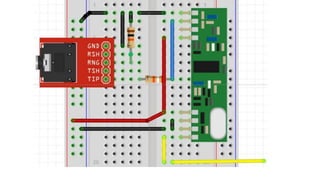
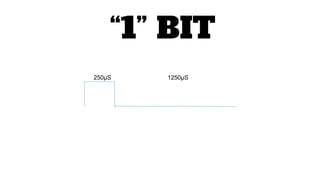
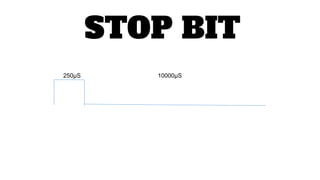
This document outlines a presentation about hacking your home by controlling devices remotely through wireless communication protocols. It discusses using an Arduino board connected to wireless transmitter and receiver modules to send and receive signals that control devices like lights and appliances. Code examples and diagrams show how to set up the hardware and software to create a basic home automation system that can toggle devices on and off remotely. Contact information is provided for the presenter for anyone interested in learning more.




































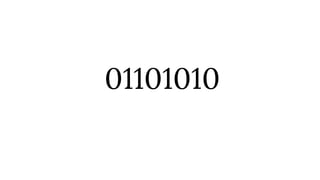

![3x - 32 BIT PACKAGE
[S][26 BIT ADD][G][C]](https://image.slidesharecdn.com/hackingyourhomehandout-150622184021-lva1-app6891/85/Hacking-your-home-48-320.jpg)