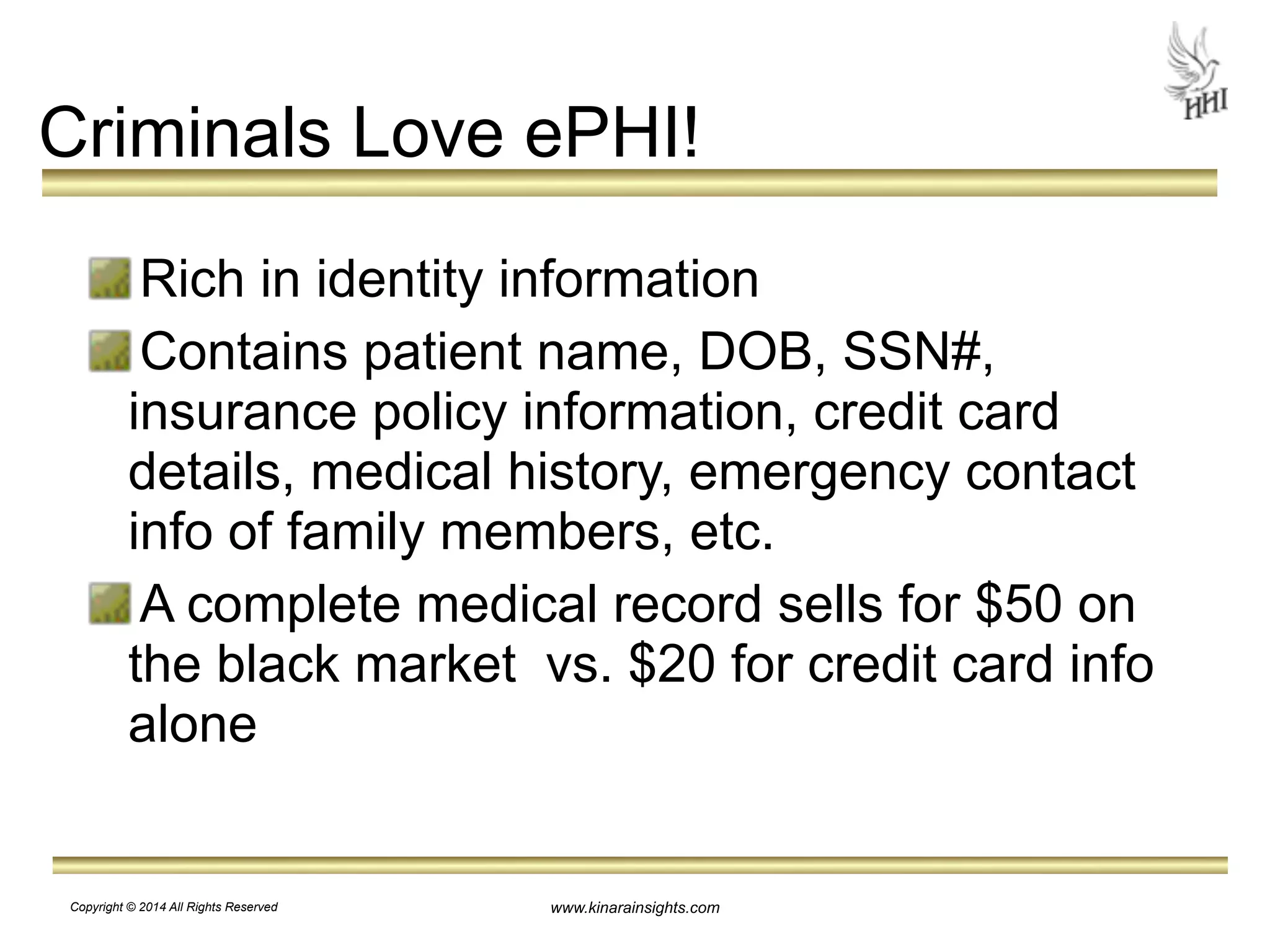
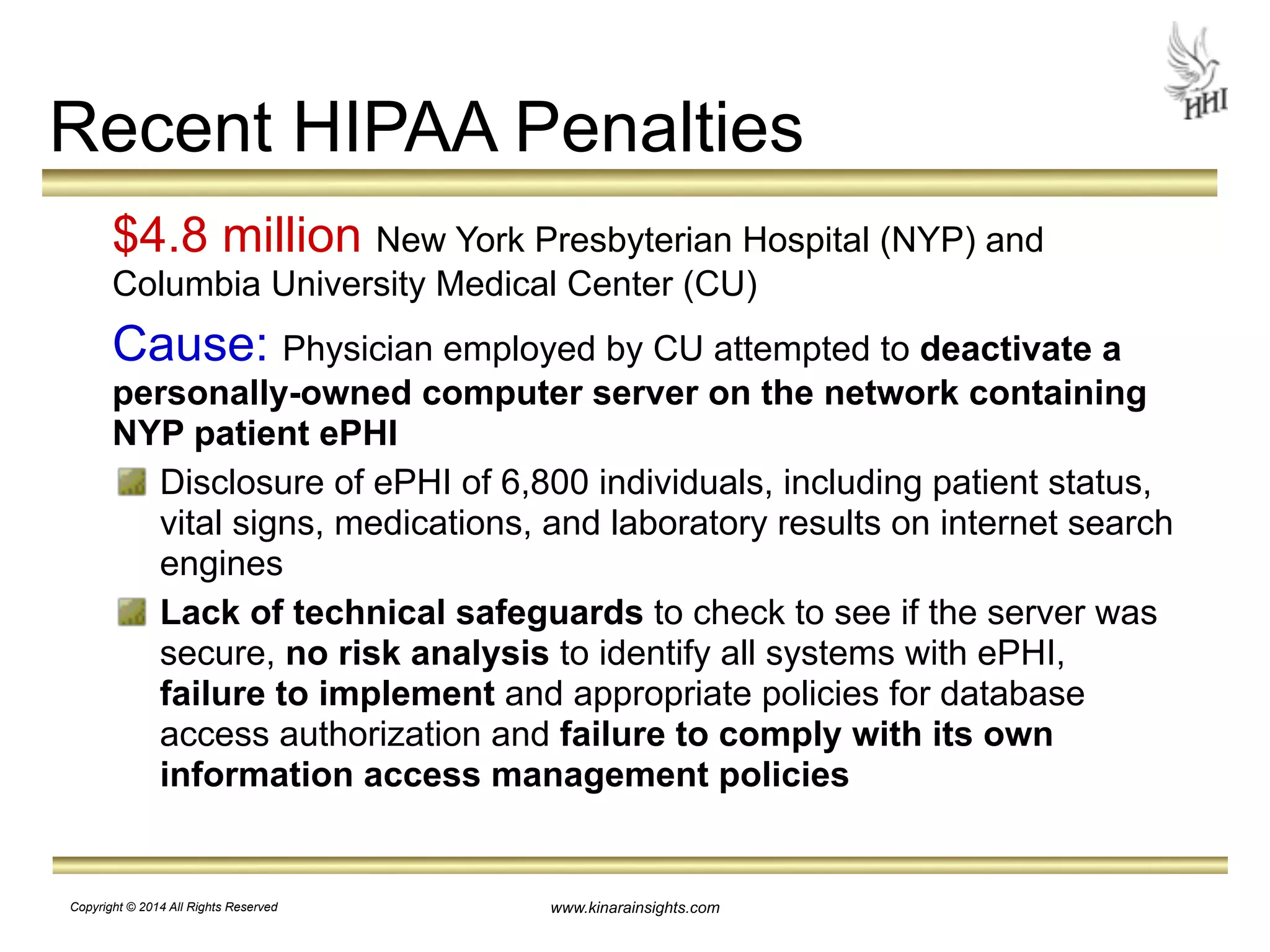
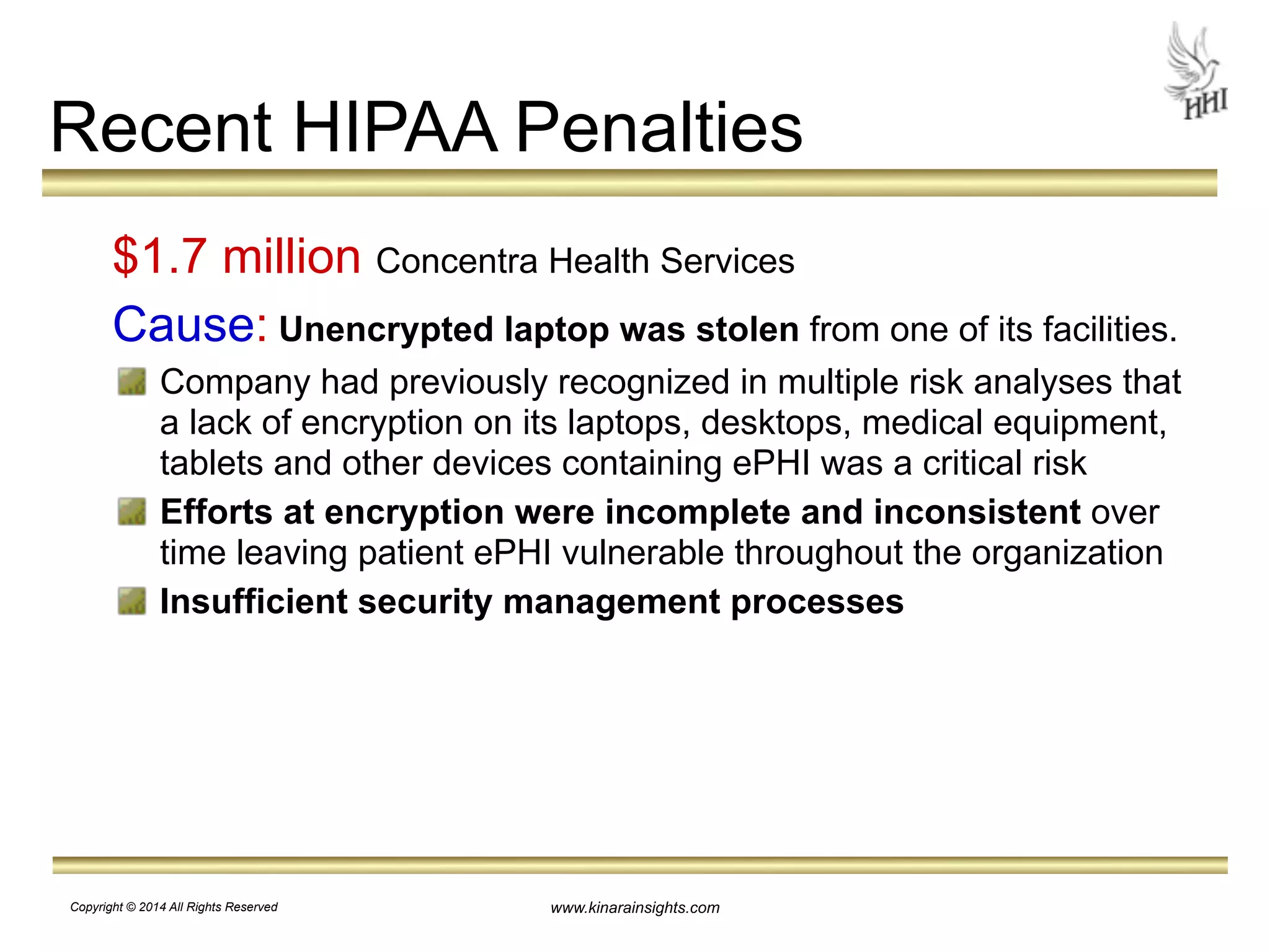
