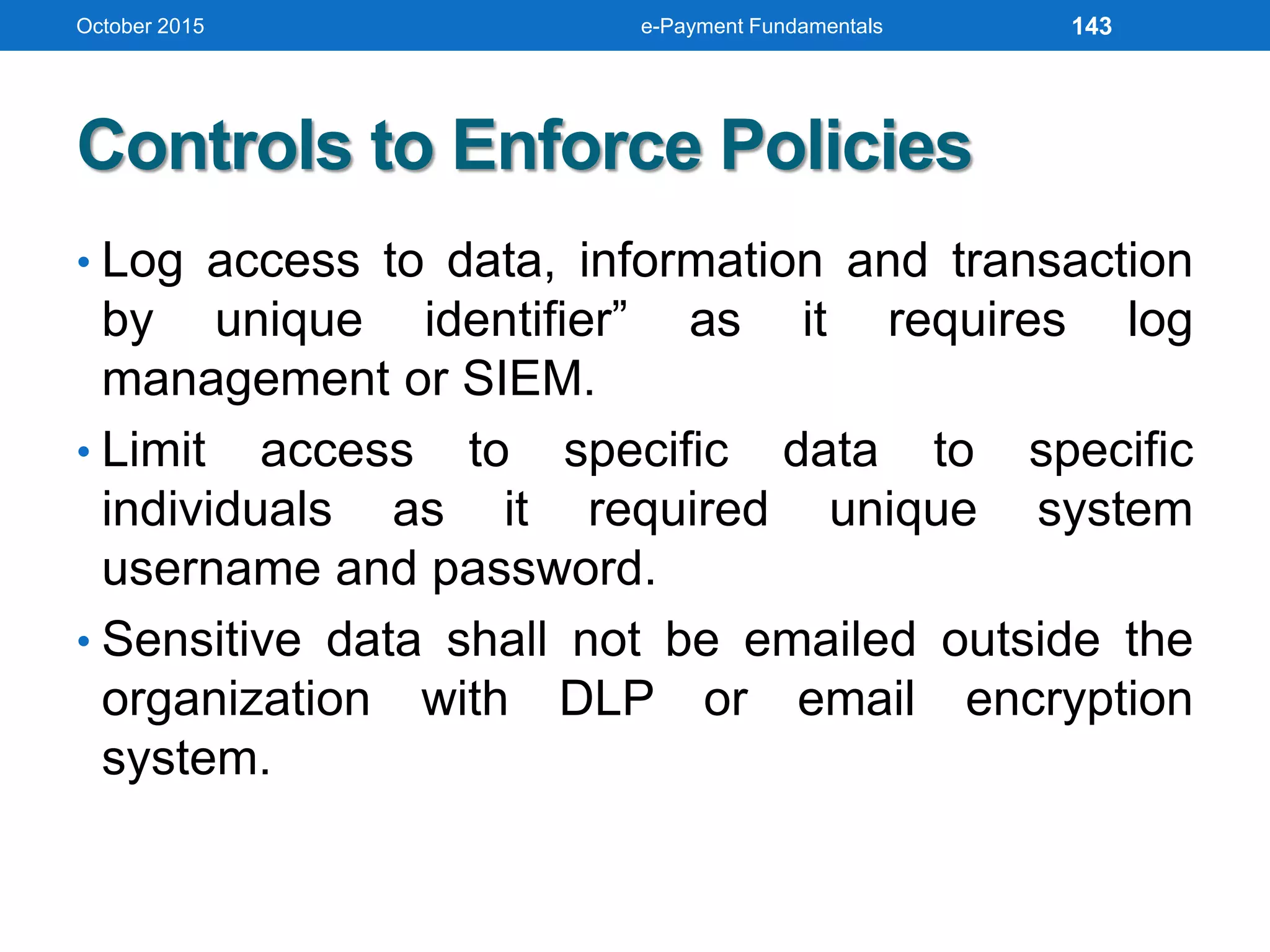
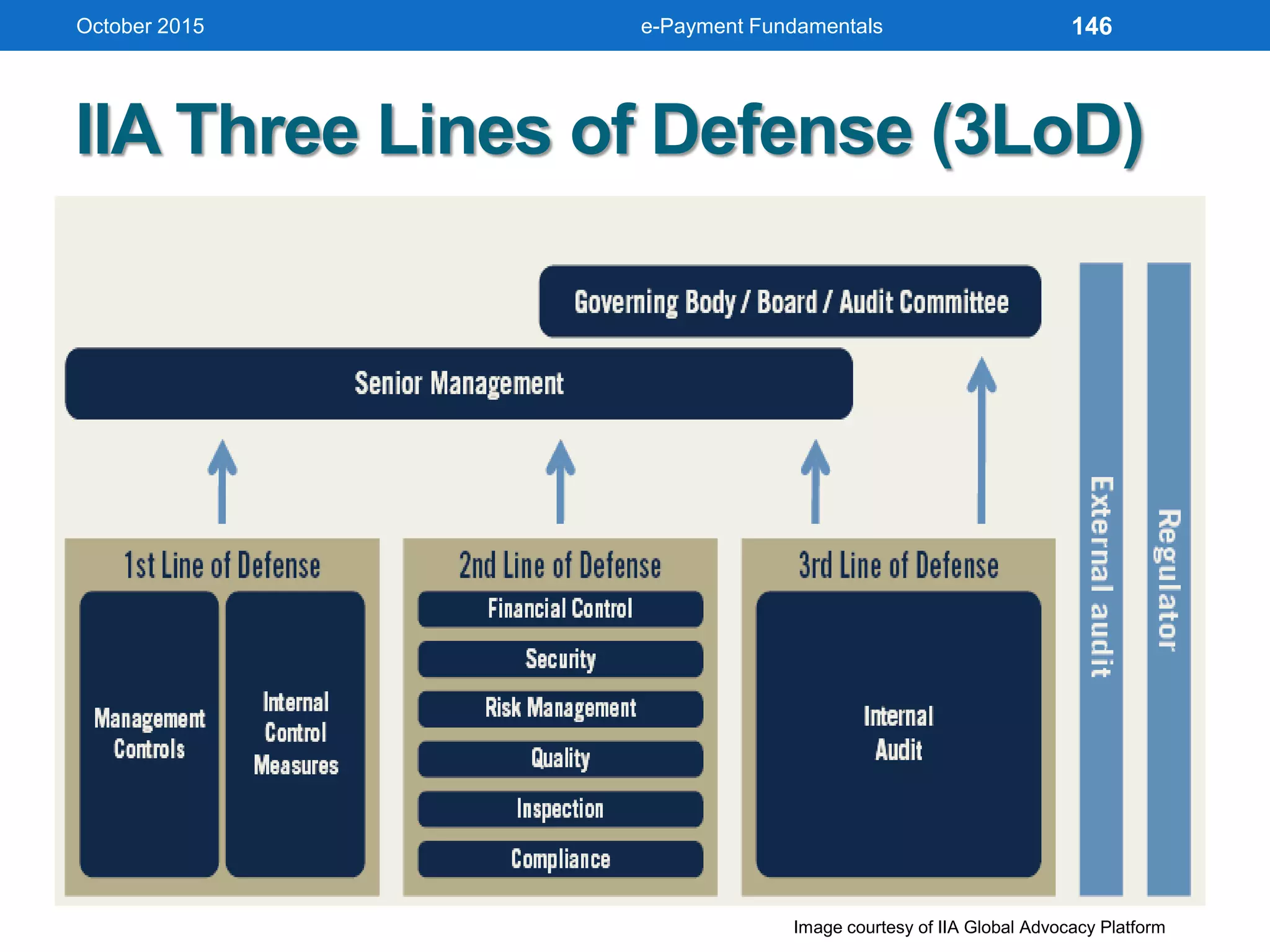
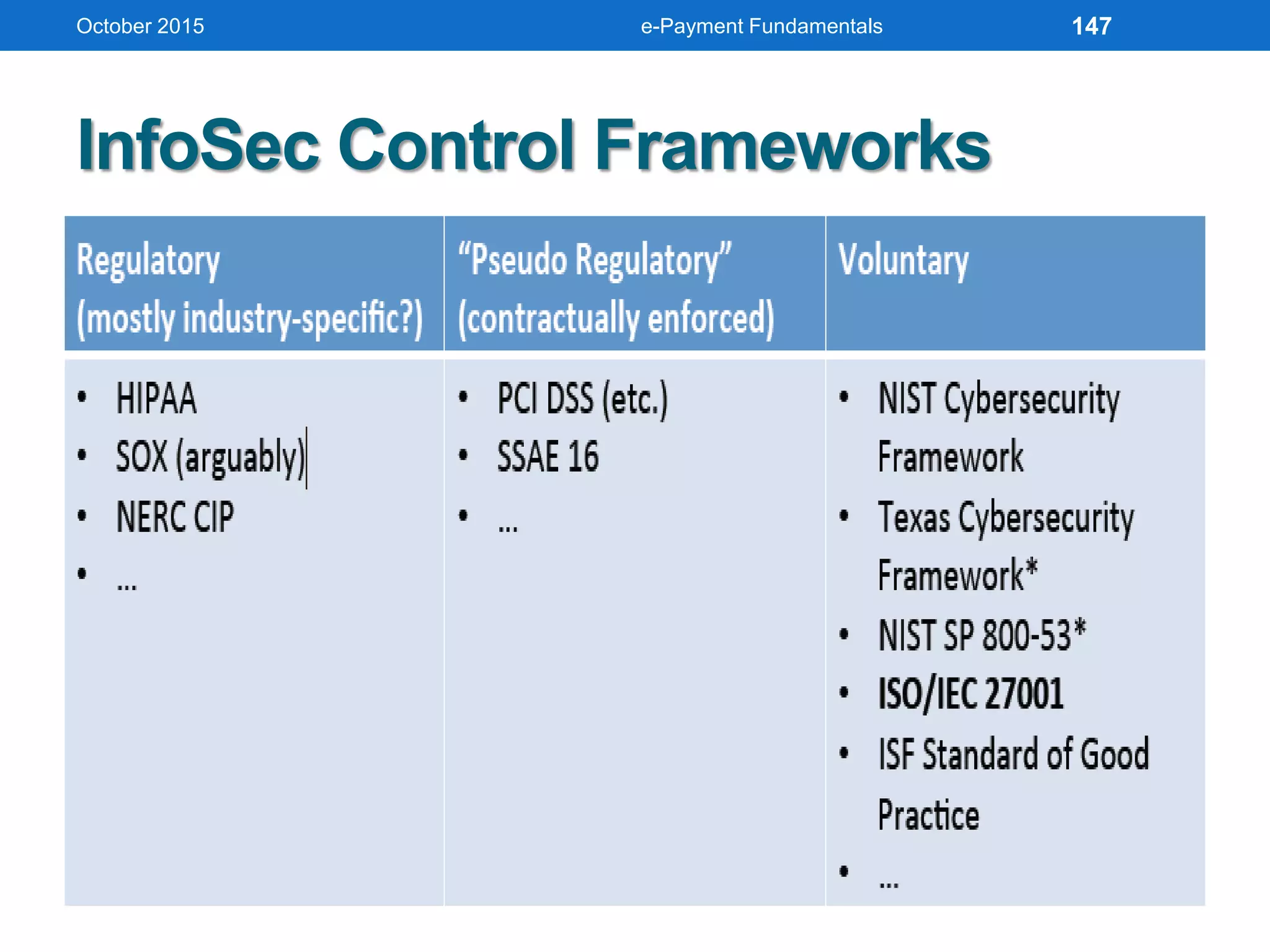
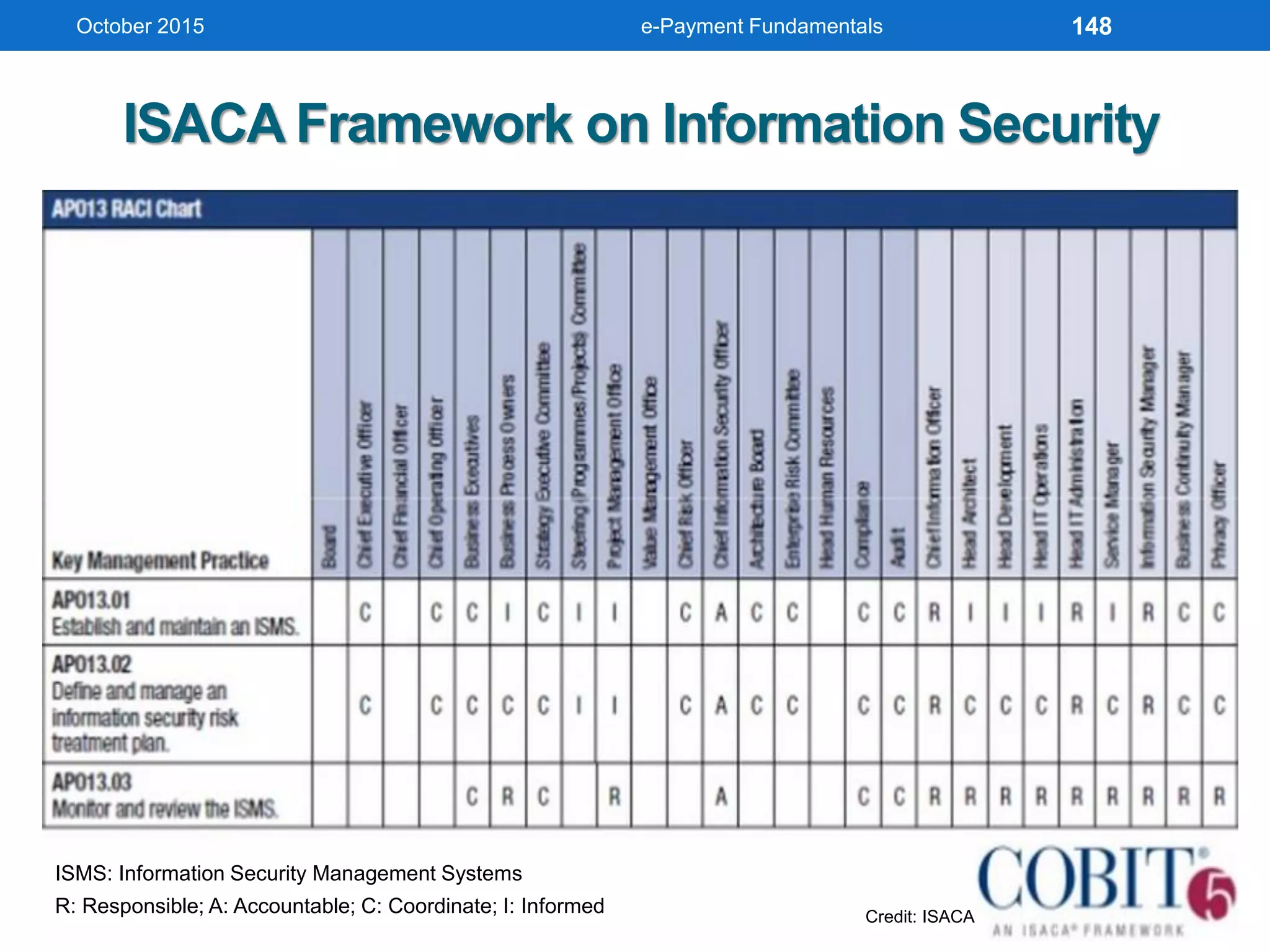
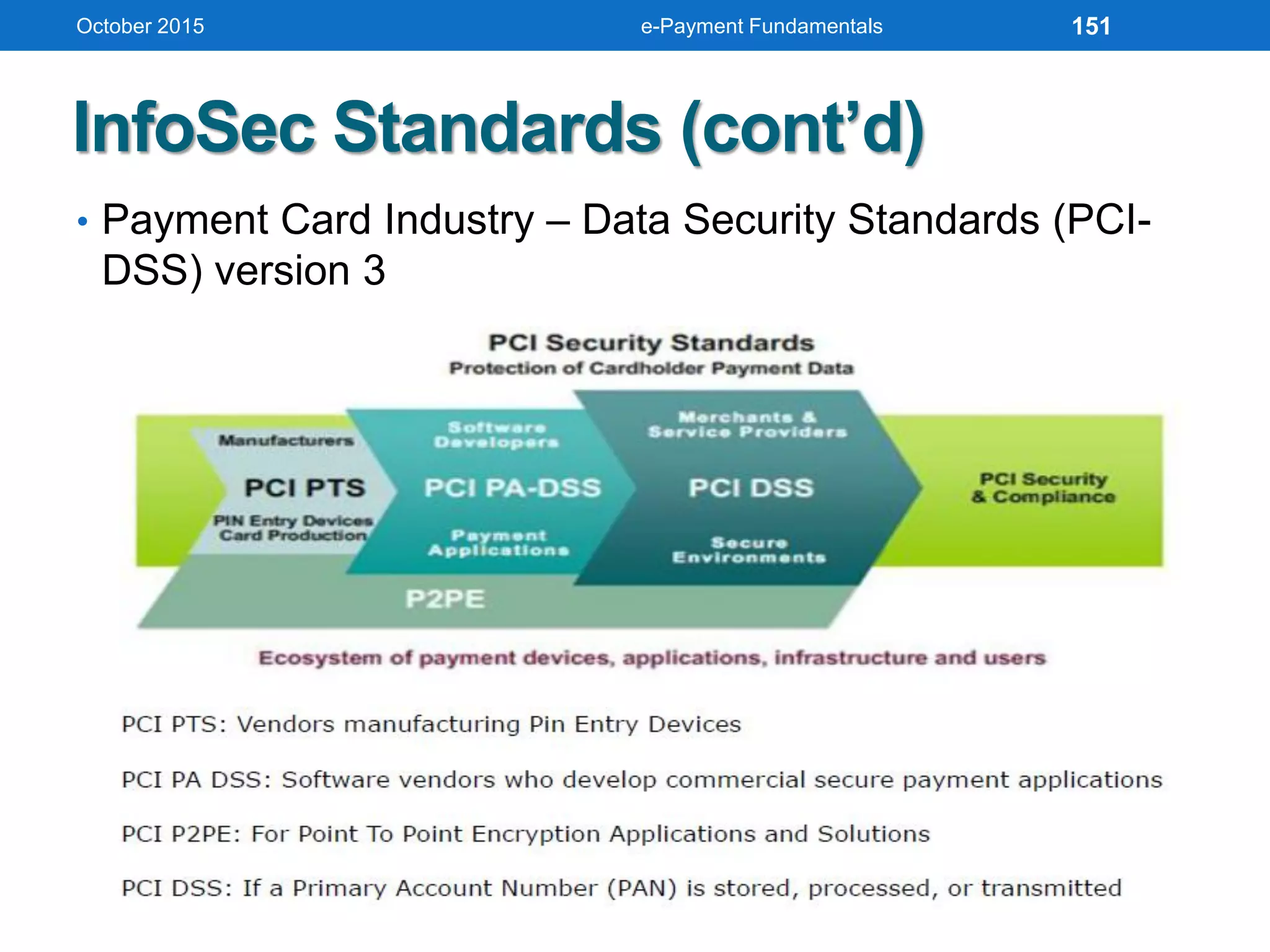
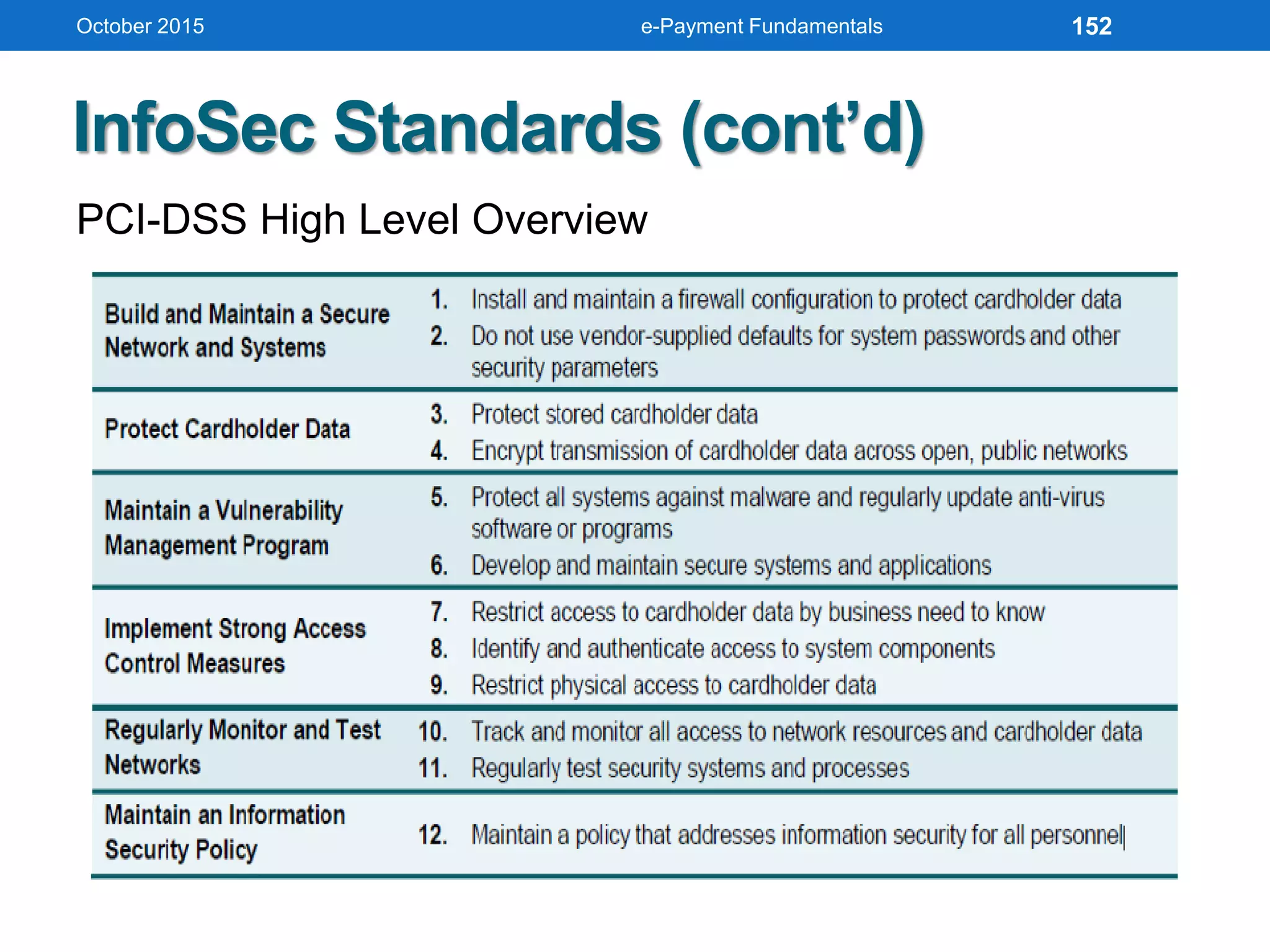
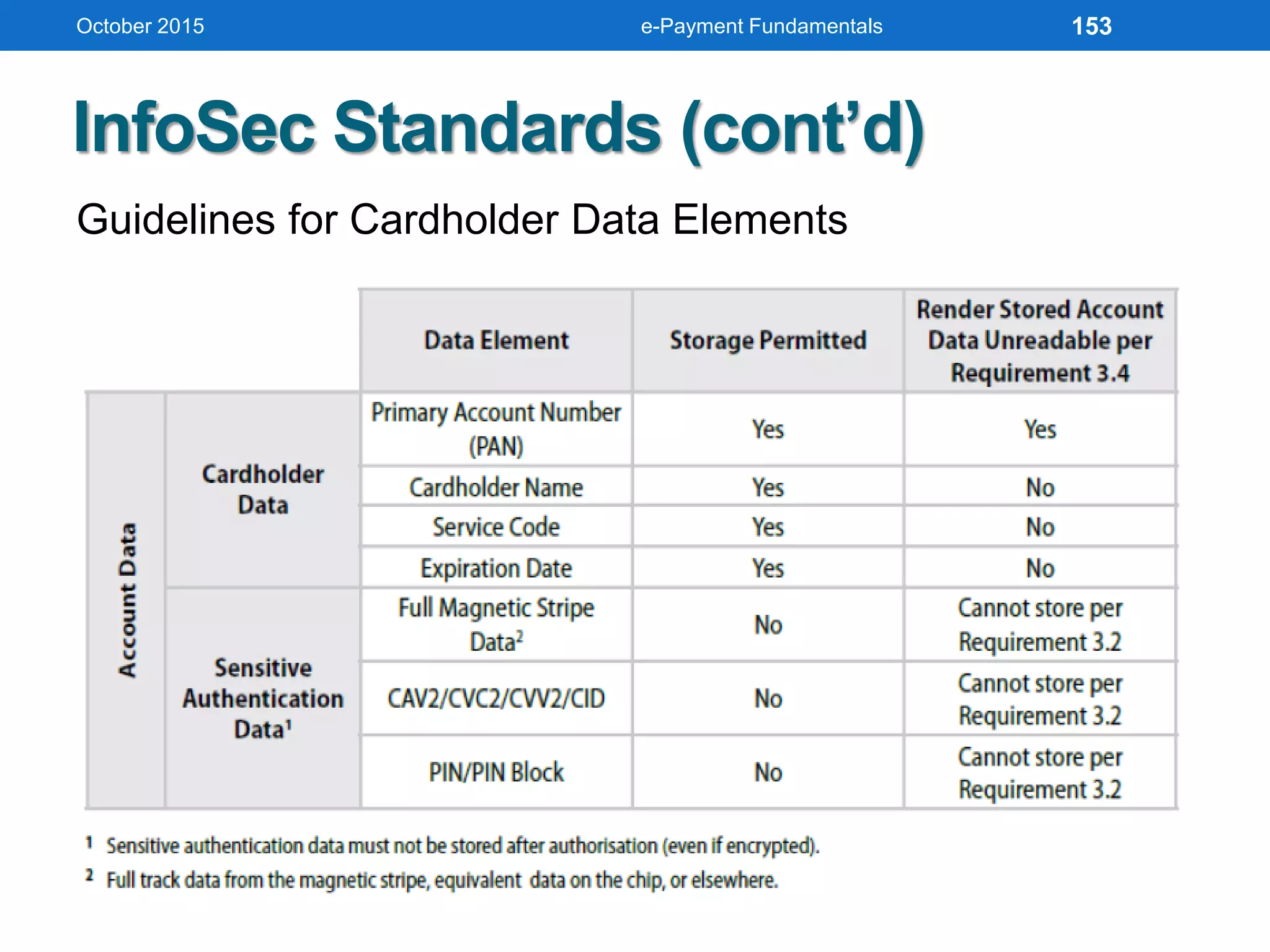
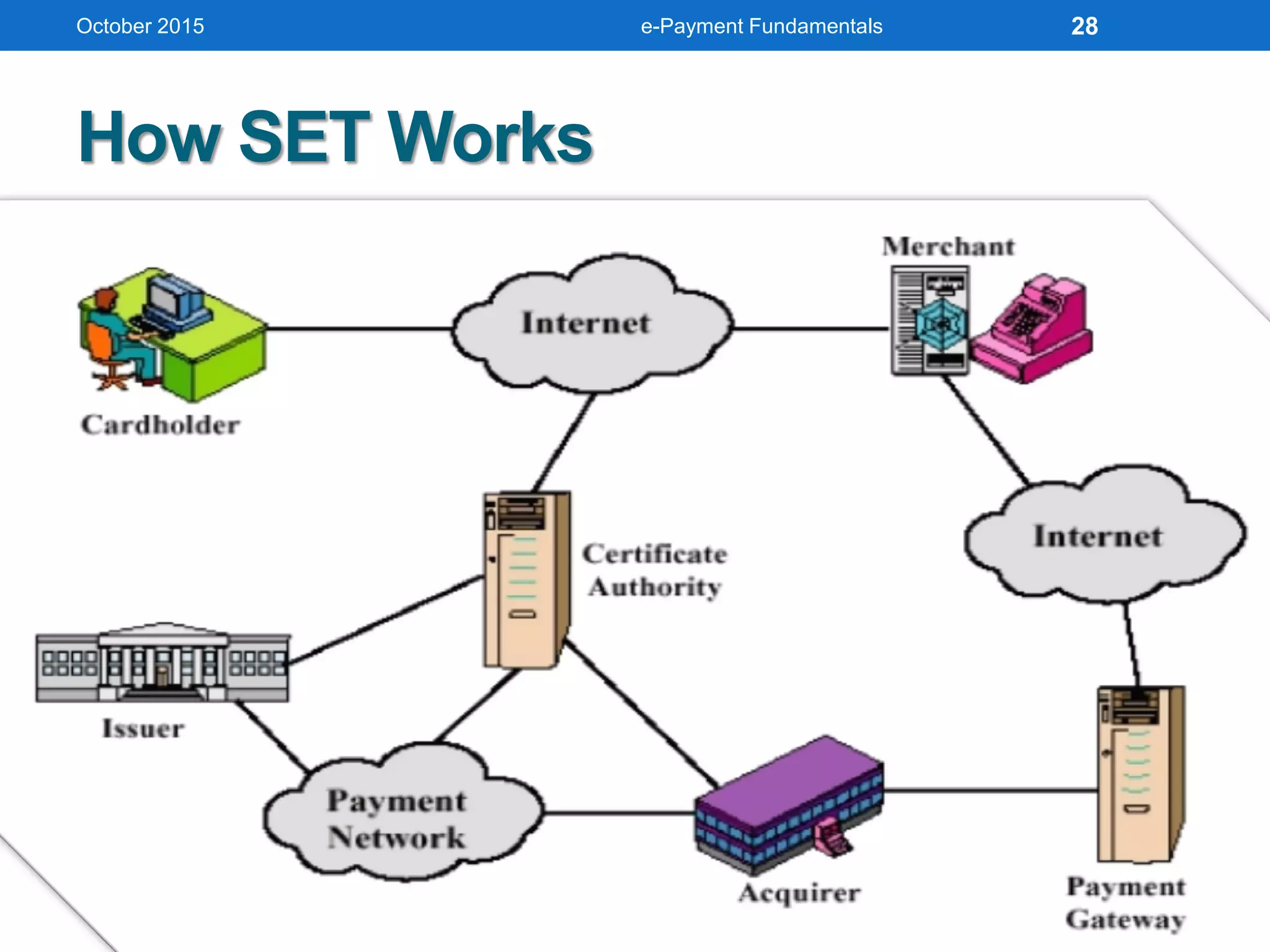
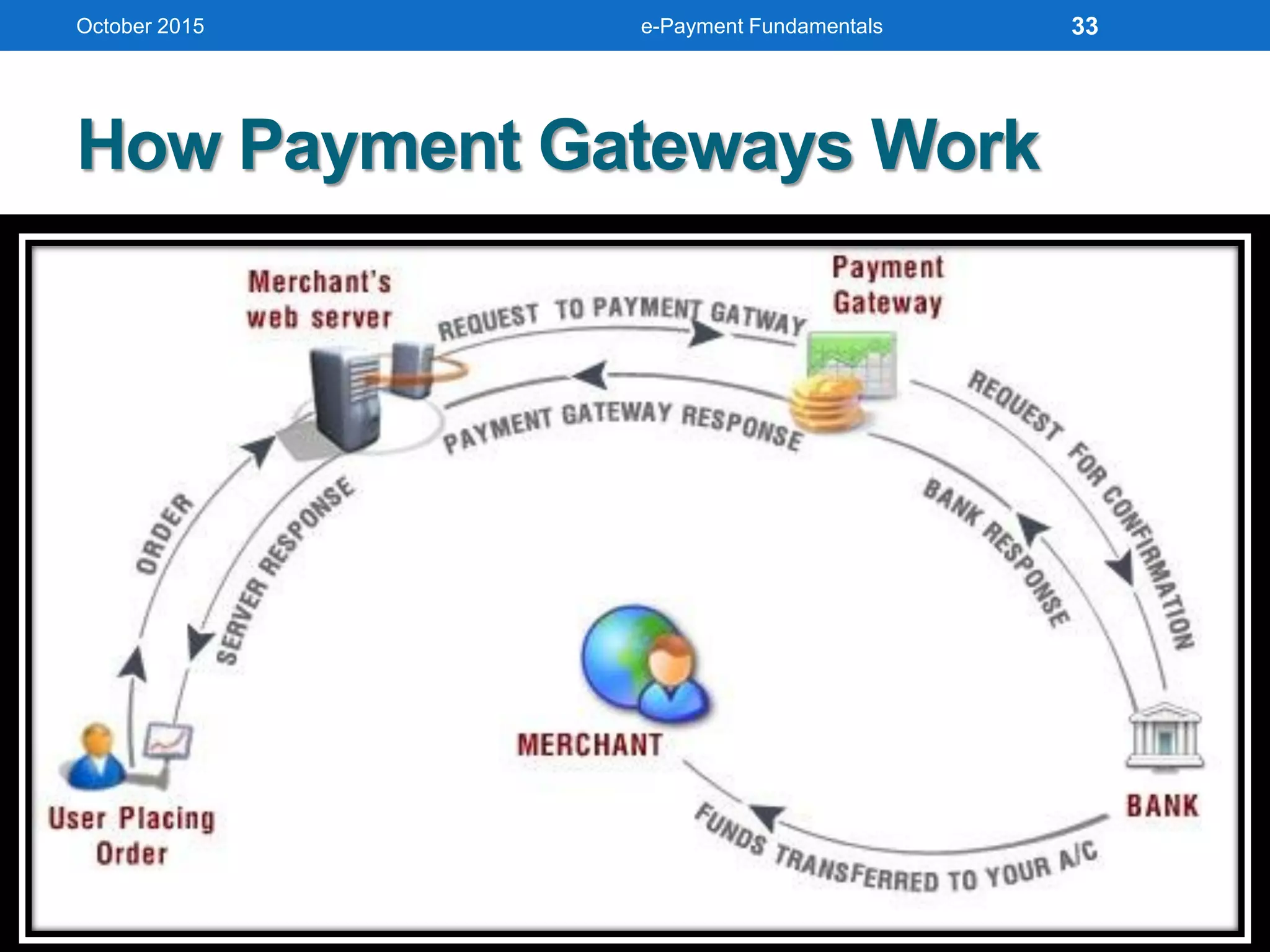
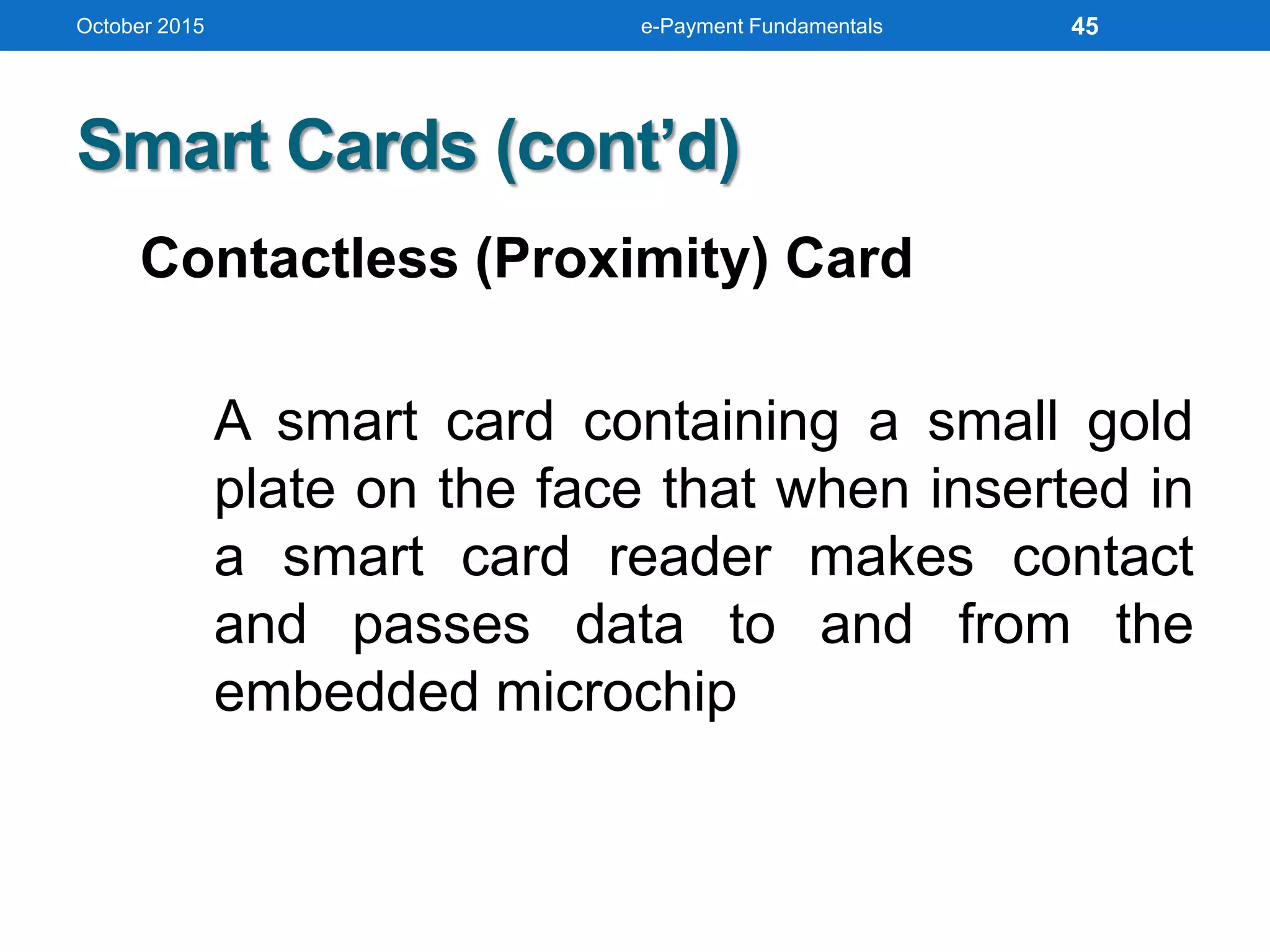
