity and scale, the USGS must continue to explore innovative solutions to improve its management, curation, sharing, delivering, and preservation approaches for large-scale research data. Supporting these needs, the USGS has partnered with the University of Chicago-Globus to research and develop advanced repository components and workflows leveraging its current investment in Globus. The primary outcome of this partnership includes the development of a prototype enterprise repository, driven by USGS Data Release requirements, through exploration and implementation of the entire suite of the Globus platform offerings, including Globus Flow, Globus Auth, Globus Transfer, and Globus Search. This presentation will provide insights into this research partnership, introduce the unique requirements and challenges being addressed and provide relevant project progress.
Lecture 1 Introduction to games development

Software engineering
Game Development
unity Game Development
Quarkus Hidden and Forbidden Extensions

Quarkus has a vast extension ecosystem and is known for its subsonic and subatomic feature set. Some of these features are not as well known, and some extensions are less talked about, but that does not make them less interesting - quite the opposite.
Come join this talk to see some tips and tricks for using Quarkus and some of the lesser known features, extensions and development techniques.
In 2015, I used to write extensions for Joomla, WordPress, phpBB3, etc and I ...

In 2015, I used to write extensions for Joomla, WordPress, phpBB3, etc and I didn't get rich from it but it did have 63K downloads (powered possible tens of thousands of websites).
Understanding Globus Data Transfers with NetSage

NetSage is an open privacy-aware network measurement, analysis, and visualization service designed to help end-users visualize and reason about large data transfers. NetSage traditionally has used a combination of passive measurements, including SNMP and flow data, as well as active measurements, mainly perfSONAR, to provide longitudinal network performance data visualization. It has been deployed by dozens of networks world wide, and is supported domestically by the Engagement and Performance Operations Center (EPOC), NSF #2328479. We have recently expanded the NetSage data sources to include logs for Globus data transfers, following the same privacy-preserving approach as for Flow data. Using the logs for the Texas Advanced Computing Center (TACC) as an example, this talk will walk through several different example use cases that NetSage can answer, including: Who is using Globus to share data with my institution, and what kind of performance are they able to achieve? How many transfers has Globus supported for us? Which sites are we sharing the most data with, and how is that changing over time? How is my site using Globus to move data internally, and what kind of performance do we see for those transfers? What percentage of data transfers at my institution used Globus, and how did the overall data transfer performance compare to the Globus users?
Enterprise Resource Planning System in Telangana

Enterprise Resource Planning System includes various modules that reduce any business's workload. Additionally, it organizes the workflows, which drives towards enhancing productivity. Here are a detailed explanation of the ERP modules. Going through the points will help you understand how the software is changing the work dynamics.
To know more details here: https://blogs.nyggs.com/nyggs/enterprise-resource-planning-erp-system-modules/
Using IESVE for Room Loads Analysis - Australia & New Zealand

Roger Cladingboel showcases how IESVE can be used to undertake heating and cooling loads.
Dominate Social Media with TubeTrivia AI’s Addictive Quiz Videos.pdf

Dominate Social Media with TubeTrivia AI’s Addictive Quiz Videos
https://www.amb-review.com/tubetrivia-ai
Exclusive Features:
AI-Powered Questions,
Wide Range of Categories,
Adaptive Difficulty,
User-Friendly Interface,
Multiplayer Mode,
Regular Updates.
#TubeTriviaAI
#QuizVideoMagic
#ViralQuizVideos
#AIQuizGenerator
#EngageExciteExplode
#MarketingRevolution
#BoostYourTraffic
#SocialMediaSuccess
#AIContentCreation
#UnlimitedTraffic
Corporate Management | Session 3 of 3 | Tendenci AMS

