How to remove Trojan.Mirai
•
0 likes•317 views
Guidelines to get rid of Trojan.Mirai infection completely to ensure security of installed application and stored personal details. for more info - http://www.threatremovalsite.com/remove-trojan-mirai-completely-from-pc
Report
Share
Report
Share
Download to read offline
Recommended
How to remove Trojan.Vimnaspu 

Removal of Trojan.Vimnaspu Trojan infection is very urgent from PC to protect entire stored personal details and installed applications for their safety.
http://www.threatremovalsite.com/get-rid-of-trojan-vimnaspu-once-and-for-all/
How to remove Trojan.Kulekmoko

It includes the steps to eradicate all related components of Trojan.Kulekmoko which leads to make your PC free from bad impact of the Trojan.
How to remove Backdoor.Streamex

Delete Backdoor.Streamex Trojan completely to protect installed programs, registries and other settings with described methods in article. for more info - http://www.threatremovalsite.com/delete-backdoor-streamex-trojan-from-pc-completely
Errorssolvingppt

Error code 0X80508023 typically results from other errors when a system is infected with viruses, malware, or trojans. It can occur when trying to use Windows Defender or Security Essentials to remove infections. Potential fixes include scanning for infections in safe mode, performing a system restore, updating Windows and other software, or using a repair tool to fix issues with registry entries that may be causing the error code.
Errorssolvingppt

Error code 0X80508023 typically results from other errors when a system is infected with viruses, malware, or trojans. It can occur when trying to use Windows Defender or Security Essentials to remove infections. Potential fixes include scanning for malware, rebooting in safe mode, performing a system restore, updating Windows and software, and clearing temporary files. Downloading a repair tool may also help fix the error code.
Remove TROJ_PIDIEF.SMXY

TROJ_PIDIEF.SMXY is a malicious item which alters the registry and browser settings in your PC and thus invites multiple spywares to attack on your PC damaging it in fatal ways.
How can we remove window fix?

Window Fix removal tool has lot of features that will help you remove Window Fix virus. It is one of the best ways to remove Window Fix.
Remove Clickhoofind.com

http://www.removemalwarethreats.com/2014/10/11/uninstall-clickhoofind-com-from-windows-system Clickhoofind.com is nasty ad ware that destroys your system and steal your all information from your system.
Recommended
How to remove Trojan.Vimnaspu 

Removal of Trojan.Vimnaspu Trojan infection is very urgent from PC to protect entire stored personal details and installed applications for their safety.
http://www.threatremovalsite.com/get-rid-of-trojan-vimnaspu-once-and-for-all/
How to remove Trojan.Kulekmoko

It includes the steps to eradicate all related components of Trojan.Kulekmoko which leads to make your PC free from bad impact of the Trojan.
How to remove Backdoor.Streamex

Delete Backdoor.Streamex Trojan completely to protect installed programs, registries and other settings with described methods in article. for more info - http://www.threatremovalsite.com/delete-backdoor-streamex-trojan-from-pc-completely
Errorssolvingppt

Error code 0X80508023 typically results from other errors when a system is infected with viruses, malware, or trojans. It can occur when trying to use Windows Defender or Security Essentials to remove infections. Potential fixes include scanning for infections in safe mode, performing a system restore, updating Windows and other software, or using a repair tool to fix issues with registry entries that may be causing the error code.
Errorssolvingppt

Error code 0X80508023 typically results from other errors when a system is infected with viruses, malware, or trojans. It can occur when trying to use Windows Defender or Security Essentials to remove infections. Potential fixes include scanning for malware, rebooting in safe mode, performing a system restore, updating Windows and software, and clearing temporary files. Downloading a repair tool may also help fix the error code.
Remove TROJ_PIDIEF.SMXY

TROJ_PIDIEF.SMXY is a malicious item which alters the registry and browser settings in your PC and thus invites multiple spywares to attack on your PC damaging it in fatal ways.
How can we remove window fix?

Window Fix removal tool has lot of features that will help you remove Window Fix virus. It is one of the best ways to remove Window Fix.
Remove Clickhoofind.com

http://www.removemalwarethreats.com/2014/10/11/uninstall-clickhoofind-com-from-windows-system Clickhoofind.com is nasty ad ware that destroys your system and steal your all information from your system.
Remove 1 startpage.com pop up

1. 1STARTPAGE.COM is an adware program that displays unwanted advertisements and security alerts to users. It can be installed through free software and suspicious programs.
2. Once installed in a browser like Internet Explorer, Chrome or Firefox, 1STARTPAGE.COM will pop up each time the user goes online and also deliver fake messages.
3. To remove 1STARTPAGE.COM, the document provides steps to uninstall it from Control Panel and delete associated files and registry keys created by the adware from the computer.
Remove search.portsayd.com redirect virus

This document provides instructions for removing the Search.portsayd.com virus. It is a trojan horse that can exploit system vulnerabilities to infect PCs. It slows down systems with porn pop-ups and uses resources to run malicious processes. The virus may also expose systems to additional malware. The document outlines steps to uninstall suspicious programs, remove related browser extensions, refresh browsers, and delete leftover files and processes to fully remove the virus.
How to remove uncheckit ads adware

UNCHECKIT ADS is just another annoying adware that was made as moneymaking tool to benefit its authors. This potentially unwanted program is effective on Google Chrome and Safari browser running under Macintosh system. Other systems may soon be the target of UNCHECKIT ADSl (also called Shop Tool) because Windows and mobile version of this adware are under development.
Remove efishedo.info from Windows PCs

efishedo.info is very dangerous browser hijacker program that is able to hijack your main browser and modifies its default setting as well. For more details:
https://www.malware-board.com/blog/remove-efishedo-info-recommended-solution
Remove flexible shopper ads

