CHS-II Exam Notes: Risk Management and Intelligence
- 1. EXAM NOTES for the Certified in Homeland Security – Level II Developed as a courtesy by: Dave Sweigert, CEH, CHS-II, CISA, CISSP, HCISPP, PMP, SEC+ Key points: two circles (1) risk management (2) intelligence
- 3. The core of the CHS-II test is the DHS Risk Management Framework Core concepts: Risk Analysis – The development of a quantitative estimate of risk based on technical evaluation and mathematical techniques for combining estimates of incident likelihood and consequences. Risk Assessment – The process by which results of a risk analysis are used to make decisions, either through relative ranking of risks and risk reduction strategies or through comparison with risk targets. Risk Management – The ongoing process of planning, organizing, leading and controlling people, assets, and activities to minimize the potential consequences and/or probability of risks identified and appraised through risk assessment. DHS Risk managementCycle
- 4. 5 DHS Risk Management principles: Unity of Effort – risk management efforts should be coordinated and integrated among the organization as a whole. Transparency – open and direct communication is essential to effective security risk management. Adaptability – risk management strategies and processes should be designed to be flexible and responsive to change. Practicality – homeland security risk management cannot eliminate all uncertainty nor identify all risks. Customization – risk management efforts should be structured and tailored to fit the needs and values of the organization. What are the parts of the Intelligence process? Planning and direction, Collection, Processing and exploitation, Analysis and production, Dissemination and integration Scientific & Technical Intelligence? Encompasses foreign developments in S&T w/warfare potential Estimative Intelligence? Forecasts the unknown based on an analysis of known facts using techniques such as pattern analysis, inference, and statistical probability. Current intelligence? Provides updated support for ongoing ops across the range of military operations (ROMO) Warning intelligence? Very time-sensitive. Forewarns of adversary actions or intentions. Research Intelligence? Basic intelligence or Intelligence for operational support
- 5. The NIPP
- 6. DHS TVC Analysis Natural Hazards Analysis There is a solid foundation of data, models, and scholarship to underpin the Federal Emergency Management Agency’s (FEMA’s) risk analyses for earthquakes, flooding, and hurricanes which uses the Risk = T × V × C model. This paradigm has been applied to natural hazards, especially flooding, more than a century. Perhaps the earliest use of the Risk = T × V × C model—often referred to as “probabilistic risk assessment” in other fields—dates to its use in forecasting flood risks on the Thames in the nineteenth century.
- 9. Terror attacks 1978-1995 - Three people die and 23 others are wounded after a string of mail bombings carried out by Ted Kaczynski. "The Unabomber," as he is also known, is serving eight life sentences for murder. He was not charged with terrorism, but the string of bombings is considered to be a terror case. February 26, 1993 - A bomb explodes on the second subterranean level of Vista Hotel's public parking garage, below the 2 World Trade Center building. Six people are killed, and more than 1,000 people are treated for injuries. Six suspects are convicted of participating in the bombing. The seventh suspect, Abdul Rahman Yasin, is still at large. April 19, 1995 - A bomb rips through the Alfred P. Murrah Federal Building in Oklahoma City, Oklahoma, killing 168 people and injuring almost 700. Timothy McVeigh is convicted on federal murder charges and executed in 2001. July 27, 1996 - A bomb explodes in Centennial Olympic Park in Atlanta during the middle of a concert during the Summer Olympics. One person is killed, another dies from a heart attack, and 111 others are injured. Bombing suspect Eric Robert Rudolph is arrested in North Carolina in 2003, after being indicted in 2000 for the Atlanta bombing and for other bombings, including one at an abortion clinic where one person died. Rudolph is serving four consecutive sentences of life in prison plus 120 years for the attacks. September 11, 2001 - Nineteen al Qaeda members hijack four US passenger airliners. Two are flown into the Twin Towers in New York, one crashes into the Pentagon and another crashes into the Pennsylvania countryside after passengers attempt to wrest control of the aircraft to prevent an attack on the US Capitol. At the World Trade Center site 2,753 people are killed; 184 at the Pentagon; and 40 in Shanksville, Pennsylvania. A total of 2,977 people are killed. Richard Colvin Reid (born 12 August 1973), also known as the Shoe Bomber, is a British man arrested as the prime suspect who attempted to detonate explosives packed into the shoes he was wearing, while on American Airlines Flight 63 from Paris to Miami on December 22, 2001.
