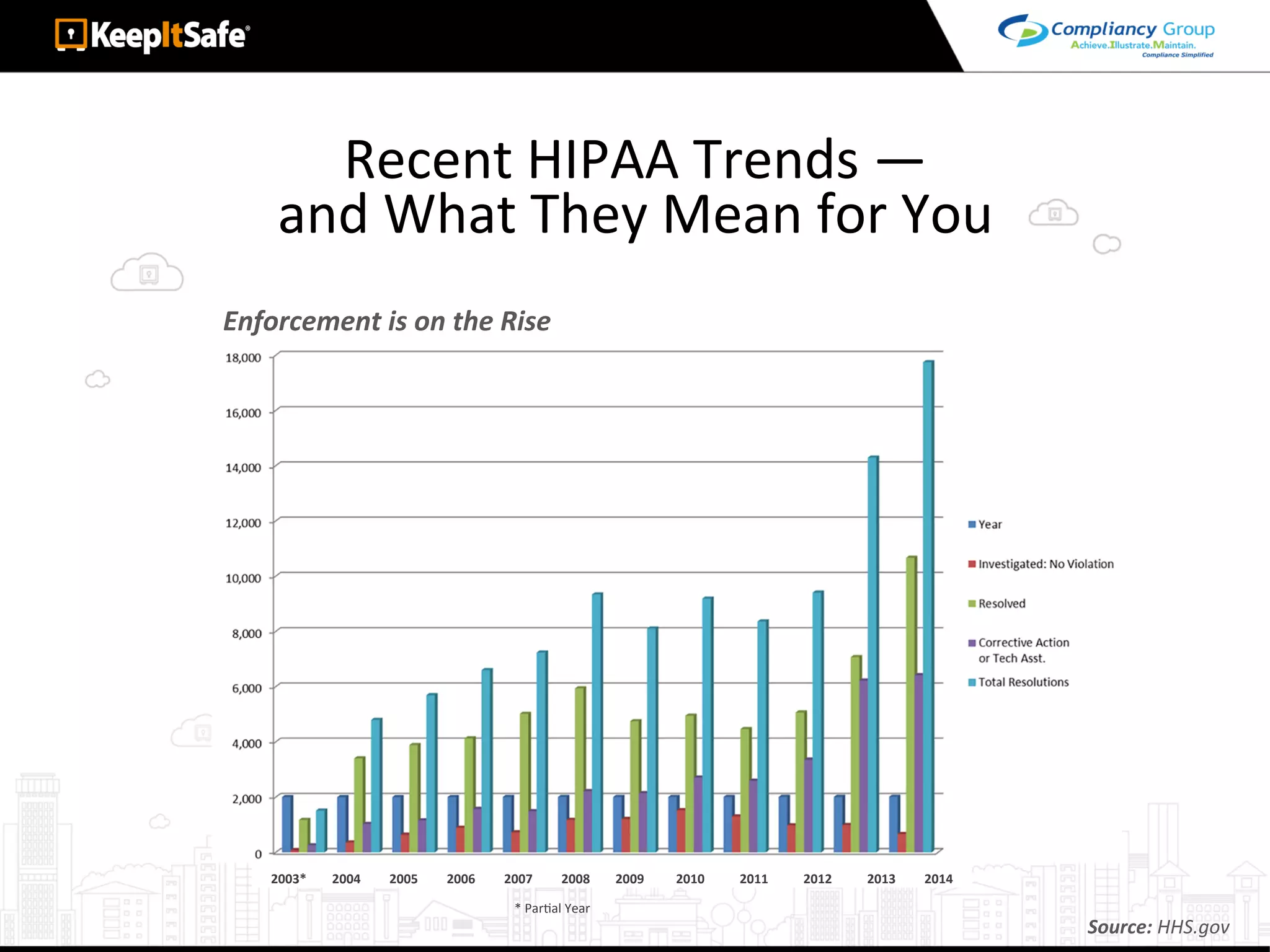
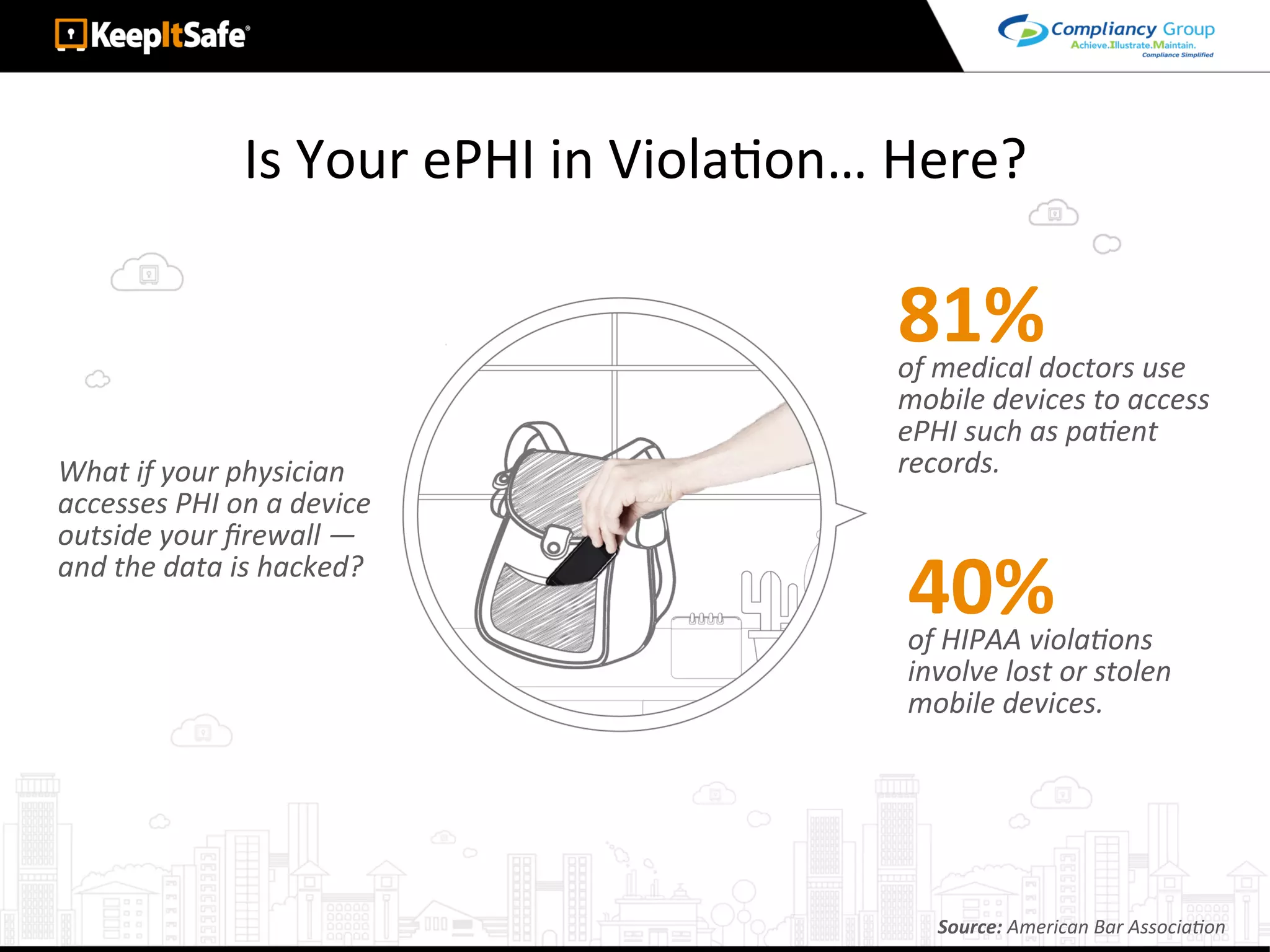
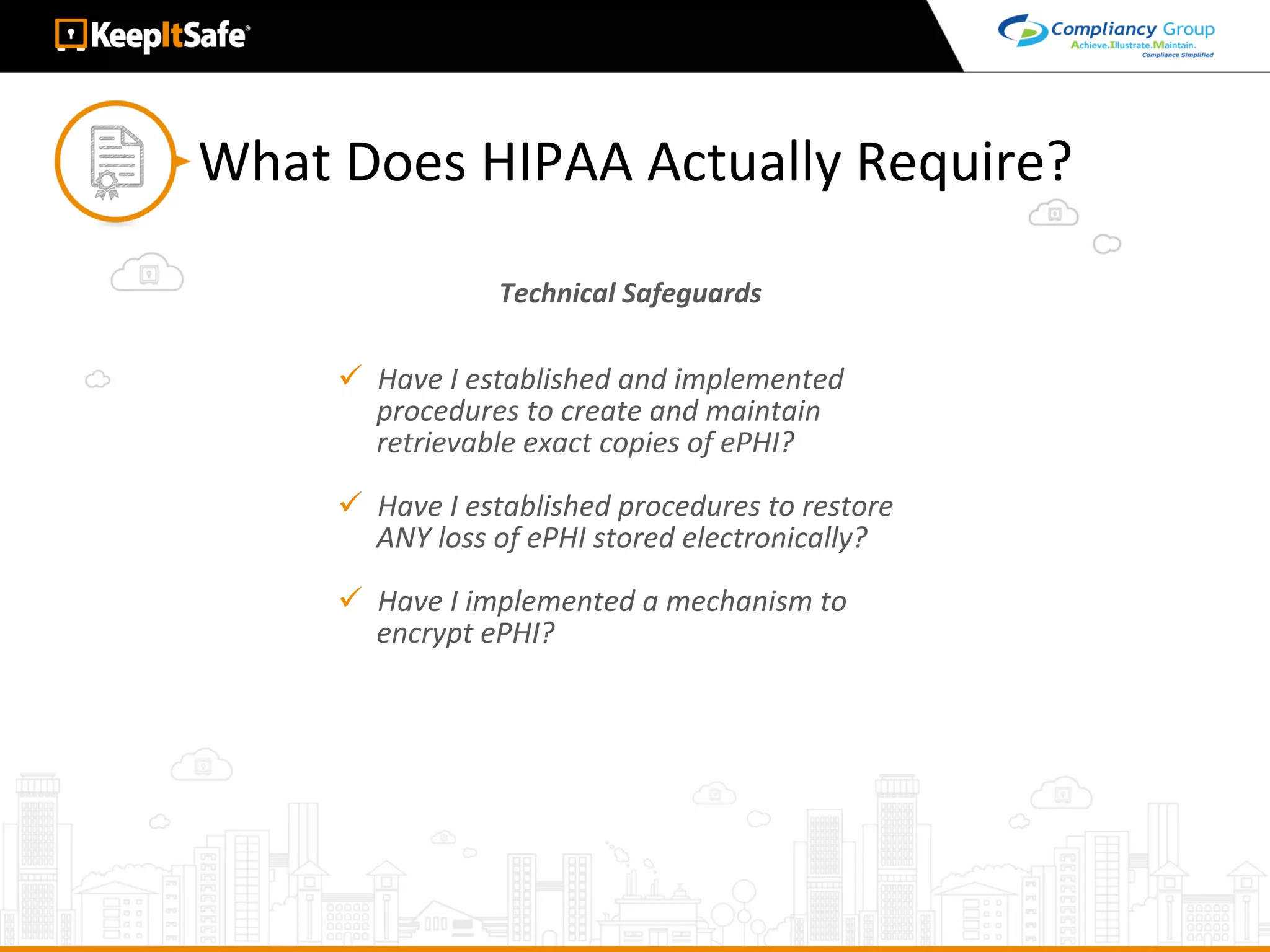