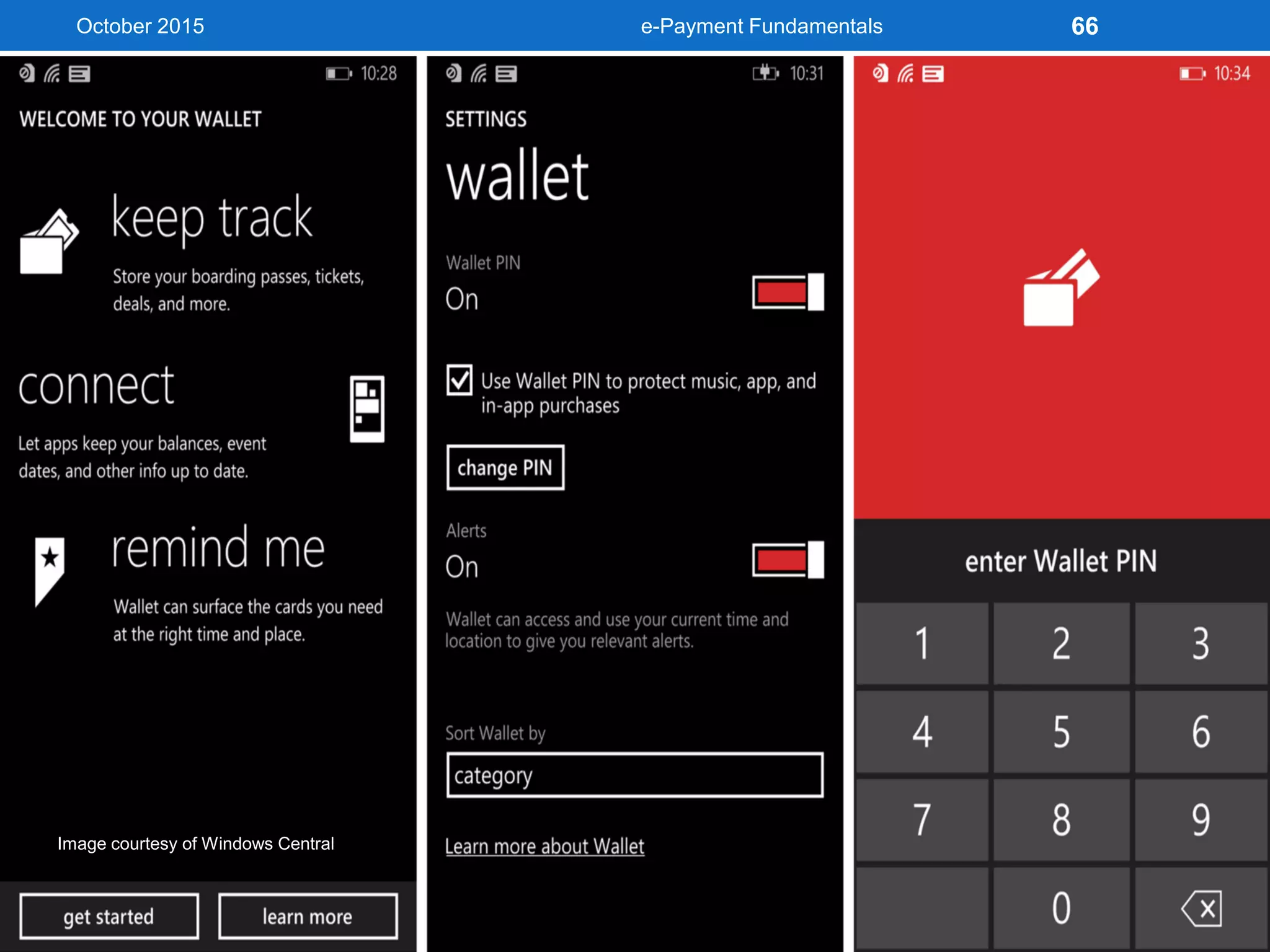
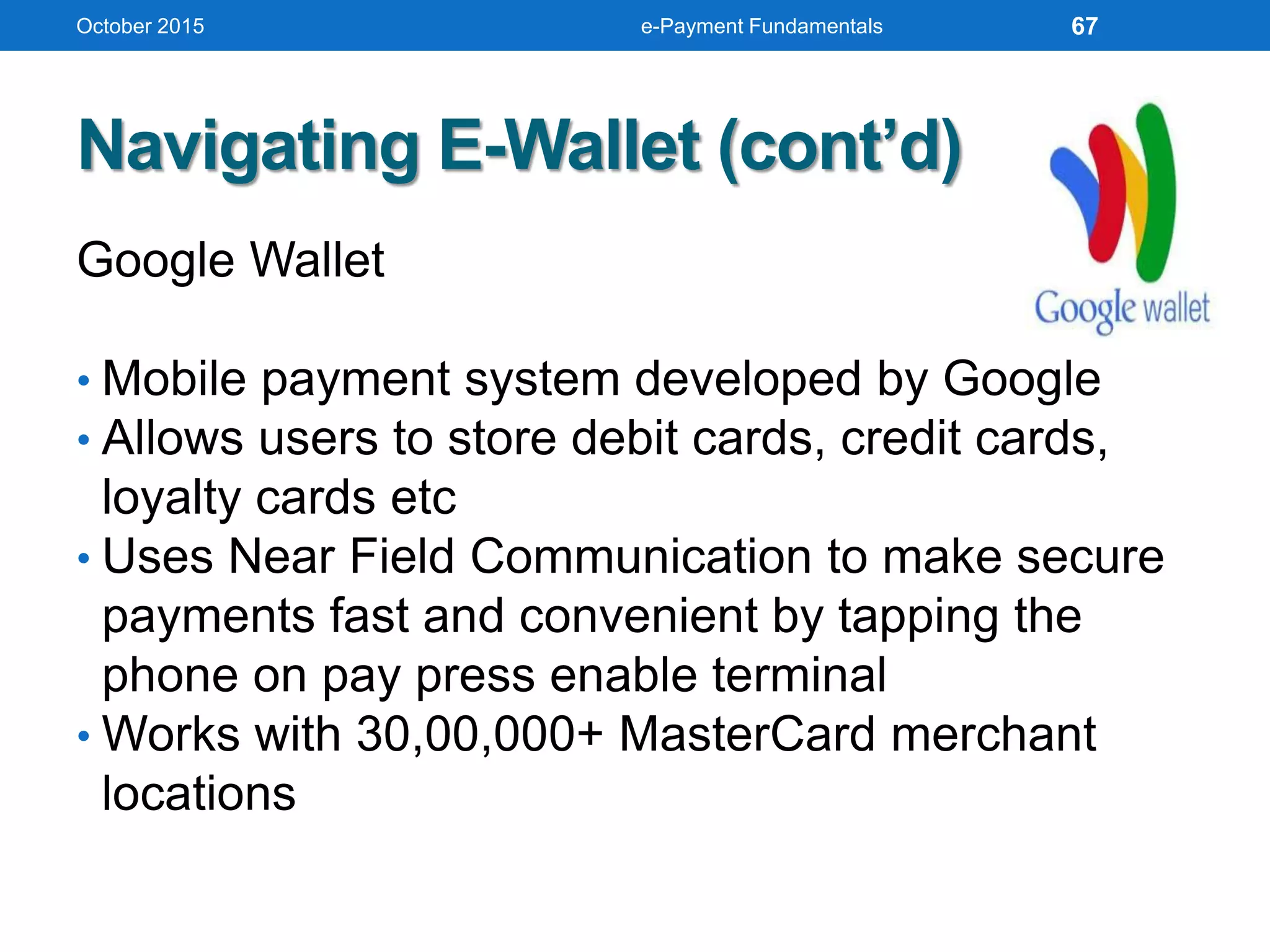
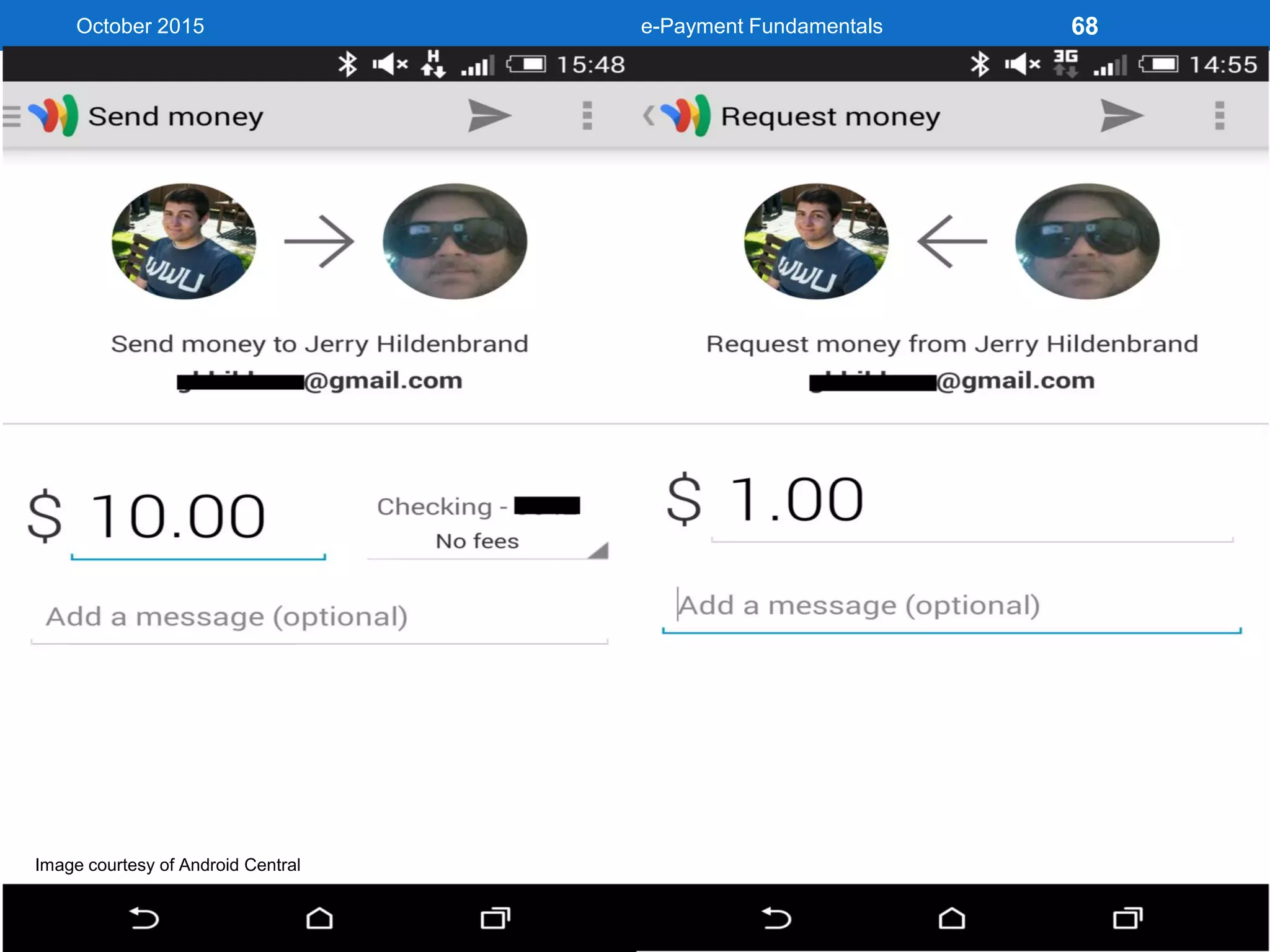
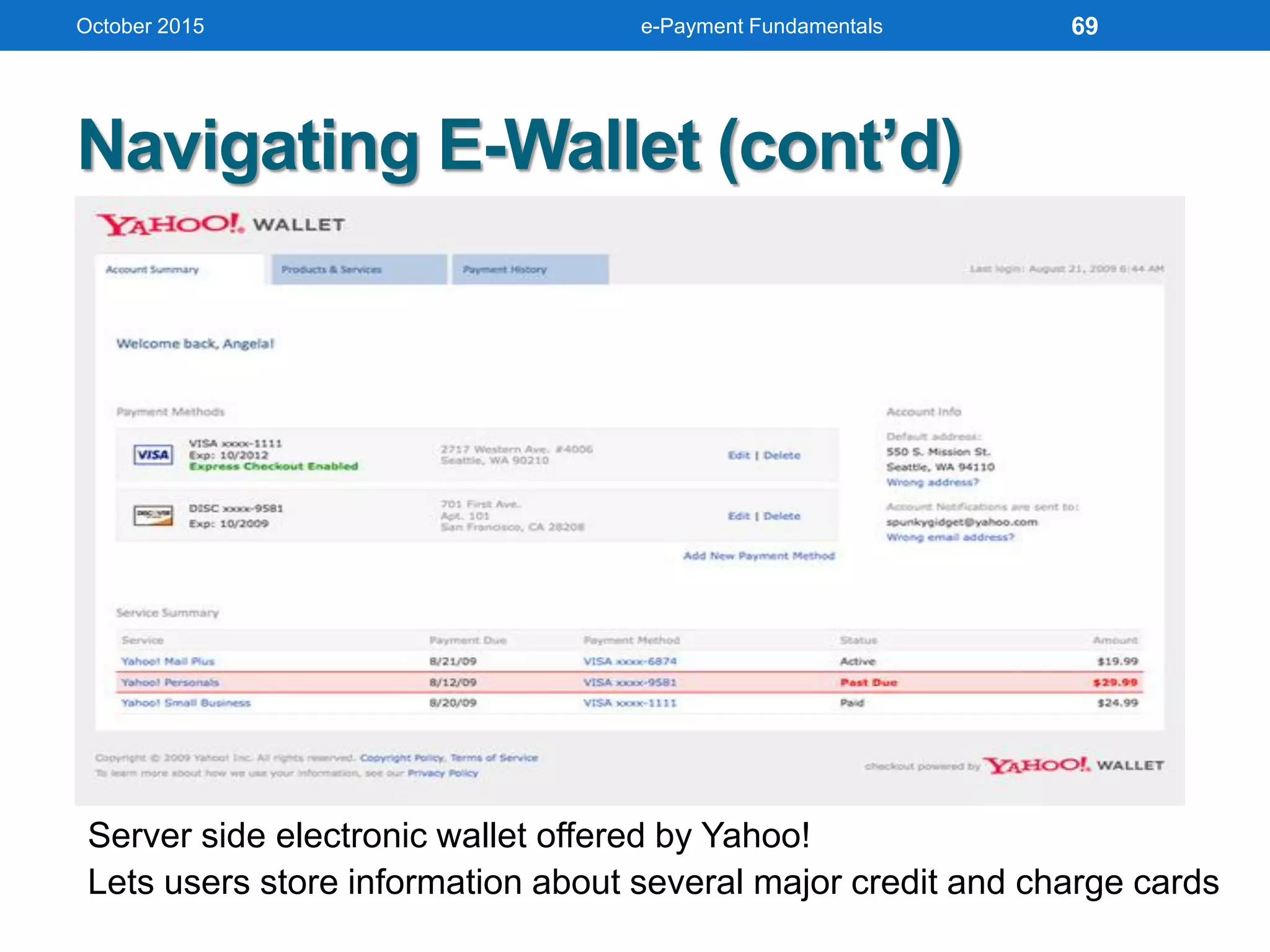
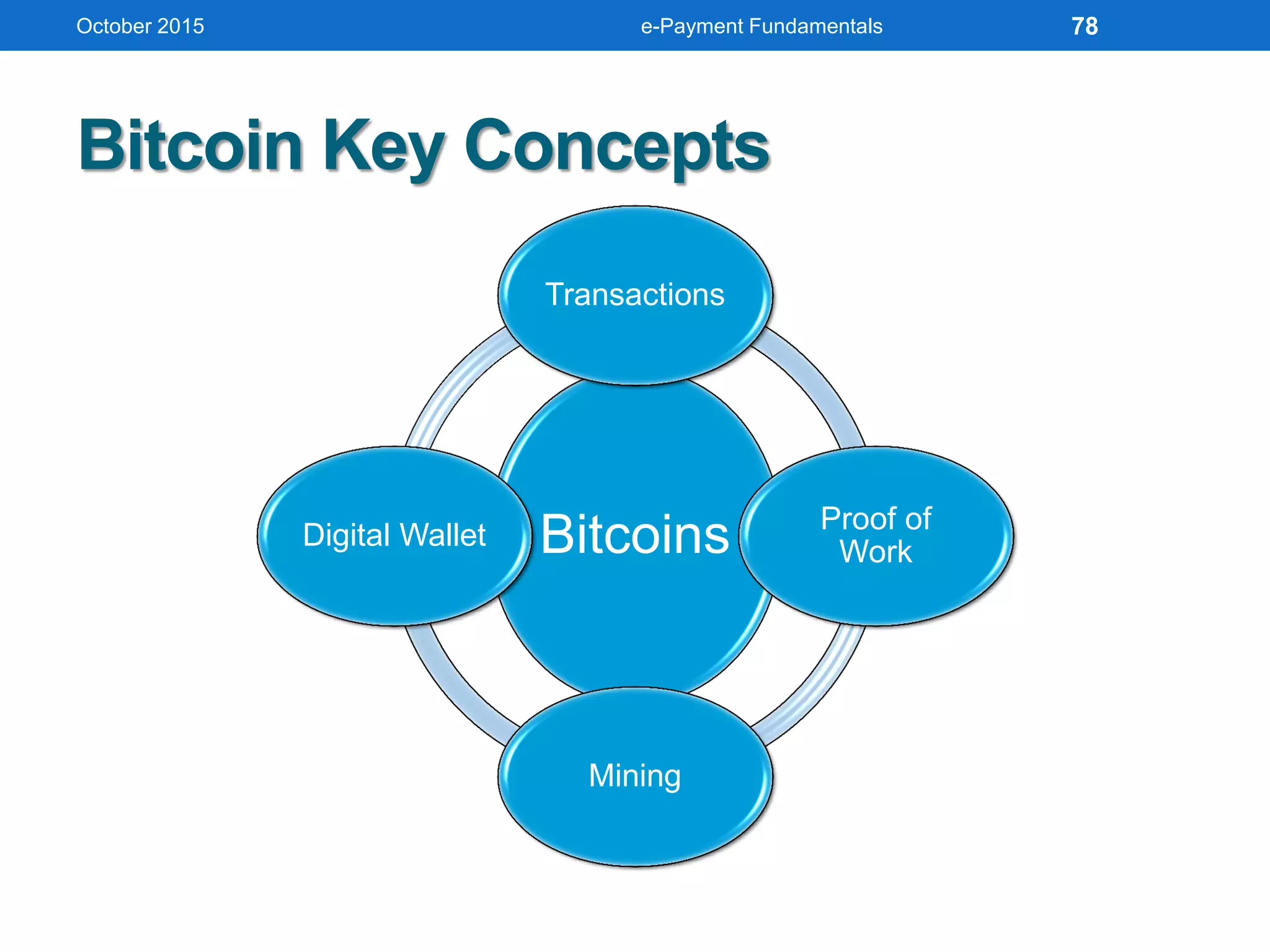
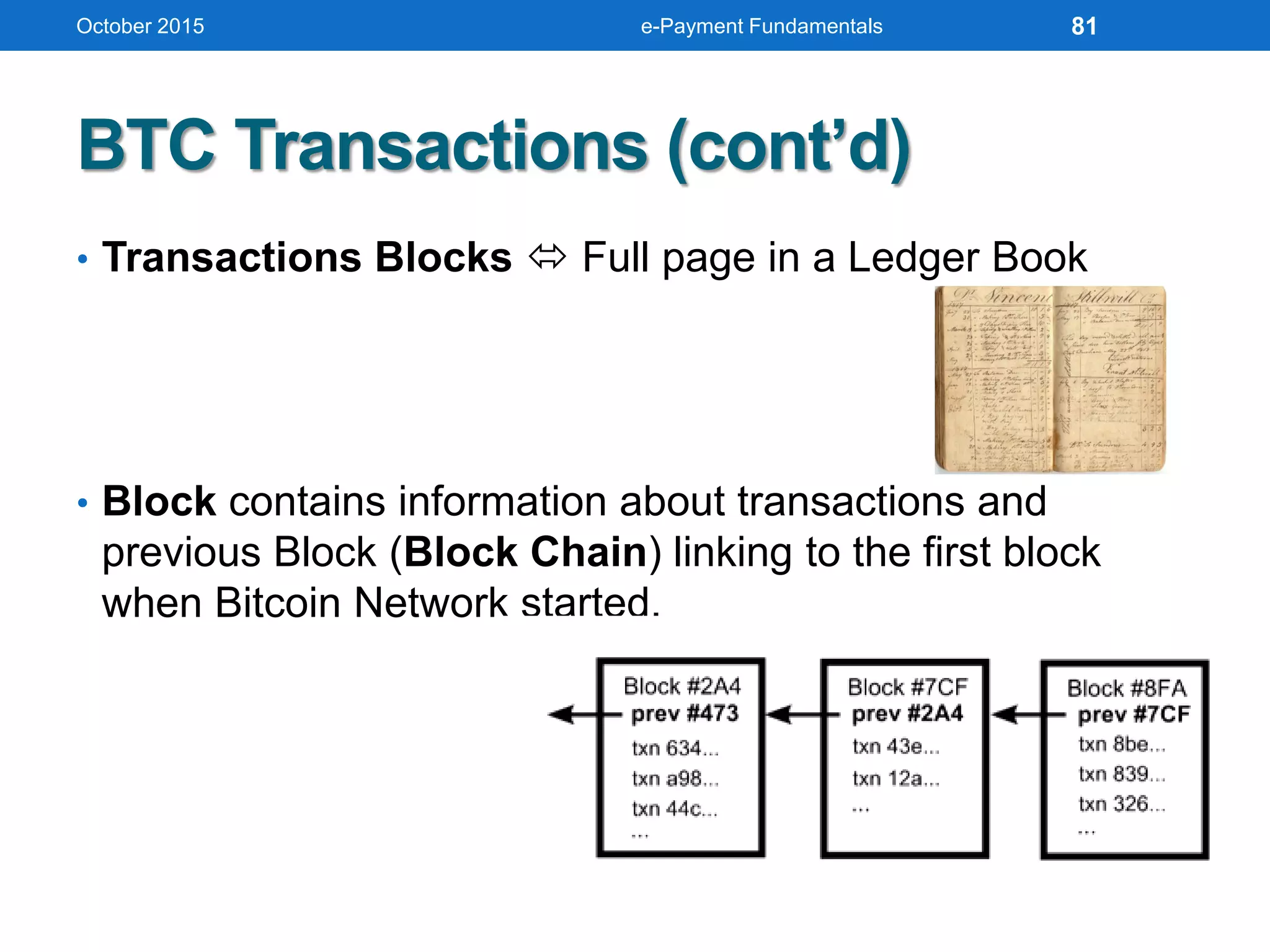
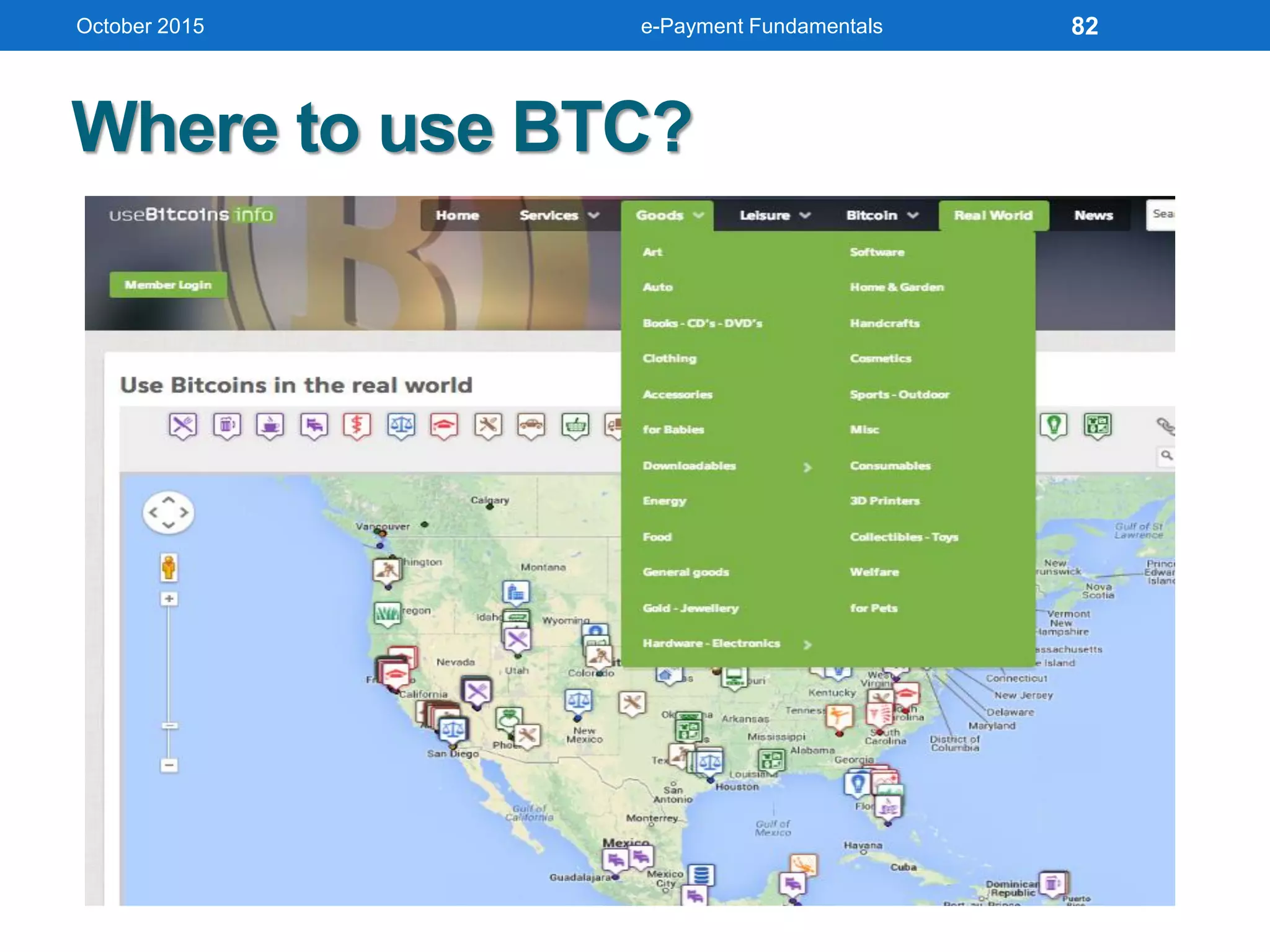
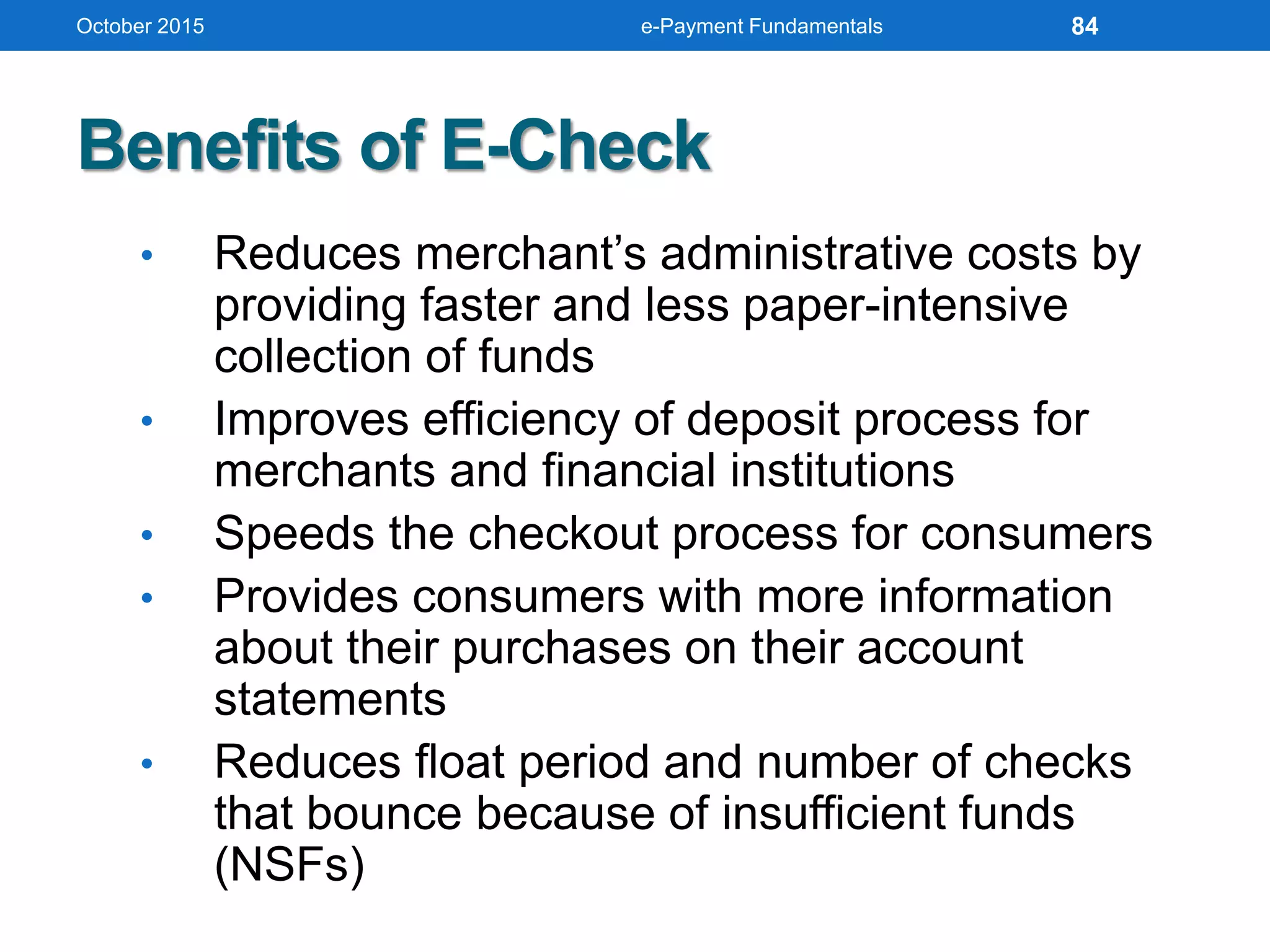
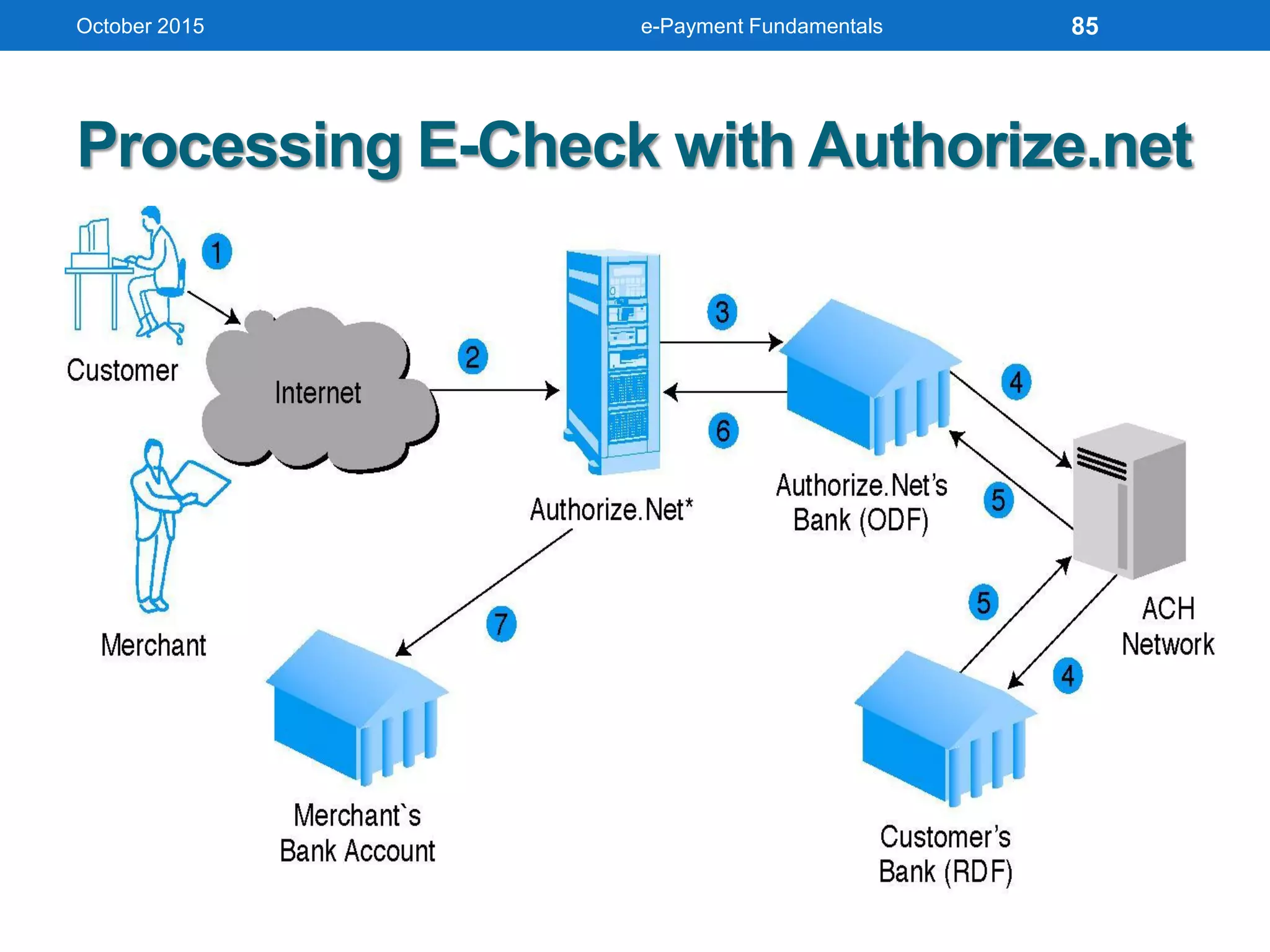
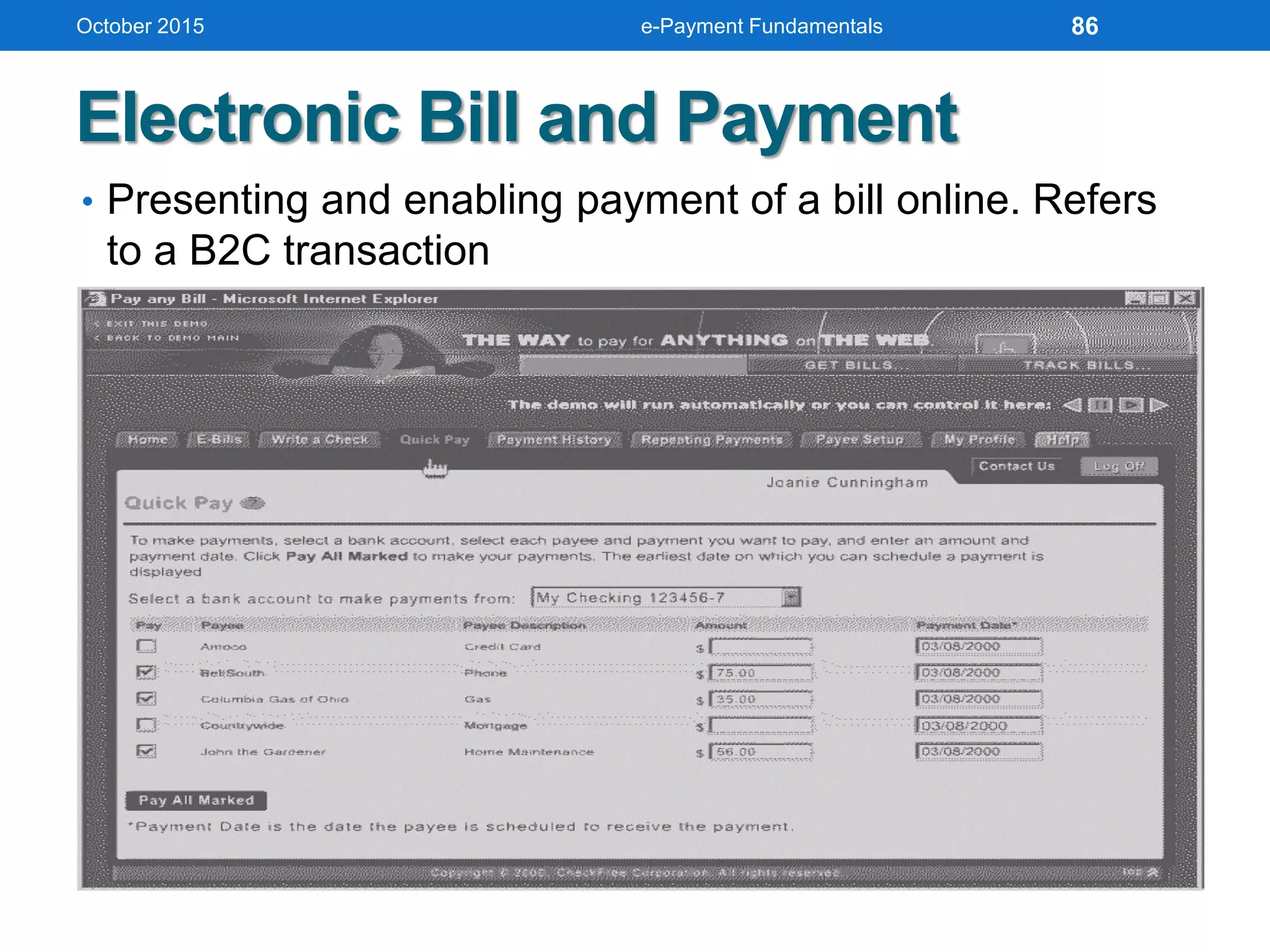