This document provides information about FlexibleShopper ads and how to remove it. It describes how FlexibleShopper ads can harm a system by altering settings without permission and opening security vulnerabilities. Several manual methods are outlined to remove FlexibleShopper ads such as using safe mode, task manager, deleting related files and registry entries. An automatic removal tool is also mentioned that can securely scan and uninstall FlexibleShopper ads and related files/processes.
How to get rid of adware win32 open candy virus

This document provides a 28 step process to remove the Adware:Win32/OpenCandy virus from an infected XP computer. The steps involve starting the computer in safe mode, disabling the proxy server, using Rkill to terminate virus processes, downloading and running Malwarebytes Anti-Malware to perform a full system scan and removal of detected threats, then restarting the computer.
RANSOMWARE

Ransomware is a type of malware that locks users out of their devices and demands ransom for access. It can enter devices through email attachments, infected websites, or networks. To prevent ransomware, users should keep software updated, firewalls on, avoid suspicious links, delete temp files, and back up data. If infected, users can use antivirus software, system restore, or data backups to remove ransomware. Staying informed and cautious about links and downloads can help prevent ransomware attacks.
Remove Savuerone

SavuErone s harmful adware whic infect your computer and steal your valuable data . So, you must remove SavuErone immeidately from your PC.
How to get rid of stop online piracy automatic protection system virus

This document provides a 28 step process to remove the Stop Online Piracy Automatic Protection System Virus from an infected Windows XP computer. The steps involve starting the computer in safe mode, using various browser links to download and run removal tools like Rkill and Malwarebytes Anti-Malware to identify and remove the virus and infected processes. After scanning and removing threats, the computer should be restarted.
Remove gangnamgame.net from pc

Most of us have had a love-hate experience relationship with online games. We all come up with bizarre ways to play some casual games online when we have browsed the web for a longtime. But when we are approaching to some websites, we usually do not have the ability to figure out whether this site is safe or not. For example, there is a site named Gangnamgame.net which is reported by many net users as it has been regarded as an insecure website recently. The most hateful feature of this site from the victims who get it from free bundles is that it acts like a browser hijacker because it tends to control browser settings forcibly. Is it really dangerous? Keep reading to find answer.
Wifi doesn't have a valid IP configuration in Windows 10

This document outlines 10 methods for fixing the "Wifi doesn't have a valid IP configuration Windows 10" error. The methods include resetting TCP/IP settings, manually assigning IP addresses, changing DHCP user limits, performing a clean boot, updating wireless drivers, enabling wireless services, and uninstalling antivirus software. Step-by-step instructions are provided for each troubleshooting method.
Delete hack tool win64 gendows: how to delete HackTool:Win64/Gendows

Free Download
http://semsols123.enigma.revenuewire.net/spyhunter/download
Buy Now
http://semsols123.enigma.revenuewire.net/spyhunter2/register
Automatic removal tool is one of the monolithic application which protects user system from all types of malicious program like HackTool:Win64/Gendows by completely deleting it from user system.
Read more:http://malware-protction1.blogspot.in/2013/02/uninstall-hacktoolwin64gendows-easy.html
While playing game getting explorer stop working

All the troubleshooting as well as causes of error "While playing game getting explorer stop working" is mentioned here. We have mentioned detail and the solutions for the same.
windows explorer has stopped working windows 7
While playing game getting explorer stop working
while playing game screen goes black
while playing game computer shuts down
While playing game getting explorer stop working
while playing game computer freezes
while playing game computer restarts
lagging while playing game
laptop overheat while playing game
While playing game getting explorer stop working
laptop shutdowns while playing game
while playing games screen flickers
computer crashes while playing games
while playing games laptop shuts down
while playing games monitor turns off
While playing game getting explorer stop working
Guide to remove infomoneyservice.com redirect virus

This document provides a 28 step guide to remove the Infomoneyservice.com redirect virus from an infected Windows XP computer. The steps involve starting the computer in safe mode, using various tools like Rkill and Malwarebytes Anti-Malware to kill virus processes and perform a full system scan and removal. After completing all steps, the computer should be restarted to complete the removal process.
Safe guide to remove P24.EXE

P24.EXE is creepy adware infection that targets all installed browser and cause plenty of annoying trouble. For smooth PC running, it is important to eliminate this nasty threat and all its related files. For more info visit: https://www.malware-board.com/blog/best-tips-to-remove-p24-exe
Remove bilisearch.com redirect virus

I am dealing with the problem of Bilisearch.com redirect virus. This site has both taken my homepage and search provider of Google Chrome without my permission. I do not know how does it come to my computer and change the browser settings at the beginning. But I am trying to find effective solutions to remove it from computer since I have found its modification. Please help.
How to get rid of polizia postale e delle virus

This document provides a 28 step process to remove Polizia postale e delle virus from an infected XP computer. The steps include starting the computer in safe mode, running various programs like Rkill and Malwarebytes to identify and remove the virus, and then restarting the computer.
Spyware Removal

To avoid spyware:
1) Be cautious of sites that appear to have what you're looking for online as visiting them could infect your computer with viruses and spyware.
2) If your computer becomes infected, do not click buttons that claim to remove infections for a fee, as this could expose your personal information.
3) To remove spyware, press Ctrl+Alt+Delete to open Task Manager, end suspicious programs' tasks, download a free spyware removal program, and scan and remove all threats.
How to get rid of microsoft security essentials alert virus