- 10. The D.C. or Beltway sniper attacks were a series of coordinated shootings that took place over three weeks in October 2002 in Maryland, Virginia, and Washington, D.C. Ten people were killed and three other victims were critically injured in several locations throughout the Washington, D.C., metropolitan area and along Interstate 95 in Virginia. November 5, 2009 - Major Nidal Hassan goes on a shooting rampage at a military processing center at Fort Hood, Texas, killing 13 and wounding 32. Hassan is convicted of 13 counts of murder and 32 counts of attempted murder. He is given the death penalty. Hassan is not charged with terrorism, but the rampage is considered by many to be a terror incident. On May 1, 2010, an attempted terrorist attack occurred in Times Square in Manhattan, New York. Two street vendors alerted New York City security personnel after they spotted smoke coming from a vehicle, and a car bomb was discovered.[1][2] The bomb had been ignited, but failed to explode, and was disarmed before it caused any casualties.[1][3][4] Two days later, federal agents arrested Faisal Shahzad, a 30-year-old Pakistan-born resident of Bridgeport, Connecticut, who had become a U.S. citizen in April 2009. April 15, 2013 - Twin bomb blasts explode near the finish line of the Boston Marathon, killing three and wounding at least 264. Suspect Dzhokhar Tsarnaev is charged by the US government with one count of using and conspiring to use a weapon of mass destruction resulting in death and one count of malicious destruction of property by means of an explosive device resulting in death. He is given the death penalty on June 25, 2015. July 16, 2015 - Mohammad Abdulazeez opens fire on a military recruiting center and a Navy reserve facility in Chattanooga, Tennessee, killing four US Marines and a Navy sailor. FBI Director James Comey later says Abdulazeez's actions were "motivated by foreign terrorist organization propaganda," adding that it's difficult to determine which terrorist group may have inspired him. December 2, 2015 - Married couple Syed Rizwan Farook and Tashfeen Malik open fire on a holiday party taking place at Inland Regional Center in San Bernardino, California, killing 14 people. Investigators believe the couple was self-radicalized. http://www.cnn.com/2013/04/18/us/u-s-terrorist-attacks-fast-facts/
- 11. The Six Steps of the Intelligence Community
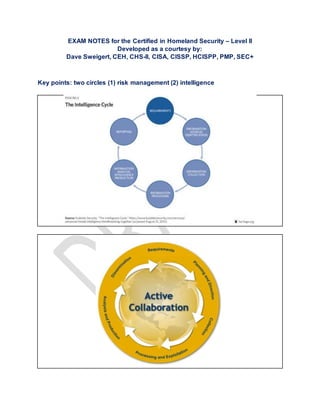
- 12. The Intelligence Cycle is the process of developing raw information into finished intelligence for policymakers to use in decision-making and action. There are five steps which constitute the Intelligence Cycle. 1. Identify Requirements Requirements refer to the information that is needed. 2. Planning and Direction This is management of the entire effort, from identifying the need for data to delivering an intelligence product to a consumer. It is the beginning and the end of the cycle--the beginning because it involves drawing up specific collection requirements and the end because finished intelligence, which supports policy decisions, generates new requirements. 3. Collection ...is the gathering of the raw information needed to produce finished intelligence. There are many sources of information including open sources such as foreign broadcasts, newspapers, periodicals, and books. Open source reporting is integral to CIA's analytical capabilities. There are also secret sources of information. CIA's operations officers collect such information from agents abroad and from defectors who provide information obtainable in no other way. 4. Processing ...involves converting the vast amount of information collected to a form usable by analysts through decryption, language translations, and data reduction. 5. All Source Analysis and Production ...is the conversion of basic information into finished intelligence. It includes integrating, evaluating, and analyzing all available data--which is often fragmentary and even contradictory--and preparing intelligence products. Analysts, who are subject-matter specialists, consider the information's reliability, validity, and relevance. They integrate data into a coherent whole, put the evaluated information in context, and produce finished intelligence that includes assessments of events and judgments about the implications of the information for the United States. 