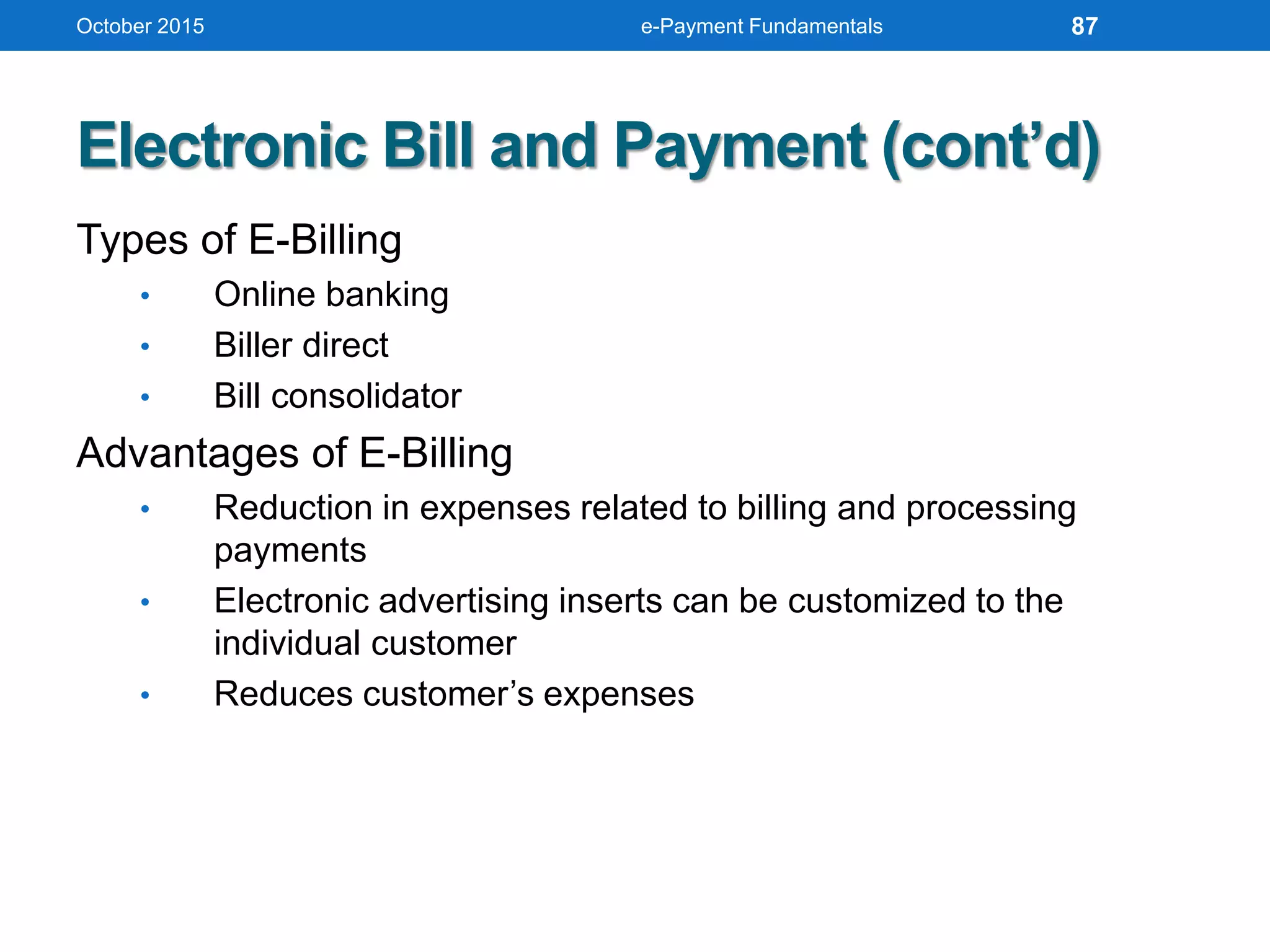
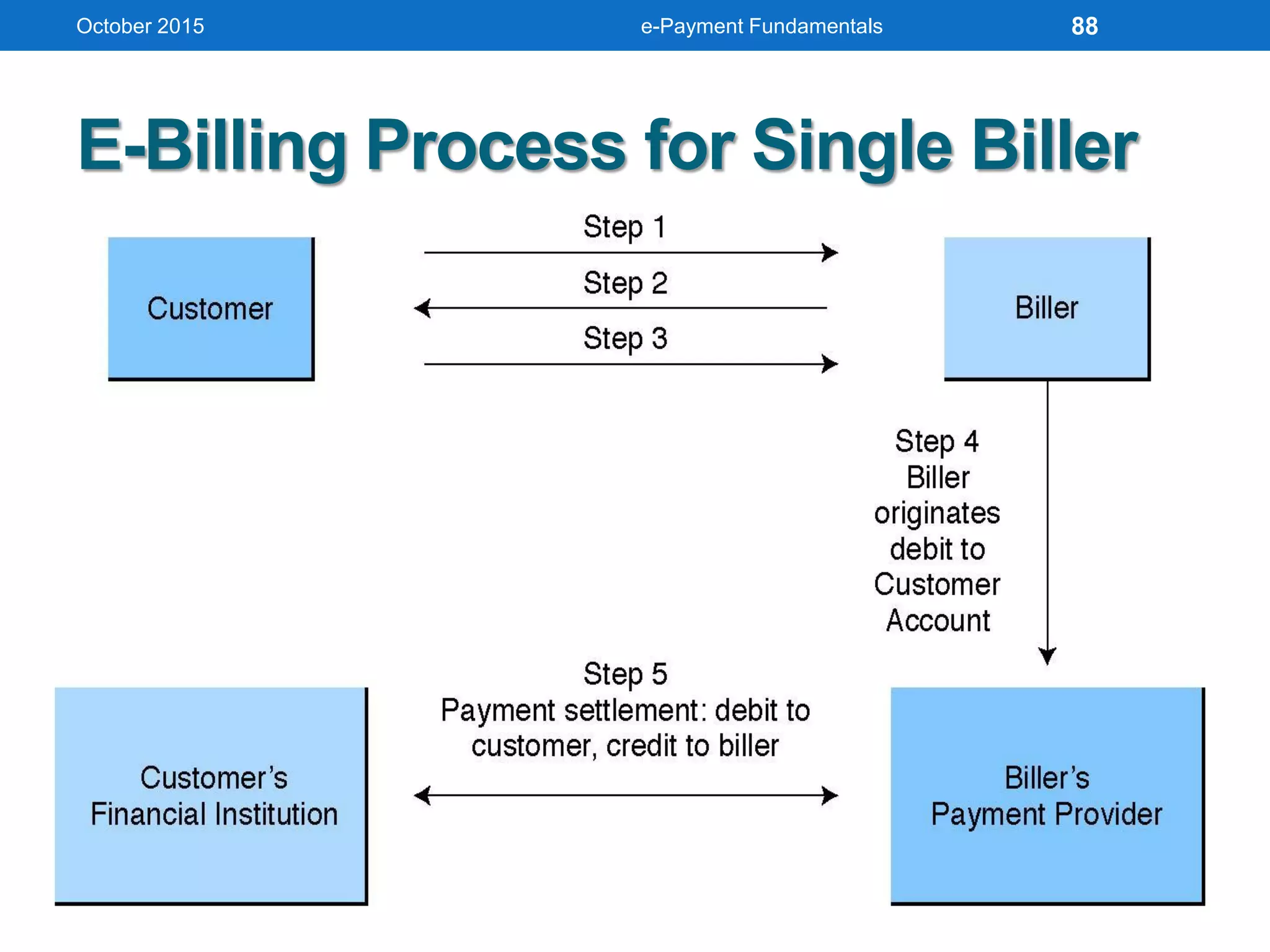
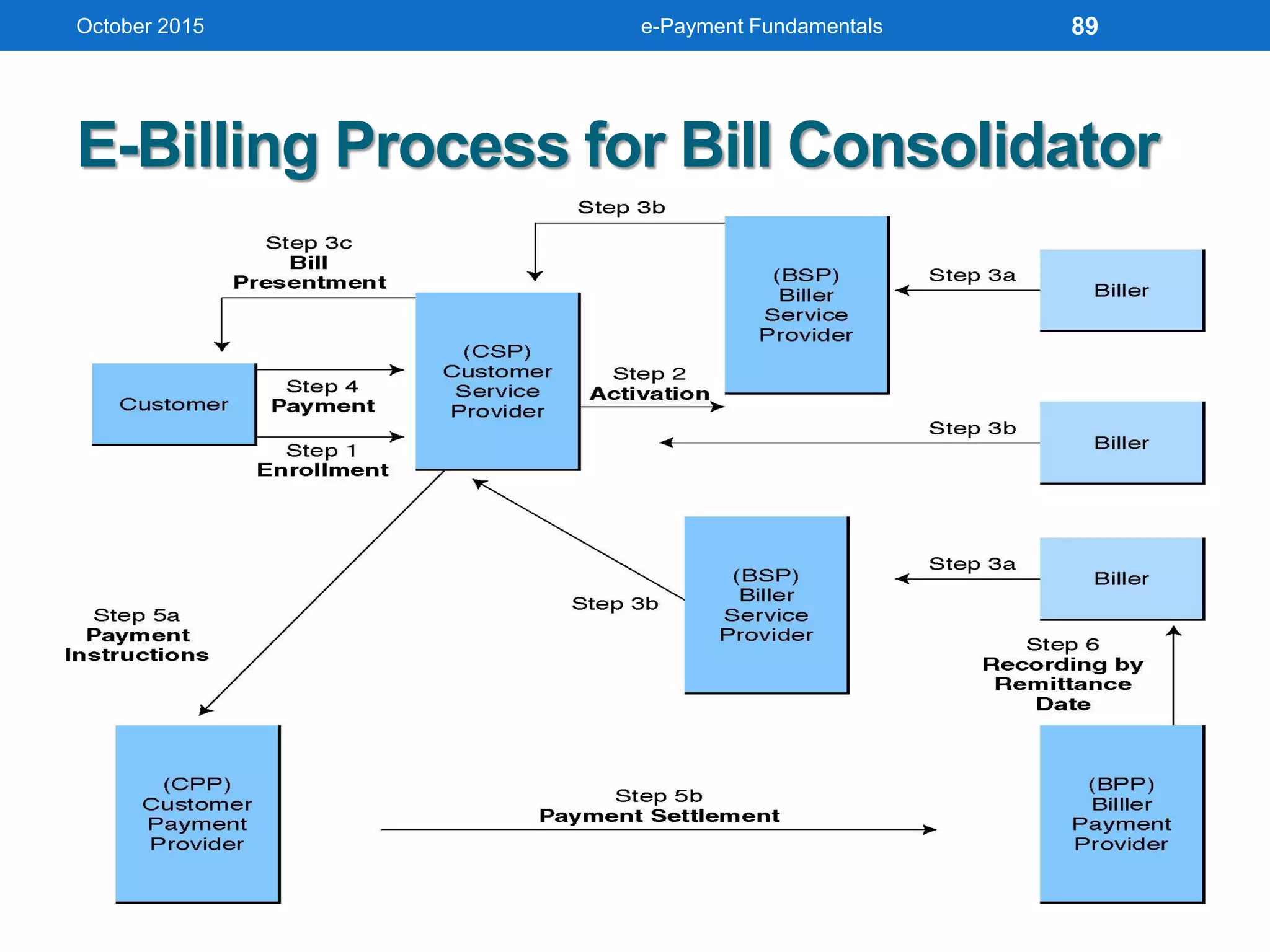
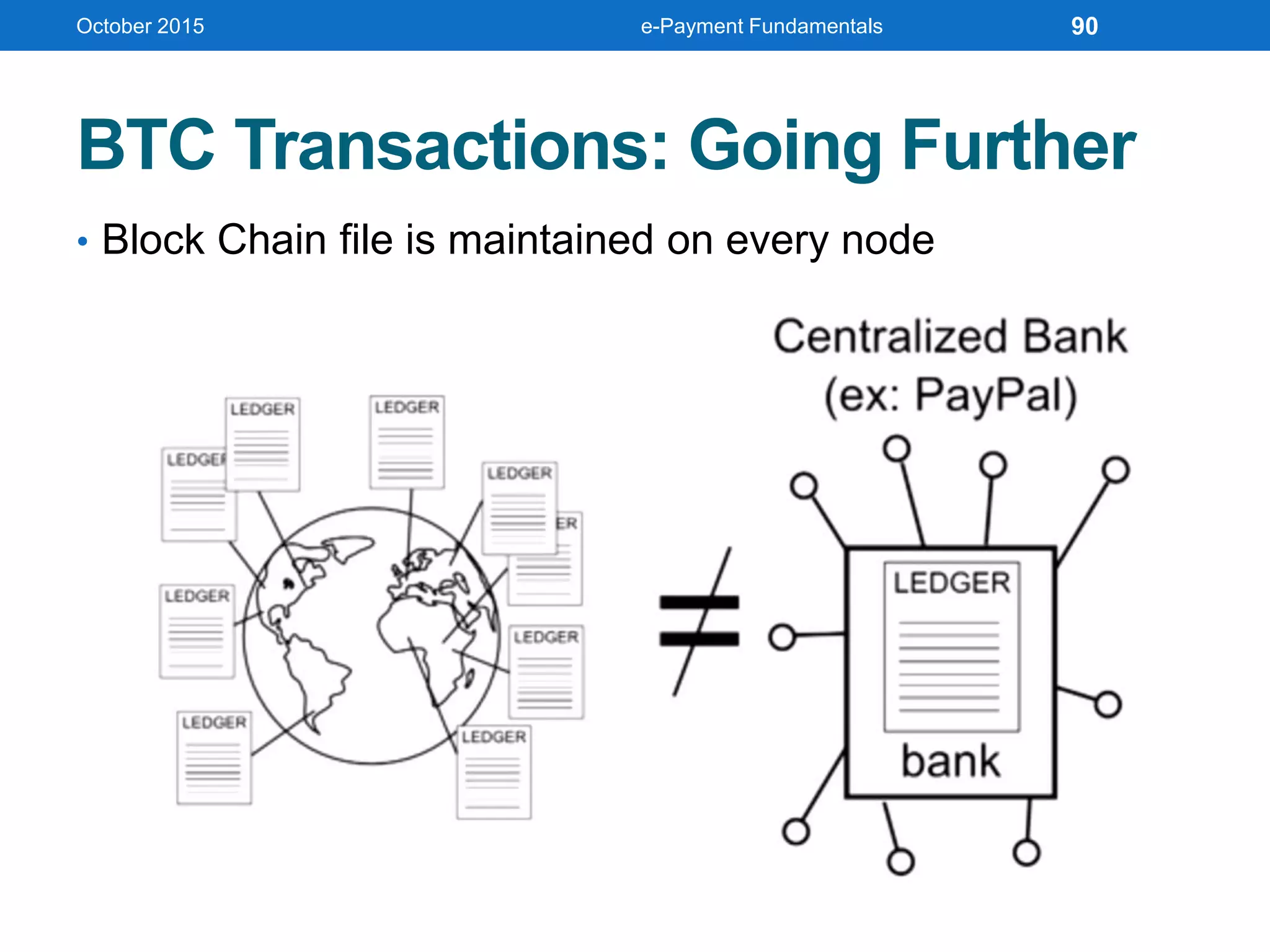
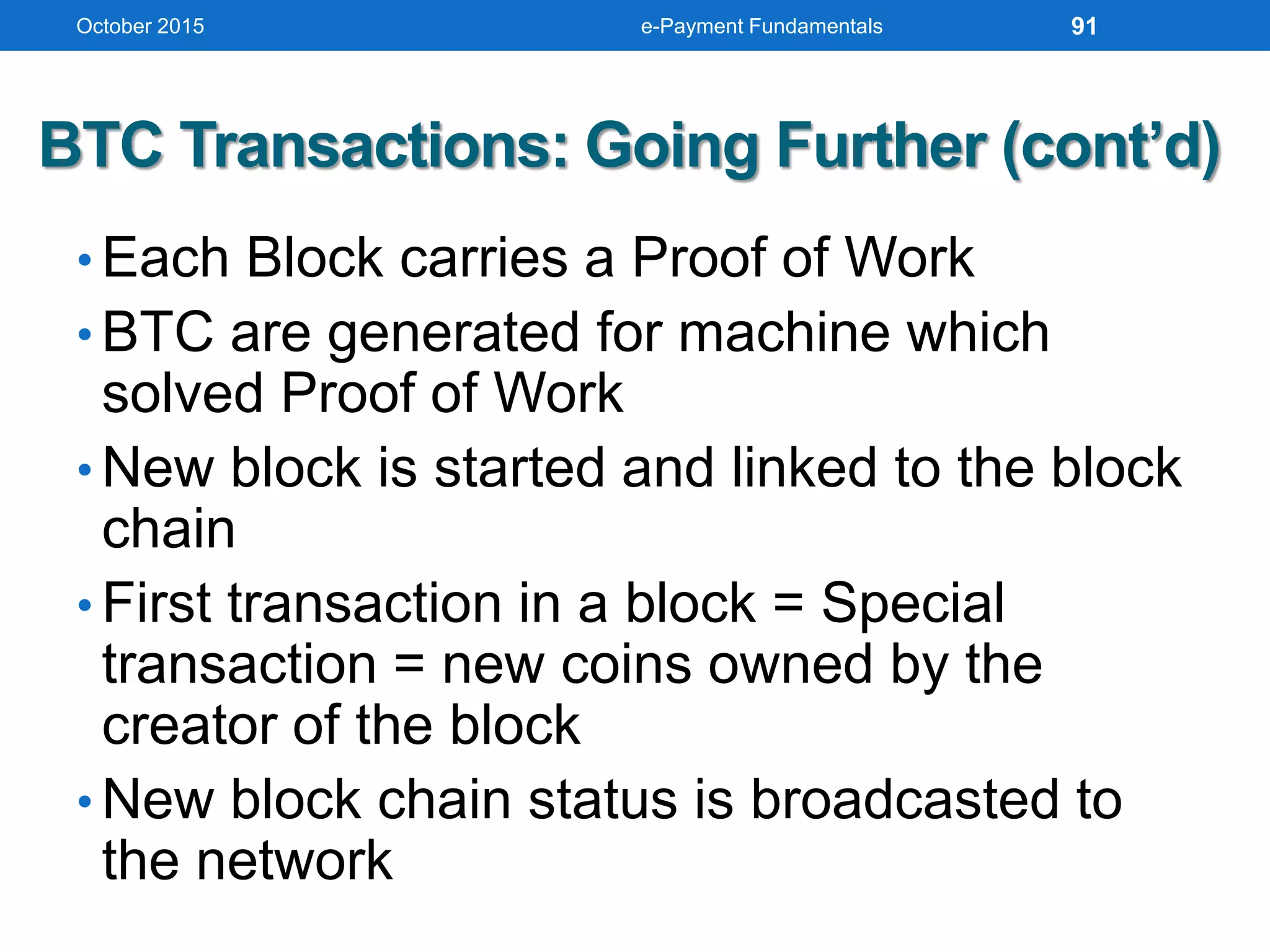
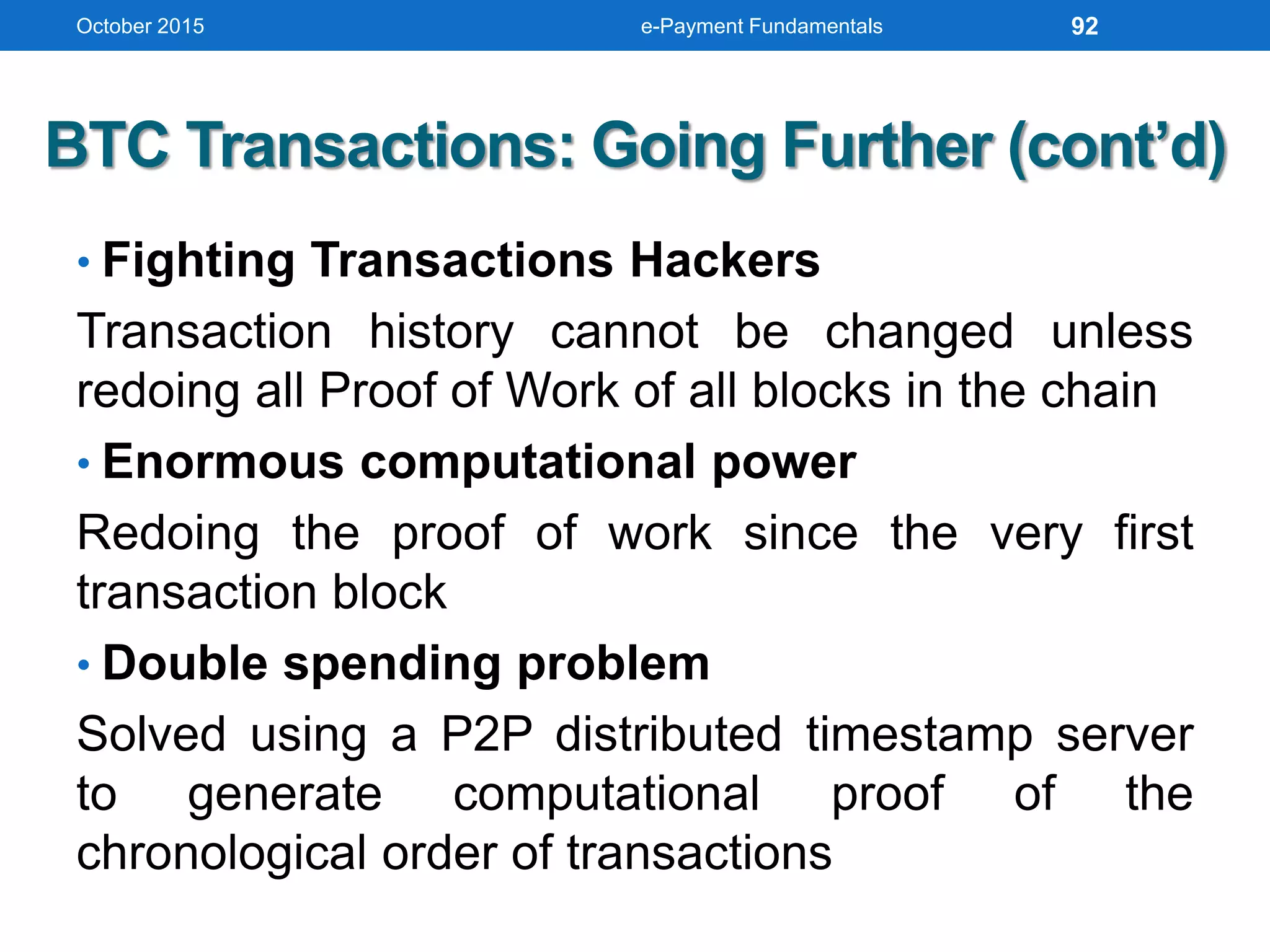
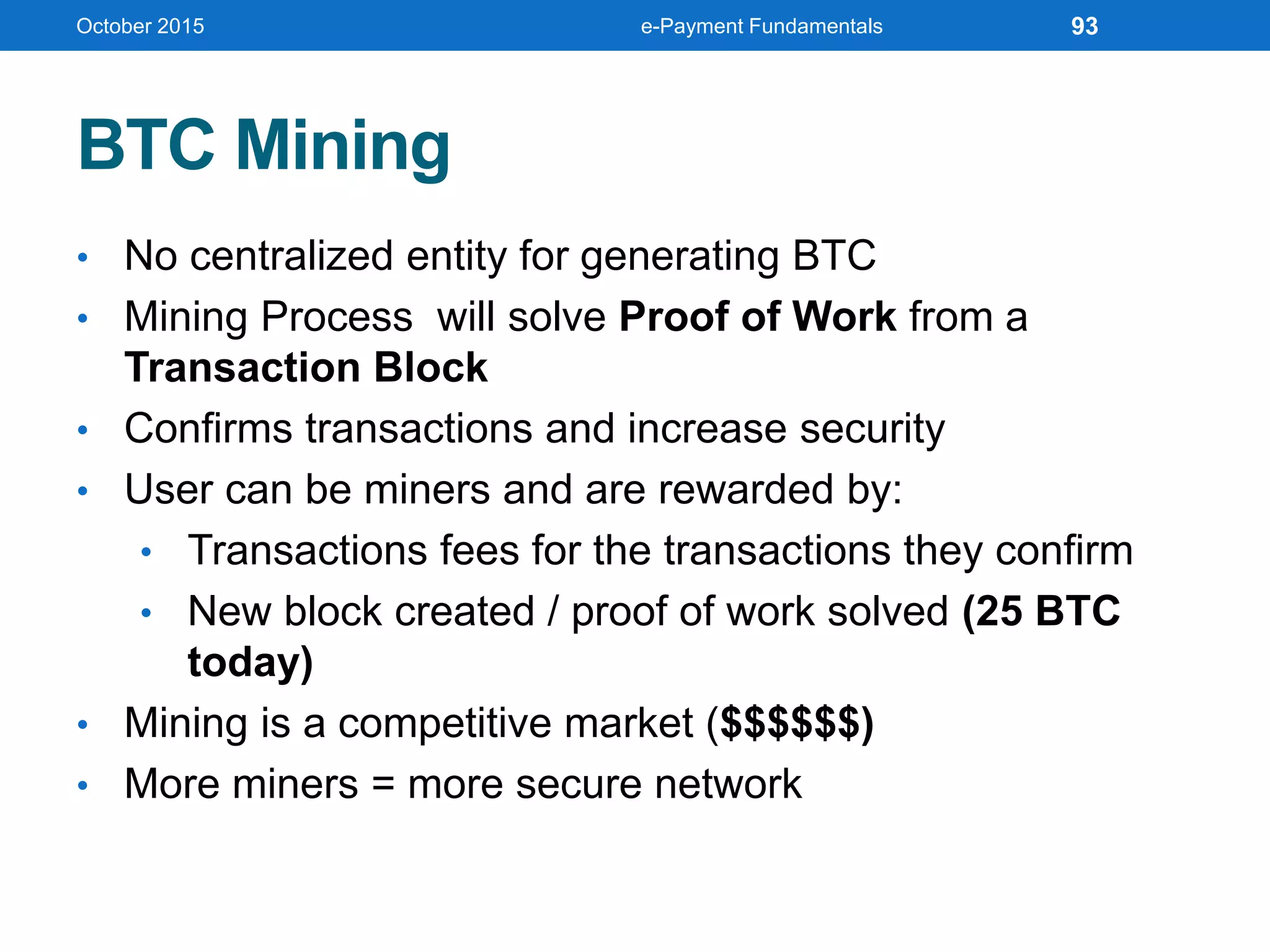
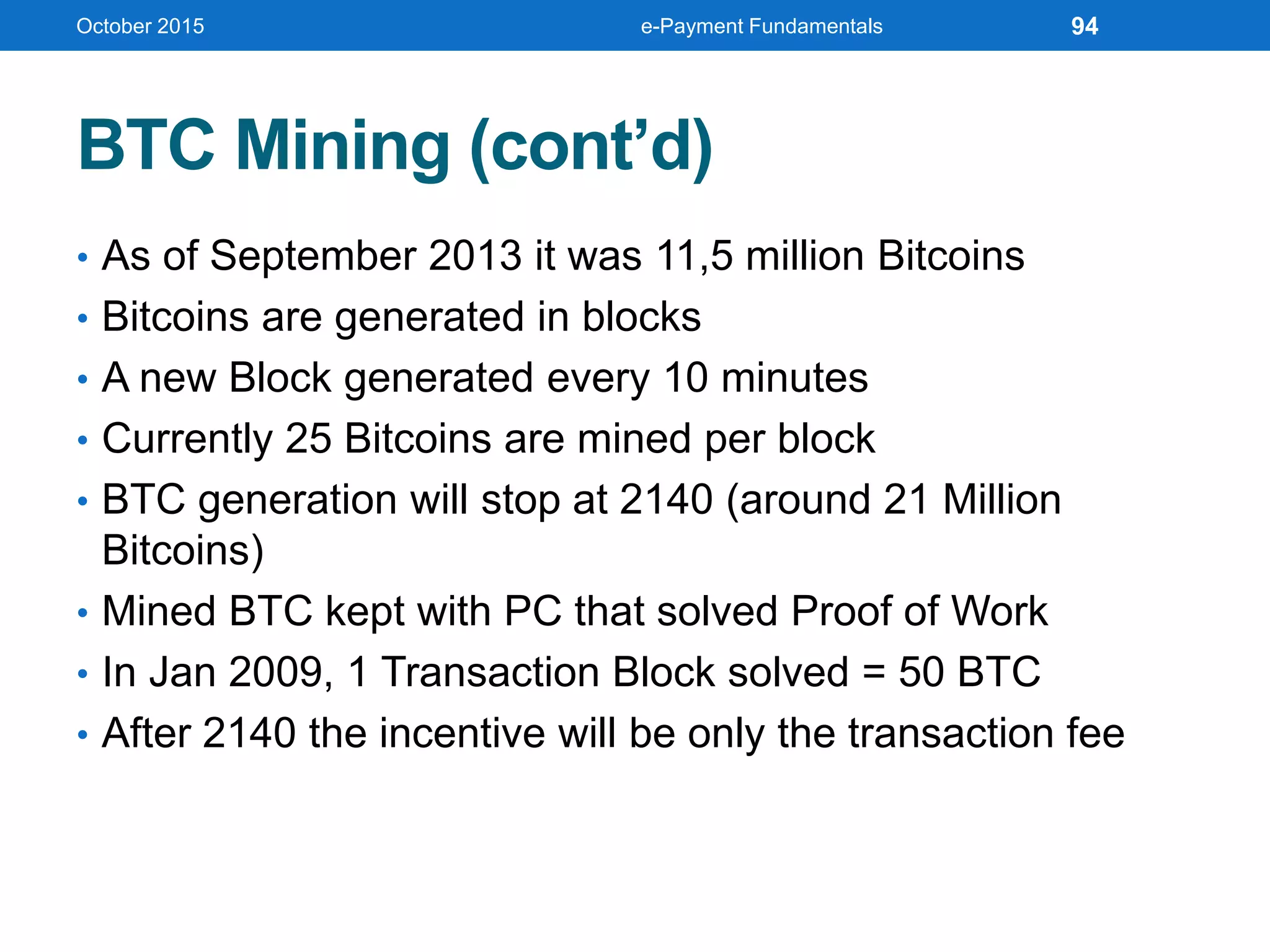
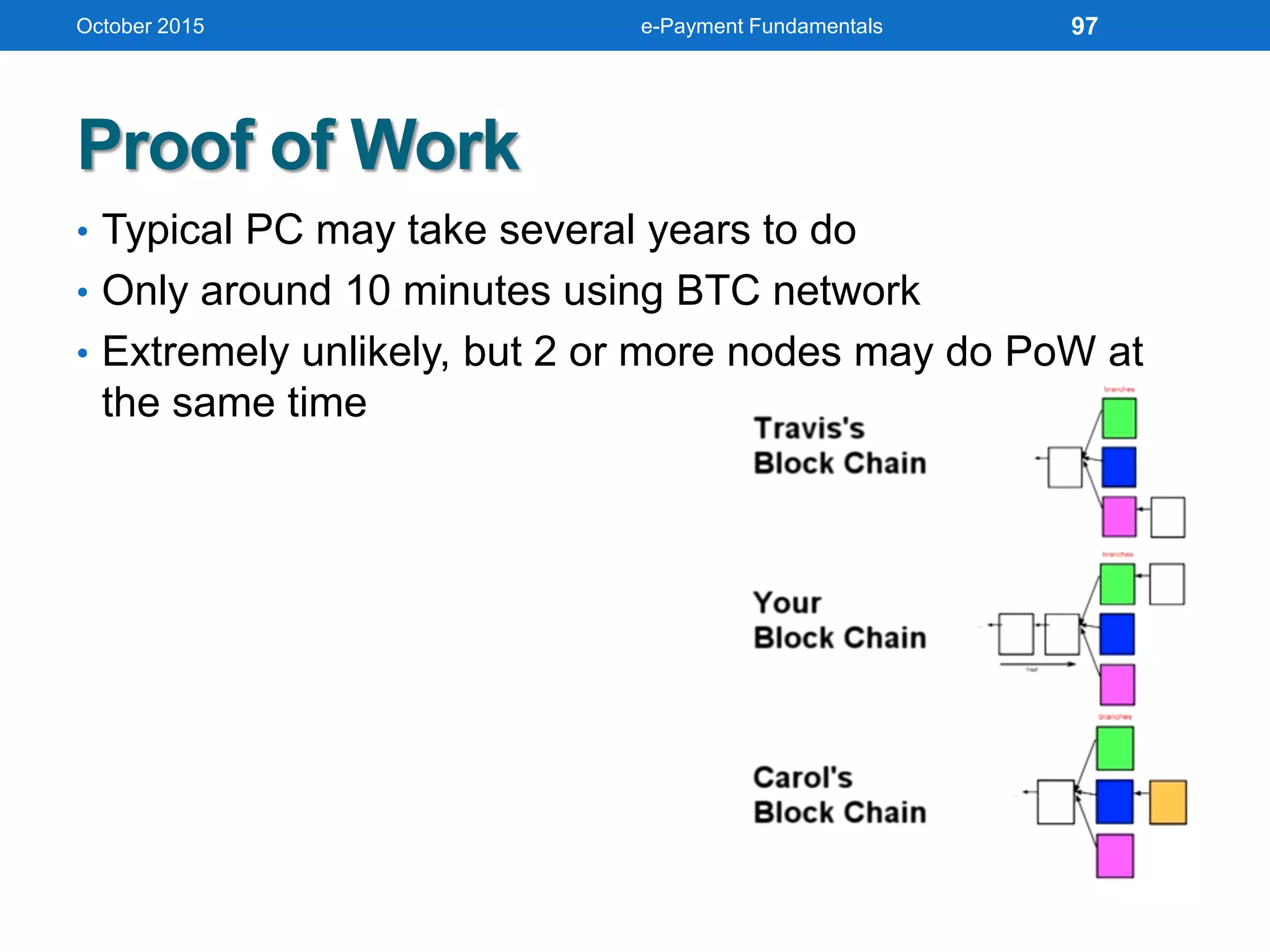