This document provides a 28 step process to remove Microsoft Security Essentials alerts about a virus called XP Antispyware 2013. The steps involve starting the computer in safe mode, using various browser links to download and run removal tools like Rkill and Malwarebytes Anti-Malware to identify and remove the infected files and processes. After scanning and selecting infected items for removal, the computer should be restarted.
How to REMOVE yoursearching.com

Nowadays, many victims of Yoursearching.com are seeking solutions online. They encounter a lot of problems when using this dubious search tool as their default homepage and search engine. For their problems, this page will give them a corresponding answer & solution.
Introduction to an ICT based cross curricular resource for PGDE Geography

Presentation given at St Andrews Building, University of Glasgow on 19th January 2017 by Anne Robertson, EDINA, University of Edinburgh about the Digimap for School service.
More Related Content
What's hot
Remove 1 startpage.com pop up

1. 1STARTPAGE.COM is an adware program that displays unwanted advertisements and security alerts to users. It can be installed through free software and suspicious programs.
2. Once installed in a browser like Internet Explorer, Chrome or Firefox, 1STARTPAGE.COM will pop up each time the user goes online and also deliver fake messages.
3. To remove 1STARTPAGE.COM, the document provides steps to uninstall it from Control Panel and delete associated files and registry keys created by the adware from the computer.
Remove search.portsayd.com redirect virus

This document provides instructions for removing the Search.portsayd.com virus. It is a trojan horse that can exploit system vulnerabilities to infect PCs. It slows down systems with porn pop-ups and uses resources to run malicious processes. The virus may also expose systems to additional malware. The document outlines steps to uninstall suspicious programs, remove related browser extensions, refresh browsers, and delete leftover files and processes to fully remove the virus.
How to remove uncheckit ads adware

UNCHECKIT ADS is just another annoying adware that was made as moneymaking tool to benefit its authors. This potentially unwanted program is effective on Google Chrome and Safari browser running under Macintosh system. Other systems may soon be the target of UNCHECKIT ADSl (also called Shop Tool) because Windows and mobile version of this adware are under development.
Remove efishedo.info from Windows PCs

efishedo.info is very dangerous browser hijacker program that is able to hijack your main browser and modifies its default setting as well. For more details:
https://www.malware-board.com/blog/remove-efishedo-info-recommended-solution
Remove flexible shopper ads

This document provides information about FlexibleShopper ads and how to remove it. It describes how FlexibleShopper ads can harm a system by altering settings without permission and opening security vulnerabilities. Several manual methods are outlined to remove FlexibleShopper ads such as using safe mode, task manager, deleting related files and registry entries. An automatic removal tool is also mentioned that can securely scan and uninstall FlexibleShopper ads and related files/processes.
How to get rid of adware win32 open candy virus

This document provides a 28 step process to remove the Adware:Win32/OpenCandy virus from an infected XP computer. The steps involve starting the computer in safe mode, disabling the proxy server, using Rkill to terminate virus processes, downloading and running Malwarebytes Anti-Malware to perform a full system scan and removal of detected threats, then restarting the computer.
RANSOMWARE

Ransomware is a type of malware that locks users out of their devices and demands ransom for access. It can enter devices through email attachments, infected websites, or networks. To prevent ransomware, users should keep software updated, firewalls on, avoid suspicious links, delete temp files, and back up data. If infected, users can use antivirus software, system restore, or data backups to remove ransomware. Staying informed and cautious about links and downloads can help prevent ransomware attacks.
Remove Savuerone

SavuErone s harmful adware whic infect your computer and steal your valuable data . So, you must remove SavuErone immeidately from your PC.
How to get rid of stop online piracy automatic protection system virus

This document provides a 28 step process to remove the Stop Online Piracy Automatic Protection System Virus from an infected Windows XP computer. The steps involve starting the computer in safe mode, using various browser links to download and run removal tools like Rkill and Malwarebytes Anti-Malware to identify and remove the virus and infected processes. After scanning and removing threats, the computer should be restarted.
Remove gangnamgame.net from pc

Most of us have had a love-hate experience relationship with online games. We all come up with bizarre ways to play some casual games online when we have browsed the web for a longtime. But when we are approaching to some websites, we usually do not have the ability to figure out whether this site is safe or not. For example, there is a site named Gangnamgame.net which is reported by many net users as it has been regarded as an insecure website recently. The most hateful feature of this site from the victims who get it from free bundles is that it acts like a browser hijacker because it tends to control browser settings forcibly. Is it really dangerous? Keep reading to find answer.
Wifi doesn't have a valid IP configuration in Windows 10

This document outlines 10 methods for fixing the "Wifi doesn't have a valid IP configuration Windows 10" error. The methods include resetting TCP/IP settings, manually assigning IP addresses, changing DHCP user limits, performing a clean boot, updating wireless drivers, enabling wireless services, and uninstalling antivirus software. Step-by-step instructions are provided for each troubleshooting method.
Delete hack tool win64 gendows: how to delete HackTool:Win64/Gendows

Free Download
http://semsols123.enigma.revenuewire.net/spyhunter/download
Buy Now
http://semsols123.enigma.revenuewire.net/spyhunter2/register
Automatic removal tool is one of the monolithic application which protects user system from all types of malicious program like HackTool:Win64/Gendows by completely deleting it from user system.
Read more:http://malware-protction1.blogspot.in/2013/02/uninstall-hacktoolwin64gendows-easy.html
While playing game getting explorer stop working