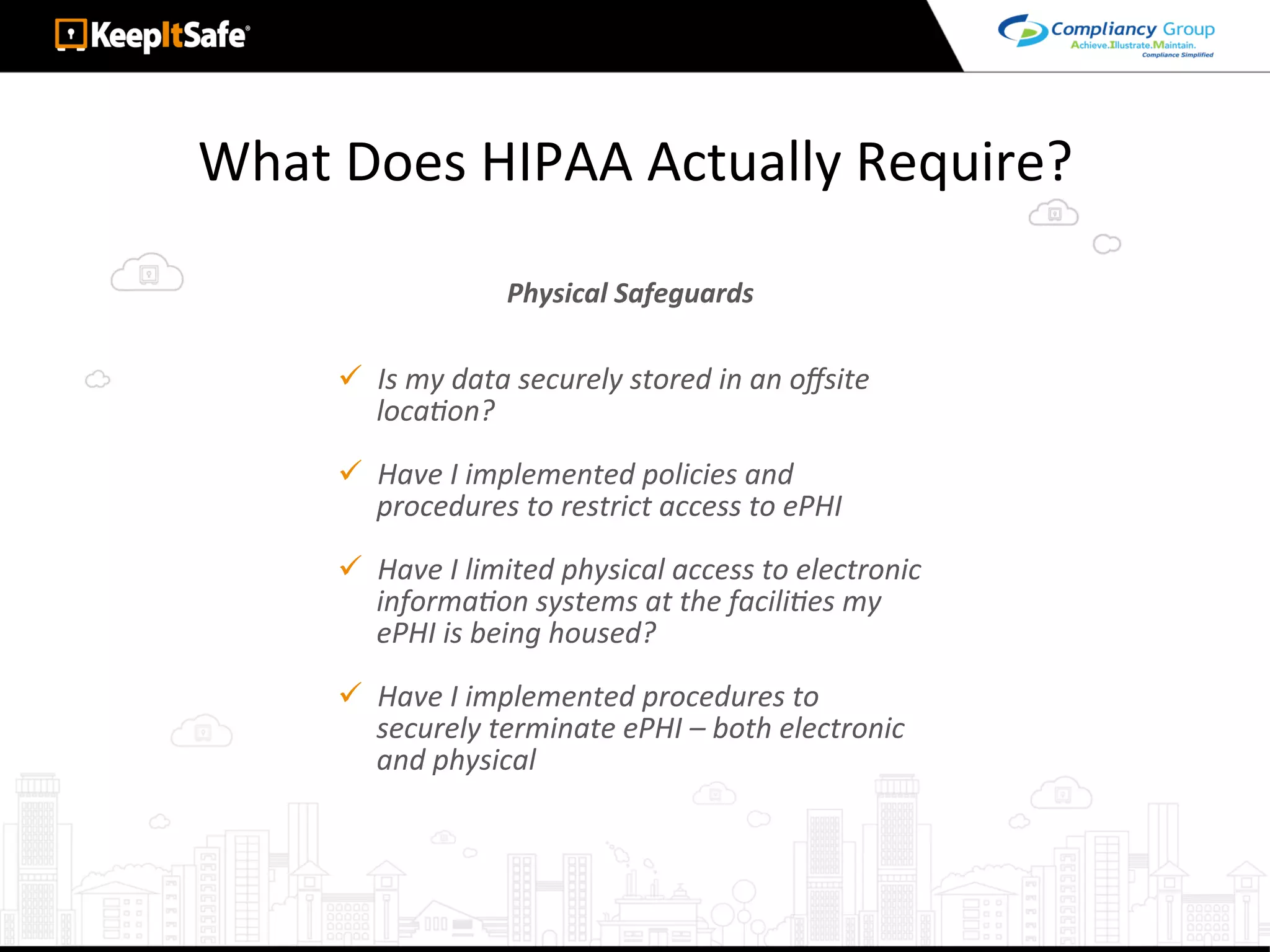
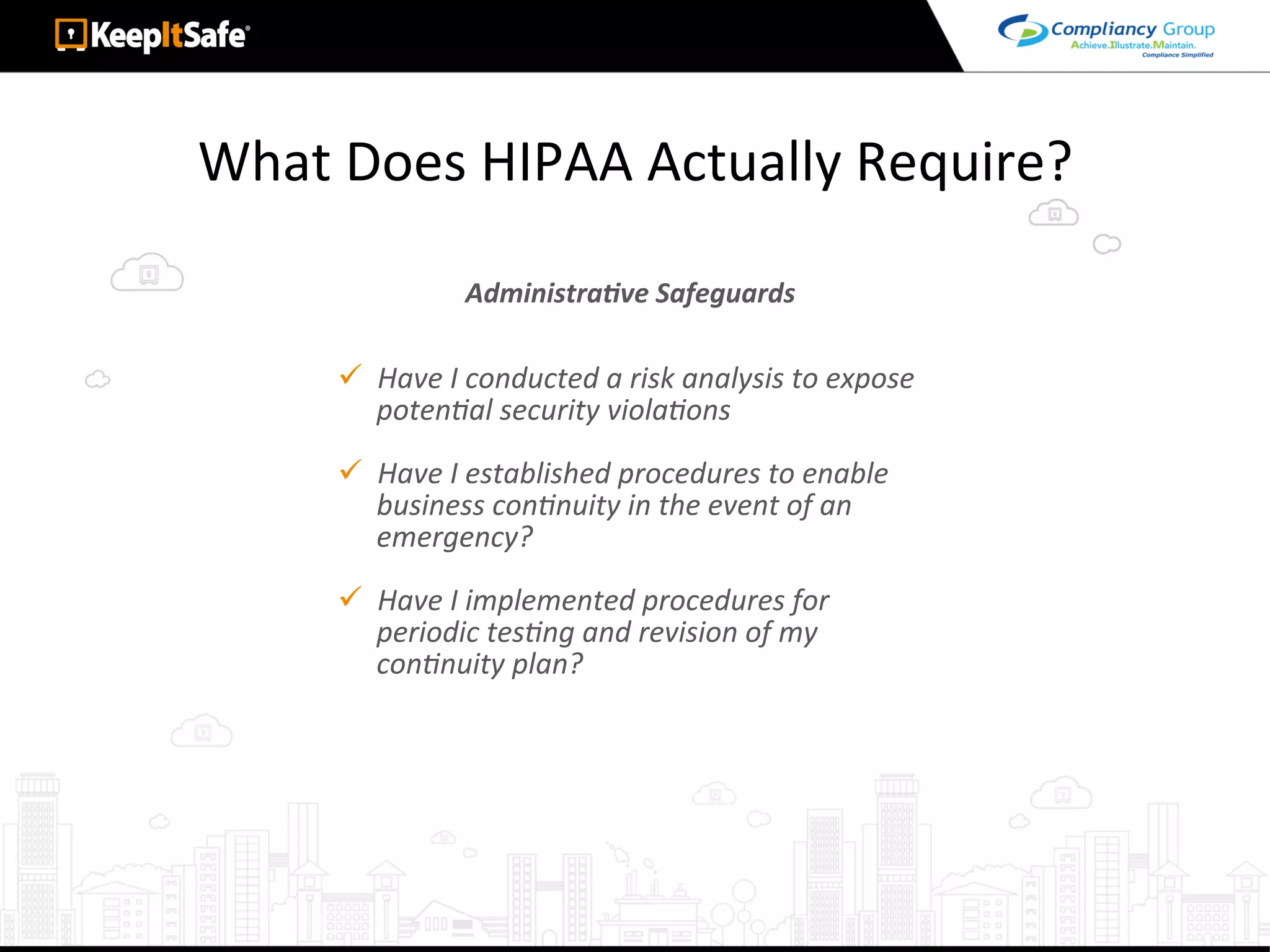
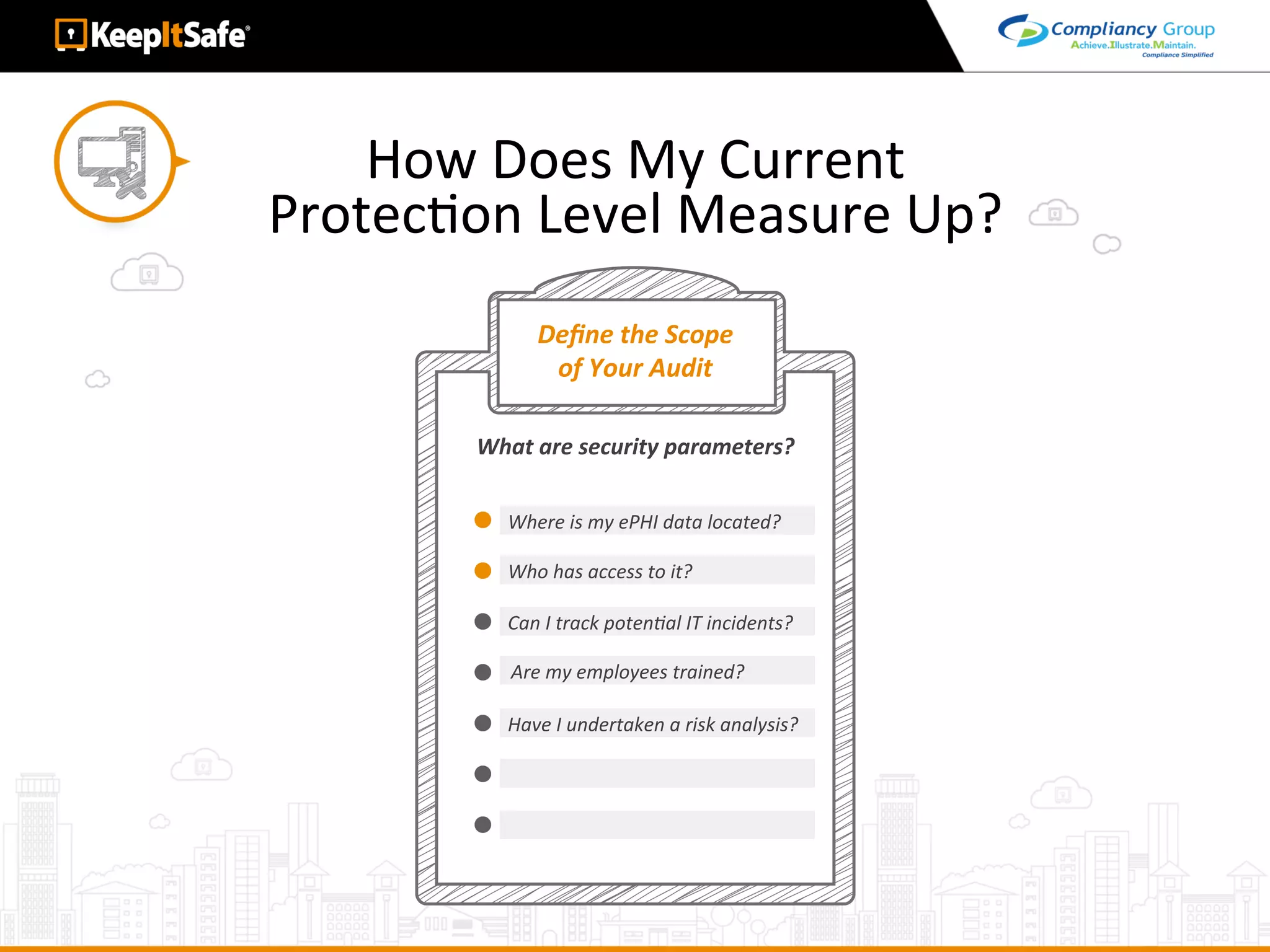