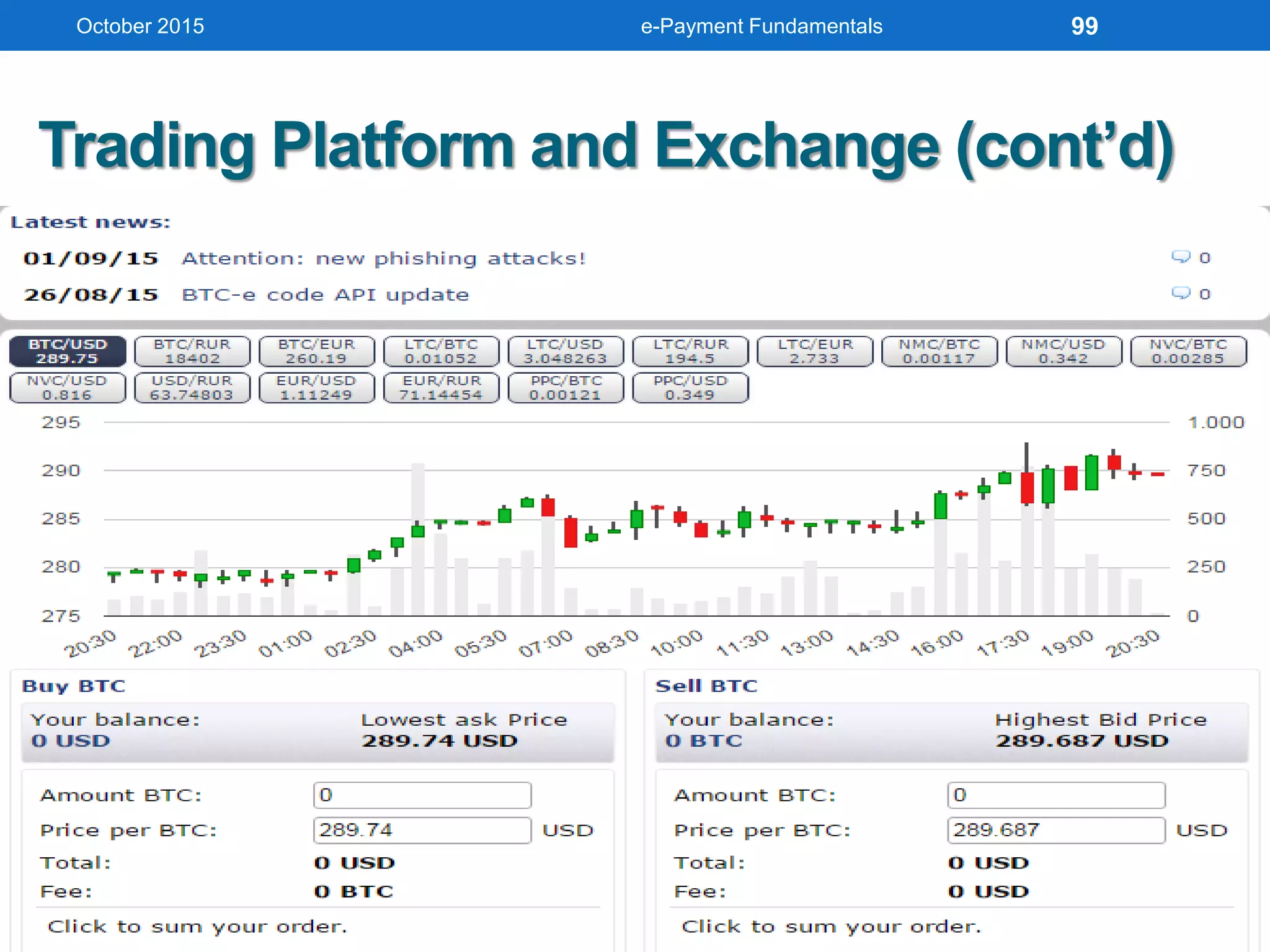
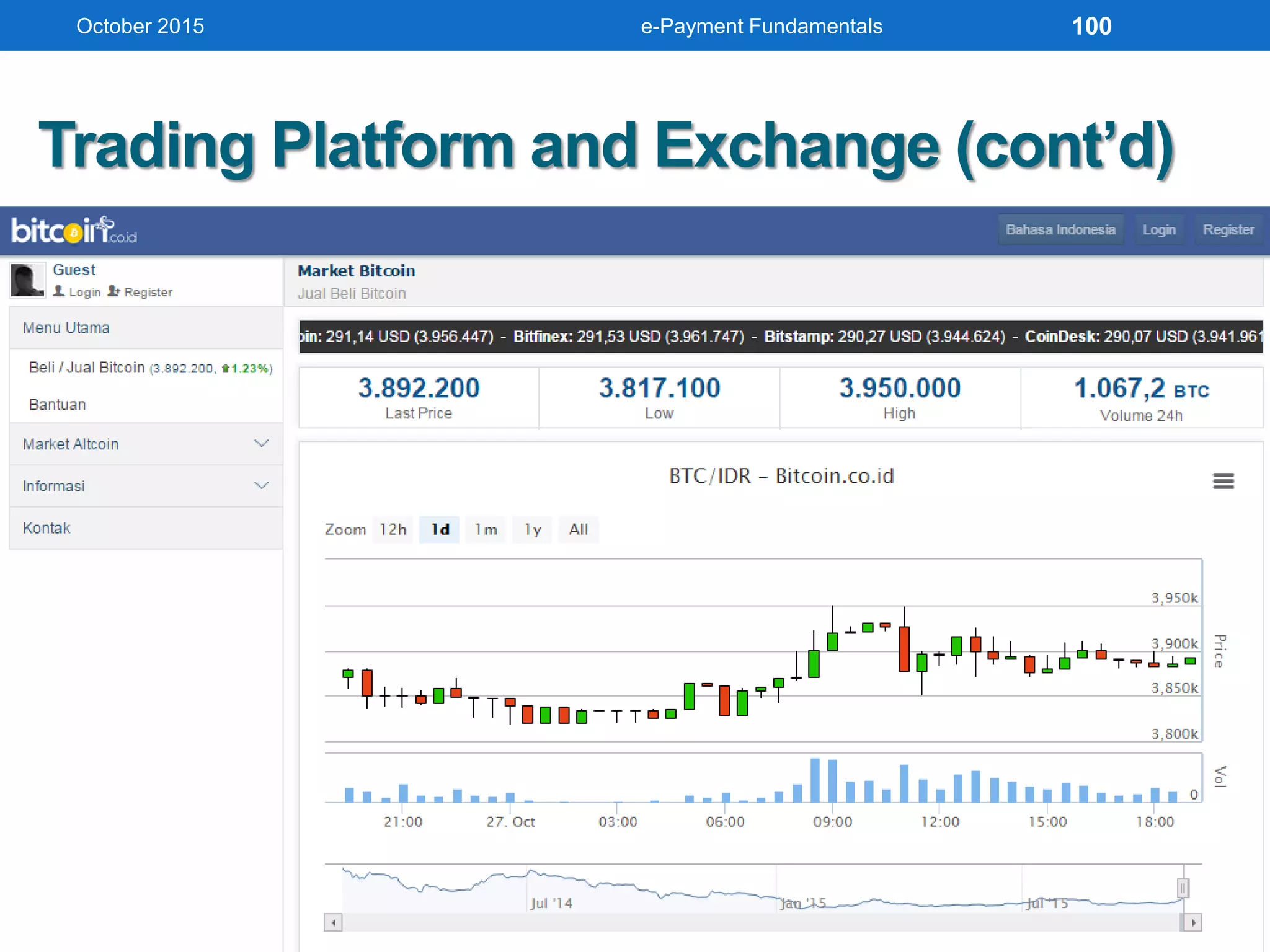
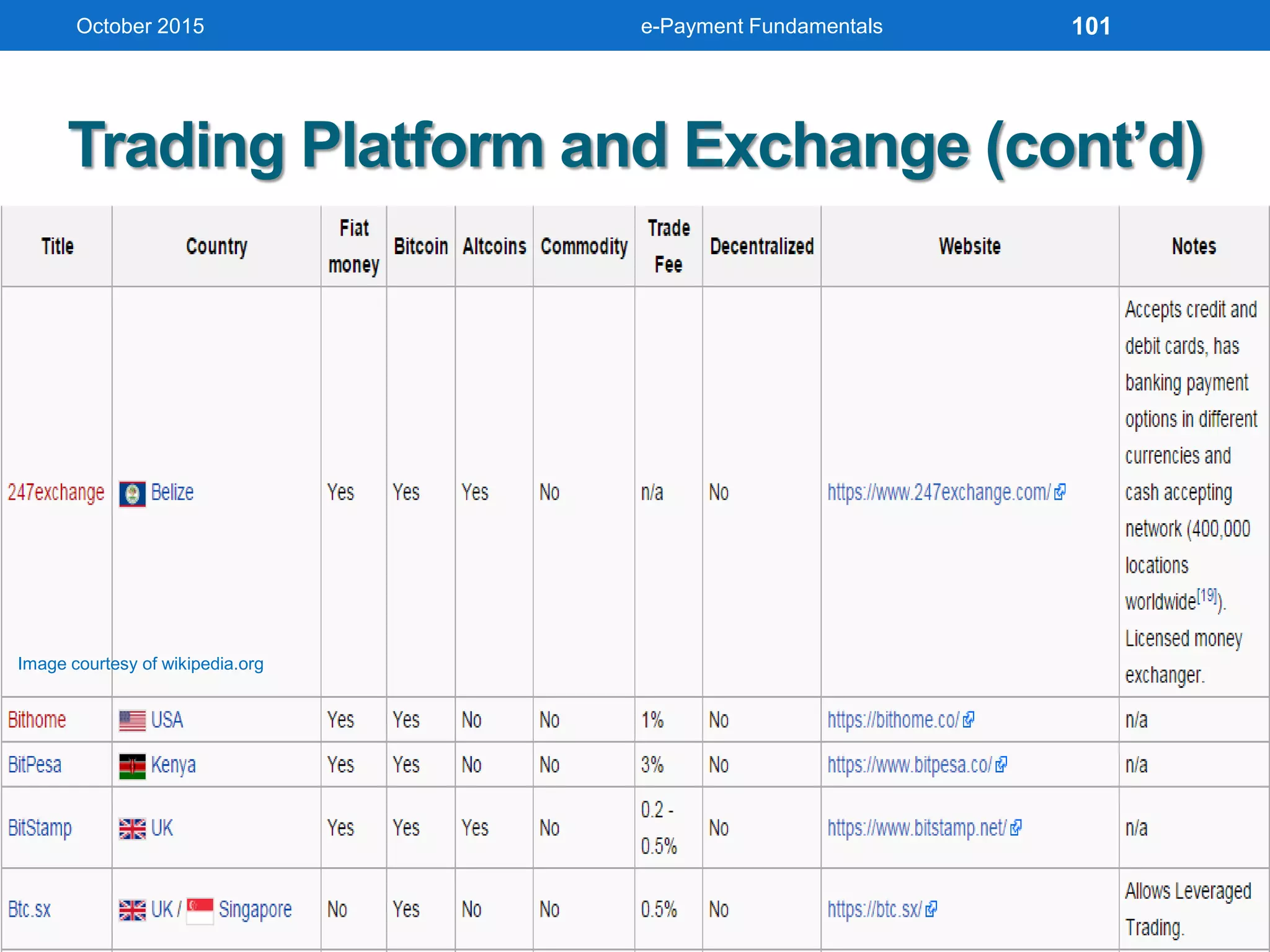
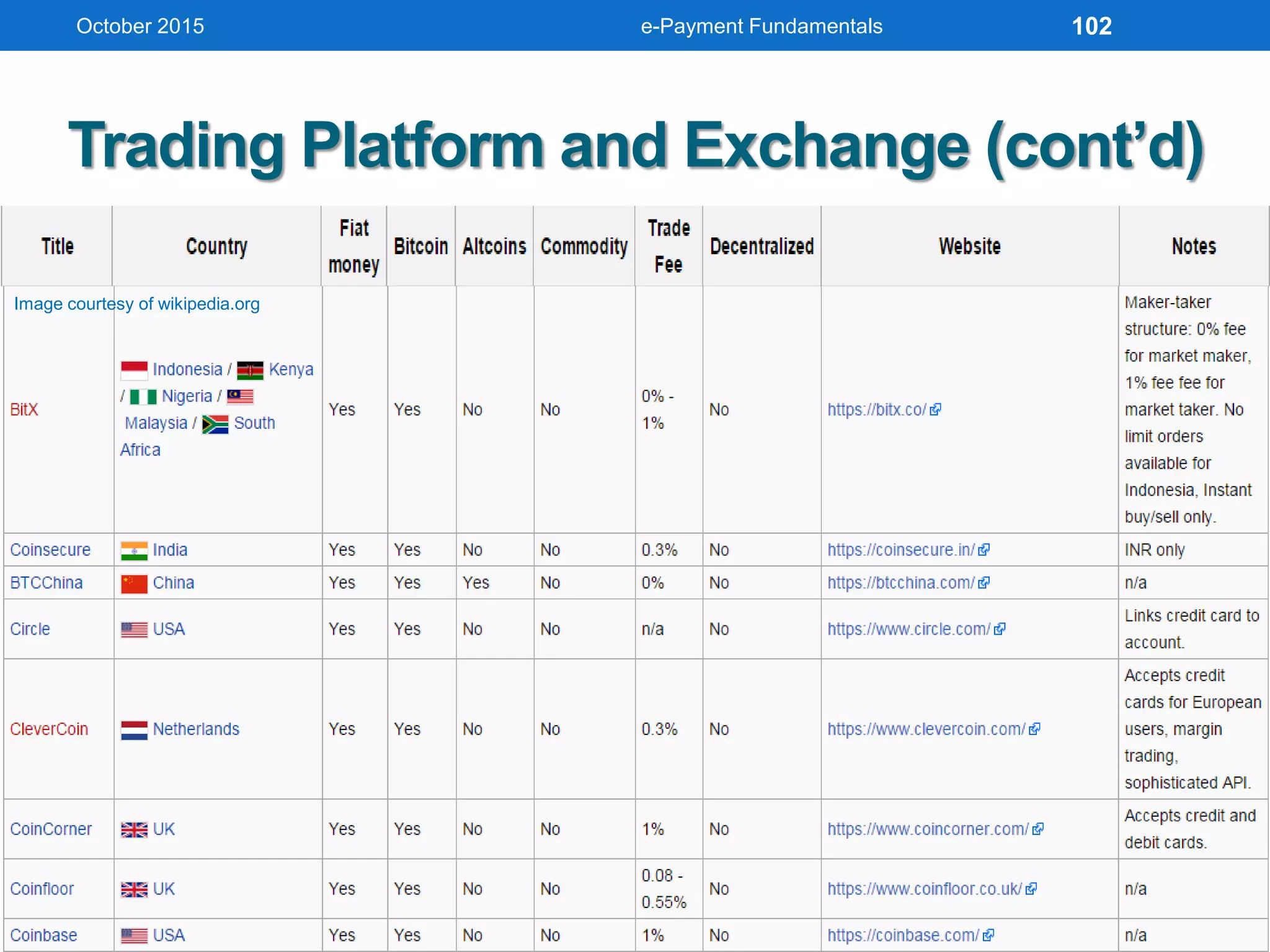
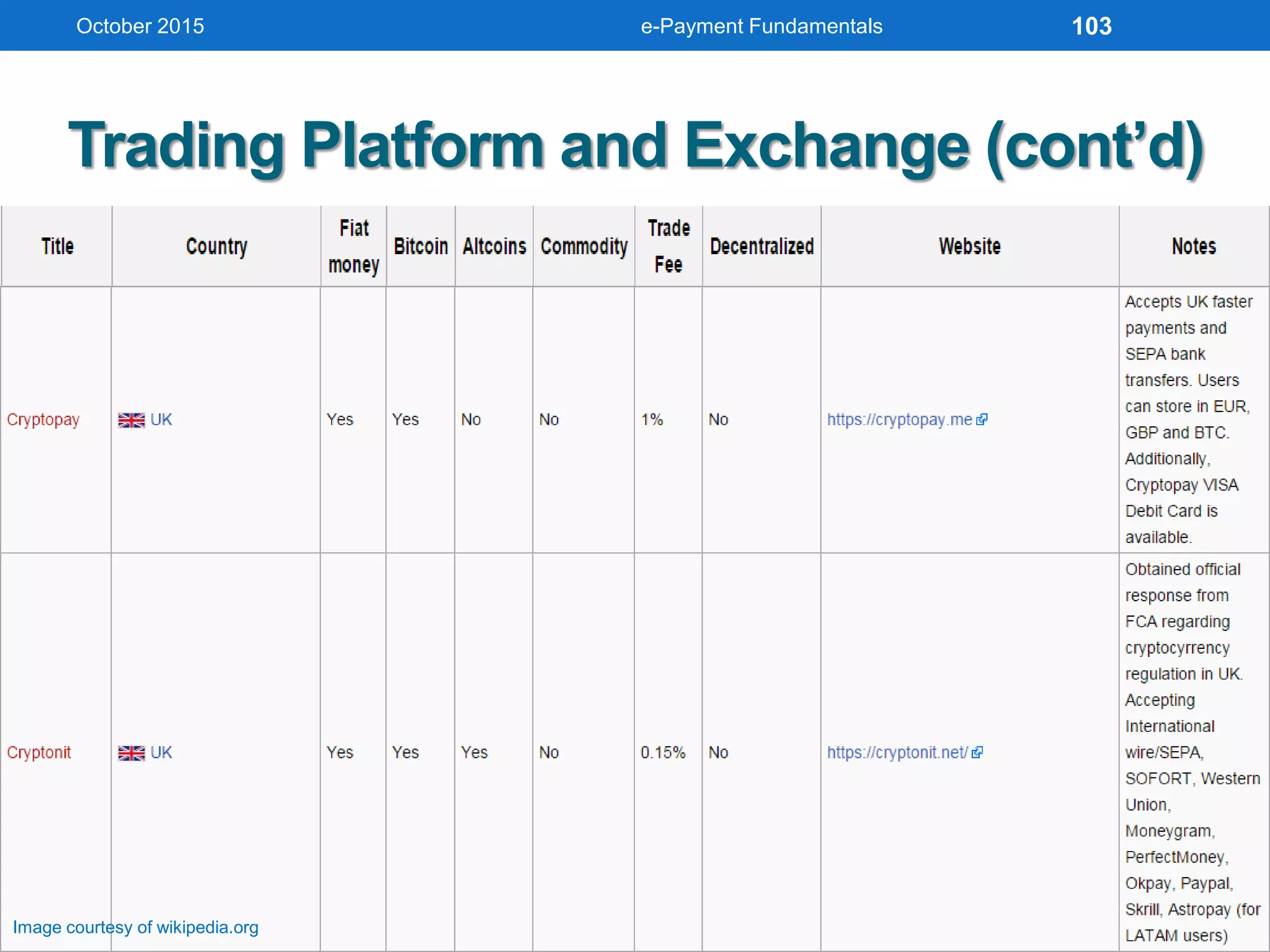
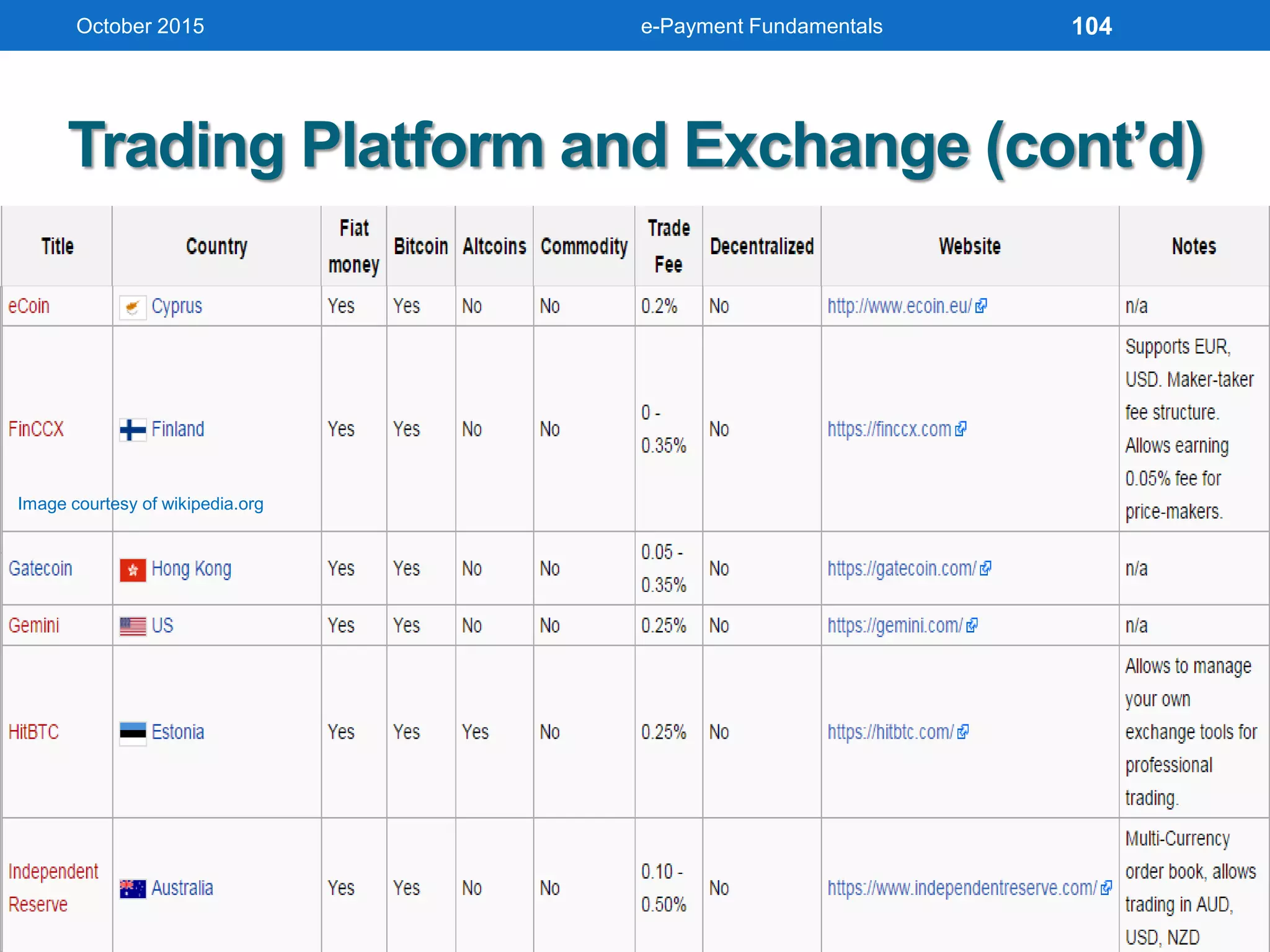
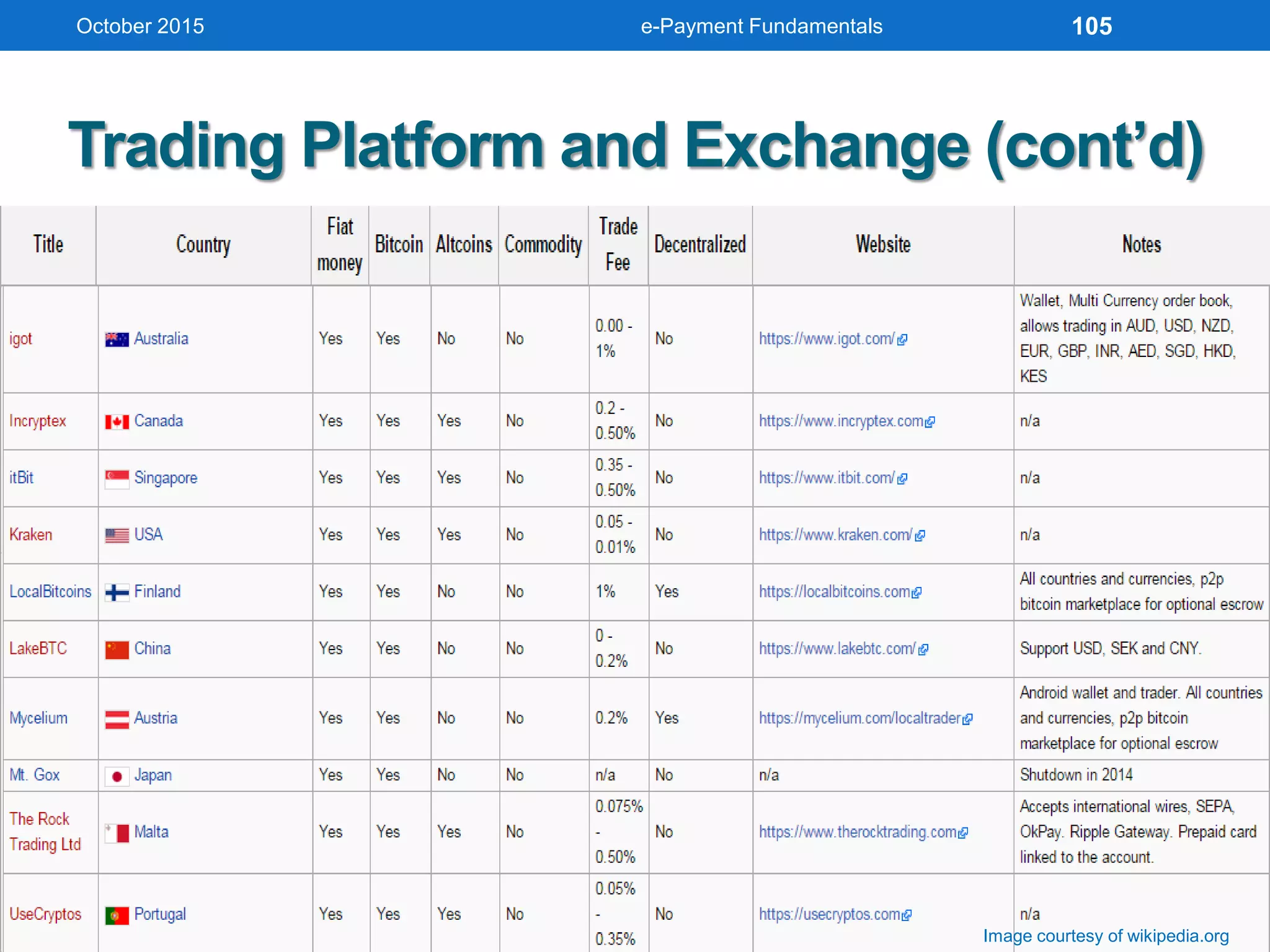
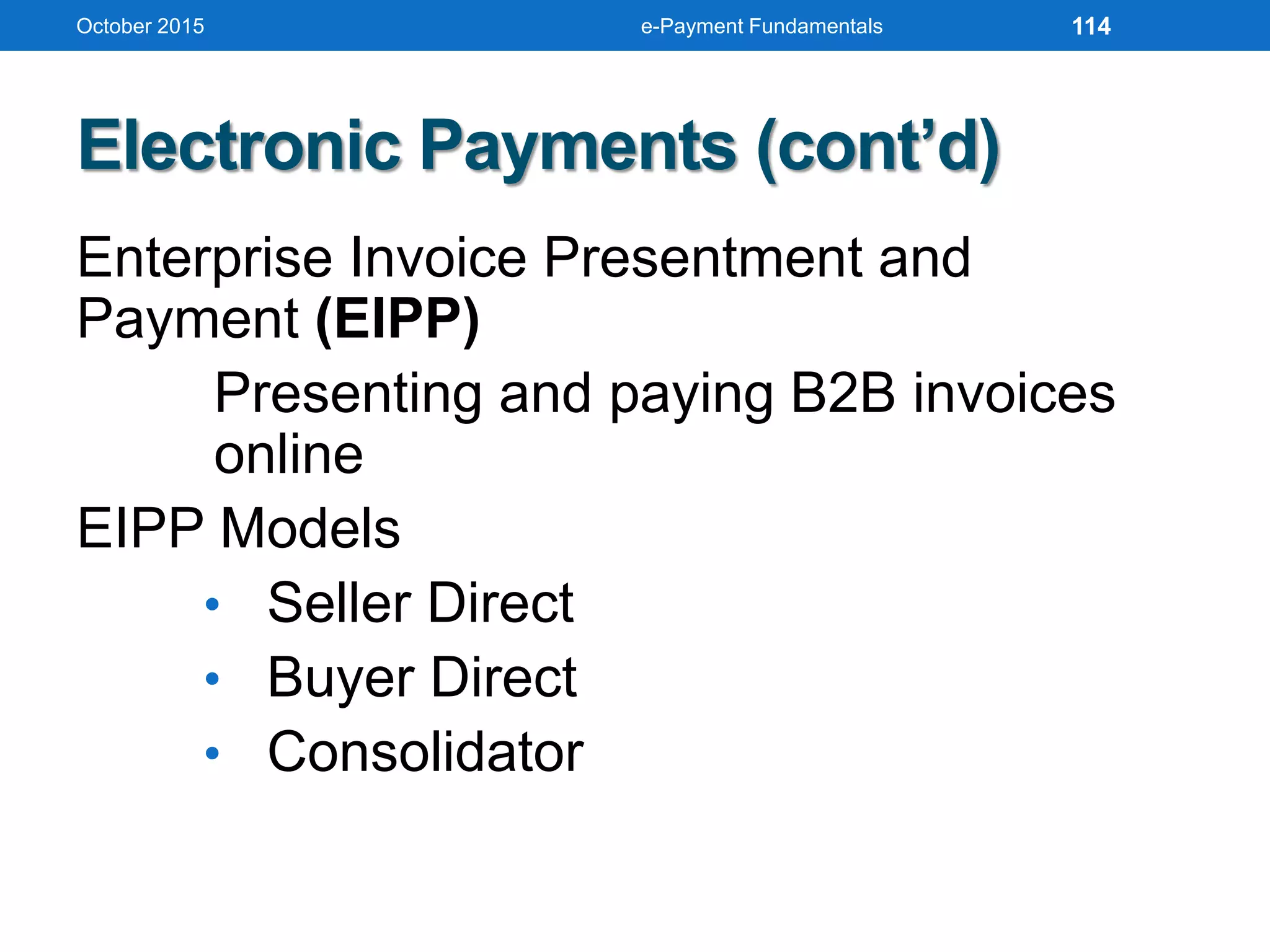
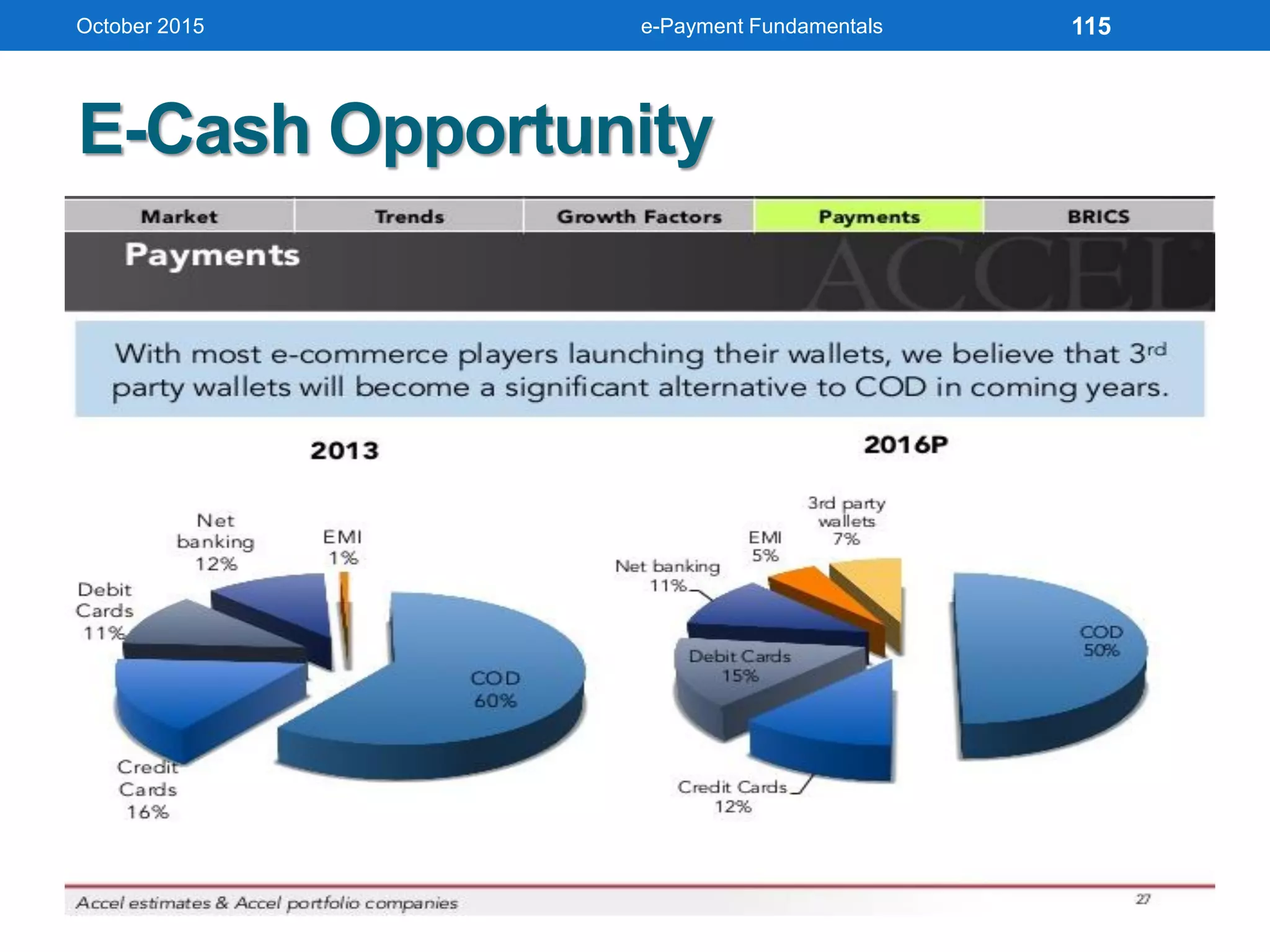
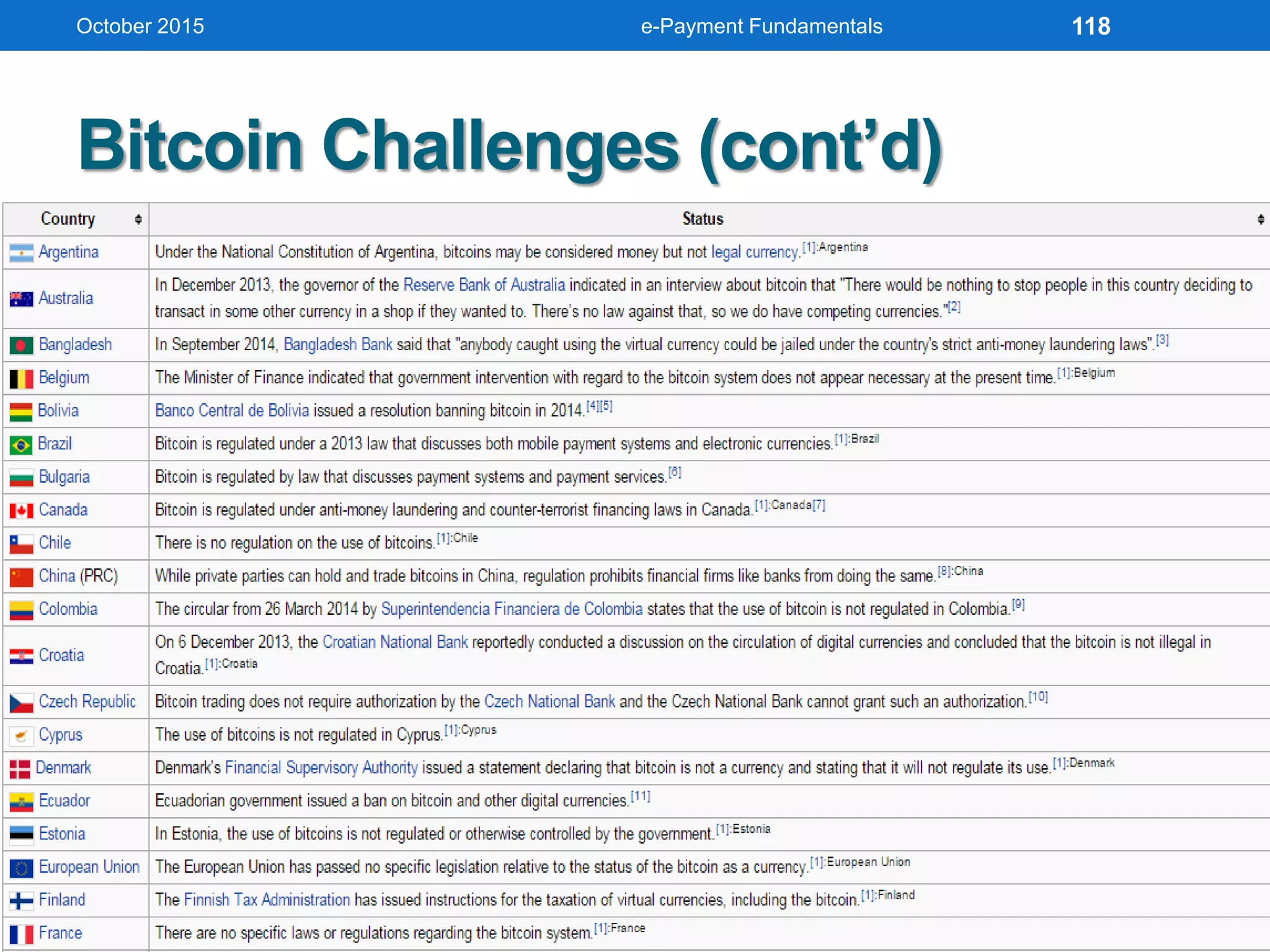