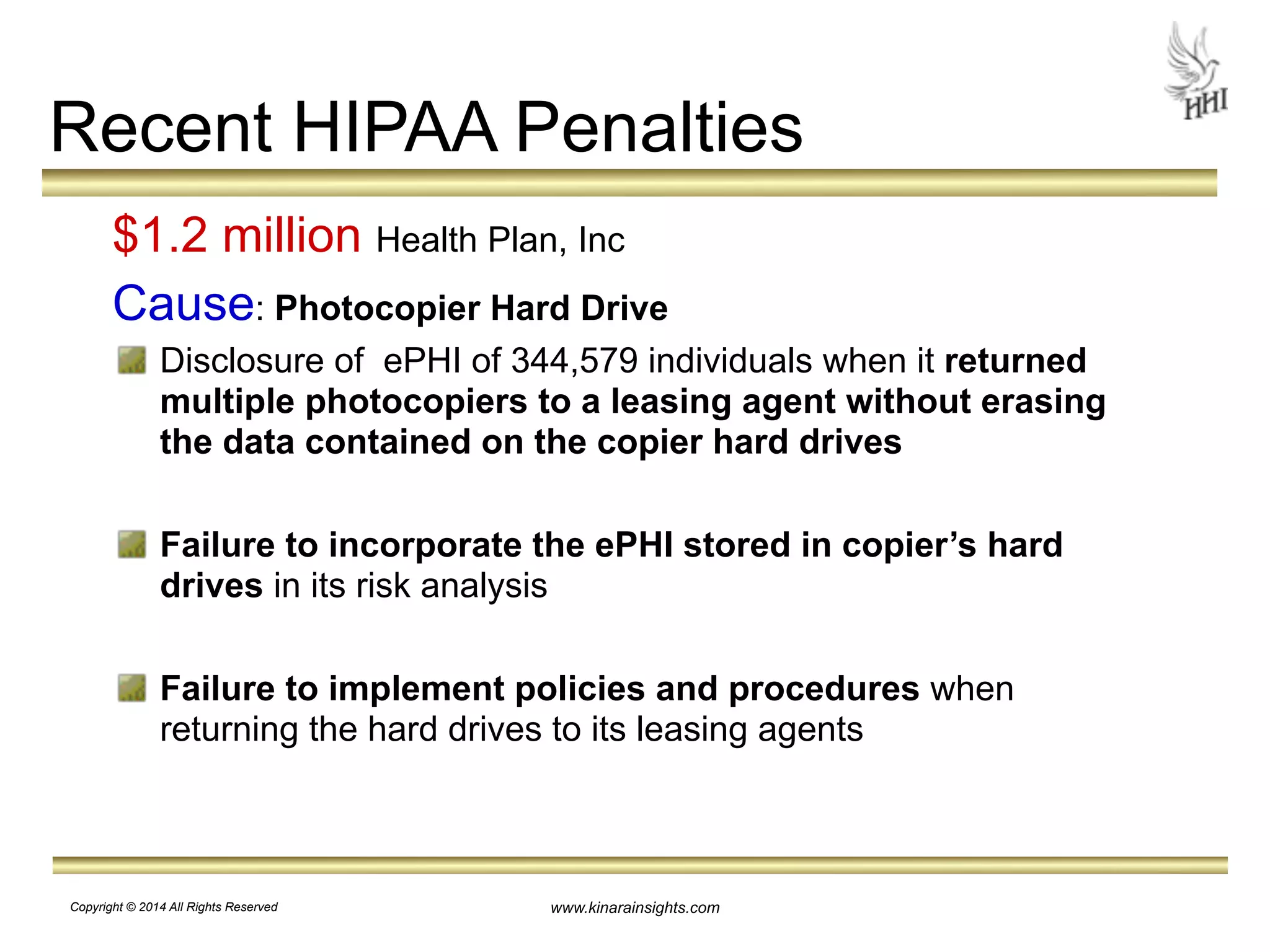
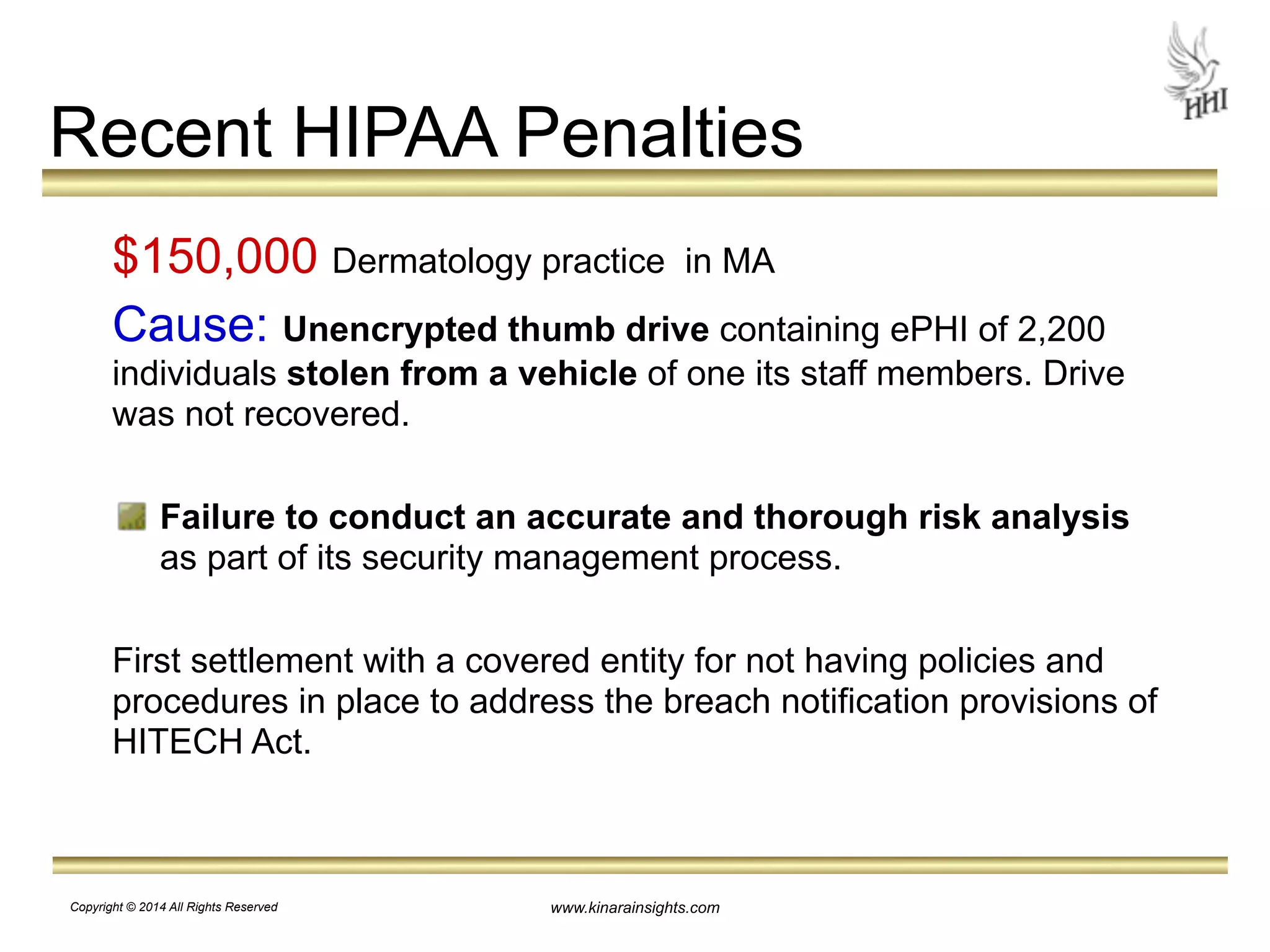
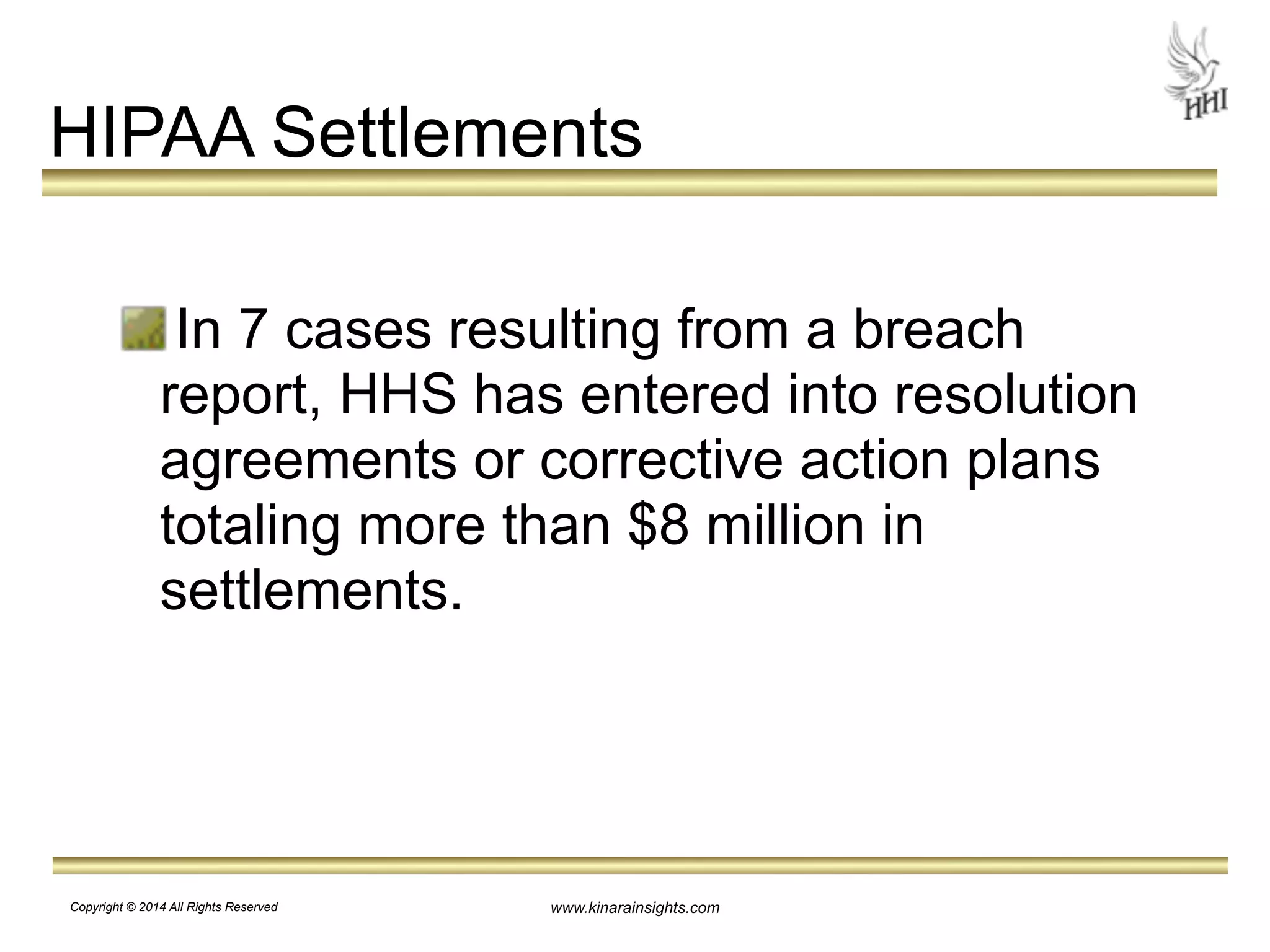