Corporate Management | Session 3 of 3 | Tendenci AMSTendenci - The Open Source AMS (Association Management Software)
Experience our free, in-depth three-part Tendenci Platform Corporate Membership Management workshop series! In Session 1 on May 14th, 2024, we began with an Introduction and Setup, mastering the configuration of your Corporate Membership Module settings to establish membership types, applications, and more. Then, on May 16th, 2024, in Session 2, we focused on binding individual members to a Corporate Membership and Corporate Reps, teaching you how to add individual members and assign Corporate Representatives to manage dues, renewals, and associated members. Finally, on May 28th, 2024, in Session 3, we covered questions and concerns, addressing any queries or issues you may have.
For more Tendenci AMS events, check out www.tendenci.com/eventsNavigating the Metaverse: A Journey into Virtual Evolution"

Join us for an exploration of the Metaverse's evolution, where innovation meets imagination. Discover new dimensions of virtual events, engage with thought-provoking discussions, and witness the transformative power of digital realms."
Webinar: Salesforce Document Management 2.0 - Smarter, Faster, Better

Check out the webinar slides to learn more about how XfilesPro transforms Salesforce document management by leveraging its world-class applications. For more details, please connect with sales@xfilespro.com
If you want to watch the on-demand webinar, please click here: https://www.xfilespro.com/webinars/salesforce-document-management-2-0-smarter-faster-better/
A Comprehensive Look at Generative AI in Retail App Testing.pdf

Traditional software testing methods are being challenged in retail, where customer expectations and technological advancements continually shape the landscape. Enter generative AI—a transformative subset of artificial intelligence technologies poised to revolutionize software testing.
Globus Compute wth IRI Workflows - GlobusWorld 2024

As part of the DOE Integrated Research Infrastructure (IRI) program, NERSC at Lawrence Berkeley National Lab and ALCF at Argonne National Lab are working closely with General Atomics on accelerating the computing requirements of the DIII-D experiment. As part of the work the team is investigating ways to speedup the time to solution for many different parts of the DIII-D workflow including how they run jobs on HPC systems. One of these routes is looking at Globus Compute as a way to replace the current method for managing tasks and we describe a brief proof of concept showing how Globus Compute could help to schedule jobs and be a tool to connect compute at different facilities.
Innovating Inference - Remote Triggering of Large Language Models on HPC Clus...

Large Language Models (LLMs) are currently the center of attention in the tech world, particularly for their potential to advance research. In this presentation, we'll explore a straightforward and effective method for quickly initiating inference runs on supercomputers using the vLLM tool with Globus Compute, specifically on the Polaris system at ALCF. We'll begin by briefly discussing the popularity and applications of LLMs in various fields. Following this, we will introduce the vLLM tool, and explain how it integrates with Globus Compute to efficiently manage LLM operations on Polaris. Attendees will learn the practical aspects of setting up and remotely triggering LLMs from local machines, focusing on ease of use and efficiency. This talk is ideal for researchers and practitioners looking to leverage the power of LLMs in their work, offering a clear guide to harnessing supercomputing resources for quick and effective LLM inference.
Cyaniclab : Software Development Agency Portfolio.pdf

CyanicLab, an offshore custom software development company based in Sweden,India, Finland, is your go-to partner for startup development and innovative web design solutions. Our expert team specializes in crafting cutting-edge software tailored to meet the unique needs of startups and established enterprises alike. From conceptualization to execution, we offer comprehensive services including web and mobile app development, UI/UX design, and ongoing software maintenance. Ready to elevate your business? Contact CyanicLab today and let us propel your vision to success with our top-notch IT solutions.
Recently uploaded (20)
SOCRadar Research Team: Latest Activities of IntelBroker

SOCRadar Research Team: Latest Activities of IntelBroker
First Steps with Globus Compute Multi-User Endpoints

First Steps with Globus Compute Multi-User Endpoints
Exploring Innovations in Data Repository Solutions - Insights from the U.S. G...

Exploring Innovations in Data Repository Solutions - Insights from the U.S. G...
In 2015, I used to write extensions for Joomla, WordPress, phpBB3, etc and I ...

