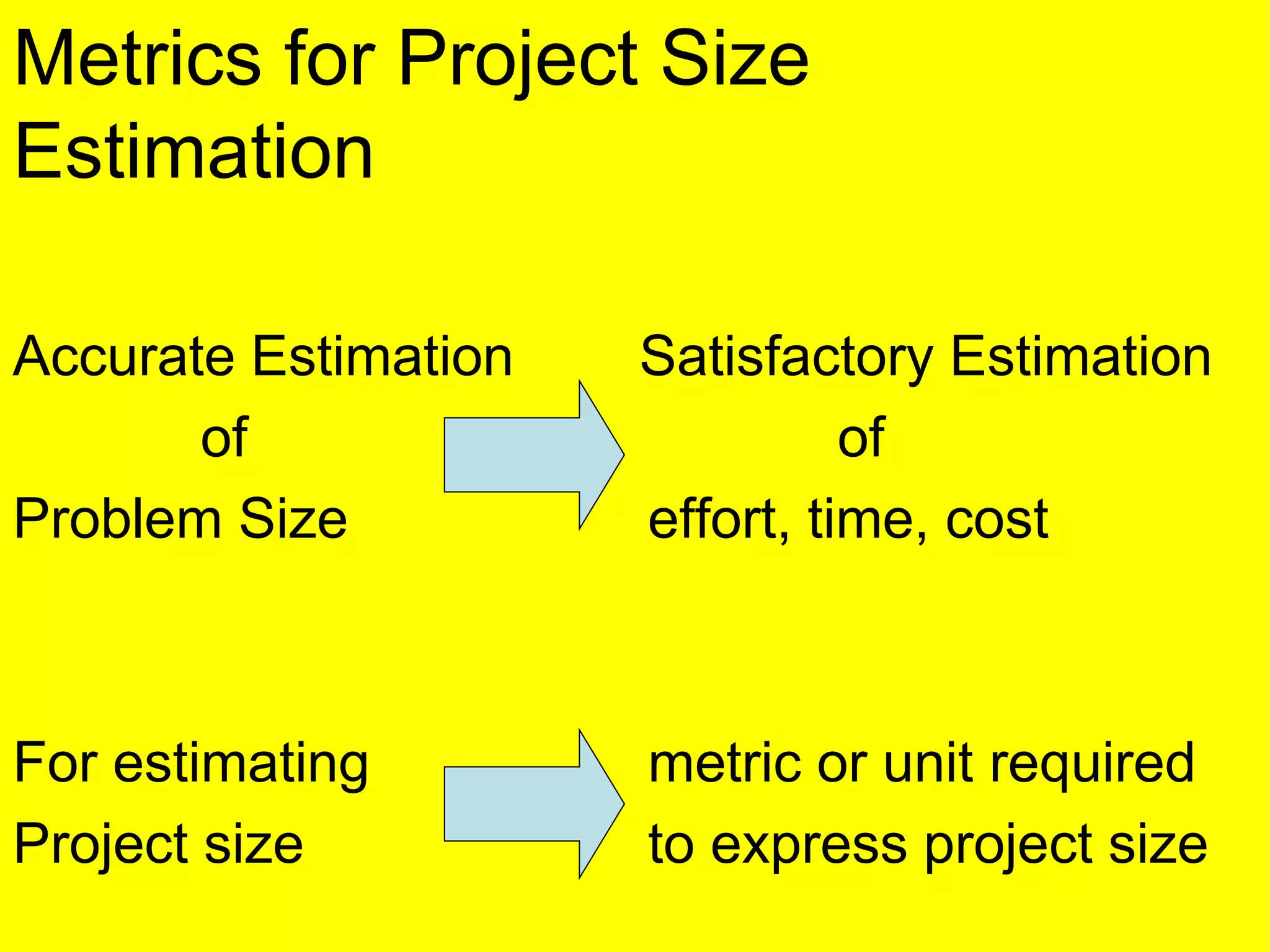
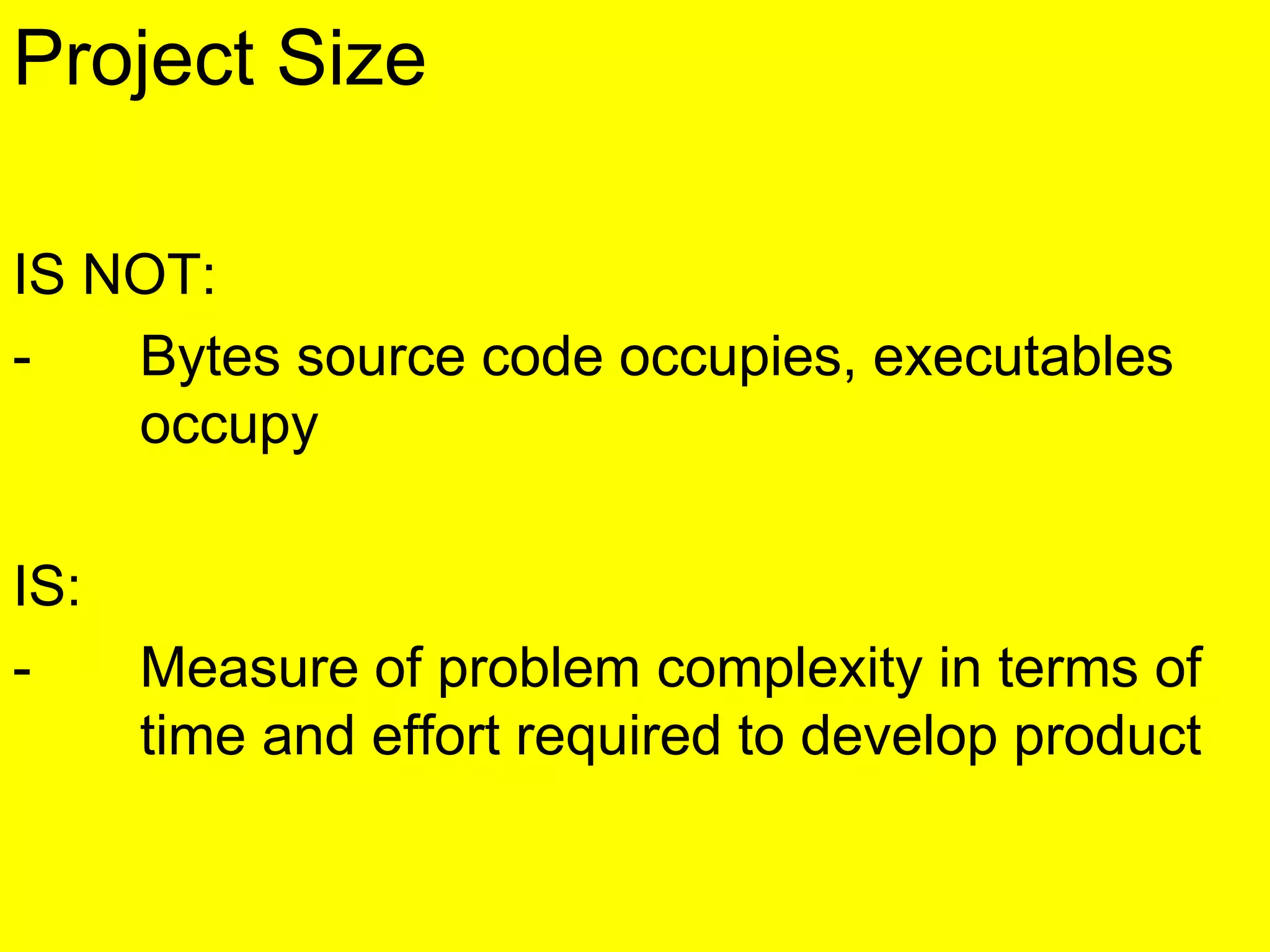
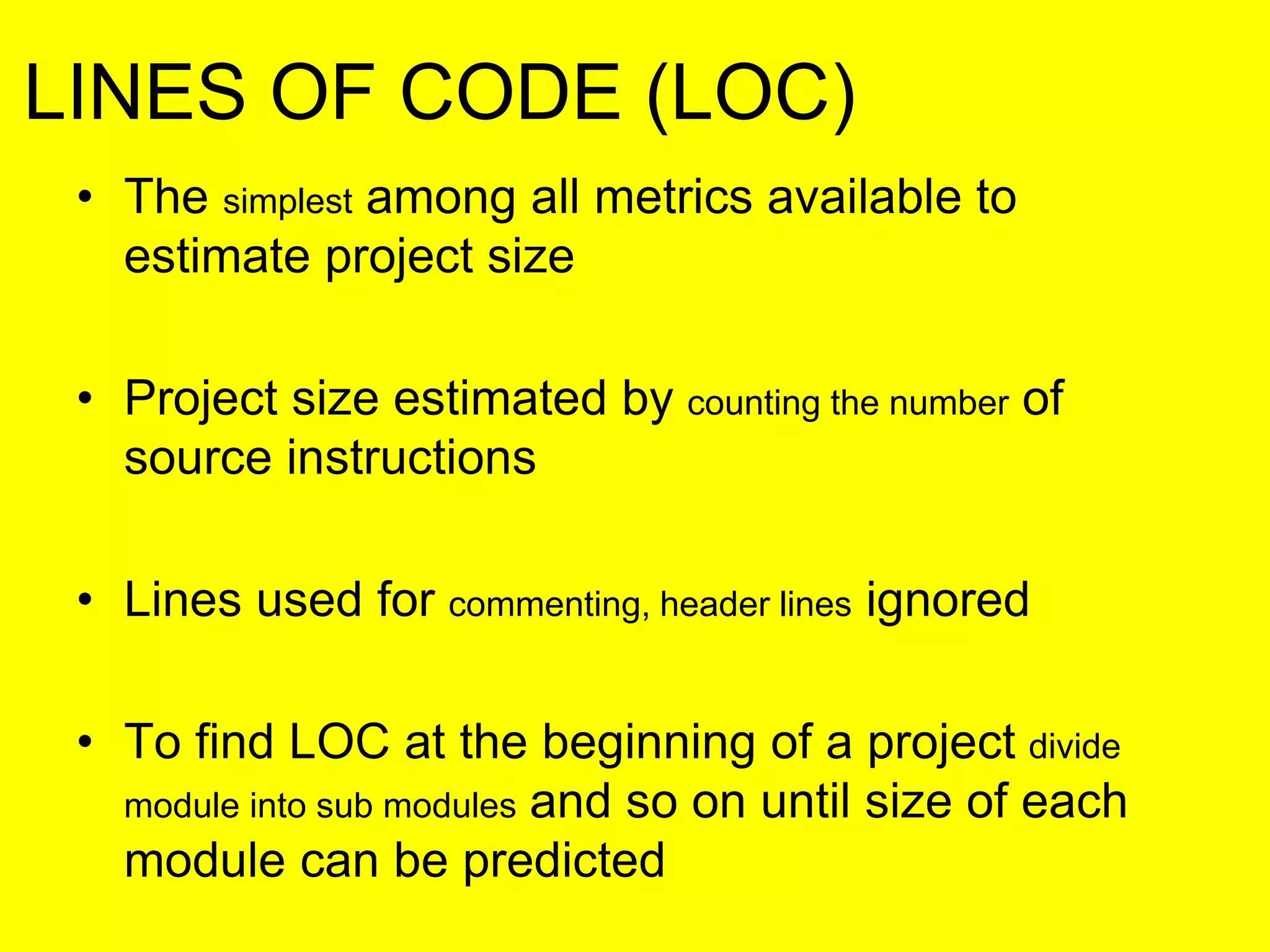
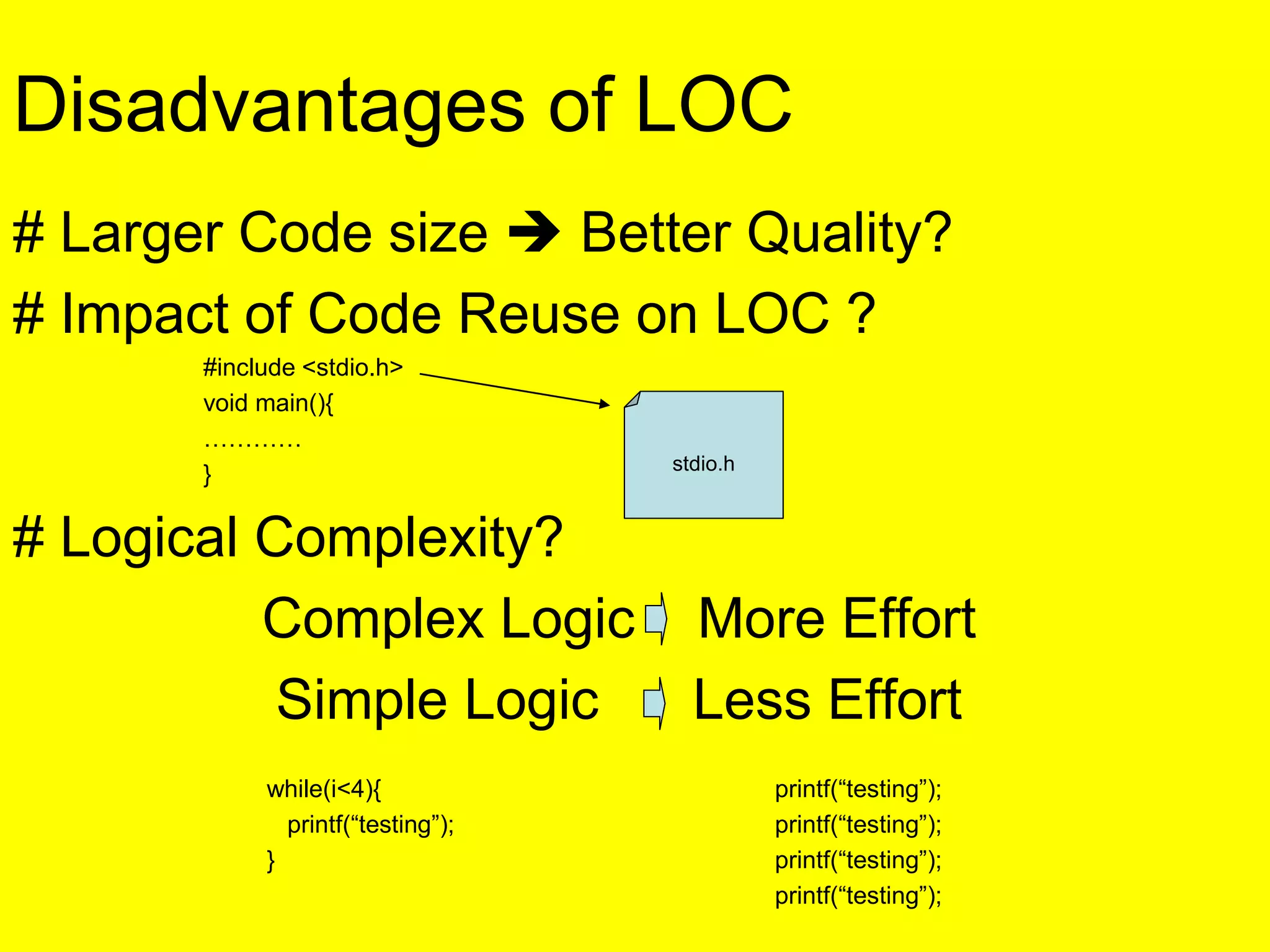