All the troubleshooting as well as causes of error "While playing game getting explorer stop working" is mentioned here. We have mentioned detail and the solutions for the same.
windows explorer has stopped working windows 7
While playing game getting explorer stop working
while playing game screen goes black
while playing game computer shuts down
While playing game getting explorer stop working
while playing game computer freezes
while playing game computer restarts
lagging while playing game
laptop overheat while playing game
While playing game getting explorer stop working
laptop shutdowns while playing game
while playing games screen flickers
computer crashes while playing games
while playing games laptop shuts down
while playing games monitor turns off
While playing game getting explorer stop working
Guide to remove infomoneyservice.com redirect virus

This document provides a 28 step guide to remove the Infomoneyservice.com redirect virus from an infected Windows XP computer. The steps involve starting the computer in safe mode, using various tools like Rkill and Malwarebytes Anti-Malware to kill virus processes and perform a full system scan and removal. After completing all steps, the computer should be restarted to complete the removal process.
Safe guide to remove P24.EXE

P24.EXE is creepy adware infection that targets all installed browser and cause plenty of annoying trouble. For smooth PC running, it is important to eliminate this nasty threat and all its related files. For more info visit: https://www.malware-board.com/blog/best-tips-to-remove-p24-exe
Remove bilisearch.com redirect virus

I am dealing with the problem of Bilisearch.com redirect virus. This site has both taken my homepage and search provider of Google Chrome without my permission. I do not know how does it come to my computer and change the browser settings at the beginning. But I am trying to find effective solutions to remove it from computer since I have found its modification. Please help.
How to get rid of polizia postale e delle virus

This document provides a 28 step process to remove Polizia postale e delle virus from an infected XP computer. The steps include starting the computer in safe mode, running various programs like Rkill and Malwarebytes to identify and remove the virus, and then restarting the computer.
Spyware Removal

To avoid spyware:
1) Be cautious of sites that appear to have what you're looking for online as visiting them could infect your computer with viruses and spyware.
2) If your computer becomes infected, do not click buttons that claim to remove infections for a fee, as this could expose your personal information.
3) To remove spyware, press Ctrl+Alt+Delete to open Task Manager, end suspicious programs' tasks, download a free spyware removal program, and scan and remove all threats.
How to get rid of microsoft security essentials alert virus

This document provides a 28 step process to remove Microsoft Security Essentials alerts about a virus called XP Antispyware 2013. The steps involve starting the computer in safe mode, using various browser links to download and run removal tools like Rkill and Malwarebytes Anti-Malware to identify and remove the infected files and processes. After scanning and selecting infected items for removal, the computer should be restarted.
How to REMOVE yoursearching.com

Nowadays, many victims of Yoursearching.com are seeking solutions online. They encounter a lot of problems when using this dubious search tool as their default homepage and search engine. For their problems, this page will give them a corresponding answer & solution.
What's hot (20)
How to get rid of stop online piracy automatic protection system virus

How to get rid of stop online piracy automatic protection system virus
Wifi doesn't have a valid IP configuration in Windows 10

Wifi doesn't have a valid IP configuration in Windows 10
Delete hack tool win64 gendows: how to delete HackTool:Win64/Gendows

Delete hack tool win64 gendows: how to delete HackTool:Win64/Gendows
Guide to remove infomoneyservice.com redirect virus

Guide to remove infomoneyservice.com redirect virus
How to get rid of microsoft security essentials alert virus

How to get rid of microsoft security essentials alert virus
Viewers also liked
Introduction to an ICT based cross curricular resource for PGDE Geography

Presentation given at St Andrews Building, University of Glasgow on 19th January 2017 by Anne Robertson, EDINA, University of Edinburgh about the Digimap for School service.
Definiciones de las diferentes amenazas de seguridad informática, 1 b

Un virus informático es un programa malicioso que se propaga infectando otros archivos y programas sin el consentimiento del usuario, con el objetivo de dañar o alterar el funcionamiento del sistema. Puede copiarse a sí mismo y propagarse, ocasionando desde efectos molestos hasta daños graves e irreparables en los datos y sistemas. Los troyanos también son considerados virus aunque no se reproduzcan, y pueden robar información confidencial o ejecutar acciones no deseadas en el sistema.
Almonds

Almonds originate from Prunus dulcis trees and are cultivated for their edible seeds. There are different types of almonds including bitter, sweet, and California almonds. Almonds provide many health benefits as they are a rich source of proteins, vitamins, minerals, fats, and fiber. Specifically, almonds may help prevent heart disease, support brain health, maintain skin health, control blood sugar levels, aid in weight loss, and increase nutrient absorption. While almonds provide these benefits, they also face issues in international trade that must be discussed.
Global Phenotypic Data Sharing Standards to Maximize Diagnostics and Mechanis...