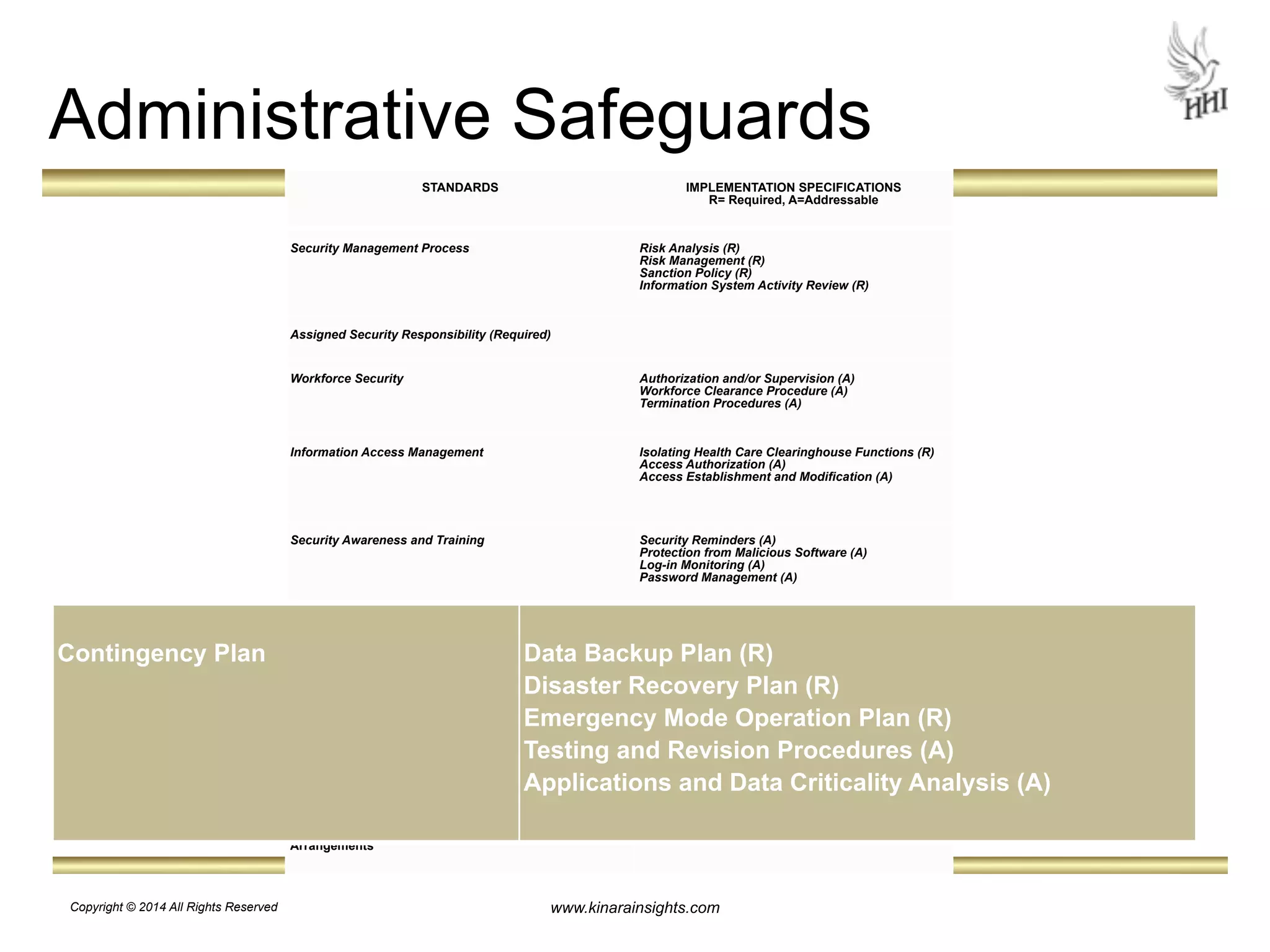
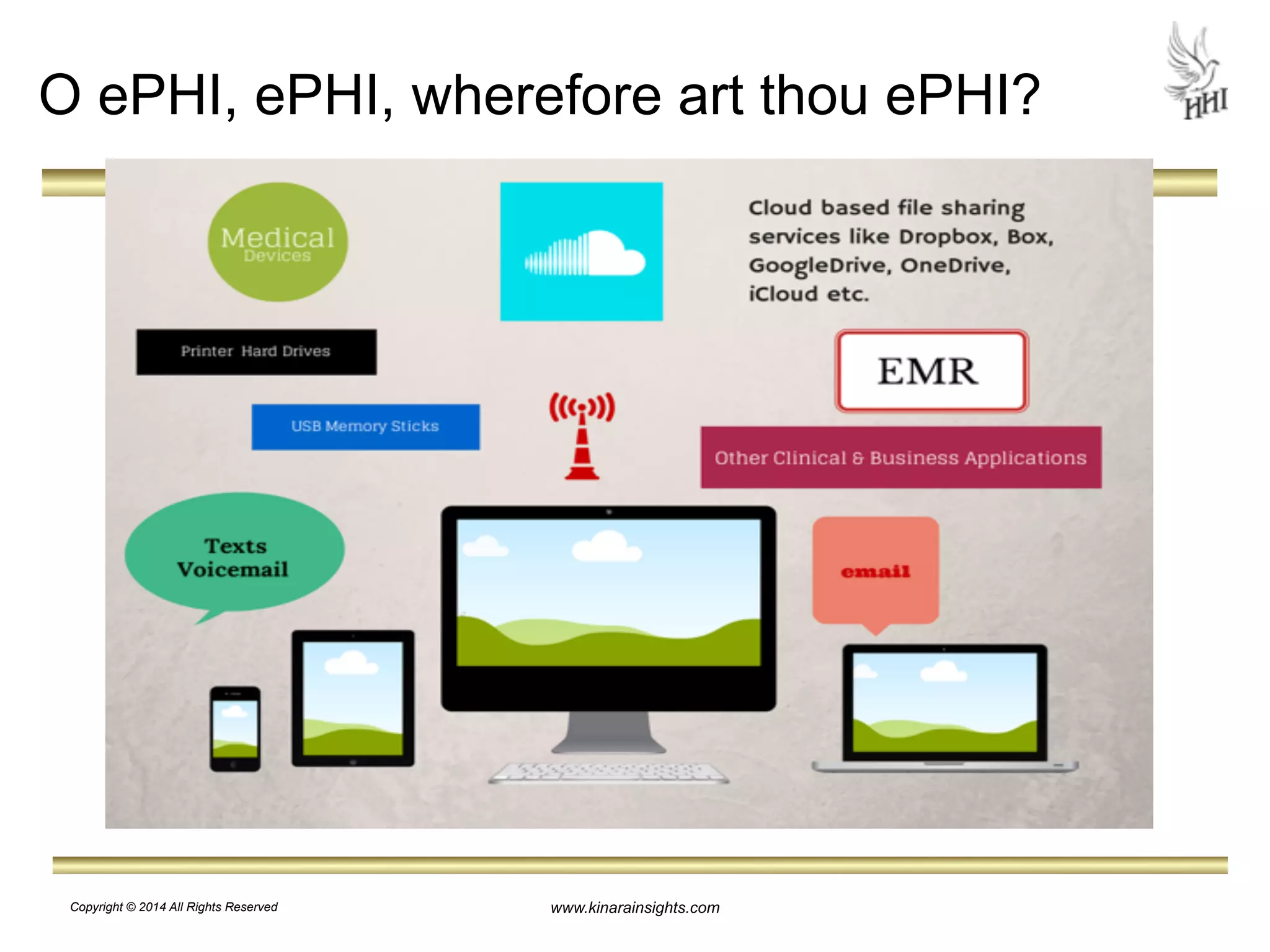
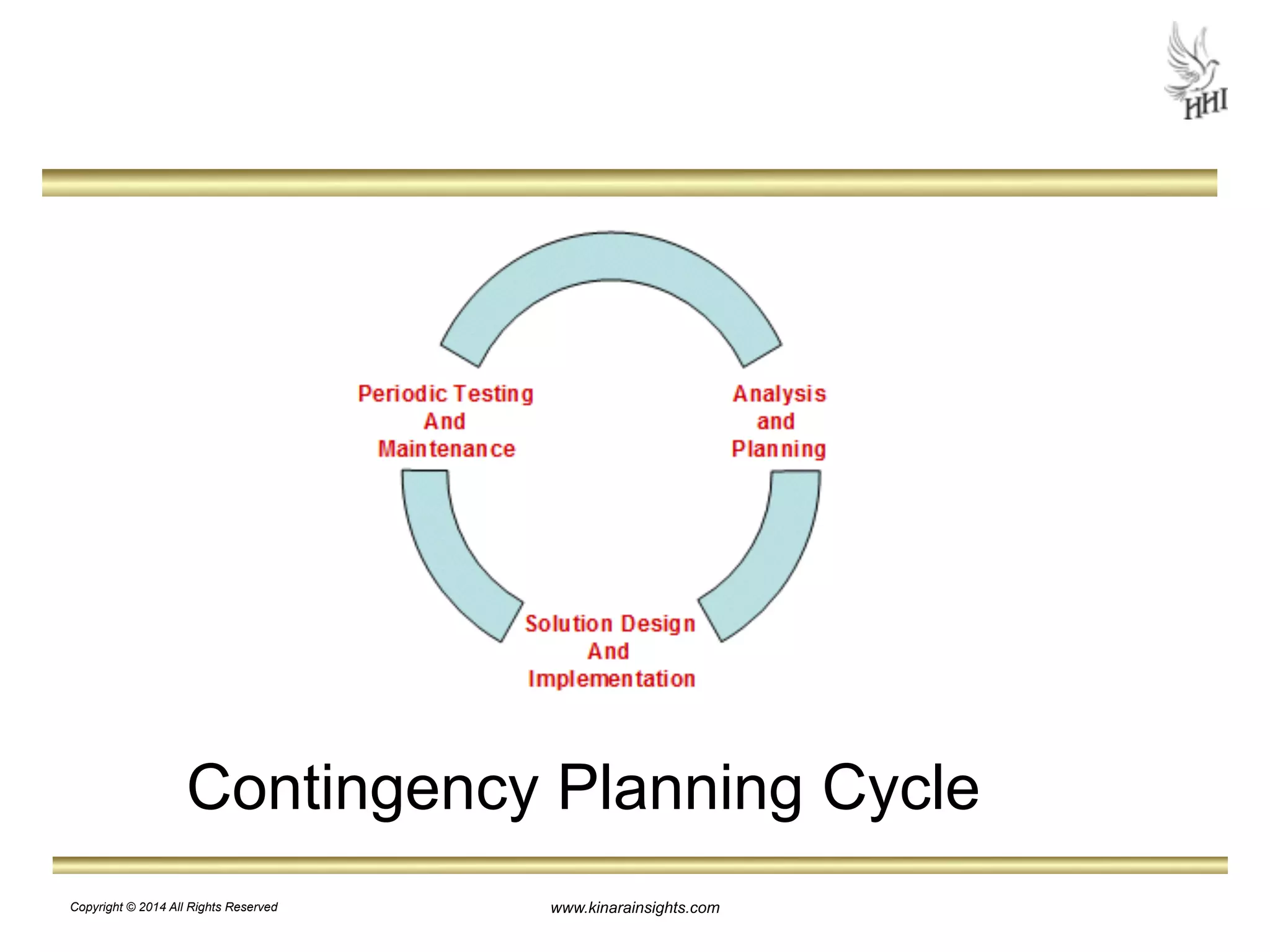
