Embed presentation
Downloaded 15 times














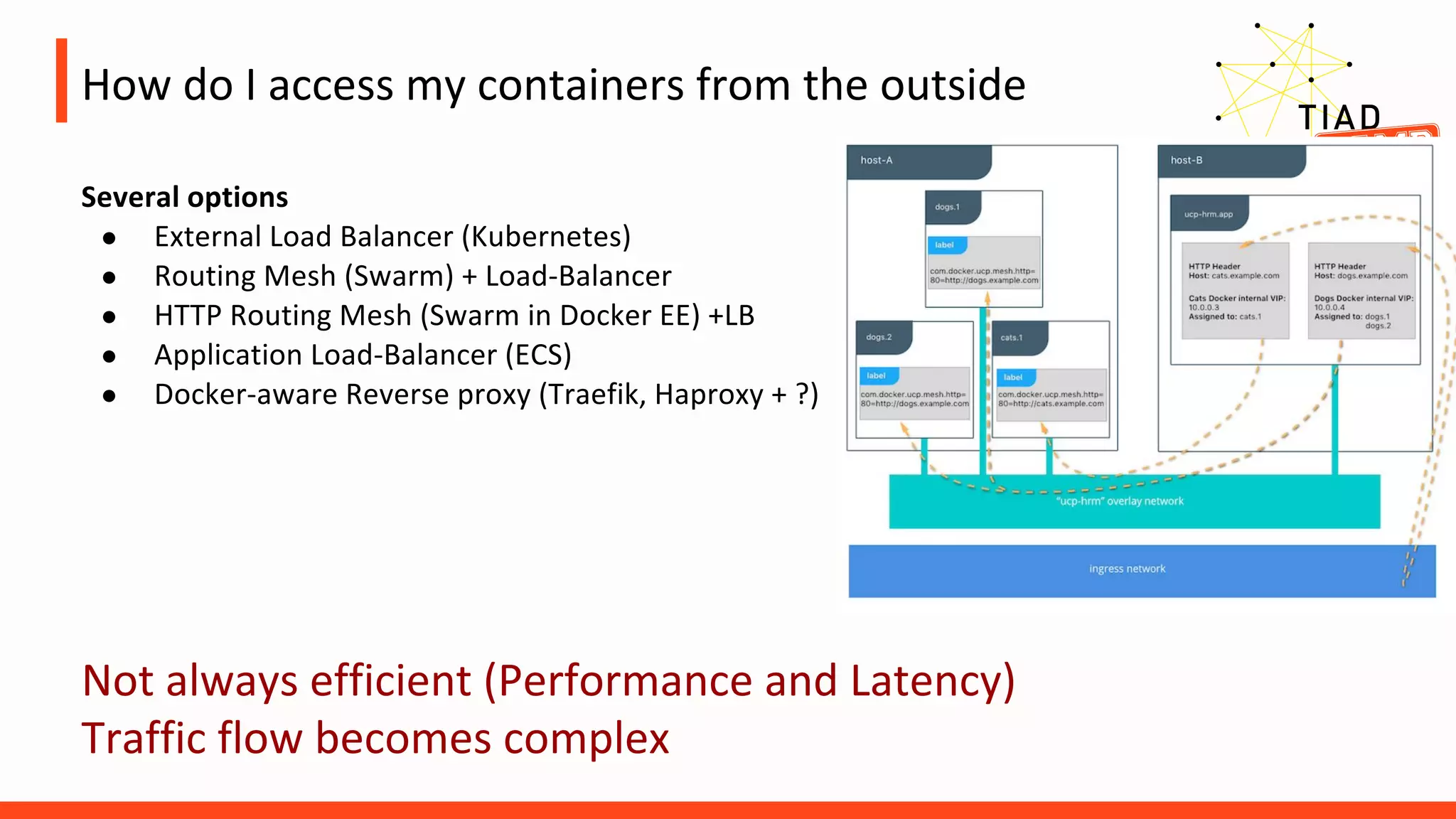


The document contains the agenda for an Automation Day event focused on Docker strategies. It lists the schedule of presentations and workshops on topics like virtualization, containerization, monitoring, migration to Docker, and orchestrating Docker in production. The day includes sessions for beginners and advanced users, with keynotes in the morning and beers in the afternoon.





















