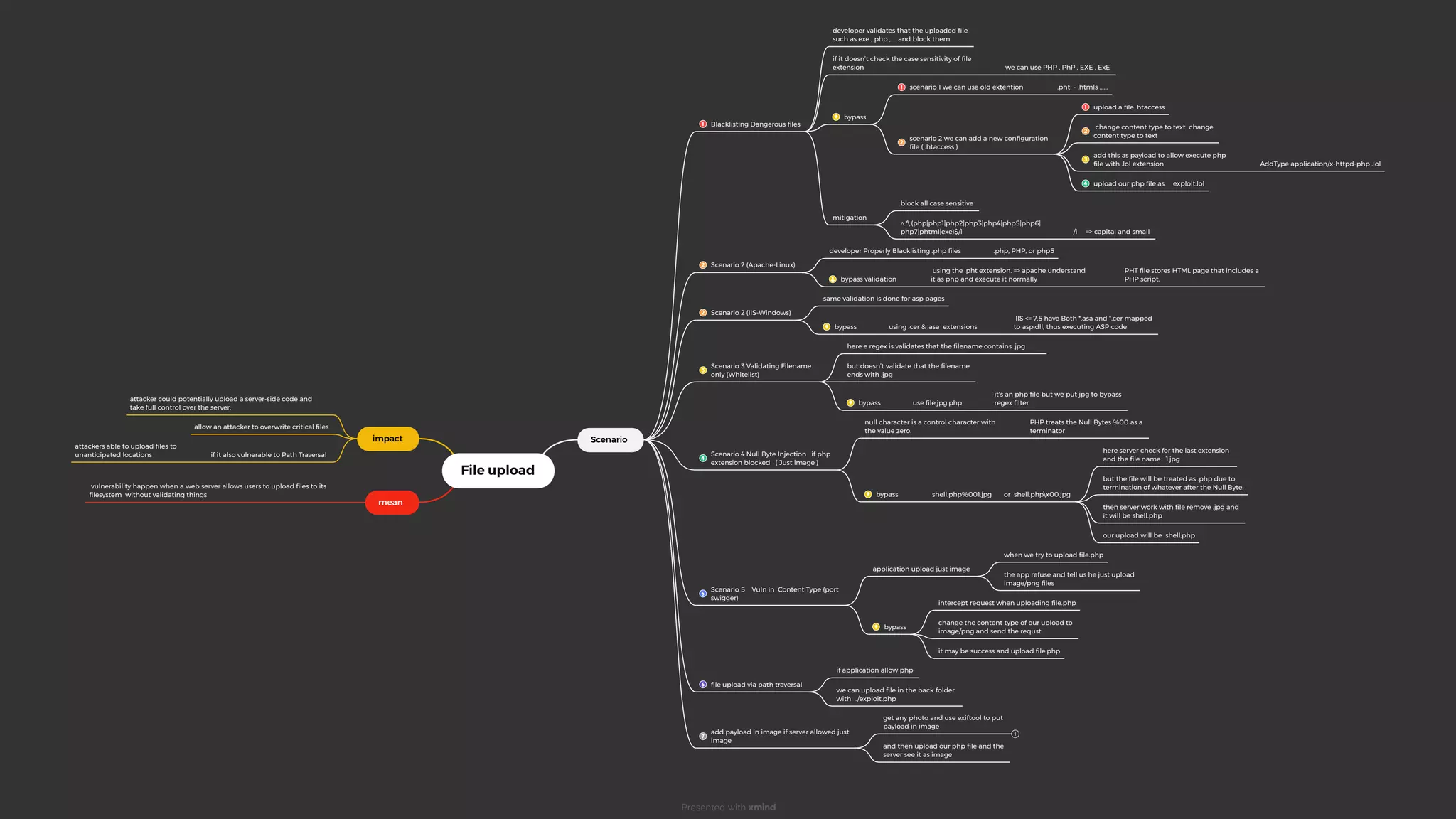
The document outlines various scenarios where file upload vulnerabilities can occur if developers do not properly validate and sanitize file extensions and paths. Attackers can bypass restrictions by exploiting things like case sensitivity of extensions, null byte injection, modifying content types, or using alternate file extensions like .pht that are treated as PHP by servers. This could allow attackers to upload malicious server-side code or overwrite critical files.