Presented at the IRDiRC 2017 conference in Paris, Feb 9th, 2017 (http://irdirc-conference.org/). This talk reviews use of the Human Phenotype Ontology for phenotype comparisons against other patients, known diseases, and animal models for diagnostic discovery. It also discusses the new Phenopackets Exchange mechanism for open phenotypic data sharing.
www.monarchinitiative.org
www.phenopackets.org
www.human-phenotype-ontology.org
Dear Mr. Kilmer

1. Richard lives on a farm in Iowa with his family in 1917. He and his brother Gus hike to their hunting cabin in the woods where Richard plans to shoot his first deer the next day.
2. The next morning, they wait by a large pool and Richard prays that no deer will come. A large buck appears nearby but Richard deliberately misses shooting it.
3. Richard's father asks why he missed the deer, and Richard explains that he does not feel right killing animals as it is painful and makes him sad.
Blue brain

The Blue Brain project aims to create a virtual human brain using supercomputers. Started in 2005 in Switzerland, it seeks to understand the brain and help treat diseases. The project uses supercomputers and custom components to simulate neurons and neural connections in the brain. Its goal is to fully simulate the human brain with 86 billion neurons by 2023 through continued funding and development.
Mr kilmer summary

This chapter summary provides an overview of the key events and ideas discussed in a chapter. In a concise manner, it outlines the main characters, plot points, and themes covered to help the reader understand what occurred without having to read the full chapter text. The summary efficiently conveys the essential narrative and analytical content for the reader.
Si no ets a Linkedin, no et trobaran

Sessió de formació als estudiants i graduats de la UdG organitzada per la Borsa de Treball de la Universitat de Girona
Integration of Things (Sam Vanhoutte @Iglooconf 2017) 

To build an overall IoT solution, a lof of different technologies and skills are needed and the role of an architect is crucial to combine all the different services into a solid solution. In this presentation, you will understand more about the DNA of a typical IoT solution, based on Microsoft Azure. You will see the different pitfalls that come with implementing Industrial IoT solutions.
Viewers also liked (10)
Introduction to an ICT based cross curricular resource for PGDE Geography

Introduction to an ICT based cross curricular resource for PGDE Geography
Definiciones de las diferentes amenazas de seguridad informática, 1 b

Definiciones de las diferentes amenazas de seguridad informática, 1 b
Global Phenotypic Data Sharing Standards to Maximize Diagnostics and Mechanis...

Global Phenotypic Data Sharing Standards to Maximize Diagnostics and Mechanis...
Integration of Things (Sam Vanhoutte @Iglooconf 2017) 

Integration of Things (Sam Vanhoutte @Iglooconf 2017)
Similar to How to remove Trojan.Mirai
How to remove malware from your windows computer

Step by step guide for all PC owners that teaches you how to remove malware from your Windows computer.
Delete How tosimplified toolbar

How tosimplified toolbar is a malicious threat which can modify your browsers settings and keep slow down your system.
Remove Trojanwin32/comame!gm

Trojanwin32/comame!gm is harmful trojan infection which completely deteriorate your system performance.
Slideshare lyrics container

This document provides instructions for manually removing the LyricsContainer virus from an infected computer. LyricsContainer is a browser hijacker that promotes advertisements and steals user information. It slows down computer performance over time by running in the background and installing additional viruses. The instructions outline three steps: ending the LyricsContainer process in Task Manager, showing and deleting hidden malicious files, and removing malicious registry entries associated with LyricsContainer. Assistance is offered from Tee Support computer experts for any issues completing the removal.
lyrics container

This document provides instructions for manually removing the LyricsContainer virus from an infected computer. LyricsContainer is a browser hijacker that promotes advertisements and steals user information. It slows down computer performance over time by running in the background and installing additional viruses. The instructions outline three steps: ending the LyricsContainer process in Task Manager, showing and deleting hidden malicious files, and removing malicious registry entries associated with LyricsContainer. Assistance is offered from Tee Support computer experts for any issues completing the removal.
Win32patched blogspot in

The good thing about this virus is that it does not disable the Task manager. Open the task manager by right clicking the
uninstall Bit toolbar

Bit toolbar is a malicious ad ware program that corrupt your browsers activity cheats your all information from your system.
Win32 trojan gen

What’s Win32:Trojan-gen? What are the Win32-trojan-gen removal tools? How to manually delete Win32 Trojan? Numerous methods for you to choose from.
Remove monstermarketplace.com

This document provides instructions to remove the Monstermarketplace.com virus from a user's computer. It describes the virus as a browser hijacker that redirects the user to unwanted websites and slows down system performance. A 5-step manual removal process is outlined that includes ending virus processes, clearing browser history/files, removing add-ons, finding and deleting malicious files, and removing registry entries associated with the virus. Users needing additional help are advised to contact online computer support.
How To Uninstall Masksearch.com

Is your system deluged with unknown or Masksearch.com? Are you frequently rerouted to the unfamiliar or suspicious sites?
Get Rid Of Windows High-End Protection In Few Simple Automatic Steps

Windows High-End Protection claims to be a security application but is actually a malicious application that can cause several problem and can even lead to various corruption issues.Once it attacks your system leads to slowing in the system performance.It is extremely harmful for your system that results in hindering the working of system.
Virus Elimination Course 

Learn How to eliminate Computer Viruses, Windows Registry, Group Policy and useful built in tools in Microsoft Windows.
Remove alnaddy.com computer virus

Are you bored by alnaddy.com computer virus? The antivirus software failed to delete alnaddy.com redirect, what should you do? read this passage and learn the most effective method to get rid of alnaddy.com infection
Best guide to remove ads by dealnj popup

Do you often receive lots of ads by Dealnj when using the web browsers, especially when visiting shopping sites? Why do those ads which have never occurred before keep showing up on your browsers? Is your computer infected by a virus? How can you get rid of it? Follow the guide below and you will learn more about Dealnj as well as the methods of removing it.
Uninstall Win 7 Security Cleaner Pro

Win 7 Security Cleaner Pro is a malicious item which alters the registry and browser settings in your PC and thus invites multiple spywares to attack on your PC damaging it in fatal ways.
Tips to remove contradeplatform