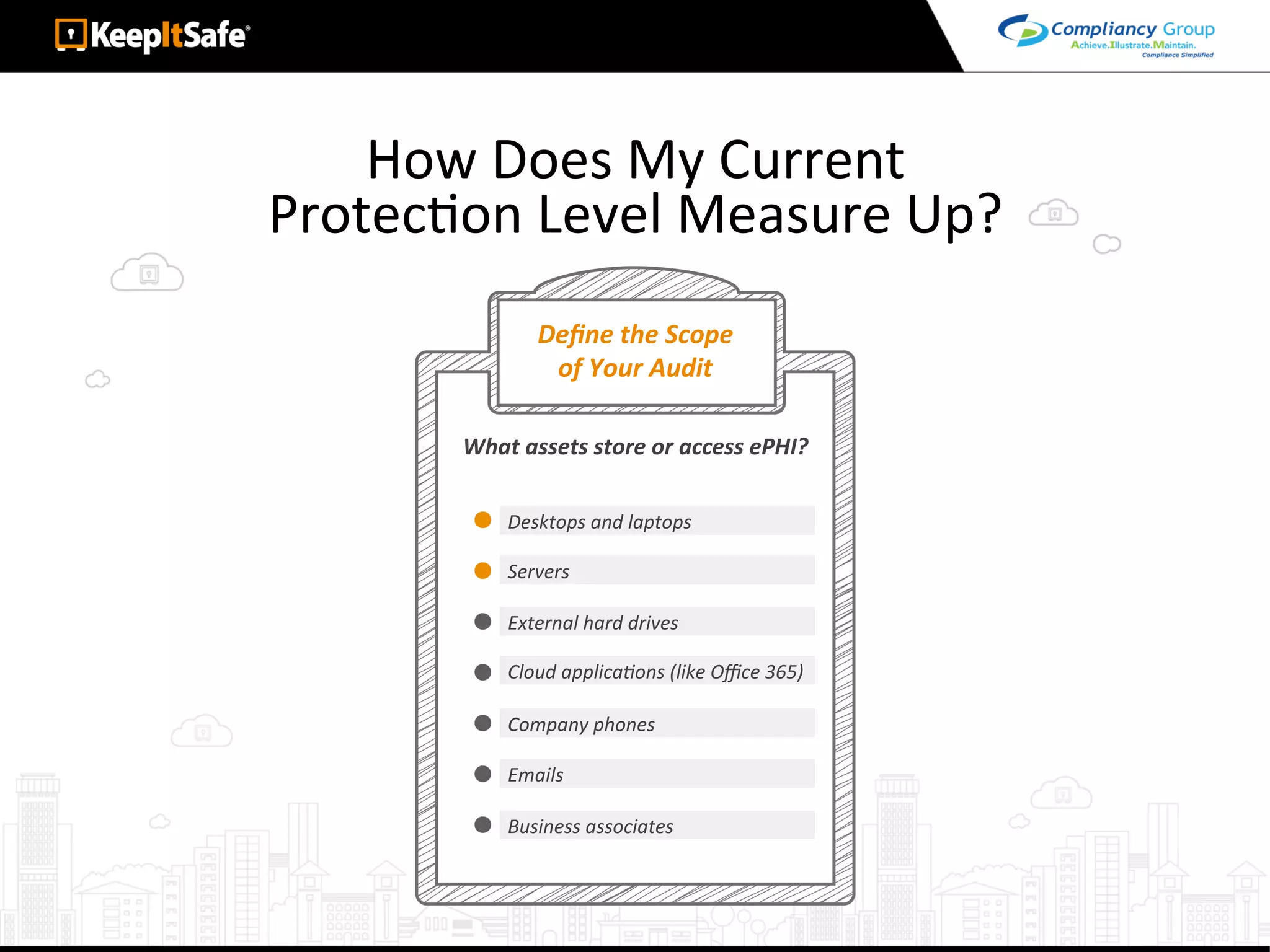
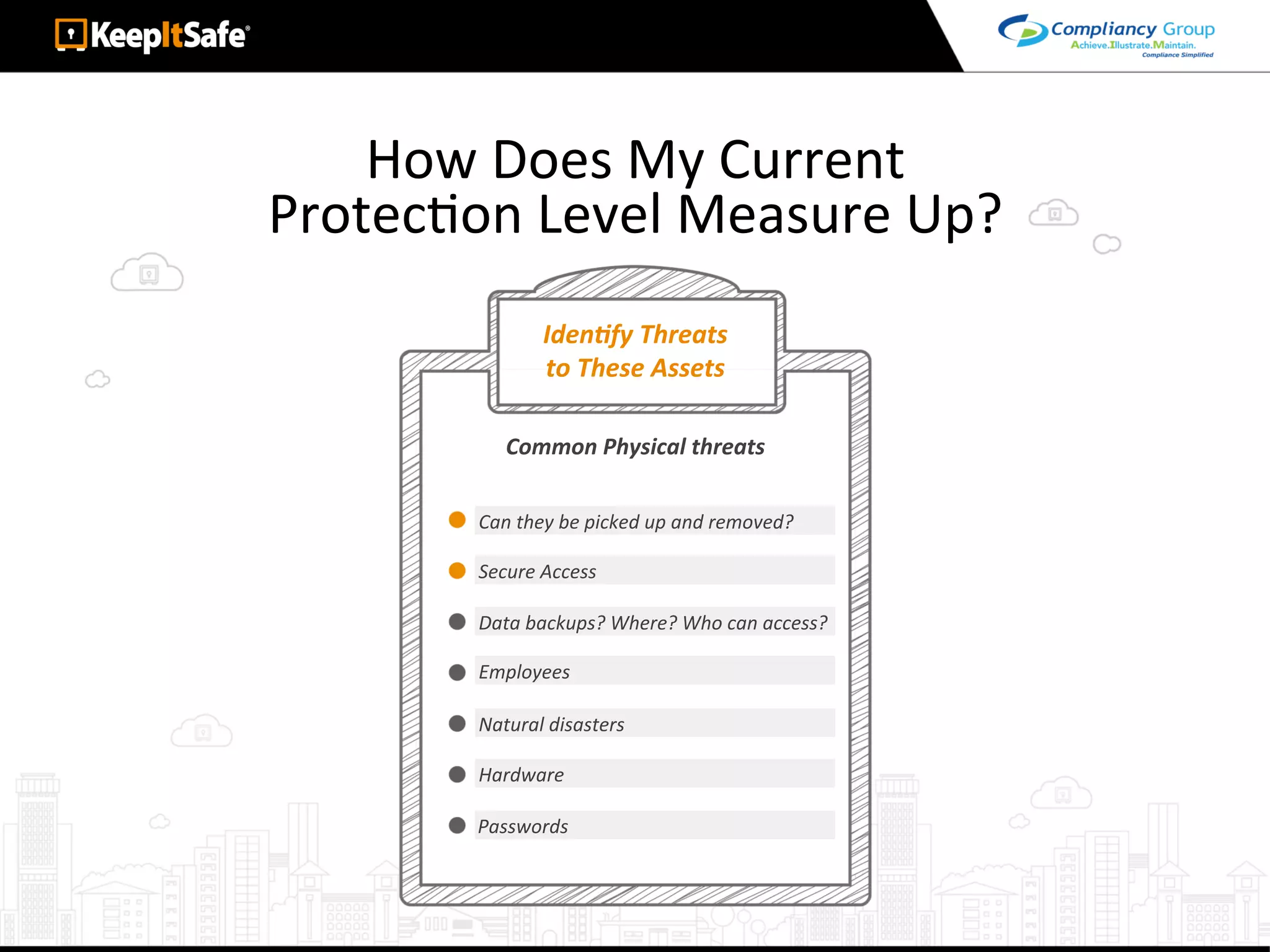
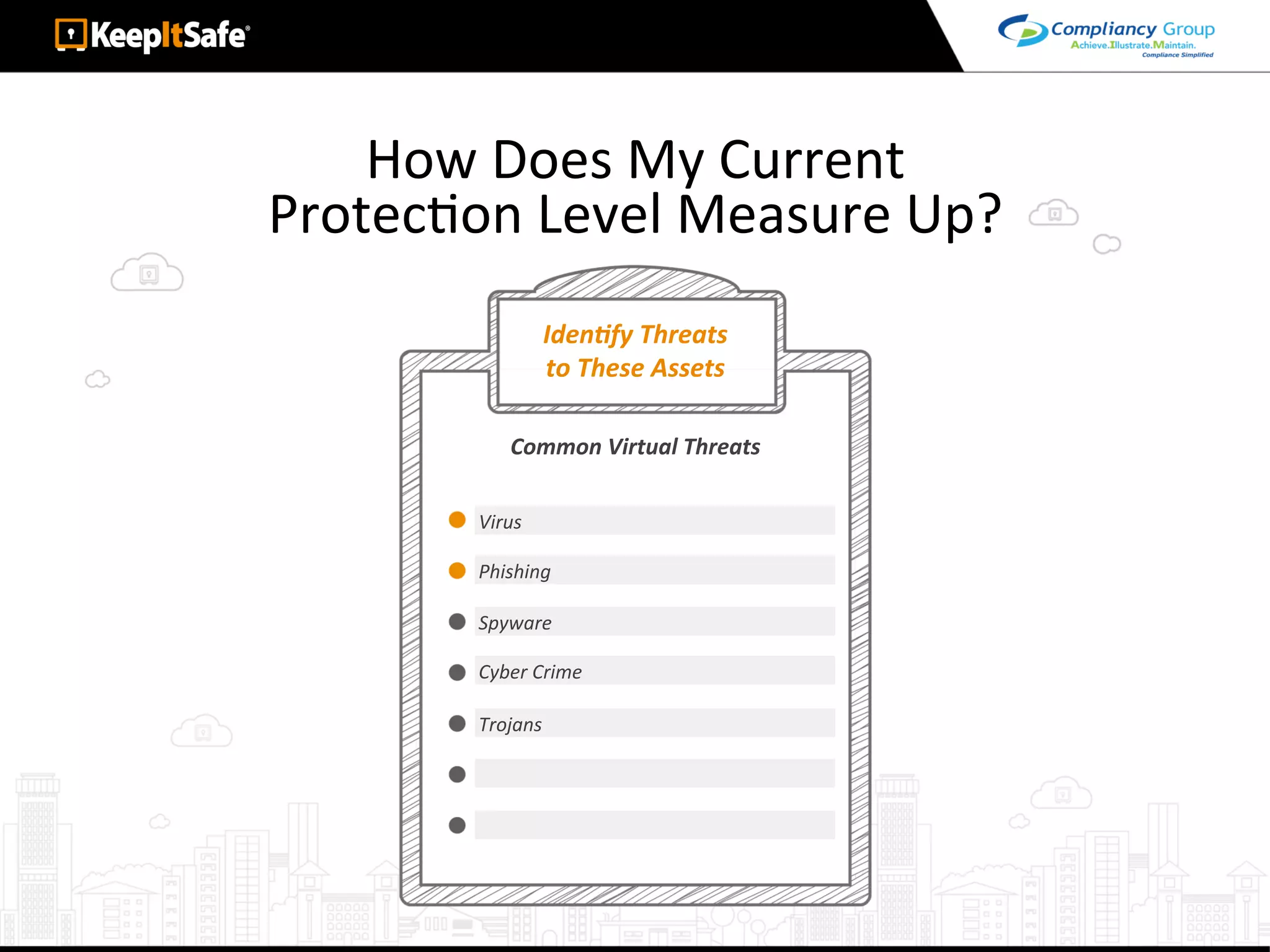
