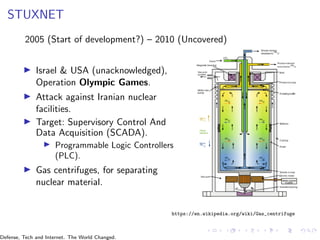
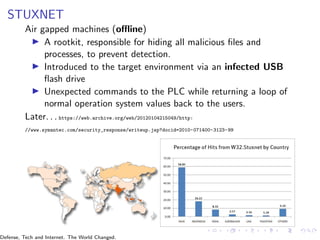
This document discusses the evolution of cyber defense and technology. It first provides background on the author and their research interests. It then summarizes the Stuxnet attack on Iranian nuclear facilities between 2005-2010, believed to be carried out by Israel and the US. This marked a shift to states using cyber capabilities. The document next discusses cyberattacks that occurred during the Ukraine war and outlines a strategy of hybrid warfare combining conventional and cyber operations. It concludes by recommending related reading on cyber weapons and security.