In 2015, I used to write extensions for Joomla, WordPress, phpBB3, etc and I ...
Using IESVE for Room Loads Analysis - Australia & New Zealand

Using IESVE for Room Loads Analysis - Australia & New Zealand
Dominate Social Media with TubeTrivia AI’s Addictive Quiz Videos.pdf

Dominate Social Media with TubeTrivia AI’s Addictive Quiz Videos.pdf
Corporate Management | Session 3 of 3 | Tendenci AMS

Corporate Management | Session 3 of 3 | Tendenci AMS
Navigating the Metaverse: A Journey into Virtual Evolution"

Navigating the Metaverse: A Journey into Virtual Evolution"
Webinar: Salesforce Document Management 2.0 - Smarter, Faster, Better

Webinar: Salesforce Document Management 2.0 - Smarter, Faster, Better
A Comprehensive Look at Generative AI in Retail App Testing.pdf

A Comprehensive Look at Generative AI in Retail App Testing.pdf
Globus Compute wth IRI Workflows - GlobusWorld 2024

Globus Compute wth IRI Workflows - GlobusWorld 2024
Innovating Inference - Remote Triggering of Large Language Models on HPC Clus...

Innovating Inference - Remote Triggering of Large Language Models on HPC Clus...
Cyaniclab : Software Development Agency Portfolio.pdf