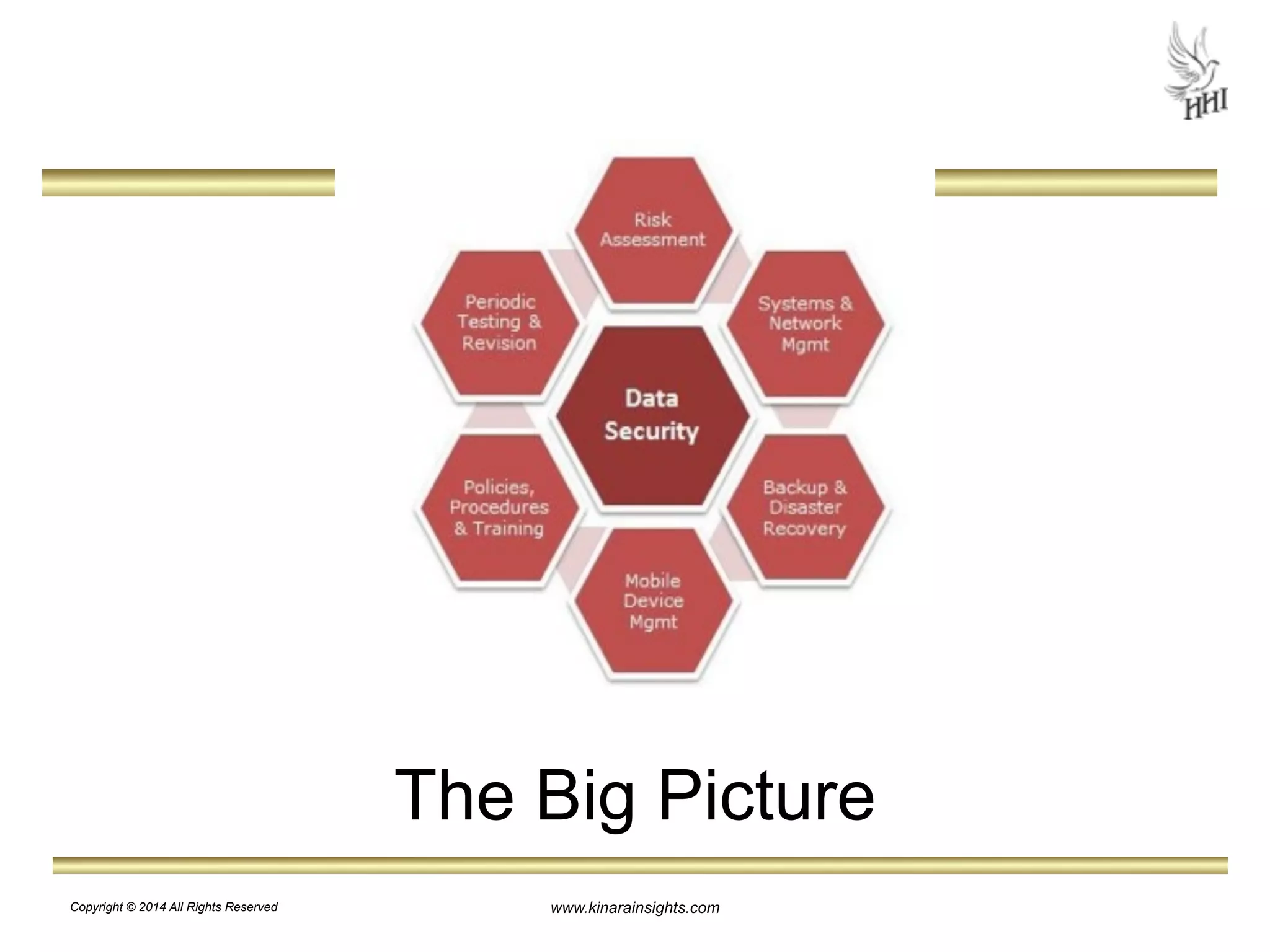
The document outlines essential steps for protecting electronic health information (ePHI) in nursing homes, emphasizing the importance of data security and HIPAA compliance. It details risks associated with medical identity theft and data breaches, highlighting strategies such as risk analysis, employee training, and encryption to safeguard patient information. The presentation is intended for educational purposes, aiming to empower organizations to implement effective data protection measures and navigate the complexities of HIPAA regulations.