Browsers as Chrome, Firefox, IE and other famous browsers will be targeted by such infection firstly as it can be installed onto the system via acting like a browser add-on or extension. Under most situations, it is utilized to promote commercial sites so as to increase page-rank of the sites or advertise programs or services provided by those sites in order to get money.
Remove Windows Premium Guard In Few Simple Automatic Steps

Windows Premium Guard claims to be a security application but is actually a malicious application that can cause several problem and can even lead to various corruption issues.
Dosearches virus removal

Do Searches is a browser hijacker that changes the browser homepage and search engine settings without permission. It displays ads on the homepage and collects search terms. It is distributed through other free software installers. To remove it, use AdwCleaner to remove malicious files, Junkware Removal Tool to remove it from browsers, manually edit browser shortcuts, use Malwarebytes to scan for remaining files, and use HitmanPro as a second scan. Always be careful during software installs and opt out of optional installs you don't want.
Coupon chaser

Coupon Chaser appears in-front of user as an stand-alone application but is actually an infectious adware that bundles numerous infection in it. Presence of Coupon Chaser can lead to several issues as system starts responding abruptly , problem in loading OS , redirection to malicious sites and unwanted uploads etc.
Click The Link Below :
http://www.winsecuritythreatremoval.com/2014/08/03/remove-couponchaser/
Fixing browser redirection viruses

Browser hijacking is a serious nuisance in today’s web surfing experience. Fortunately, avoiding a browser hijacking is not impossible if you stay aware, and take a few simple precautions.
Similar to How to remove Trojan.Mirai (20)
Get Rid Of Windows High-End Protection In Few Simple Automatic Steps

Get Rid Of Windows High-End Protection In Few Simple Automatic Steps
Remove Windows Premium Guard In Few Simple Automatic Steps

Remove Windows Premium Guard In Few Simple Automatic Steps
Recently uploaded
HCL Notes and Domino License Cost Reduction in the World of DLAU

Webinar Recording: https://www.panagenda.com/webinars/hcl-notes-and-domino-license-cost-reduction-in-the-world-of-dlau/
The introduction of DLAU and the CCB & CCX licensing model caused quite a stir in the HCL community. As a Notes and Domino customer, you may have faced challenges with unexpected user counts and license costs. You probably have questions on how this new licensing approach works and how to benefit from it. Most importantly, you likely have budget constraints and want to save money where possible. Don’t worry, we can help with all of this!
We’ll show you how to fix common misconfigurations that cause higher-than-expected user counts, and how to identify accounts which you can deactivate to save money. There are also frequent patterns that can cause unnecessary cost, like using a person document instead of a mail-in for shared mailboxes. We’ll provide examples and solutions for those as well. And naturally we’ll explain the new licensing model.
Join HCL Ambassador Marc Thomas in this webinar with a special guest appearance from Franz Walder. It will give you the tools and know-how to stay on top of what is going on with Domino licensing. You will be able lower your cost through an optimized configuration and keep it low going forward.
These topics will be covered
- Reducing license cost by finding and fixing misconfigurations and superfluous accounts
- How do CCB and CCX licenses really work?
- Understanding the DLAU tool and how to best utilize it
- Tips for common problem areas, like team mailboxes, functional/test users, etc
- Practical examples and best practices to implement right away
GraphRAG for Life Science to increase LLM accuracy

GraphRAG for life science domain, where you retriever information from biomedical knowledge graphs using LLMs to increase the accuracy and performance of generated answers
Generating privacy-protected synthetic data using Secludy and Milvus

During this demo, the founders of Secludy will demonstrate how their system utilizes Milvus to store and manipulate embeddings for generating privacy-protected synthetic data. Their approach not only maintains the confidentiality of the original data but also enhances the utility and scalability of LLMs under privacy constraints. Attendees, including machine learning engineers, data scientists, and data managers, will witness first-hand how Secludy's integration with Milvus empowers organizations to harness the power of LLMs securely and efficiently.
Project Management Semester Long Project - Acuity

Acuity is an innovative learning app designed to transform the way you engage with knowledge. Powered by AI technology, Acuity takes complex topics and distills them into concise, interactive summaries that are easy to read & understand. Whether you're exploring the depths of quantum mechanics or seeking insight into historical events, Acuity provides the key information you need without the burden of lengthy texts.
20240607 QFM018 Elixir Reading List May 2024

Everything I found interesting about the Elixir programming ecosystem in May 2024
How to Get CNIC Information System with Paksim Ga.pptx

Pakdata Cf is a groundbreaking system designed to streamline and facilitate access to CNIC information. This innovative platform leverages advanced technology to provide users with efficient and secure access to their CNIC details.
Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack

Discover the seamless integration of RPA (Robotic Process Automation), COMPOSER, and APM with AWS IDP enhanced with Slack notifications. Explore how these technologies converge to streamline workflows, optimize performance, and ensure secure access, all while leveraging the power of AWS IDP and real-time communication via Slack notifications.
Cosa hanno in comune un mattoncino Lego e la backdoor XZ?

