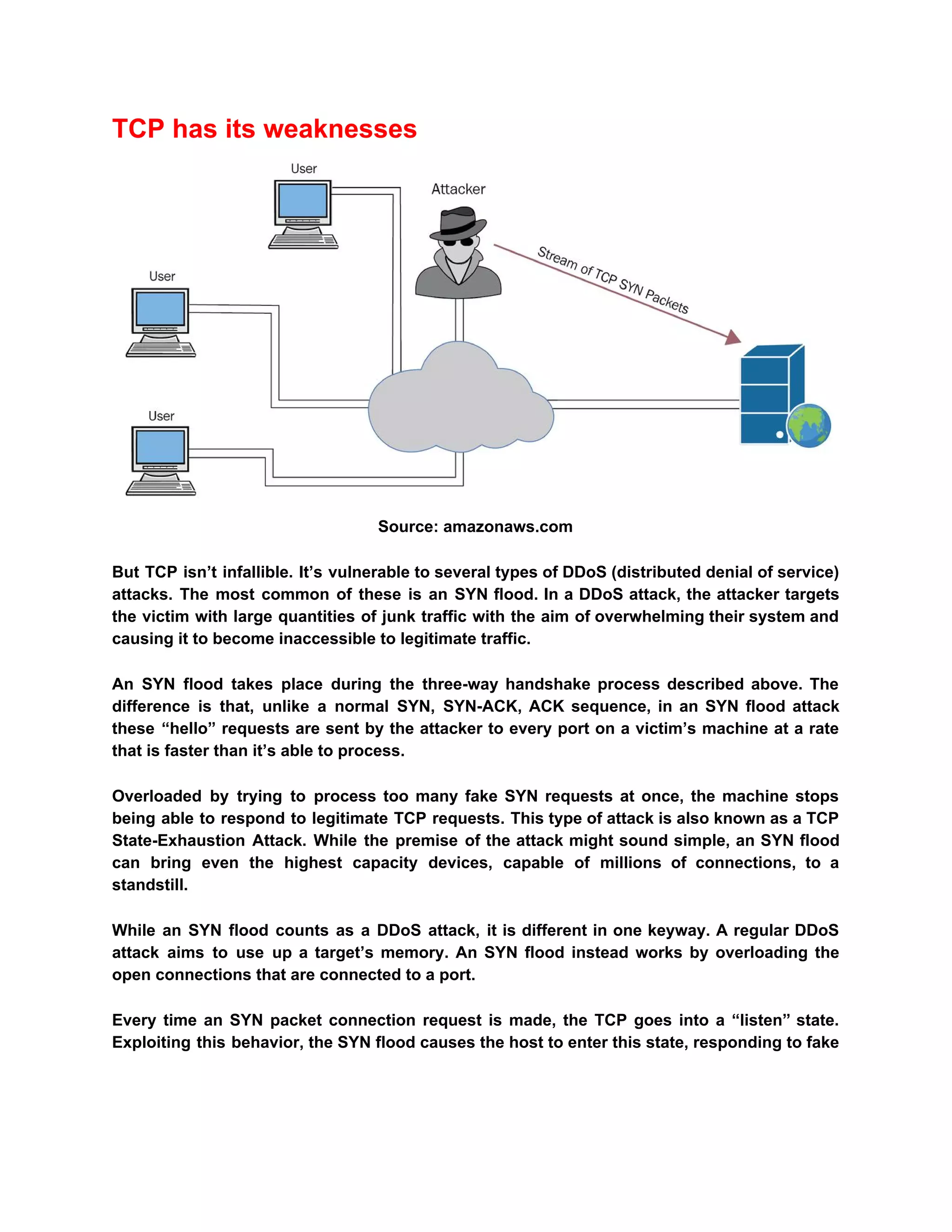
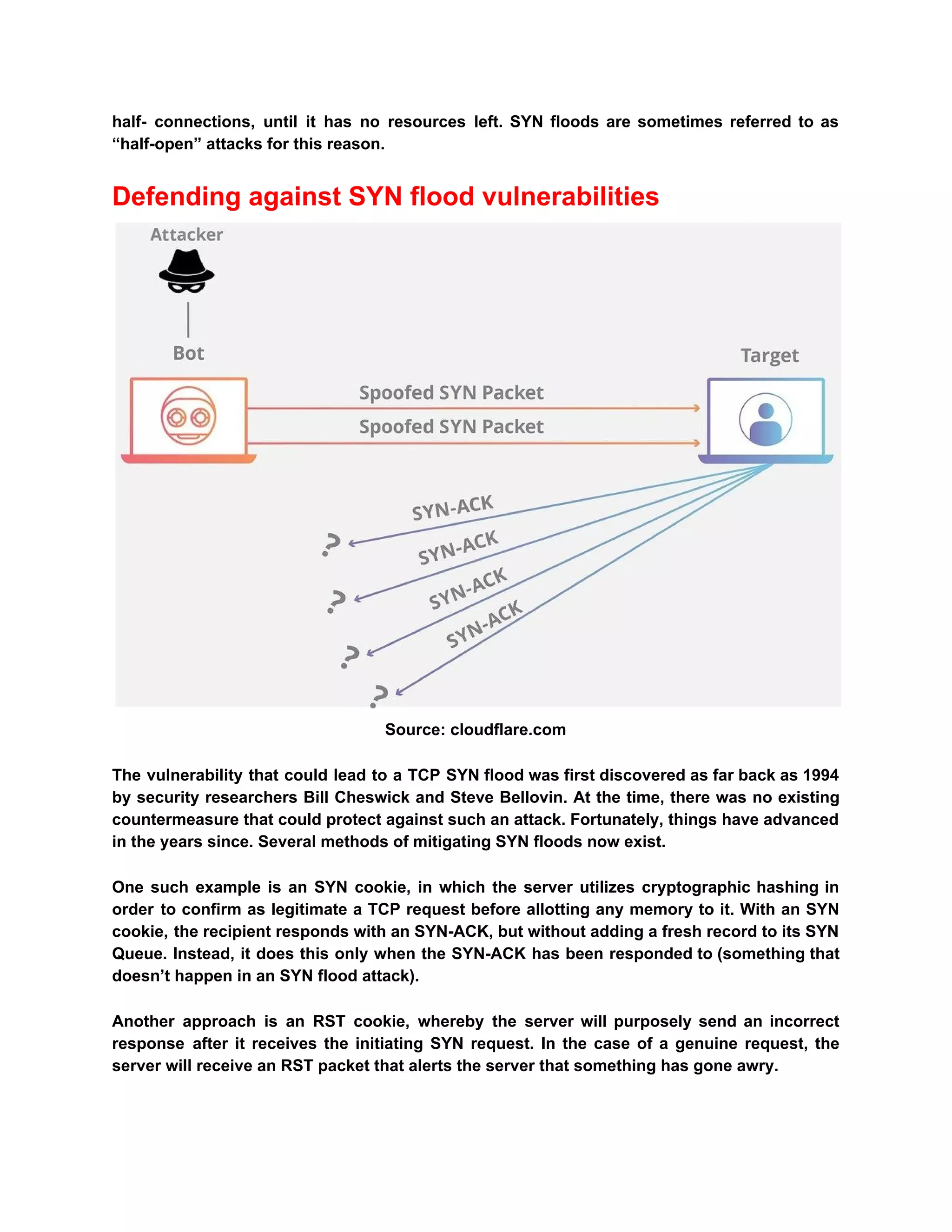
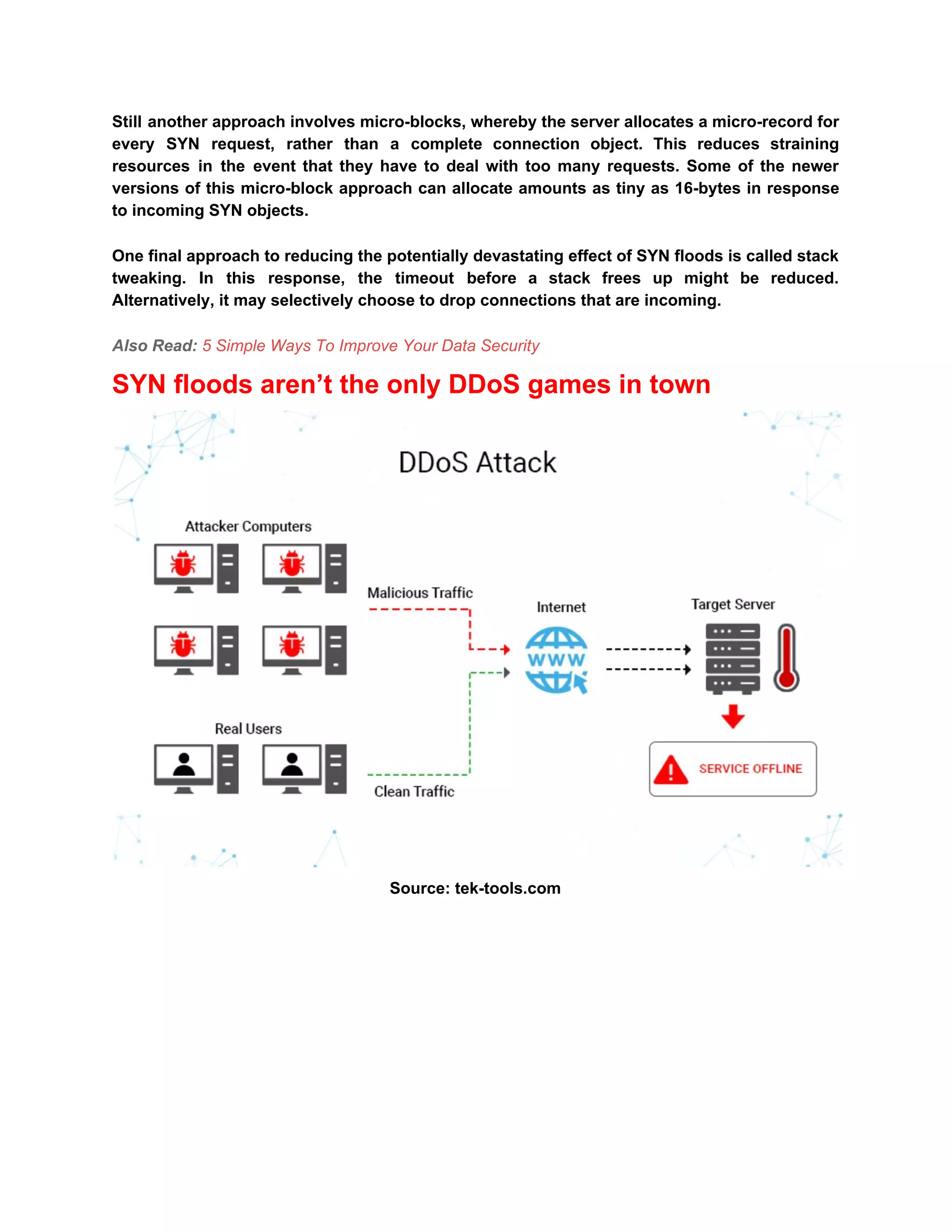
The document describes TCP SYN flood attacks, where an attacker overwhelms a victim's system during the TCP three-way handshake, preventing it from processing legitimate requests. It outlines the vulnerabilities of TCP to such attacks and presents several mitigation strategies like SYN cookies, RST cookies, micro-blocks, and stack tweaking. Additionally, it emphasizes the importance of robust DDoS protection for organizations to prevent financial and reputational losses.