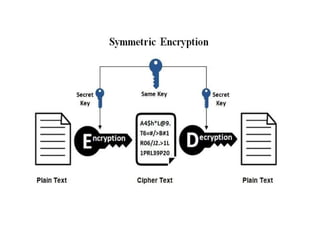
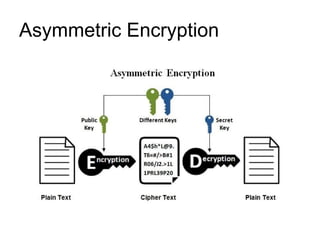
1. Encryption involves encoding information using an algorithm and cryptographic key to convert plain text into an encrypted cipher text that hides the information from anyone except the intended recipient. Symmetric encryption uses a single shared key for encryption and decryption while asymmetric encryption uses separate public and private keys.
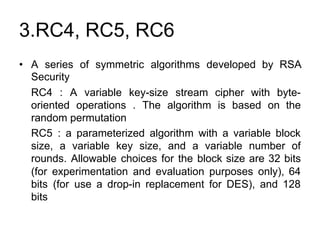
2. Common encryption algorithms and standards discussed include AES, DES, RSA, MD5, and SHA which vary in their key sizes, block sizes, number of rounds, use of public/private keys, and applications for encrypting data and verifying message integrity.
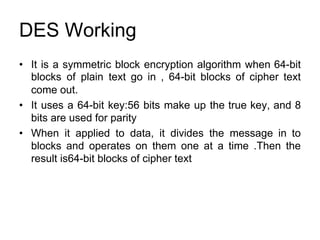
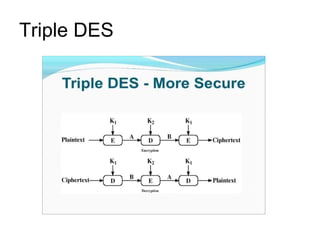
3. Symmetric algorithms like AES and DES are block ciphers that encrypt fixed sized blocks of plain text while asymmetric algorithms like RSA use public/private key pairs