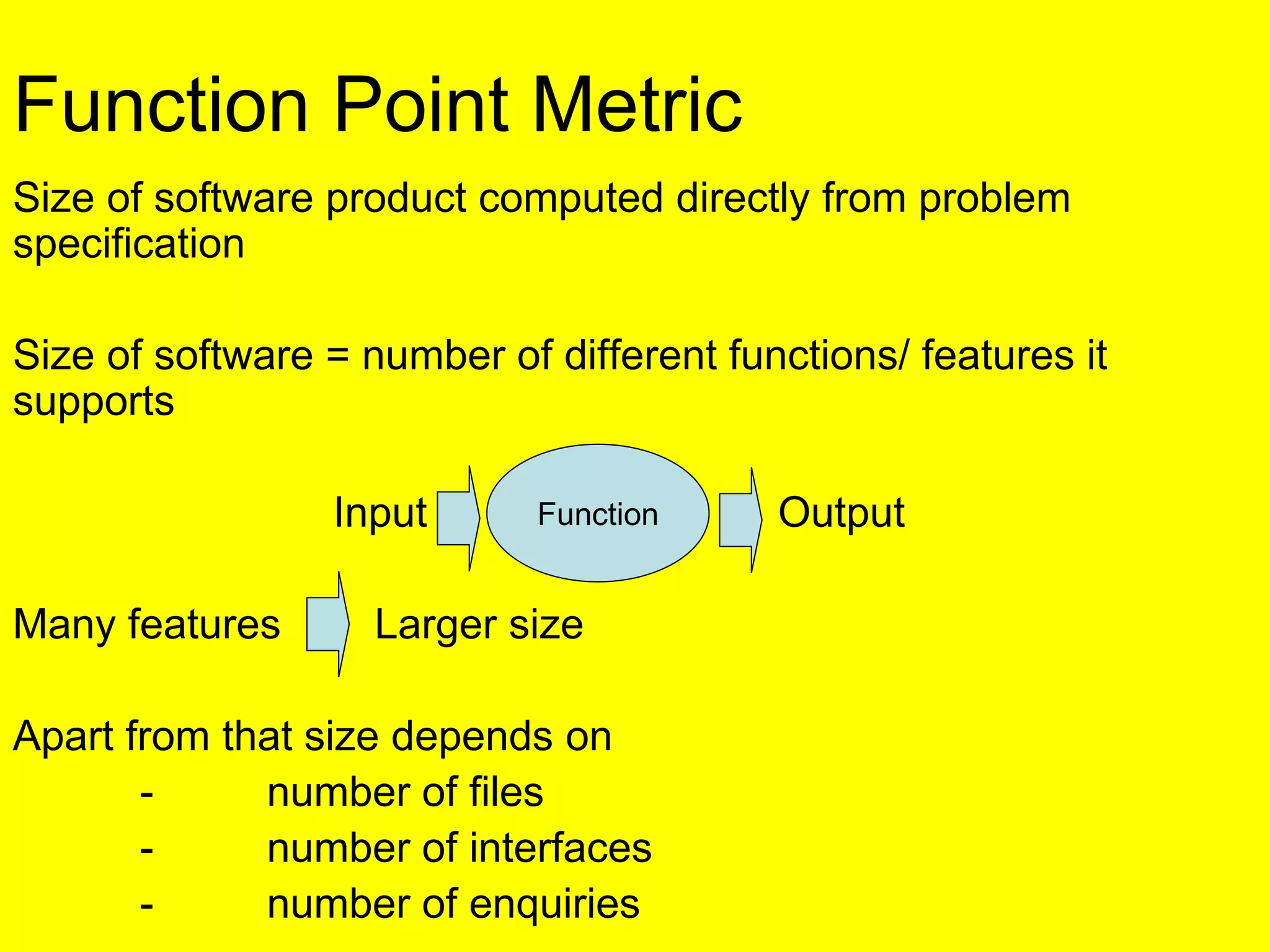
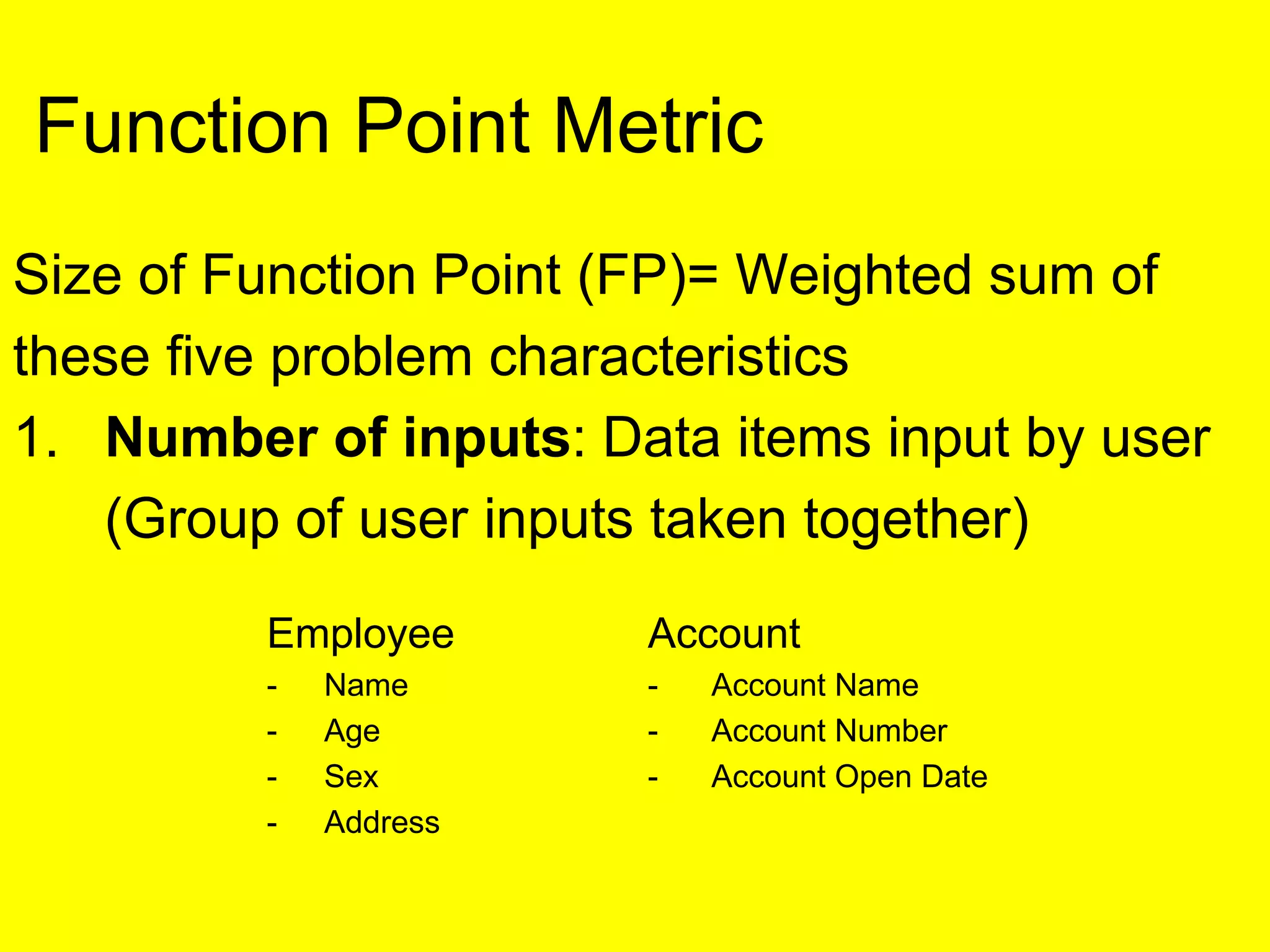
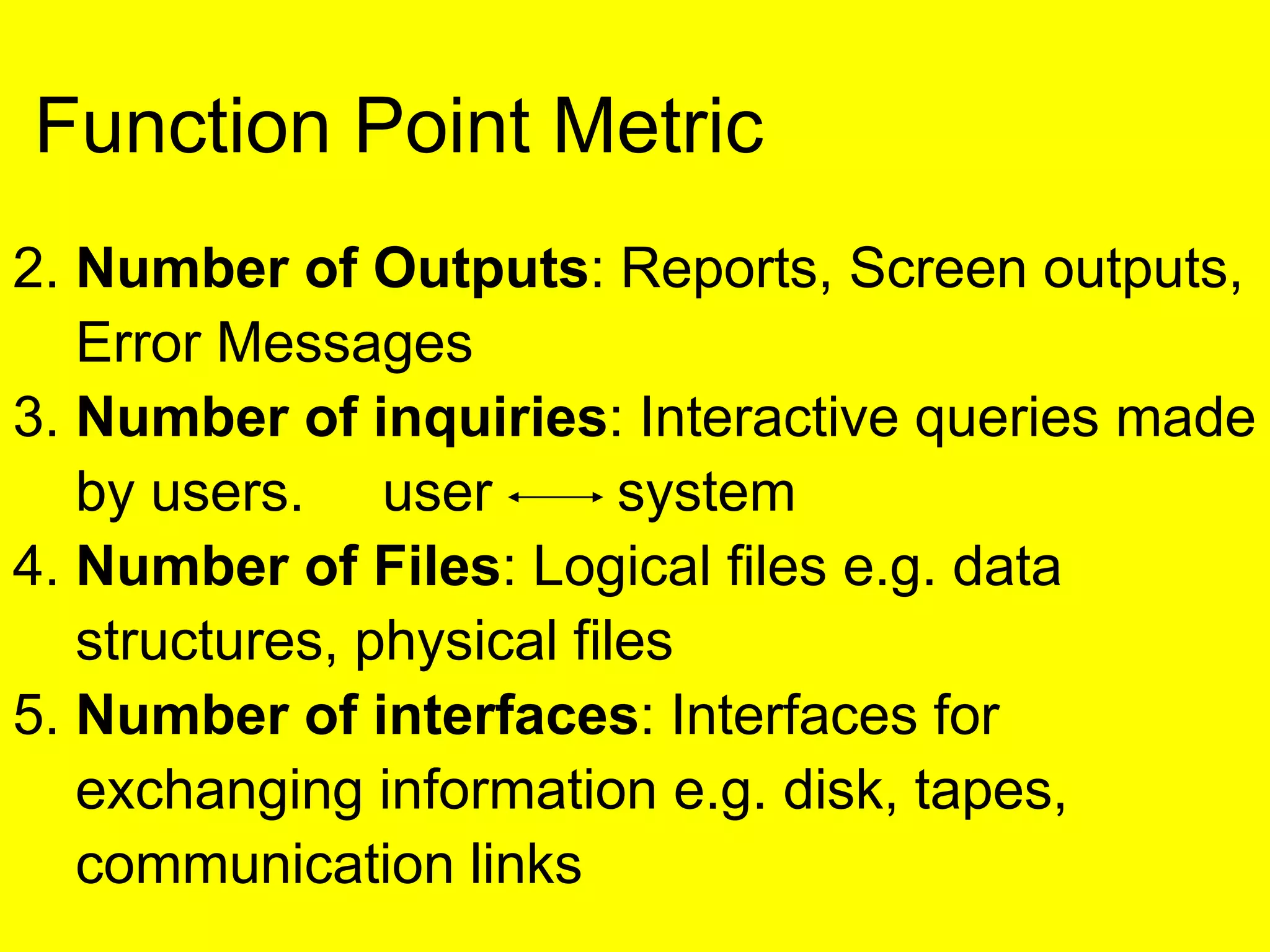