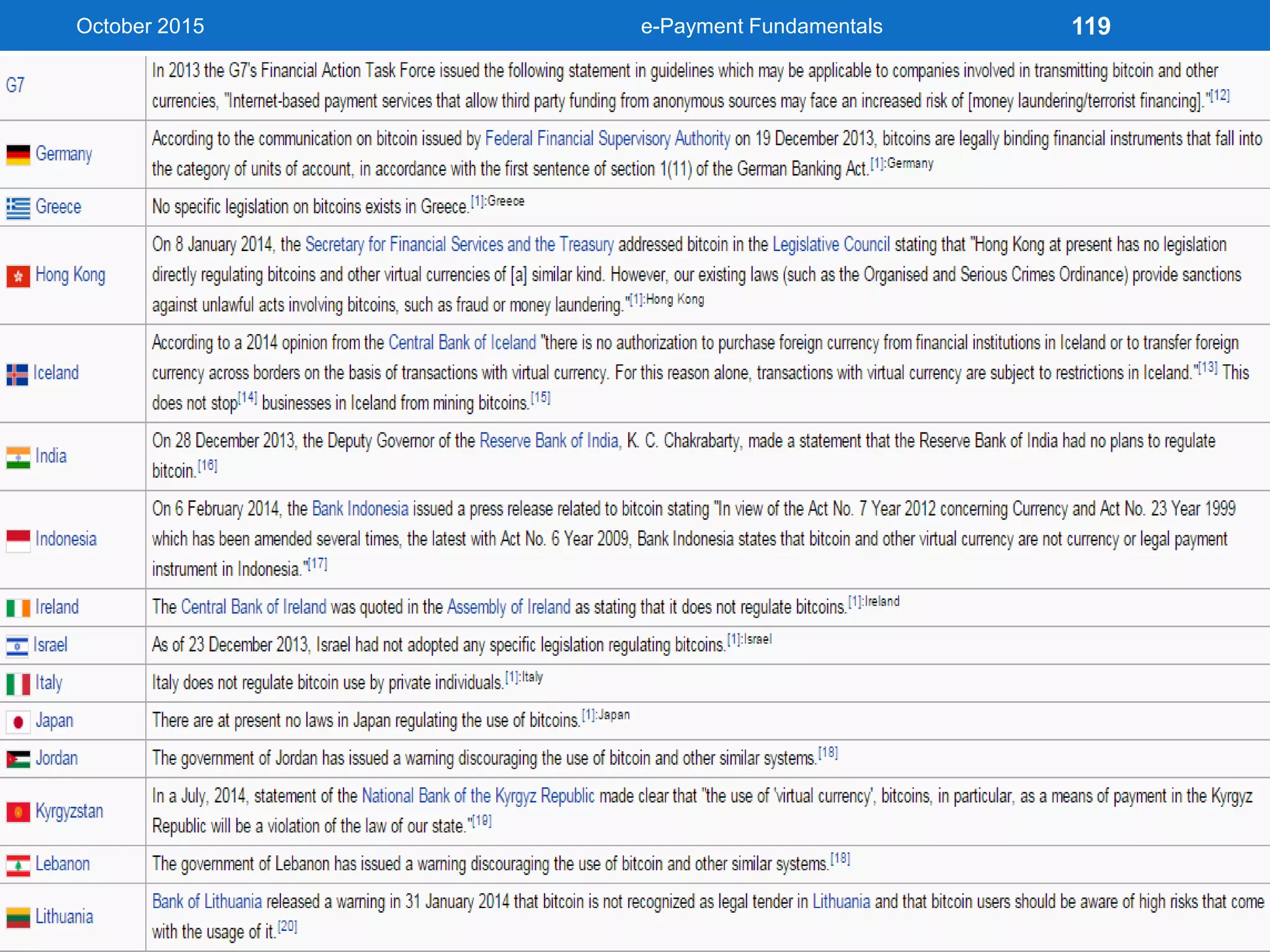
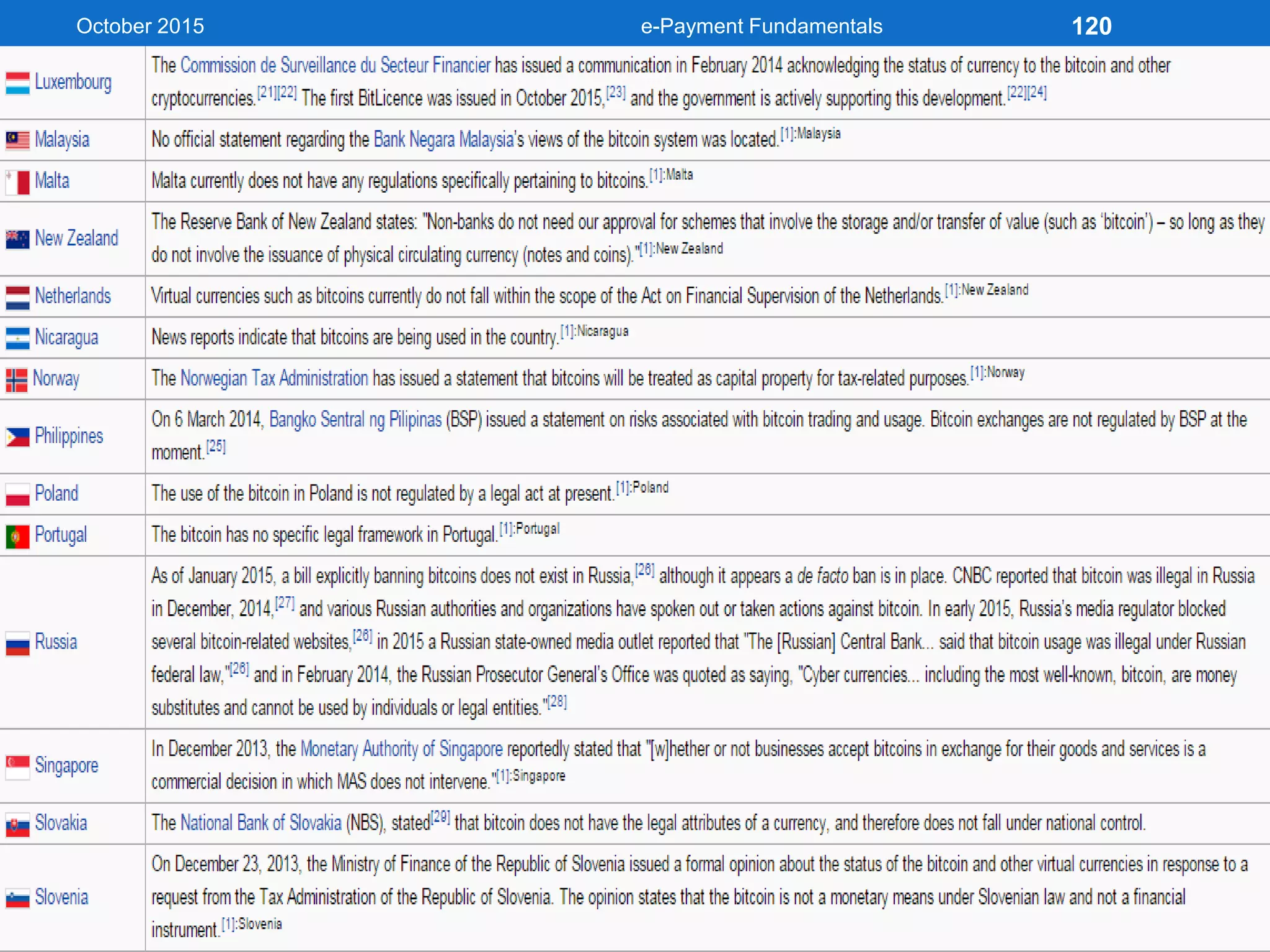
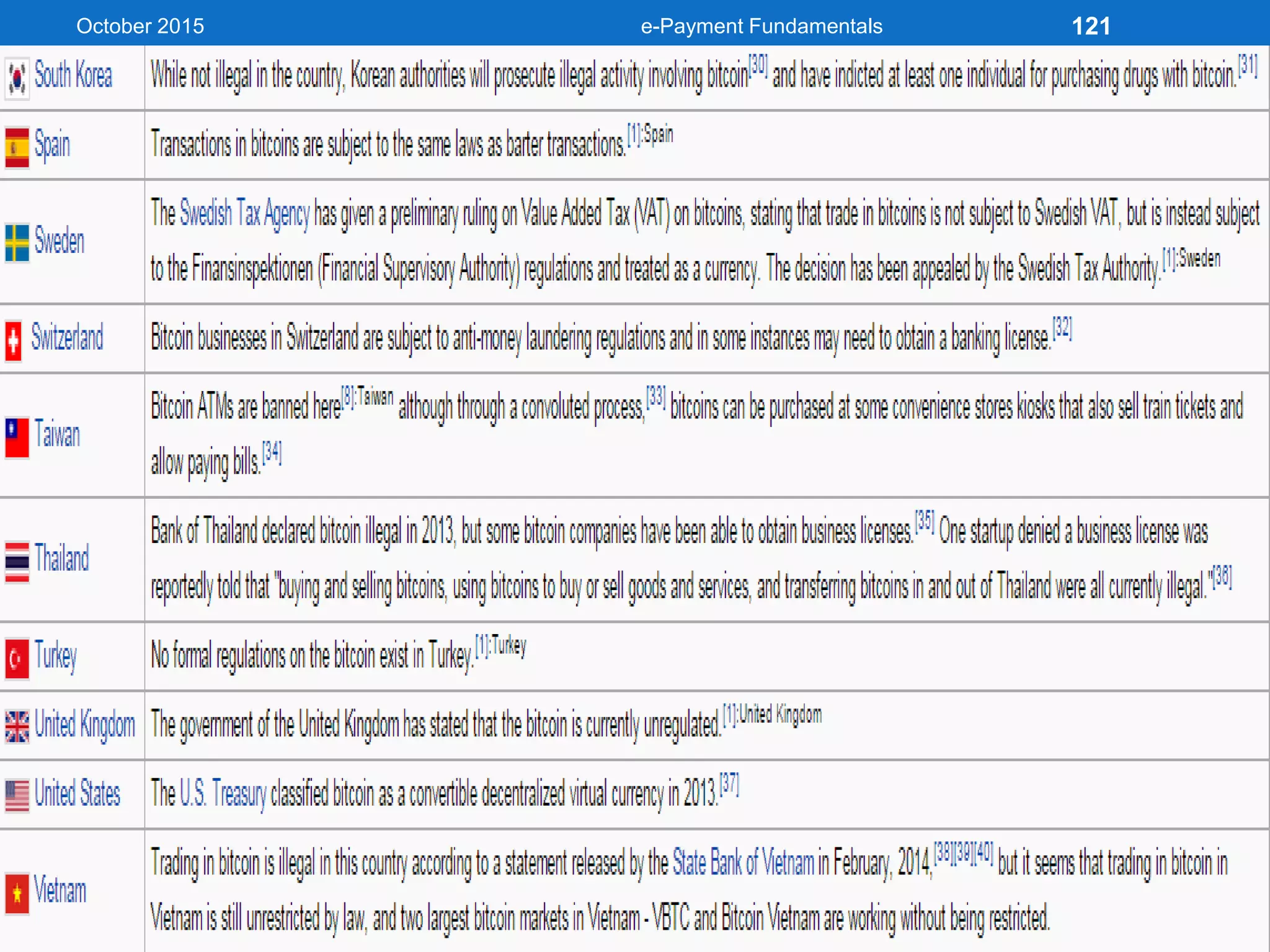
The document outlines an agenda for an e-payment fundamentals workshop held in October 2015. The workshop covers various topics over two days, including understanding electronic payment systems and how they work, exploring different e-payment methods like e-cash, e-wallets, smart