Cyaniclab : Software Development Agency Portfolio.pdf
How to Secure Your Mobile Commerce App.pdf
- 1. How to Secure Your Mobile Commerce App? M-commerce development services are growing very rapidly in the market as more and more users are using their mobile and tablets for online transactions. Mobile commerce applications are now processing a lot more data than ever which includes sensitive information about users and their transactions. Before going deep into this, Let’s first understand : What is mobile commerce? M-commerce (mobile commerce) is the buying and selling of goods and services through wireless handheld devices such as smartphones and tablets. Basically, transactions that happen online via a mobile or tablet are known as mobile commerce. Mobile commerce is a form of e-commerce and thus it enables users to access online shopping platforms without using a desktop computer. Some of the examples of m-commerce include mobile banking, in-app purchasing, virtual marketplace apps
- 2. like the Amazon mobile app or a digital wallet such as Apple Pay, Android Pay and Samsung Pay. Why does Mobile commerce require more security these days? Because of the increasing volume of transitions through mobile devices, it has become a necessity for businesses to step up and provide security. Businesses must ensure security of sensitive data of people’s transactions in order to win the trust of customers and build a good reputation. Providing security is even more important to sectors that deal with a lot of such data with healthcare and financial services. And because these transactions are done through smartphones using the internet, m-commerce is required to create more security for their users than traditional e-commerce has to. If you are looking for a customized mobile application development company connect with Ozonesoft Solutions. Why is mobile commerce security crucial for your business? Securing m-commerce is crucial to businesses for such reasons : ● As businesses provide mobile transactions, they must secure their m-commerce application. They are responsible for securing themselves against chargebacks and they must ensure safety of the data for both the business and customers. ● Lack of security or breach in security can cause their users to abandon their application or it might even drop their revenue stream. ● Security problems can cause trust issues towards your application or even towards your brand.
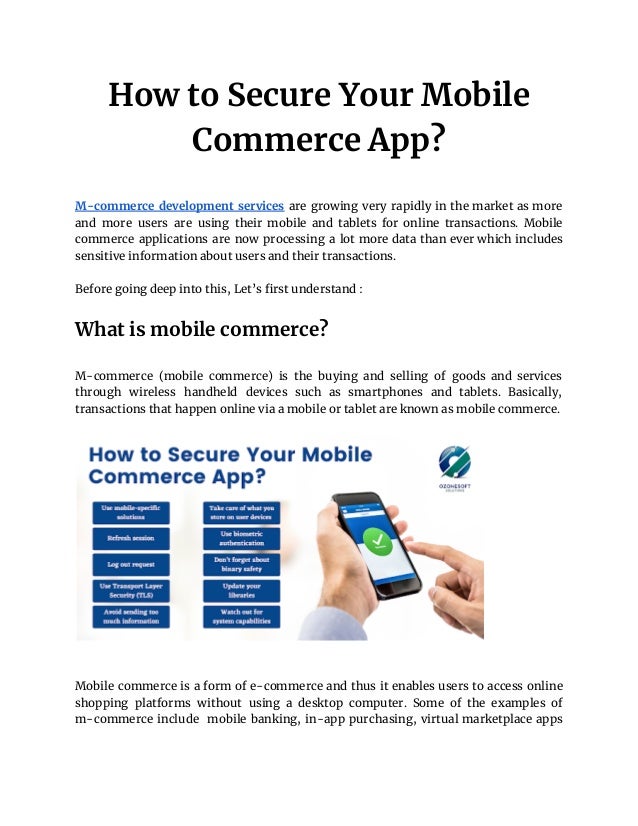
- 3. No business can guarantee a 100% data security for transactions. But that does not mean your data can be breached or exposed easily. Businesses need to make sure that their security measures can slow down the attackers for long enough that their app becomes an unattractive target. Ways to secure your mobile commerce app Mobile commerce developers are constantly dealing with cyber-attacks and harmful viruses, thus security is a top priority. Hackers are always attempting to gain access to your mobile commerce app through security flaws and cause you harm. So, here are ways to secure your mobile commerce app : Backend communication security tips ● Use mobile-specific solutions : Trusting users is much easier when they create an account with phone verification. Moreover, for mobile apps, using phone verification is much more convenient than using email, which needs launching another app/web browser. ● Refresh session : Shorten the life of access tokens to several minutes, it will still keep the app user-friendly by introducing refresh tokens. These tokens can be used to obtain a new token. If the attacker tries to acquire a token, it will be useless after some minutes. ● Log out request : Tokens that are no longer in use should be signaled invalidate, stating that the session is closed. ● Use Transport Layer Security (TLS) : TLS creates an end-to-end encryption, which ensures that nobody reads our messages even if messages are sent through an unencrypted channel (for example, a WiFi access point without a password). ● Avoid sending too much information : Stop sending unnecessary data or splitting them to many requests, this way it will become harder for the
- 4. attacker to obtain the personal data. Even if an attacker intercepts a single request, the information obtained by them may not be sufficient to do harm. Mobile app security tips ● Take care of what you store on user devices : There are chances that unencrypted data on a mobile device can be stolen. Encrypt every sensitive information that you need to store. Nowadays, phones provide secure storage for sensitive data, so we should also remove unnecessary and temporary files as soon as possible. ● Use biometric authentication : Biometric authentication is now supported by almost all devices. It can be used as a convenient means of access or an additional layer of security for sensitive data. ● Don’t forget about binary safety : Compilers can also protect the app from data interception attempts from the produced source code. This makes it impossible for attackers to fake attacks or learn about the app's security weaknesses. ● Update your libraries : Mobile systems and libraries receive updates regularly, so the app should stay up to date as well. Attacks can be prevented, if people update libraries to the newest versions. Attackers can easily exploit a bug that has been announced to the public at least a few months prior. ● Watch out for system capabilities : Capabilities such as clipboards can store data across all applications. There exist some apps or websites that can steal data from clipboards or place their tracking data there. See if the app should share data with other apps, don't permit third party apps to open an unsupported file for preview. Conclusion
- 5. As mentioned above, strengthen your mobile app development process and include the essential security measures. It will assist you in protecting both your audience and your company from potential risks. If you are looking for someone who can build a mobile commerce app for you with all the security, contact Ozonesoft Solutions. We are the pioneers in mobile app development with expertise in Android app development and iPhone app development. Our еxtеnѕіvе experience in the mobile world enables uѕ to develop and deliver breakthrough mоbіlе solutions in vаrіоuѕ vеrtісаlѕ including Entеrрrіѕе, Navigation, Hеаlth Cаrе, Wearable Technology, Augmented Rеаlіtу, E-commerce, News, Utility, Events and Organizers, and Education еtс. We Redefine your Business or Startup Goals with Advanced Website & Mobile App Development Solutions Powered by Robust Architecture and AI-based Algorithms. So if you are looking for mobile app development services contact Ozonesoft Solutions. Source : https://bit.ly/3Mdxs1S