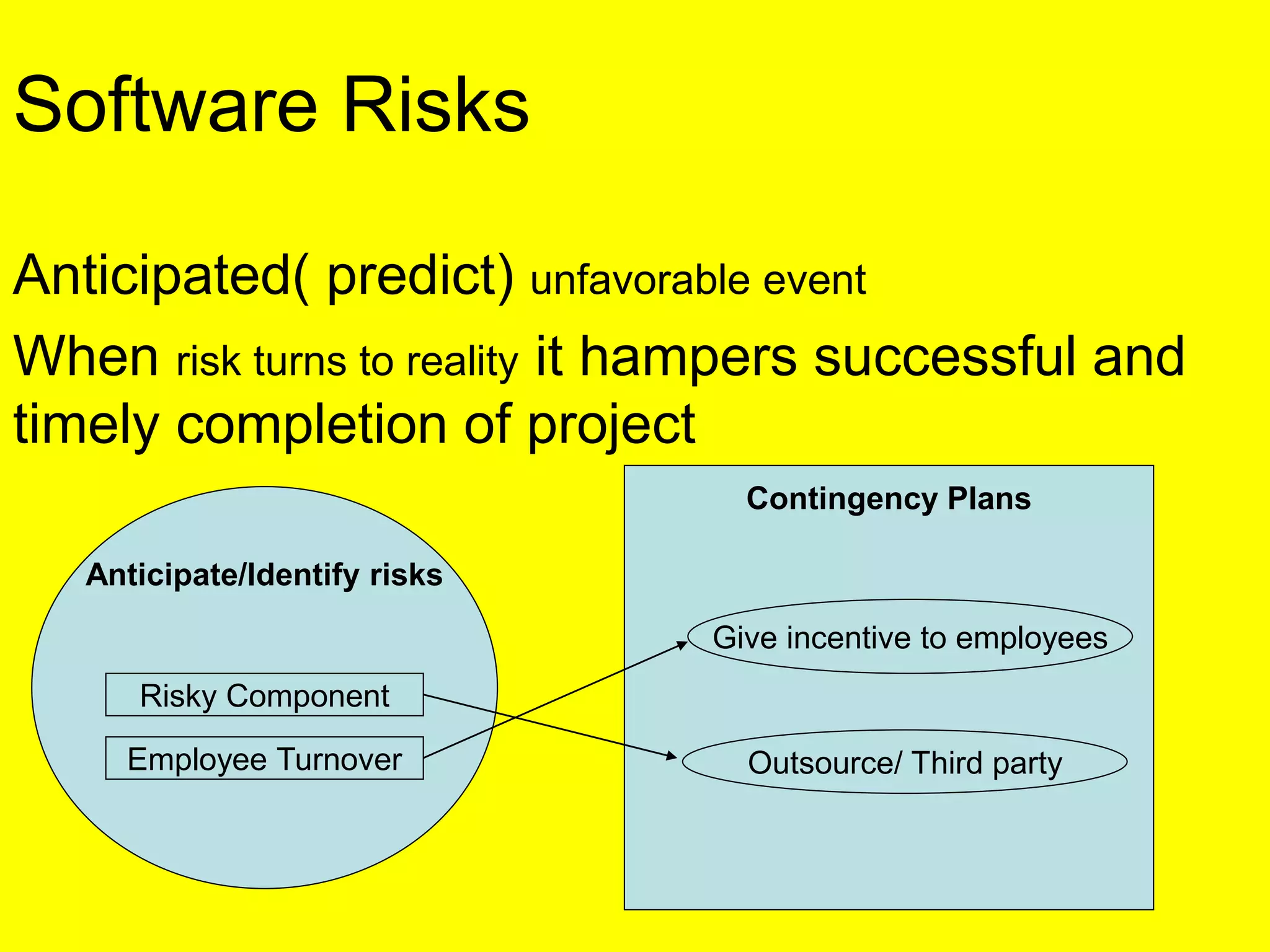
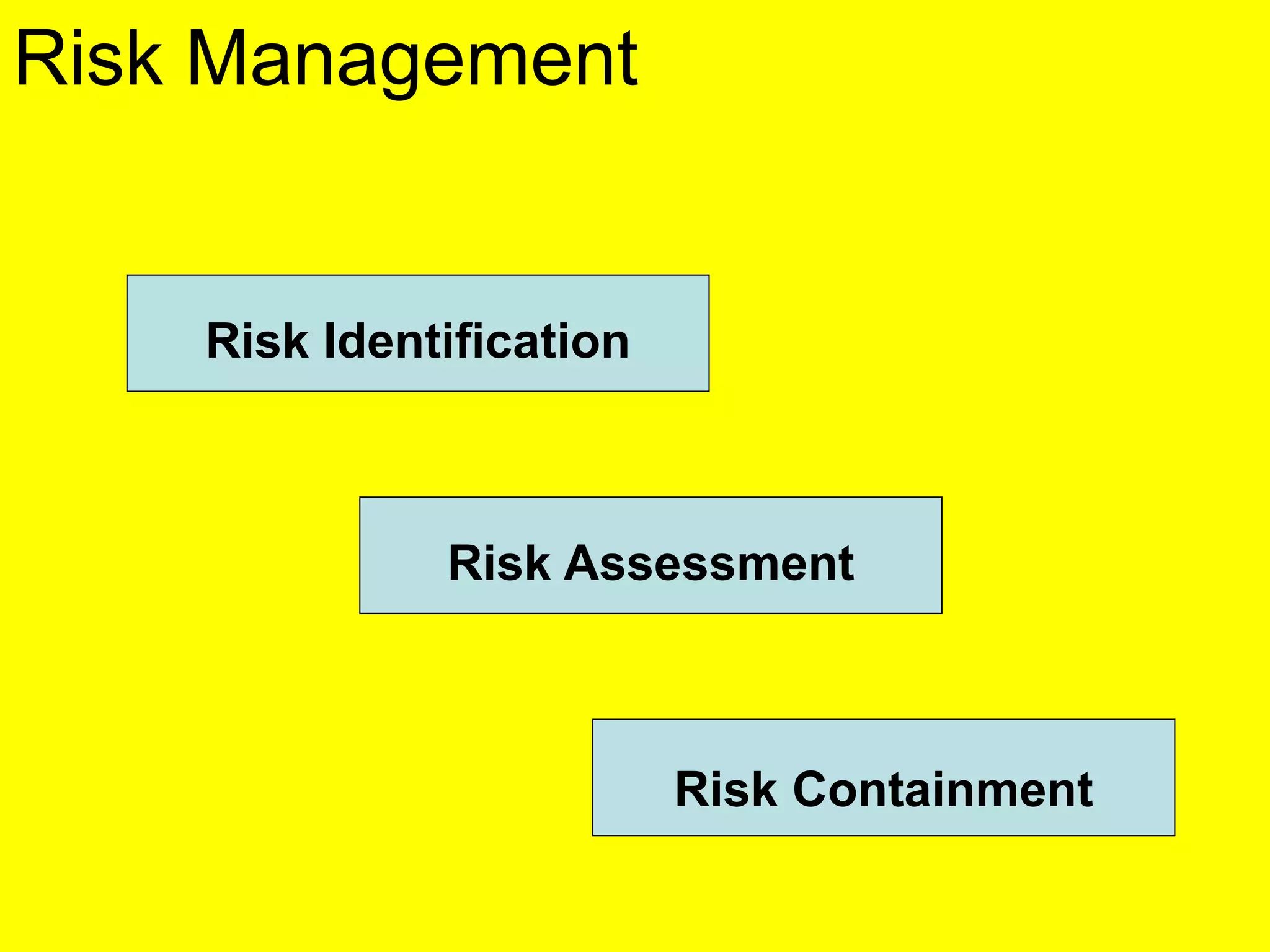
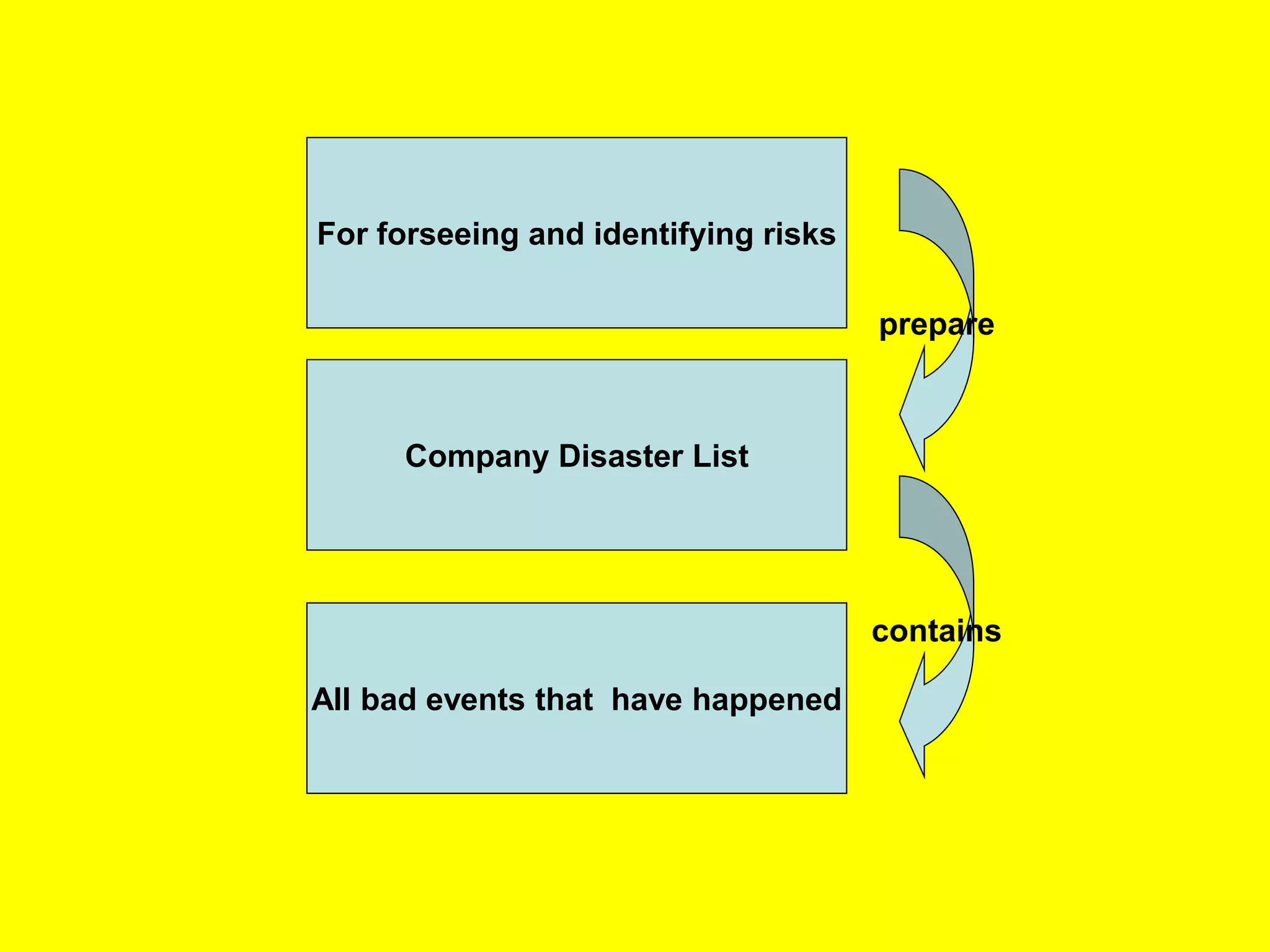
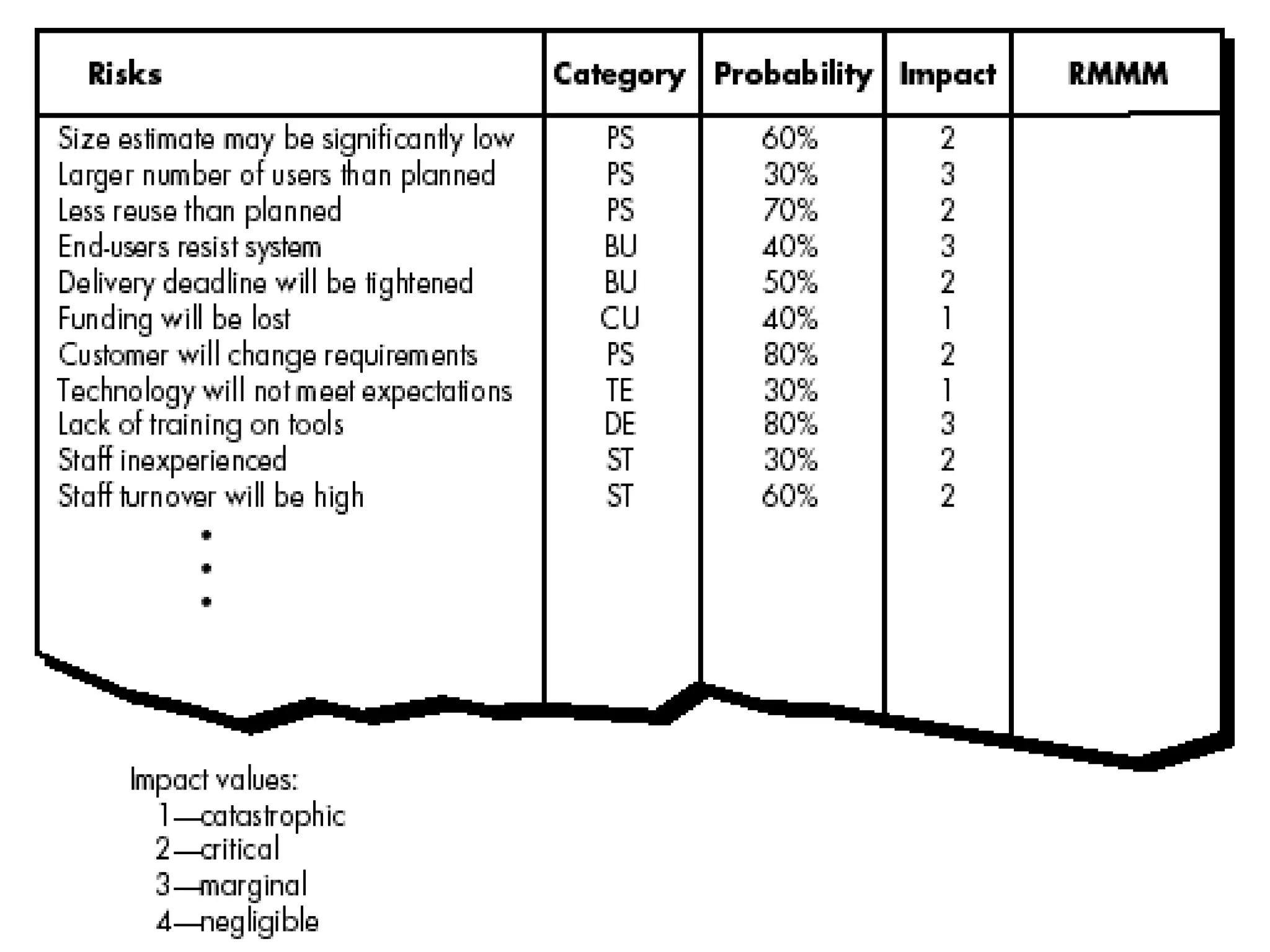