6. Dissemination The last step, which logically feeds into the first, is the distribution of the finished intelligence to the consumers, the same policymakers whose needs initiated the intelligence requirements. Finished intelligence is hand-carried daily to the President and key national security advisers. The policymakers, the recipients of finished intelligence, then make decisions based on the information, and these decisions may lead to the levying of more requirements, thus triggering the Intelligence Cycle
- 14. Quadrennial Homeland Security Review (QHSR) The purpose of the first-ever Quadrennial Homeland Security Review (QHSR) is to outline the strategic framework to guide the activities of participants in homeland security toward a common end. A safe and secure homeland must mean more than preventing terrorist attacks from being carried out. It must also ensure that the liberties of all Americans are assured, privacy is protected, and the means by which we interchange with the world—through travel, lawful immigration, trade, commerce, and exchange—are secured. https://www.dhs.gov/quadrennial-homeland-security-review# 3 KEY CONCEPTS 5 DHS MISSION AREAS
- 16. 2014 Quadrennial Homeland Security Review THE FIVE HOMELAND SECURITY MISSIONS The first quadrennial review established the five enduring missions of homeland security. This review reaffirms the five-mission structure and updates the missions (detailed in the Mission Framework In Depth section). The updated missions are: Prevent Terrorism and Enhance Security; Secure and Manage Our Borders; Enforce and Administer Our Immigration Laws; Safeguard and Secure Cyberspace; and Strengthen National Preparedness and Resilience. https://www.dhs.gov/sites/default/files/publications/2014-qhsr-final-508.pdf
- 18. PRESIDENTIAL DIRECTIVES PPD 8 National Preparedness Presidential Policy Directive / PPD-8 is aimed at strengthening the security and resilience of the United States through systematic preparation for the threats that pose the greatest risk to the security of the nation, including acts of terrorism, cyber-attacks, pandemics, and catastrophic natural disasters. States the goal: “A secure and resilient nation with the capabilities required across the whole community to prevent, protect against, mitigate, respond to and recover from the threats and hazards that pose the greatest risk.” Defines a series of national preparedness elements (called core capabilities) that we need to achieve the goal. Emphasizes the need for the whole community to work together in a variety of ways and make the best use of resources.
- 20. The National Preparedness Goal defines what it means for the whole community to be prepared for all types of disasters and emergencies. The goal itself is succinct: “A secure and resilient nation with the capabilities required across the whole community to prevent, protect against, mitigate, respond to, and recover from the threats and hazards that pose the greatest risk.”
- 21. The National Preparedness Goal organizes the core capabilities into the five mission areas: Prevention. Prevent, avoid or stop an imminent, threatened or actual act of terrorism. Protection. Protect our citizens, residents, visitors and assets against the greatest threats and hazards in a manner that allows our interests, aspirations and way of life to thrive. Mitigation. Reduce the loss of life and property by lessening the impact of future disasters. Response. Respond quickly to save lives, protect property and the environment, and meet basic human needs in the aftermath of a catastrophic incident. Recovery. Recover through a focus on the timely restoration, strengthening and revitalization of infrastructure, housing and a sustainable economy, as well as the health, social, cultural, historic and environmental fabric of communities affected by a catastrophic incident.
