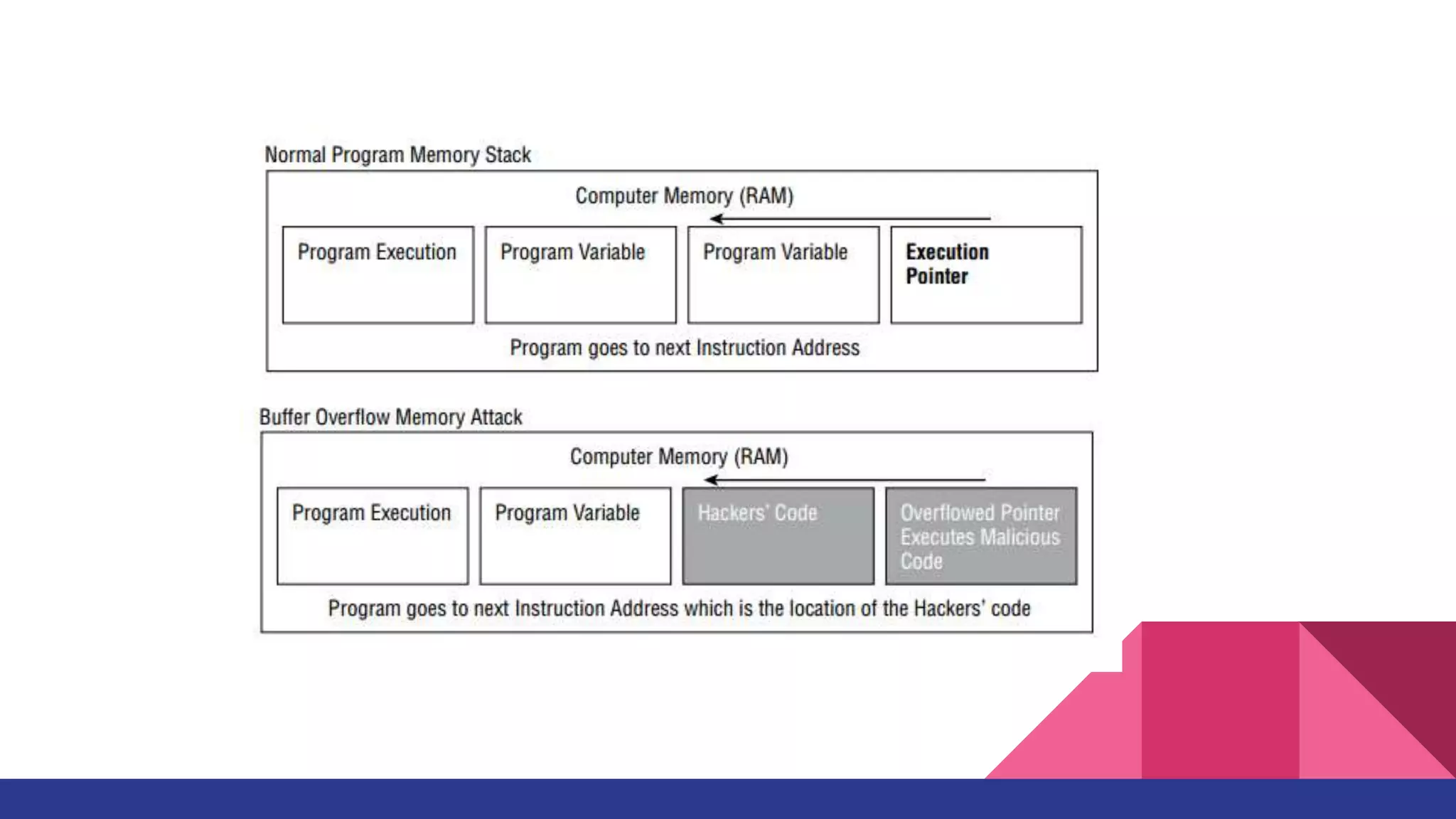
SQL injection and buffer overflows are two common application attacks discussed in the chapter. SQL injection occurs when user input is not sanitized before being used to construct SQL queries, allowing attackers to alter queries or access unauthorized data. Buffer overflows happen when more data is written to a buffer than it can hold, overwriting adjacent memory and potentially allowing execution of arbitrary code. The document outlines how these attacks work, their goals, and countermeasures like input validation, limiting error messages, and using programming languages less vulnerable to overflows.