ABSTRACT: A prima vista, un mattoncino Lego e la backdoor XZ potrebbero avere in comune il fatto di essere entrambi blocchi di costruzione, o dipendenze di progetti creativi e software. La realtà è che un mattoncino Lego e il caso della backdoor XZ hanno molto di più di tutto ciò in comune.
Partecipate alla presentazione per immergervi in una storia di interoperabilità, standard e formati aperti, per poi discutere del ruolo importante che i contributori hanno in una comunità open source sostenibile.
BIO: Sostenitrice del software libero e dei formati standard e aperti. È stata un membro attivo dei progetti Fedora e openSUSE e ha co-fondato l'Associazione LibreItalia dove è stata coinvolta in diversi eventi, migrazioni e formazione relativi a LibreOffice. In precedenza ha lavorato a migrazioni e corsi di formazione su LibreOffice per diverse amministrazioni pubbliche e privati. Da gennaio 2020 lavora in SUSE come Software Release Engineer per Uyuni e SUSE Manager e quando non segue la sua passione per i computer e per Geeko coltiva la sua curiosità per l'astronomia (da cui deriva il suo nickname deneb_alpha).
Your One-Stop Shop for Python Success: Top 10 US Python Development Providers

Simplify your search for a reliable Python development partner! This list presents the top 10 trusted US providers offering comprehensive Python development services, ensuring your project's success from conception to completion.
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Discover how MongoDB Atlas and vector search technology can revolutionize your application's search capabilities. This comprehensive presentation covers:
* What is Vector Search?
* Importance and benefits of vector search
* Practical use cases across various industries
* Step-by-step implementation guide
* Live demos with code snippets
* Enhancing LLM capabilities with vector search
* Best practices and optimization strategies
Perfect for developers, AI enthusiasts, and tech leaders. Learn how to leverage MongoDB Atlas to deliver highly relevant, context-aware search results, transforming your data retrieval process. Stay ahead in tech innovation and maximize the potential of your applications.
#MongoDB #VectorSearch #AI #SemanticSearch #TechInnovation #DataScience #LLM #MachineLearning #SearchTechnology
Presentation of the OECD Artificial Intelligence Review of Germany

Consult the full report at https://www.oecd.org/digital/oecd-artificial-intelligence-review-of-germany-609808d6-en.htm
How to Interpret Trends in the Kalyan Rajdhani Mix Chart.pdf

A Mix Chart displays historical data of numbers in a graphical or tabular form. The Kalyan Rajdhani Mix Chart specifically shows the results of a sequence of numbers over different periods.
Artificial Intelligence for XMLDevelopment

In the rapidly evolving landscape of technologies, XML continues to play a vital role in structuring, storing, and transporting data across diverse systems. The recent advancements in artificial intelligence (AI) present new methodologies for enhancing XML development workflows, introducing efficiency, automation, and intelligent capabilities. This presentation will outline the scope and perspective of utilizing AI in XML development. The potential benefits and the possible pitfalls will be highlighted, providing a balanced view of the subject.
We will explore the capabilities of AI in understanding XML markup languages and autonomously creating structured XML content. Additionally, we will examine the capacity of AI to enrich plain text with appropriate XML markup. Practical examples and methodological guidelines will be provided to elucidate how AI can be effectively prompted to interpret and generate accurate XML markup.
Further emphasis will be placed on the role of AI in developing XSLT, or schemas such as XSD and Schematron. We will address the techniques and strategies adopted to create prompts for generating code, explaining code, or refactoring the code, and the results achieved.
The discussion will extend to how AI can be used to transform XML content. In particular, the focus will be on the use of AI XPath extension functions in XSLT, Schematron, Schematron Quick Fixes, or for XML content refactoring.
The presentation aims to deliver a comprehensive overview of AI usage in XML development, providing attendees with the necessary knowledge to make informed decisions. Whether you’re at the early stages of adopting AI or considering integrating it in advanced XML development, this presentation will cover all levels of expertise.
By highlighting the potential advantages and challenges of integrating AI with XML development tools and languages, the presentation seeks to inspire thoughtful conversation around the future of XML development. We’ll not only delve into the technical aspects of AI-powered XML development but also discuss practical implications and possible future directions.
5th LF Energy Power Grid Model Meet-up Slides

5th Power Grid Model Meet-up
It is with great pleasure that we extend to you an invitation to the 5th Power Grid Model Meet-up, scheduled for 6th June 2024. This event will adopt a hybrid format, allowing participants to join us either through an online Mircosoft Teams session or in person at TU/e located at Den Dolech 2, Eindhoven, Netherlands. The meet-up will be hosted by Eindhoven University of Technology (TU/e), a research university specializing in engineering science & technology.
Power Grid Model
The global energy transition is placing new and unprecedented demands on Distribution System Operators (DSOs). Alongside upgrades to grid capacity, processes such as digitization, capacity optimization, and congestion management are becoming vital for delivering reliable services.
Power Grid Model is an open source project from Linux Foundation Energy and provides a calculation engine that is increasingly essential for DSOs. It offers a standards-based foundation enabling real-time power systems analysis, simulations of electrical power grids, and sophisticated what-if analysis. In addition, it enables in-depth studies and analysis of the electrical power grid’s behavior and performance. This comprehensive model incorporates essential factors such as power generation capacity, electrical losses, voltage levels, power flows, and system stability.
Power Grid Model is currently being applied in a wide variety of use cases, including grid planning, expansion, reliability, and congestion studies. It can also help in analyzing the impact of renewable energy integration, assessing the effects of disturbances or faults, and developing strategies for grid control and optimization.
What to expect
For the upcoming meetup we are organizing, we have an exciting lineup of activities planned:
-Insightful presentations covering two practical applications of the Power Grid Model.
-An update on the latest advancements in Power Grid -Model technology during the first and second quarters of 2024.
-An interactive brainstorming session to discuss and propose new feature requests.
-An opportunity to connect with fellow Power Grid Model enthusiasts and users.
“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...