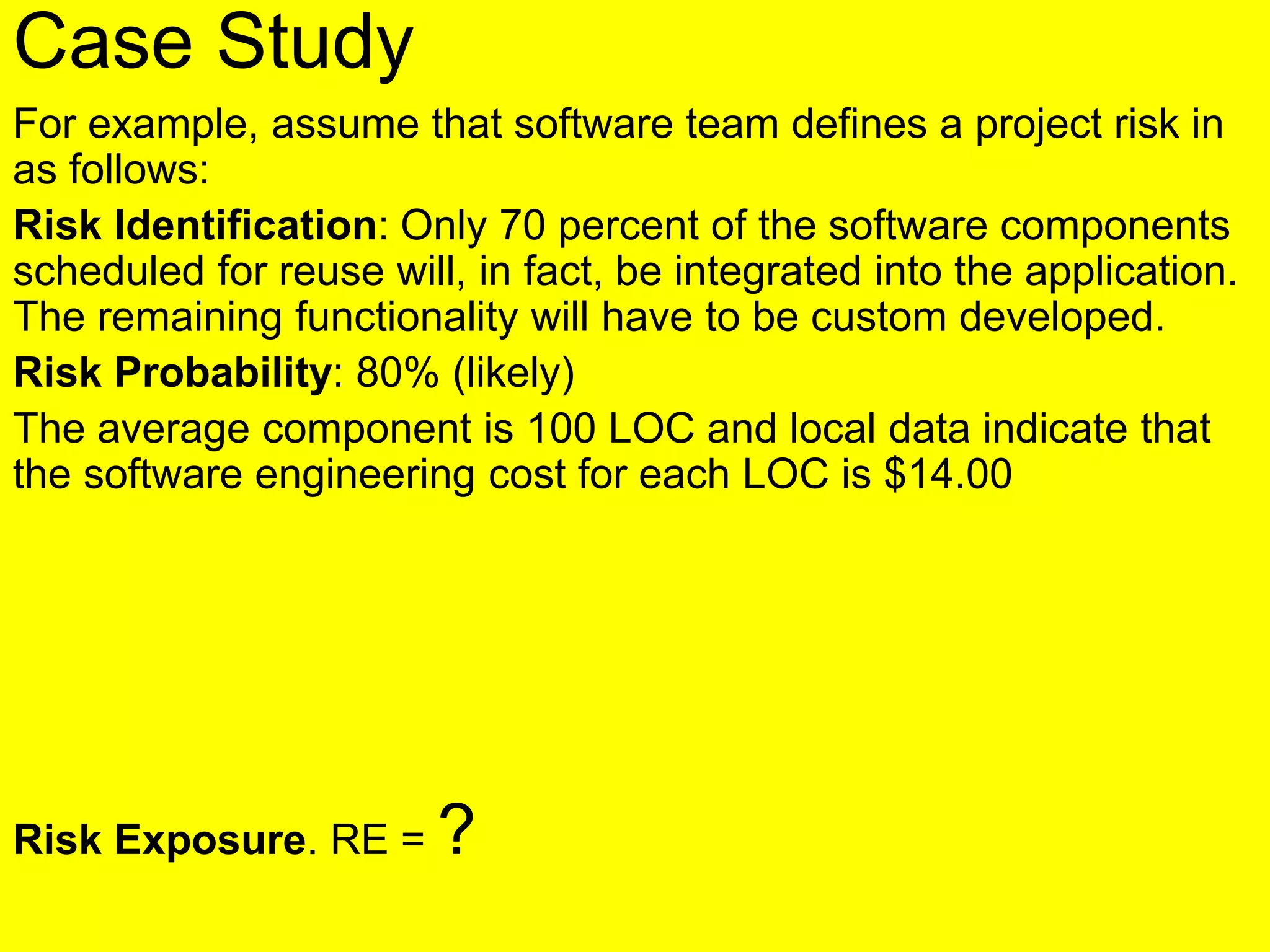
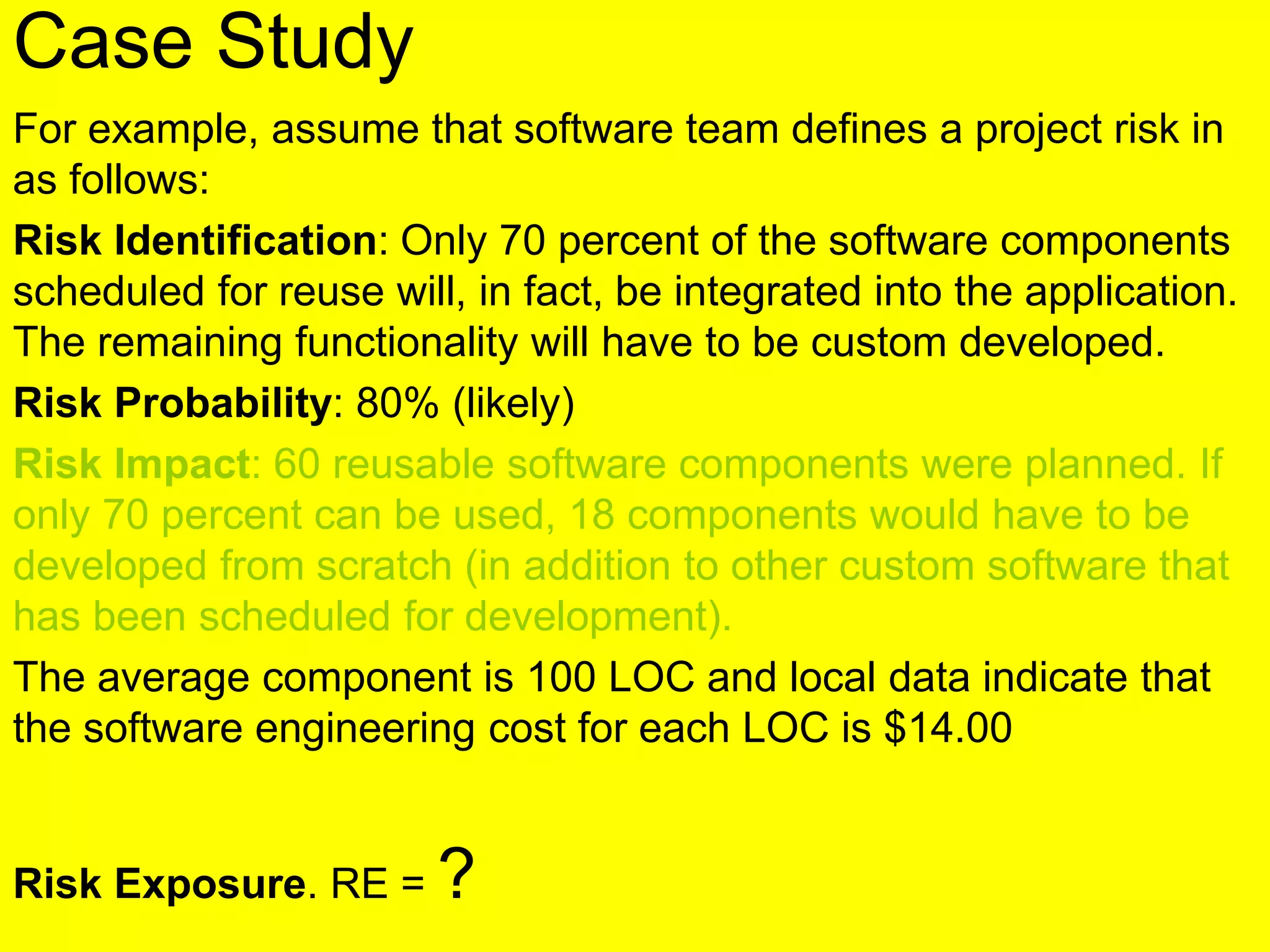
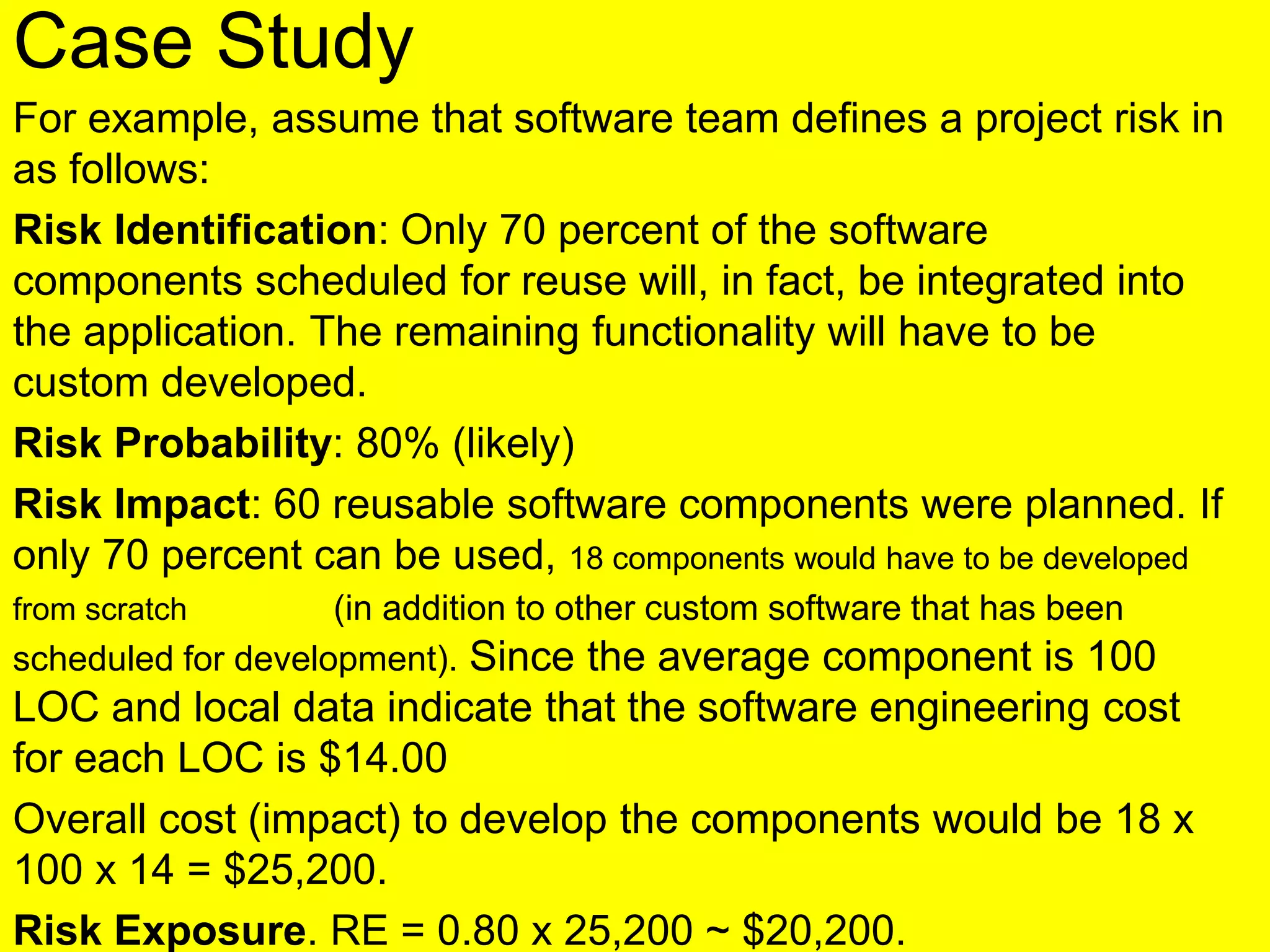
This document discusses various metrics for estimating project size, including lines of code and function points. It describes the advantages and disadvantages of lines of code, such as how coding style can affect the count. Function points measure size based on the number of user inputs, outputs, inquiries, files and interfaces. The document also covers identifying, assessing and containing risks in software projects. Risk identification involves categorizing risks, while assessment ranks risks based on probability and cost. Risk containment plans to avoid, transfer or reduce the most damaging risks.