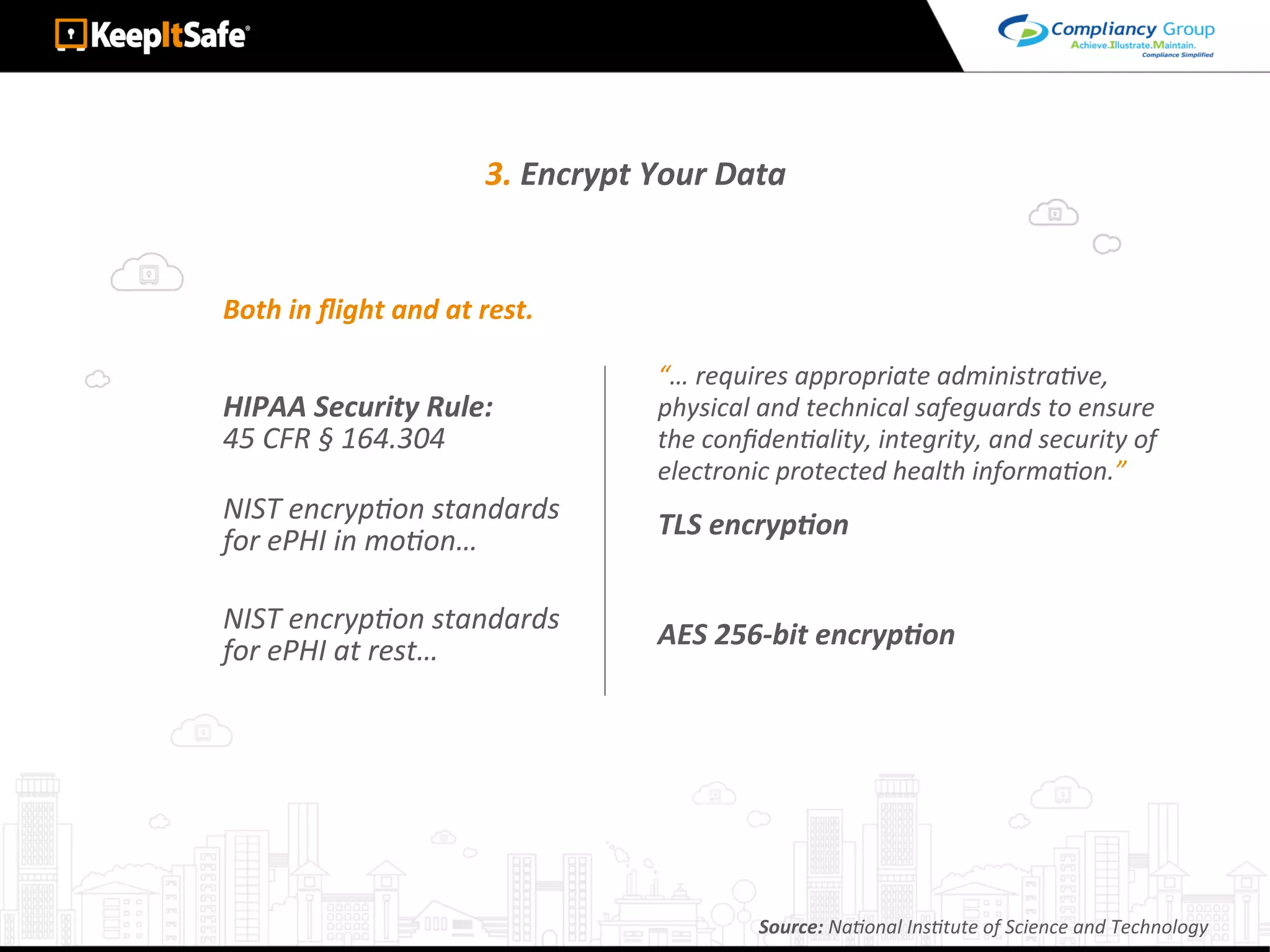
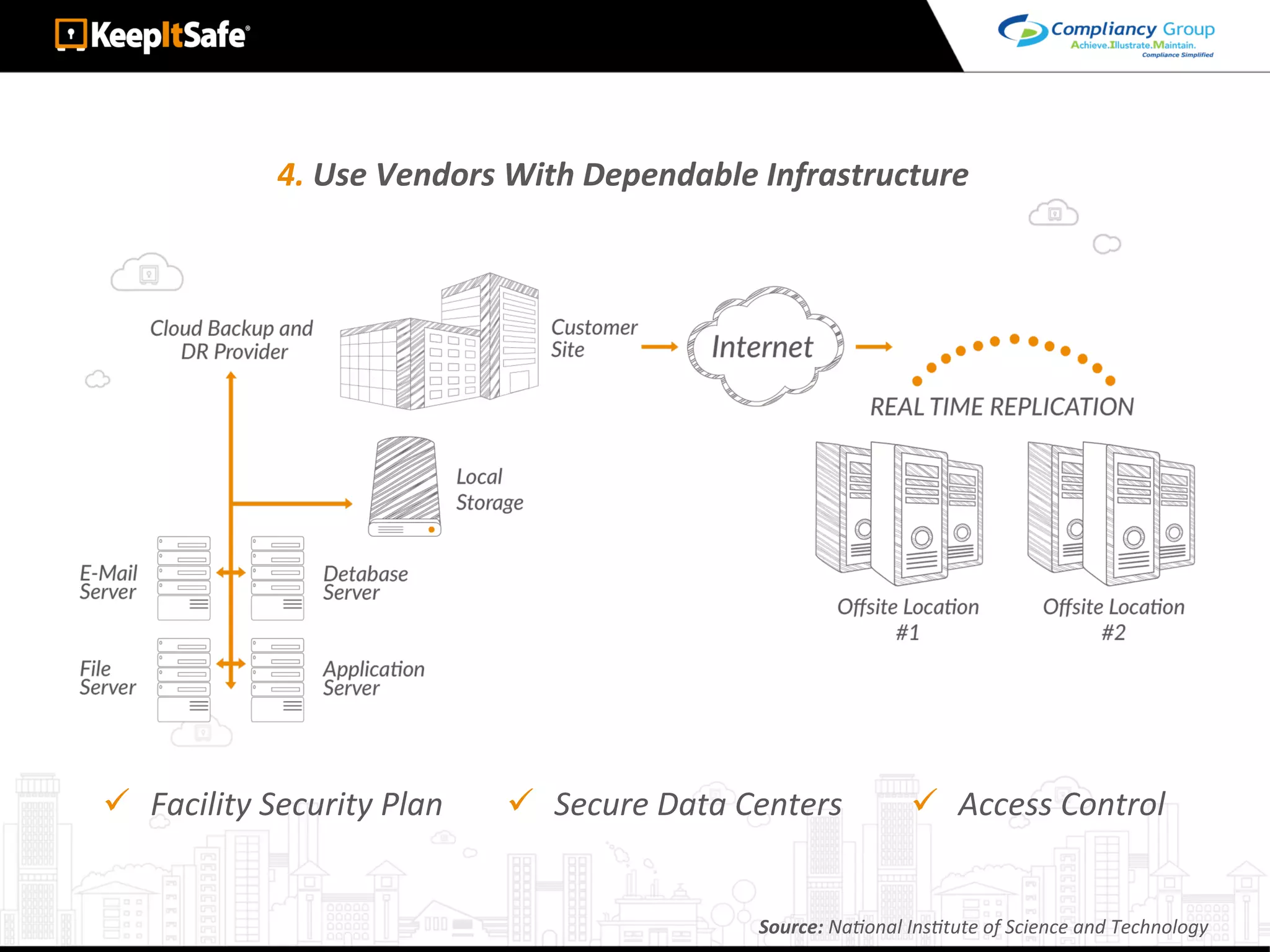
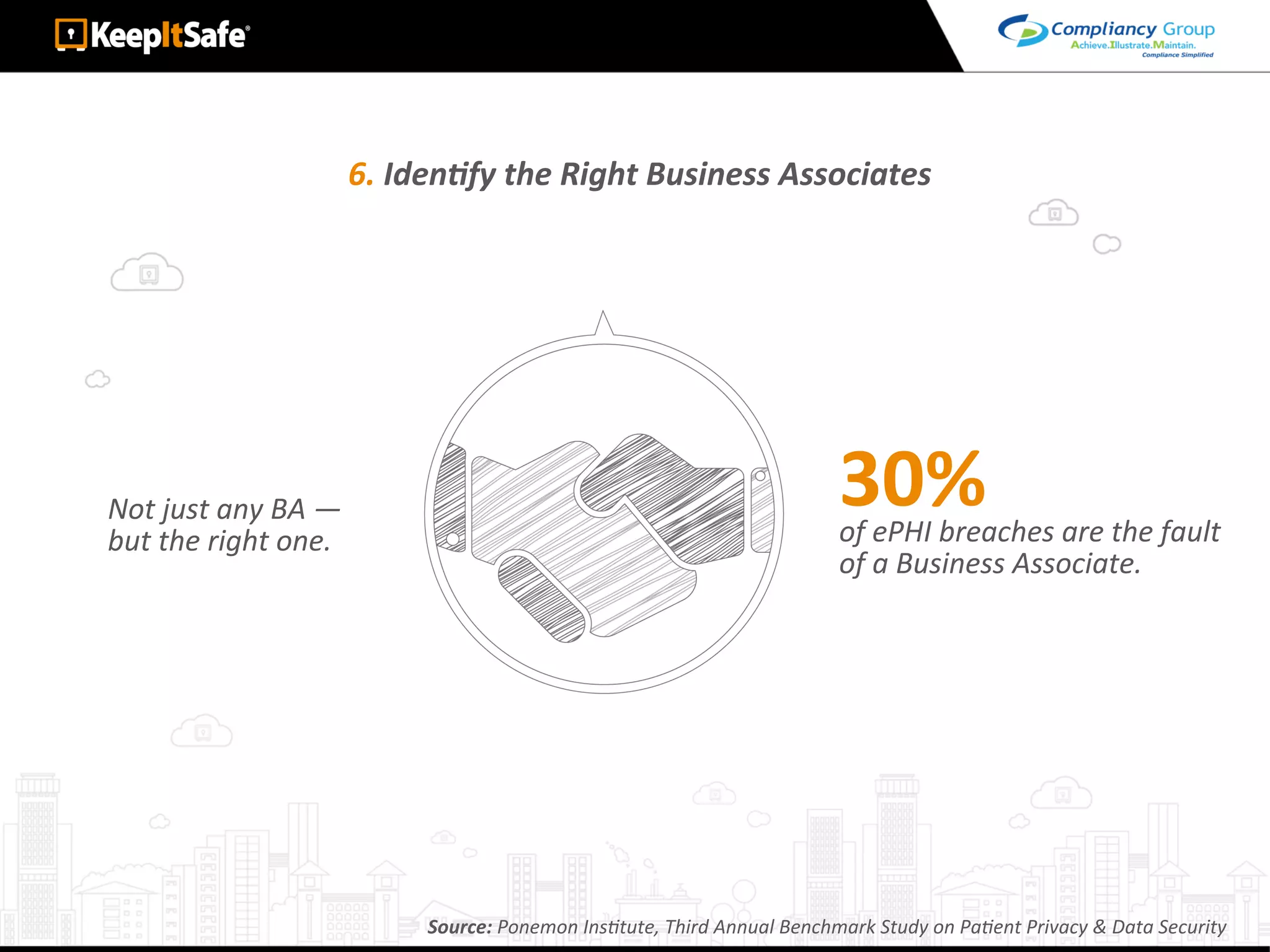
The document discusses significant HIPAA violations, citing the University of Washington's $750,000 fine due to a data breach. It outlines the essential requirements for HIPAA compliance, including technical, physical, and administrative safeguards for protecting electronic protected health information (ePHI). The document also emphasizes the importance of risk analysis, proper training, and using reliable business associates to prevent data breaches.