- 22. PPD 21 Critical Infrastructure Security and Resilience The Presidential Policy Directive (PPD) on Critical Infrastructure Security and Resilience advances a national unity of effort to strengthen and maintain secure, functioning, and resilient critical infrastructure.
- 23. MISSION OF DHS PER Quadrennial Homeland Security Review (QHSR) Prevent terrorism and enhance security Secure and manage our borders Enforce and administer our immigration laws Safeguard and secure cyberspace Strengthen national preparedness and resilience Key points: DHS combines 22 various federal agencies Established by the Homeland Security Act (Public Law 107-296) DHS officially operational on March 1, 2003
- 24. VNSA Violent non-state actors (VNSA), also known as armed non-state actors, are non- state actors, i.e. "individuals or organizations that have economic, political or social power and are able to influence at a national and sometimes international level but do not belong to or ally themselves to any particular country or state,"[1] who employ violence in pursuit of their objectives. The term has been used in several papers published by the U.S. military.[2][3][4][5] There are many reasons why violent non-state actors develop. https://en.wikipedia.org/wiki/Violent_non-state_actor Warlords Militias Insurgencies Terrorist organizations Criminal organizations and gangs A warlord is a leader able to exercise military, economic, and political control over a subnational territory within a sovereign state due to his ability to mobilize loyal armed forces. These armed forces, usually considered militias, are loyal to the warlord rather than to the state regime. Warlords have existed throughout much of history, albeit in a variety of different capacities within the political, economic, and social structure of states or ungoverned territories. A militia /mᵻˈlɪʃə/[1] is generally an army or some other type of fighting unit that is composed of non-professional fighters, citizens of a nation or subjects of a state or government who can be called upon to enter a combat situation, as opposed to a professional force of regular, full-time military personnel, or historically, members of a warrior nobility class (e.g., knights or samurai). Unable to hold their own against properly trained and equipped professional forces, it is common for militias to engage in guerrilla warfare or defense instead of being used in open attacks and offensive actions. A paramilitary is a semi-militarized force whose organizational structure, tactics, training, subculture, and (often) function are similar to those of a professional military, but which is not included as part of a state's formal armed forces.[1] Under the law of war, a state may incorporate a paramilitary organization or armed agency (such as a national police, a private volunteer militia) into its combatant armed forces. The other parties to a conflict have to be notified thereof An insurgency is a rebellion against authority (for example, an authority recognized as such by the United Nations) when those taking part in the rebellion are not recognized as belligerents.[1] An insurgency can be fought via counter-
- 25. insurgency warfare, and may also be opposed by measures to protect the population, and by political and economic actions of various kinds aimed at undermining the insurgents' claims against the incumbent regime.[2] The nature of insurgencies is an ambiguous concept. This is a list of designated terrorist groups by national governments, former governments, and inter-governmental organizations, where the proscription has a significant effect on the group's activities. Many organizations that are accused of being a terrorist organization deny using terrorism as a military tactic to achieve their goals, and there is no international consensus on the legal definition of terrorism. Organized crime is a category of transnational, national, or local groupings of highly centralized enterprises run by criminals who intend to engage in illegal activity, most commonly for money and profit. Some criminal organizations, such as terrorist groups, are politically motivated. Sometimes criminal organizations force people to do business with them, such as when a gang extorts money from shopkeepers for so-called "protection".[1] Gangs may become disciplined enough to be considered organized. A criminal organization or gang can also be referred to as a mafia, mob, or crime syndicate; the network, subculture and community of criminals may be referred to as the underworld.
- 26. DEFINITIONS C3: Cyber Crimes Center CERT: Community Emergency Response Team EX: Explosive DNDO: Domestic Nuclear Detection Office NCCIC: National Cybersecurity and Communications Integration Center NIMS: National Incident Management System NIPP: National Infrastructure Protection Plan NOC: National Operations Center NTAS: National Terrorism Advisory System OEC: Office of Emergency Communications VNSA: Violent Non-State Actors
- 27. REVIEW