“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...Edge AI and Vision Alliance
For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2024/06/building-and-scaling-ai-applications-with-the-nx-ai-manager-a-presentation-from-network-optix/
Robin van Emden, Senior Director of Data Science at Network Optix, presents the “Building and Scaling AI Applications with the Nx AI Manager,” tutorial at the May 2024 Embedded Vision Summit.
In this presentation, van Emden covers the basics of scaling edge AI solutions using the Nx tool kit. He emphasizes the process of developing AI models and deploying them globally. He also showcases the conversion of AI models and the creation of effective edge AI pipelines, with a focus on pre-processing, model conversion, selecting the appropriate inference engine for the target hardware and post-processing.
van Emden shows how Nx can simplify the developer’s life and facilitate a rapid transition from concept to production-ready applications.He provides valuable insights into developing scalable and efficient edge AI solutions, with a strong focus on practical implementation.Recently uploaded (20)
HCL Notes and Domino License Cost Reduction in the World of DLAU

HCL Notes and Domino License Cost Reduction in the World of DLAU
GraphRAG for Life Science to increase LLM accuracy

GraphRAG for Life Science to increase LLM accuracy
Generating privacy-protected synthetic data using Secludy and Milvus

Generating privacy-protected synthetic data using Secludy and Milvus
Deep Dive: AI-Powered Marketing to Get More Leads and Customers with HyperGro...

Deep Dive: AI-Powered Marketing to Get More Leads and Customers with HyperGro...
How to Get CNIC Information System with Paksim Ga.pptx

How to Get CNIC Information System with Paksim Ga.pptx
Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack

Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack
Cosa hanno in comune un mattoncino Lego e la backdoor XZ?

Cosa hanno in comune un mattoncino Lego e la backdoor XZ?
Your One-Stop Shop for Python Success: Top 10 US Python Development Providers

Your One-Stop Shop for Python Success: Top 10 US Python Development Providers
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf
Presentation of the OECD Artificial Intelligence Review of Germany

Presentation of the OECD Artificial Intelligence Review of Germany
How to Interpret Trends in the Kalyan Rajdhani Mix Chart.pdf

How to Interpret Trends in the Kalyan Rajdhani Mix Chart.pdf
WeTestAthens: Postman's AI & Automation Techniques

WeTestAthens: Postman's AI & Automation Techniques
“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...

“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...
How to remove Trojan.Mirai
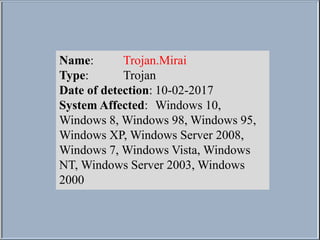
- 1. Name: Trojan.Mirai Type: Trojan Date of detection: 10-02-2017 System Affected: Windows 10, Windows 8, Windows 98, Windows 95, Windows XP, Windows Server 2008, Windows 7, Windows Vista, Windows NT, Windows Server 2003, Windows 2000
- 2. Slow Internet Connection Modification in registry folder Open backdoor Hijacked search results Hijacked homepage Sluggish Respond of software Strange Icons on desktop and/or taskbar Tons of pop ups Sponsored ads with redirect links Crashing OS frequently Symptoms of Trojan.Mirai
- 3. Only two known methods to get rid of Trojan.Mirai completely from PC: Step 1: Manual method Step 2: Automatic method (Recommended) Removal Methods for Trojan.Mirai
- 4. Manual method to remove Trojan.Mirai includes several different steps that captures entire PC section including registry folder and start up folder. Few steps to get rid of Trojan.Mirai infection from PC: -Uninstall harmful and unknown programs from control panel - Remove additional programs from start up list -Clean desktop by removing additional shortcuts -Clear registries by deleting malicious executables - Clear browsers by setting them up to correct domains Manual Methods for Trojan.Mirai
- 5. Step 1: Uninstall Trojan from control panel On any windows, simply go to control panel and then programs and features. Search for new and irrelevant installation and double click on that to uninstall. Manual Methods for Trojan.Mirai
- 6. Step 1: Uninstall Trojan from control panel Manual Methods for Trojan.Mirai
- 7. Step 2: Remove additional program from Start up Click Ctrl+Shift+esc to open task manager. Shift the tab to startup and disable unexpected program. Manual Methods for Trojan.Mirai
- 8. Step 2: Remove additional program from Start up Manual Methods for Trojan.Mirai
- 9. Step 3: Clear Registry Folder by removing additional attachments Click windows button+r, then type regedit. Now delete the programs you find related with Trojan infection. Manual Methods for Trojan.Mirai
- 10. Step 4: Reset all installed affected browsers by settings their homepage and default search provider to genuine location. Manual Methods for Trojan.Mirai
- 11. Automatic method is recommend solution to get rid of Trojan.Mirai infection completely. You need to download free security provider SpyHunter by clicking here. It is proven solution to provide PC security in future also. Automatic Method for Trojan.Mirai Download SpyHunter
- 12. After Downloading, double click on exe file and click yes to continue Automatic Method for Trojan.Mirai Download SpyHunter
- 13. Choose language Automatic Method for Trojan.Mirai
- 14. To proceed the installation, click continue button Automatic Method for Trojan.Mirai
- 15. Read and accept, end user license agreement and click Install button Automatic Method for Trojan.Mirai
- 16. Click Finish on last step. Automatic Method for Trojan.Mirai
- 17. Take Step to Remove Trojan.Mirai Permanents and Give Future Security to Your PC Thanks for Watching