cards, and credit cards, and examining security and infrastructure aspects. Diagrams and graphics are provided to illustrate concepts like how payment gateways and service providers facilitate electronic transactions between customers, merchants and banks.










































![October 2015
Source: IBM [1] UNODC Comprehensive Study on Cybercrime, 2013
e-Payment Fundamentals 124](https://image.slidesharecdn.com/electronicpaymentfundamentalsv1-151102111008-lva1-app6892/75/Electronic-Payment-Fundamentals-When-Tech-Embracing-Payment-Industry-124-2048.jpg)
![October 2015
Source: IBM
[2] FBI: Crime in the United States 2013
[3] United California Bank Robbery
[4] Center for Strategic and International Studies
e-Payment Fundamentals 125](https://image.slidesharecdn.com/electronicpaymentfundamentalsv1-151102111008-lva1-app6892/75/Electronic-Payment-Fundamentals-When-Tech-Embracing-Payment-Industry-125-2048.jpg)
![October 2015
Source: IBM [6] ESG: http://bit.ly/1xzTmUW
e-Payment Fundamentals 126](https://image.slidesharecdn.com/electronicpaymentfundamentalsv1-151102111008-lva1-app6892/75/Electronic-Payment-Fundamentals-When-Tech-Embracing-Payment-Industry-126-2048.jpg)