Embed presentation
Download as PDF, PPTX


![ “it is acknowledged that a time when investigators
will be able [sic] readily ascertain the identity of
individuals from their genetic information may not
be far away.”
There has been some success to date](https://image.slidesharecdn.com/clayton2-151117152928-lva1-app6891/75/Ellen-Wright-Clayton-Modeling-Risk-to-Privacy-in-Genomics-Research-3-2048.jpg)


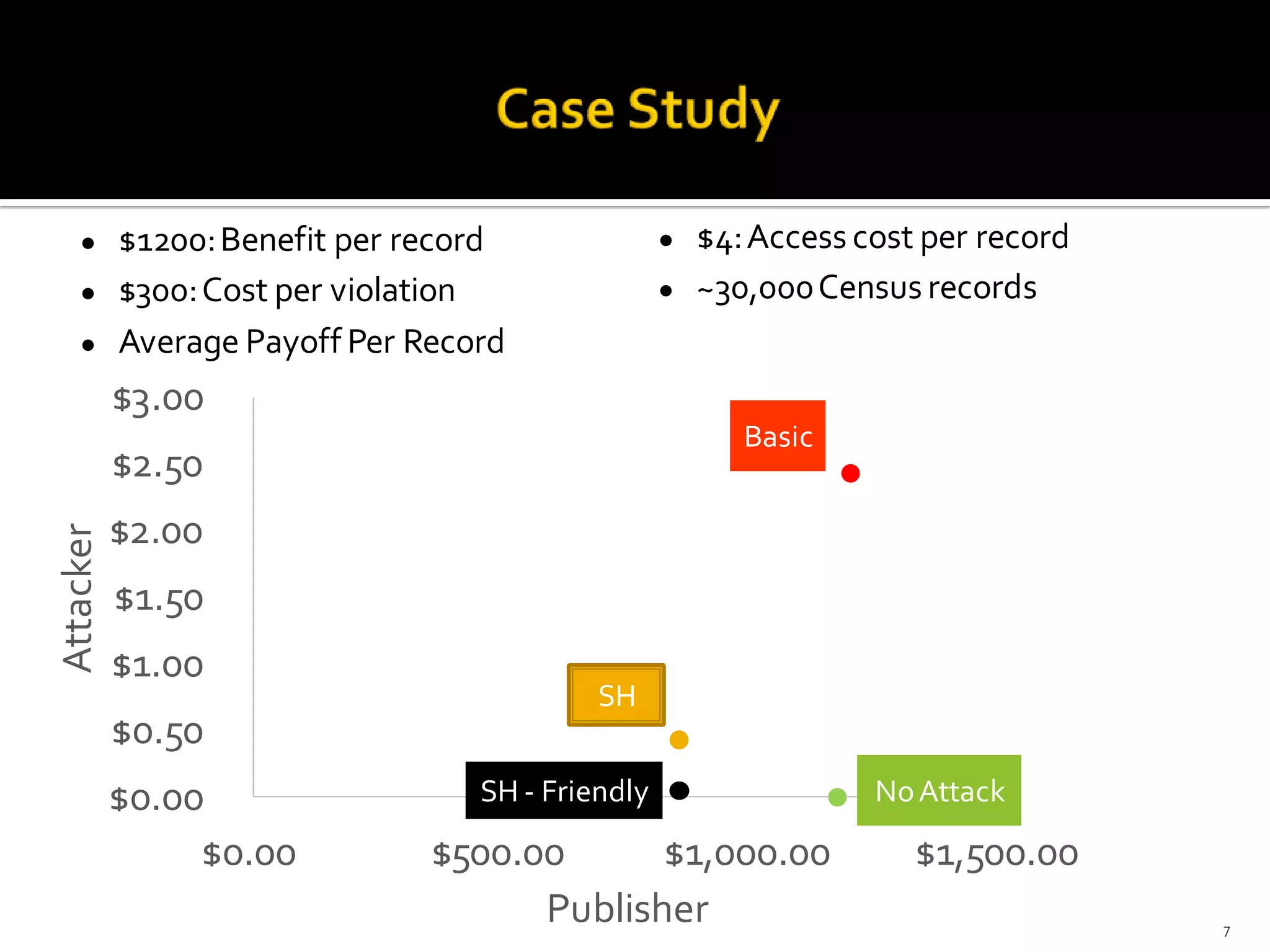



The document discusses the concerns and realities surrounding the risk of re-identification of individuals from genetic data, highlighting that while re-identification is possible, it is not prevalent. It emphasizes the need for stronger penalties for those attempting re-identification and calls for improved governance and accountability in data sharing practices. Despite some compliance violations reported, the overall compliance rate remains high, suggesting a controlled approach to data access and sharing.


![ “it is acknowledged that a time when investigators
will be able [sic] readily ascertain the identity of
individuals from their genetic information may not
be far away.”
There has been some success to date](https://image.slidesharecdn.com/clayton2-151117152928-lva1-app6891/75/Ellen-Wright-Clayton-Modeling-Risk-to-Privacy-in-Genomics-Research-3-2048.jpg)






